The document discusses various cryptographic techniques including:
- Block ciphers like the Shift Cipher, Substitution Cipher, Affine Cipher, Vigenere Cipher, Hill Cipher, and Permutation Cipher.
- Stream ciphers like the Linear Feedback Shift Register (LFSR) cipher.
- Public key cryptography techniques including RSA, Rabin, and the Digital Signature Algorithm (DSA).
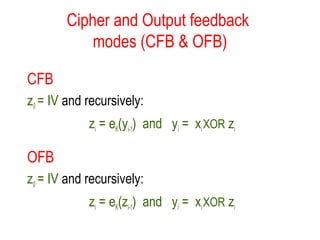
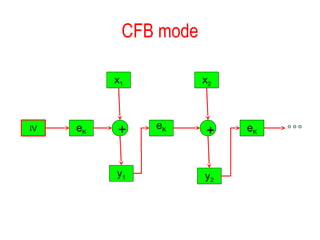
- Modes of operation for block ciphers like Electronic Codebook (ECB), Cipher Block Chaining (CBC), Cipher Feedback (CFB), and Output Feedback (OFB).

















![Some Probability Theory
• The random variables X,Y are independent
if:
Pr[x,y] = Pr[x] . Pr[y], for all x,y in X
In general,
Pr[x,y] = Pr[x|y] . Pr[y]
= Pr[y|x] . Pr[x], for all x,y in X](https://image.slidesharecdn.com/rgzoedxirmoomlwg1pef-signature-072e555ea9c42a01b892d90996a1c25135253c59813d8e7b613cf799625637a2-poli-160425163235/85/Computer-security-18-320.jpg)
![Some Probability Theory
• Bayes’ Law:
Pr[x|y] =
• Corollary:
X,Y are independent random variables (r.v.)
iff
Pr[x|y] = Pr[x] for all x,y in X
Pr[y]
Pr[y|x] . Pr[x]
---------------- for all x,y in X](https://image.slidesharecdn.com/rgzoedxirmoomlwg1pef-signature-072e555ea9c42a01b892d90996a1c25135253c59813d8e7b613cf799625637a2-poli-160425163235/85/Computer-security-19-320.jpg)
![Perfect secrecy
• A cryptosystem is perfectly secure if :
Pr[x|y] = Pr[x],
for all x in M and y in C](https://image.slidesharecdn.com/rgzoedxirmoomlwg1pef-signature-072e555ea9c42a01b892d90996a1c25135253c59813d8e7b613cf799625637a2-poli-160425163235/85/Computer-security-20-320.jpg)




![DES
It has a round function g for which:
g([Li-1
,Ri-1
]),Ki
) = (Li
,Ri
),
where
Li
= Ri-1
and Ri
= Li-1
XOR f (Ri-1
, Ki
).](https://image.slidesharecdn.com/rgzoedxirmoomlwg1pef-signature-072e555ea9c42a01b892d90996a1c25135253c59813d8e7b613cf799625637a2-poli-160425163235/85/Computer-security-25-320.jpg)