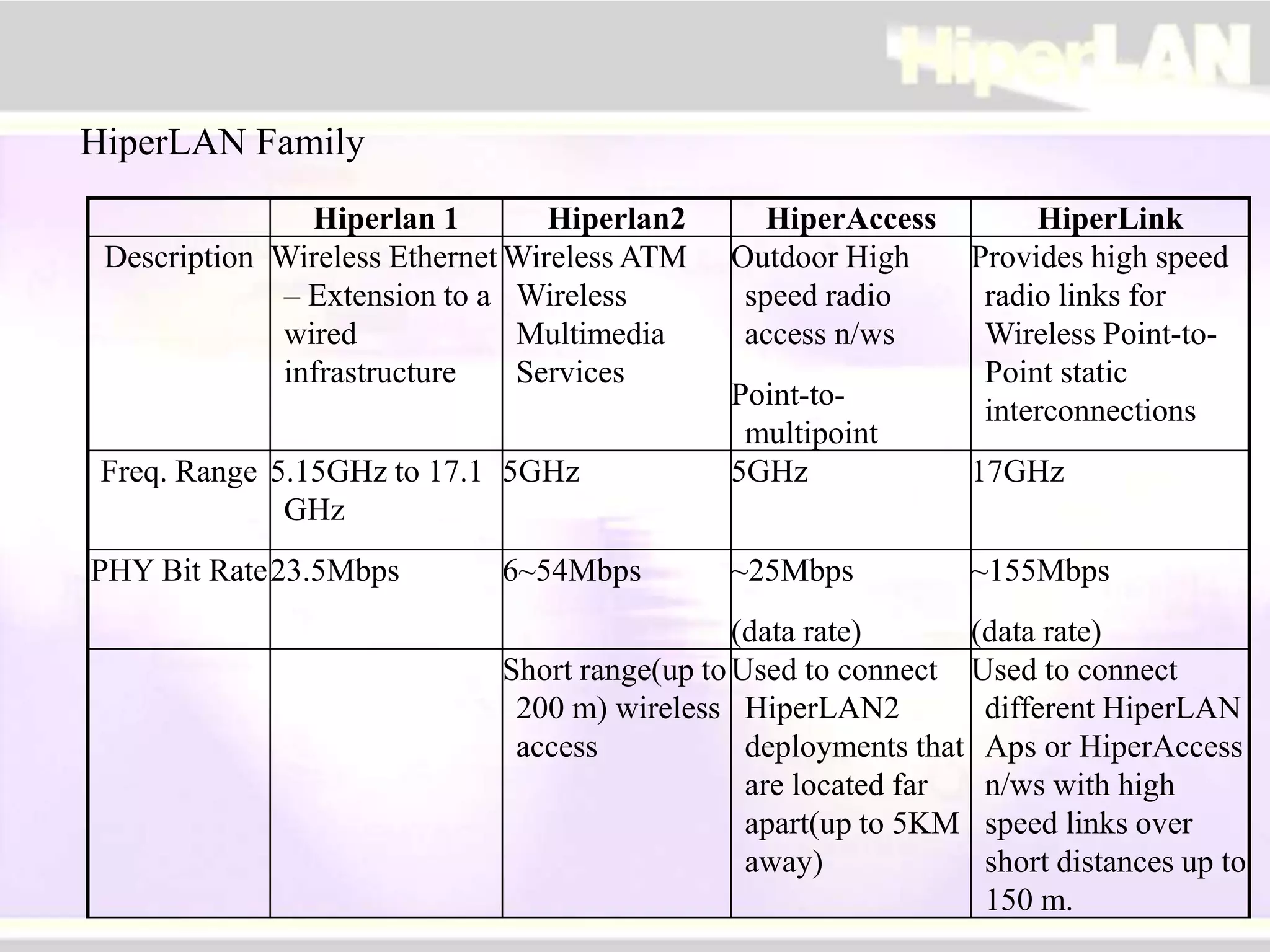
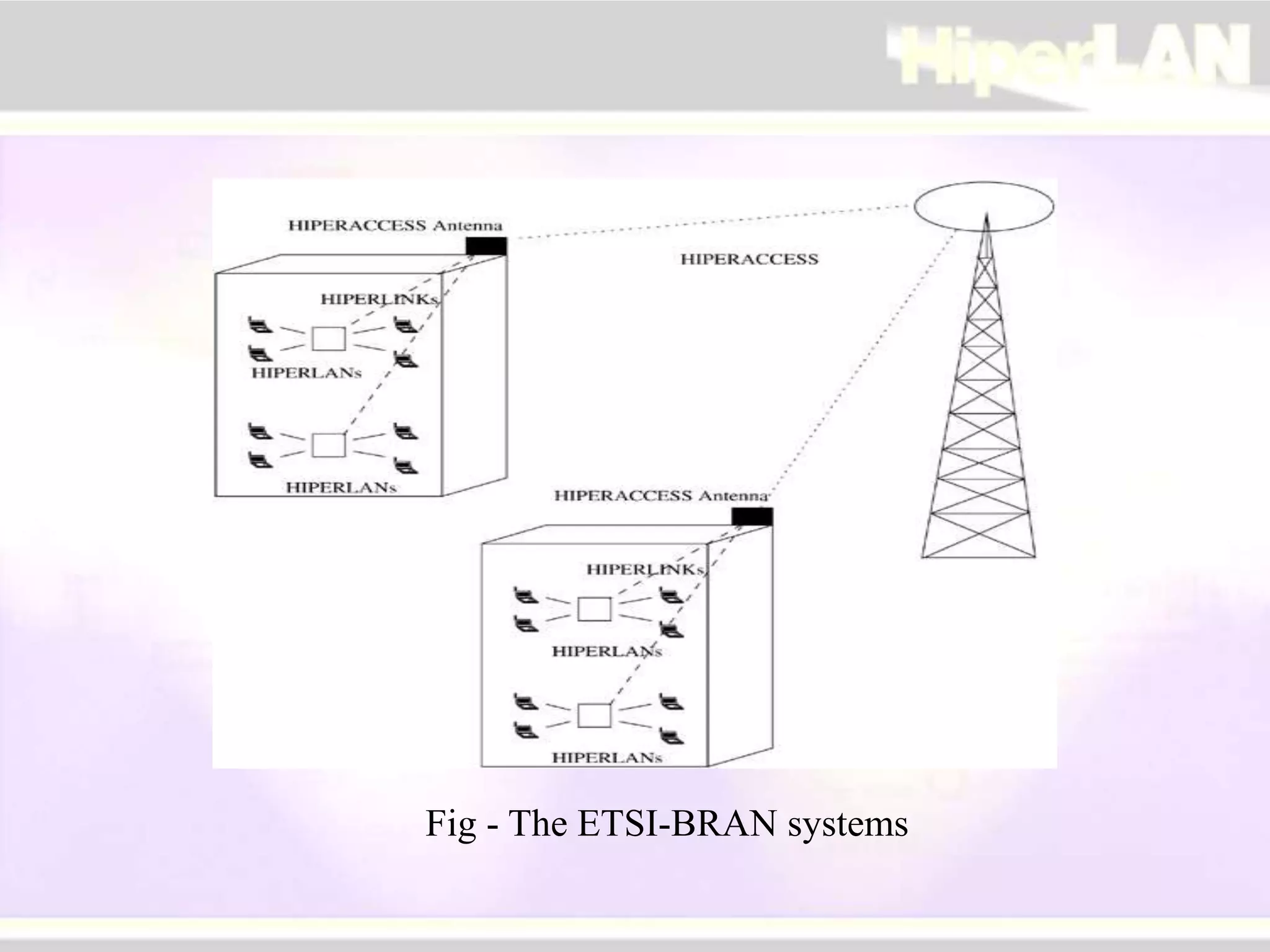
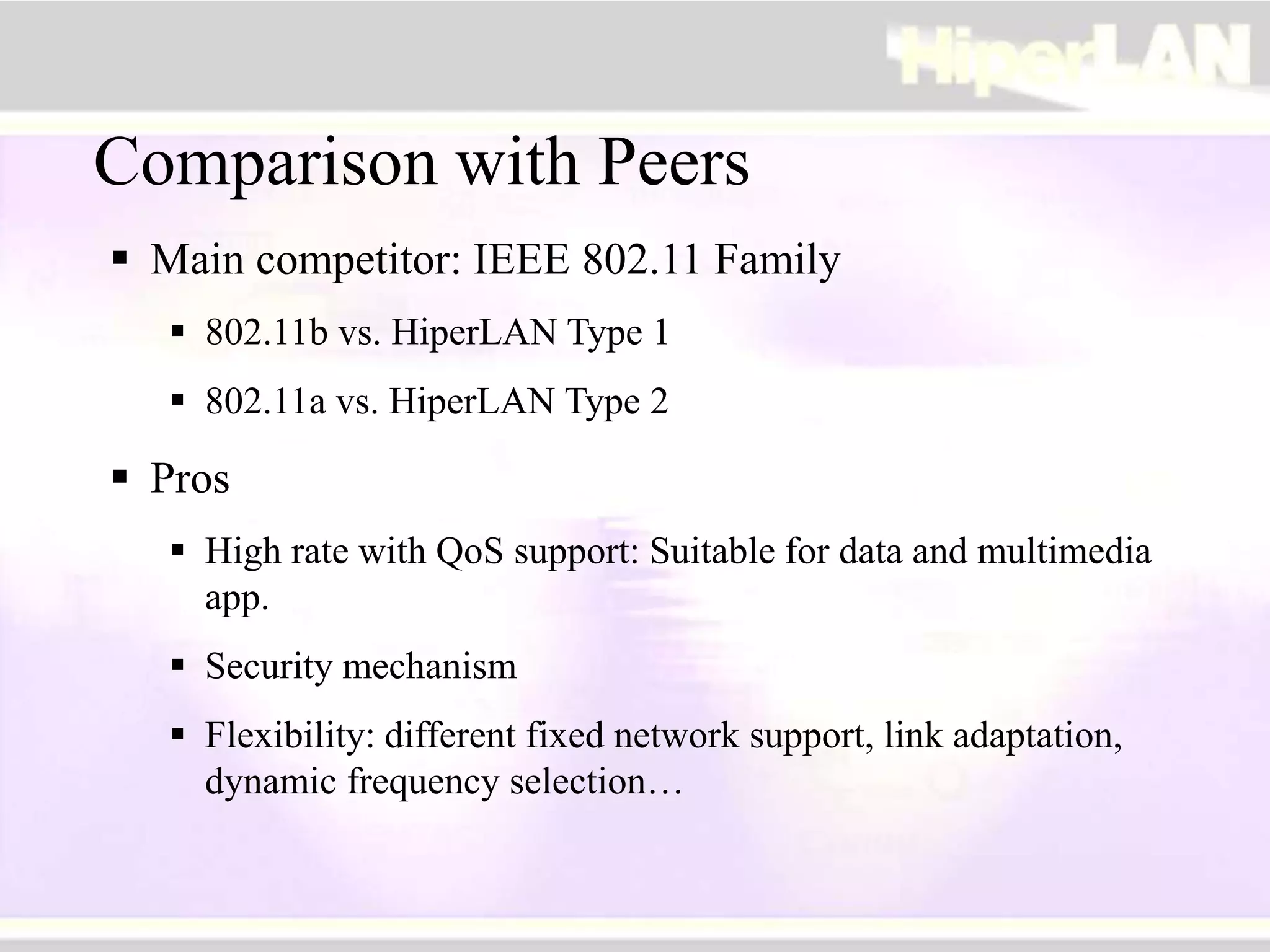
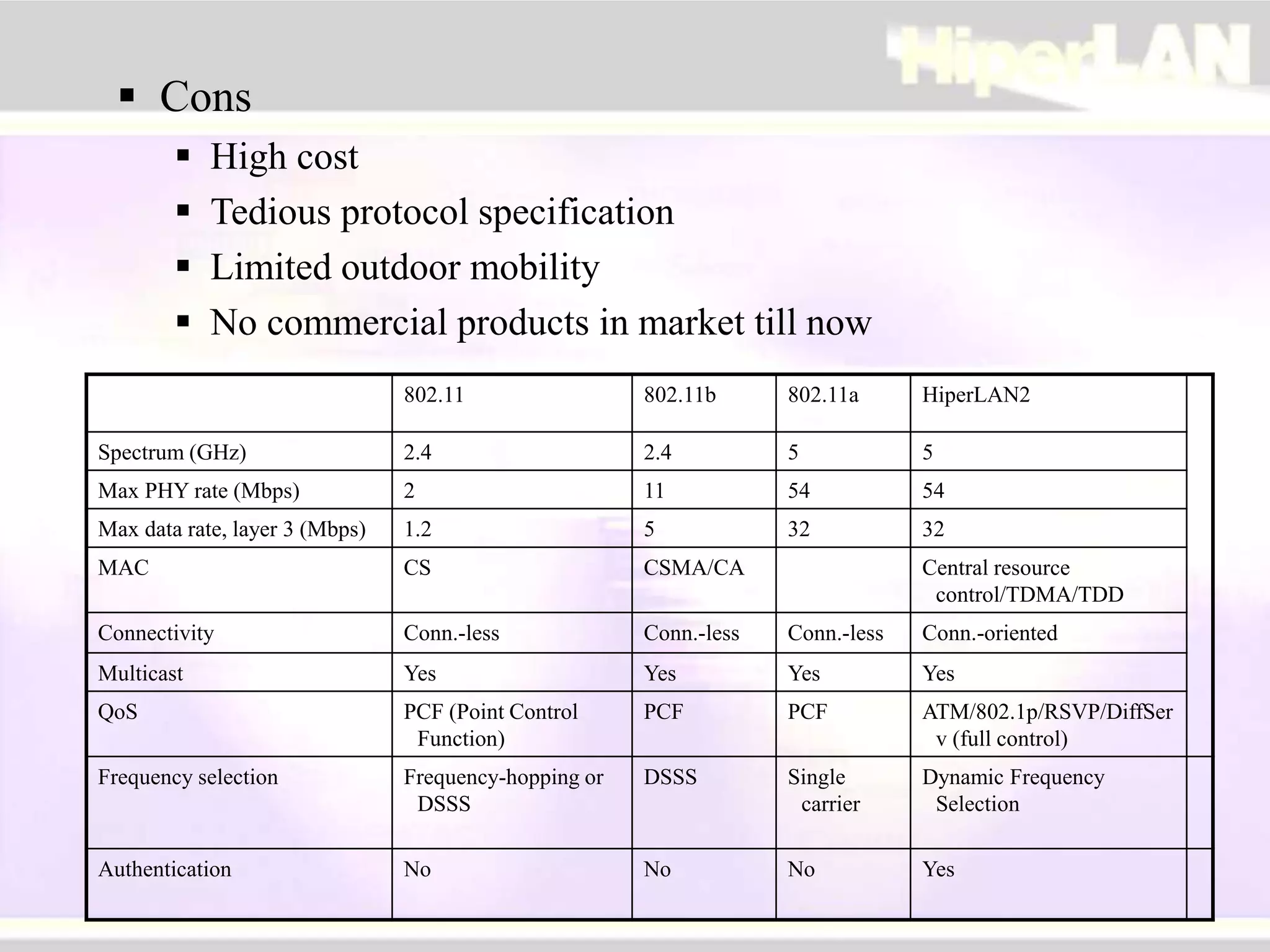
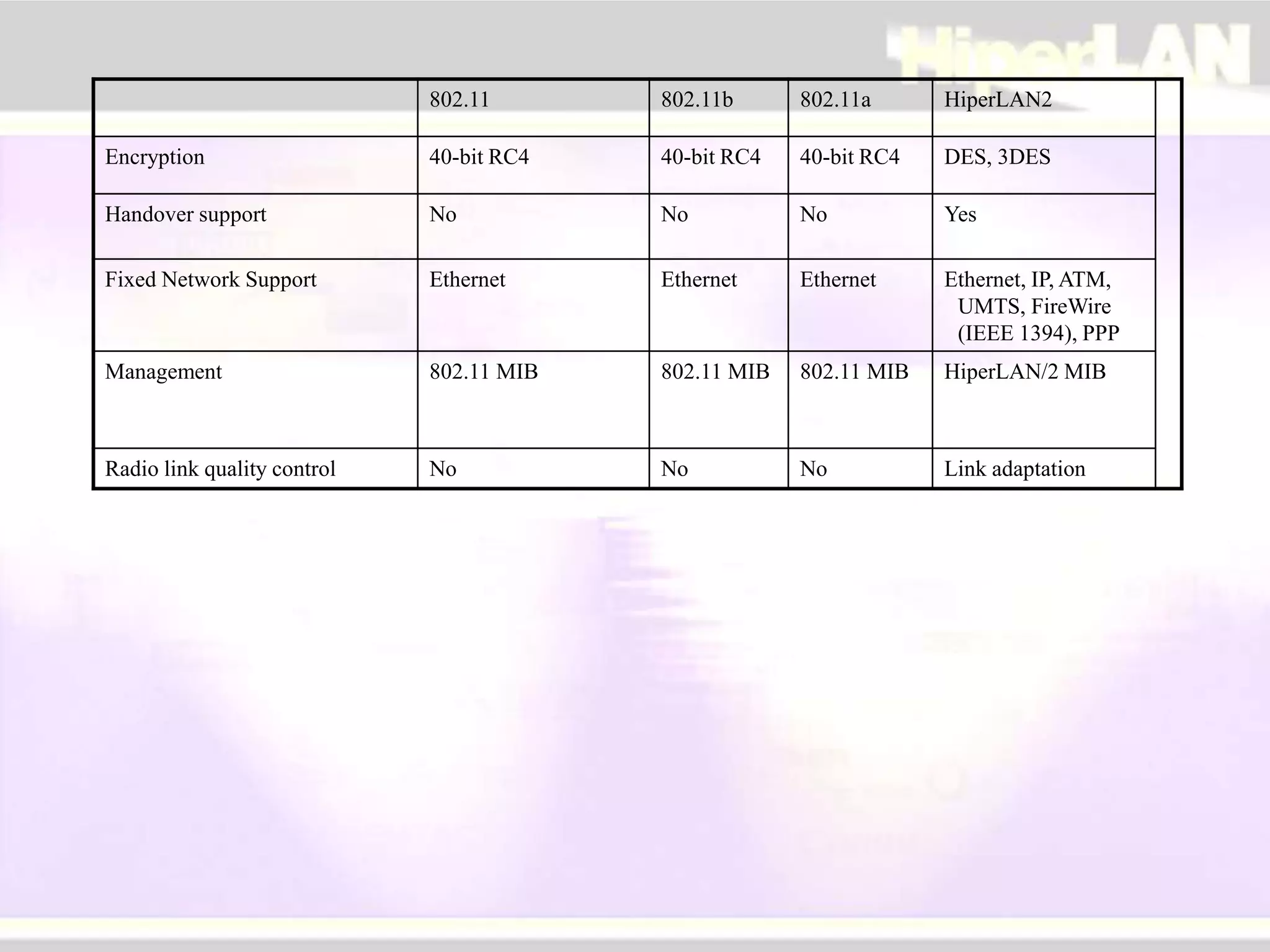
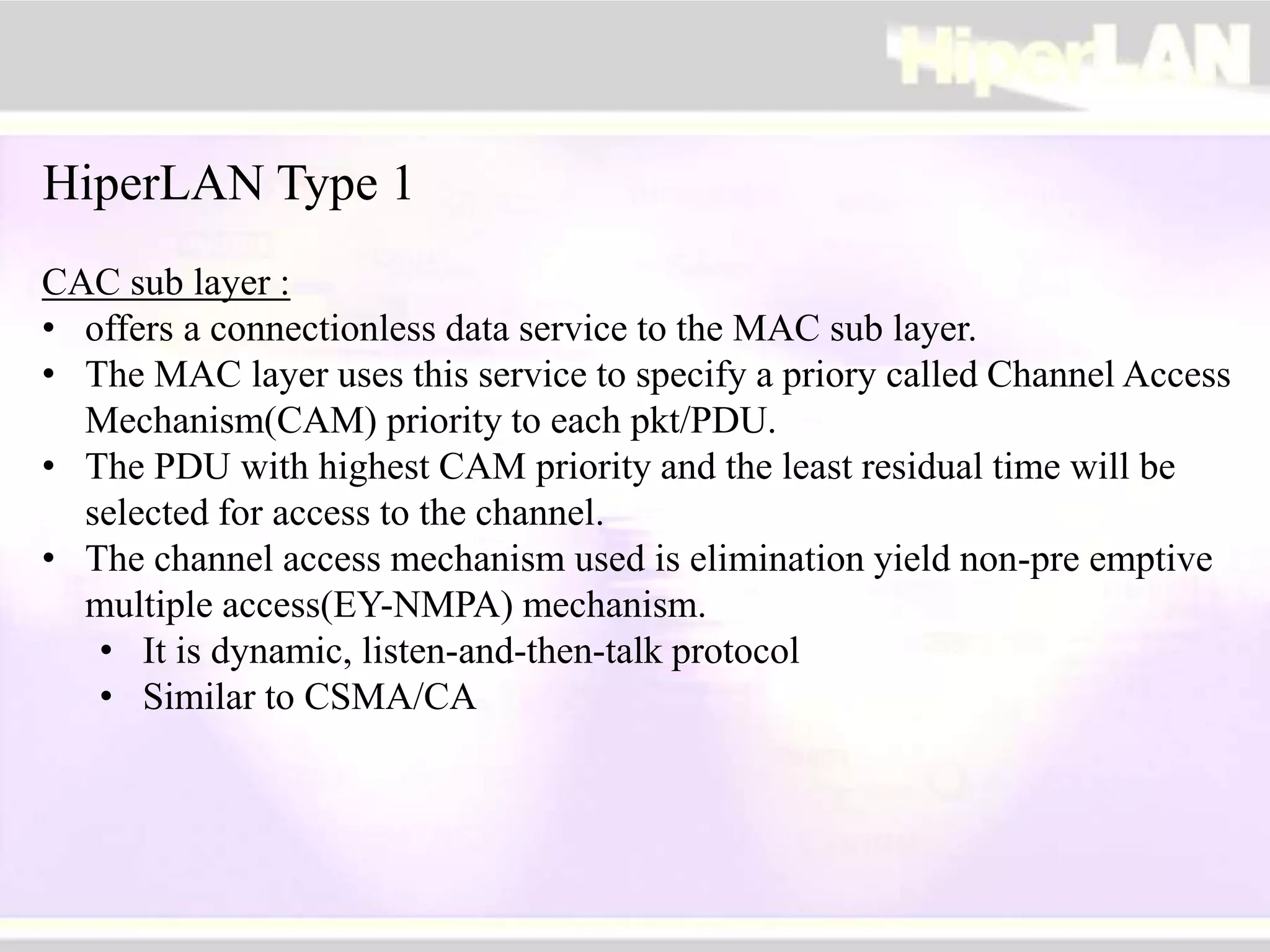
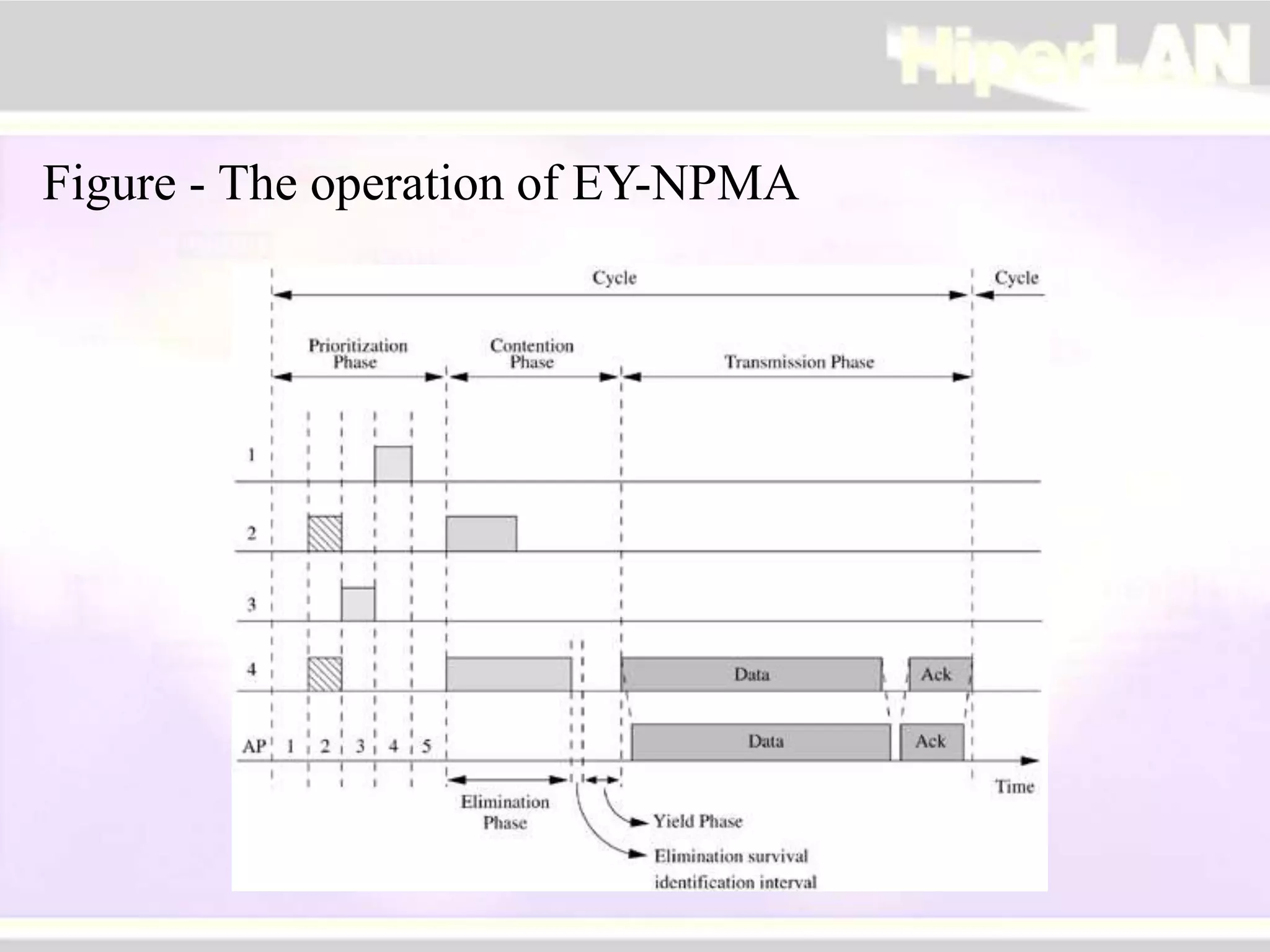
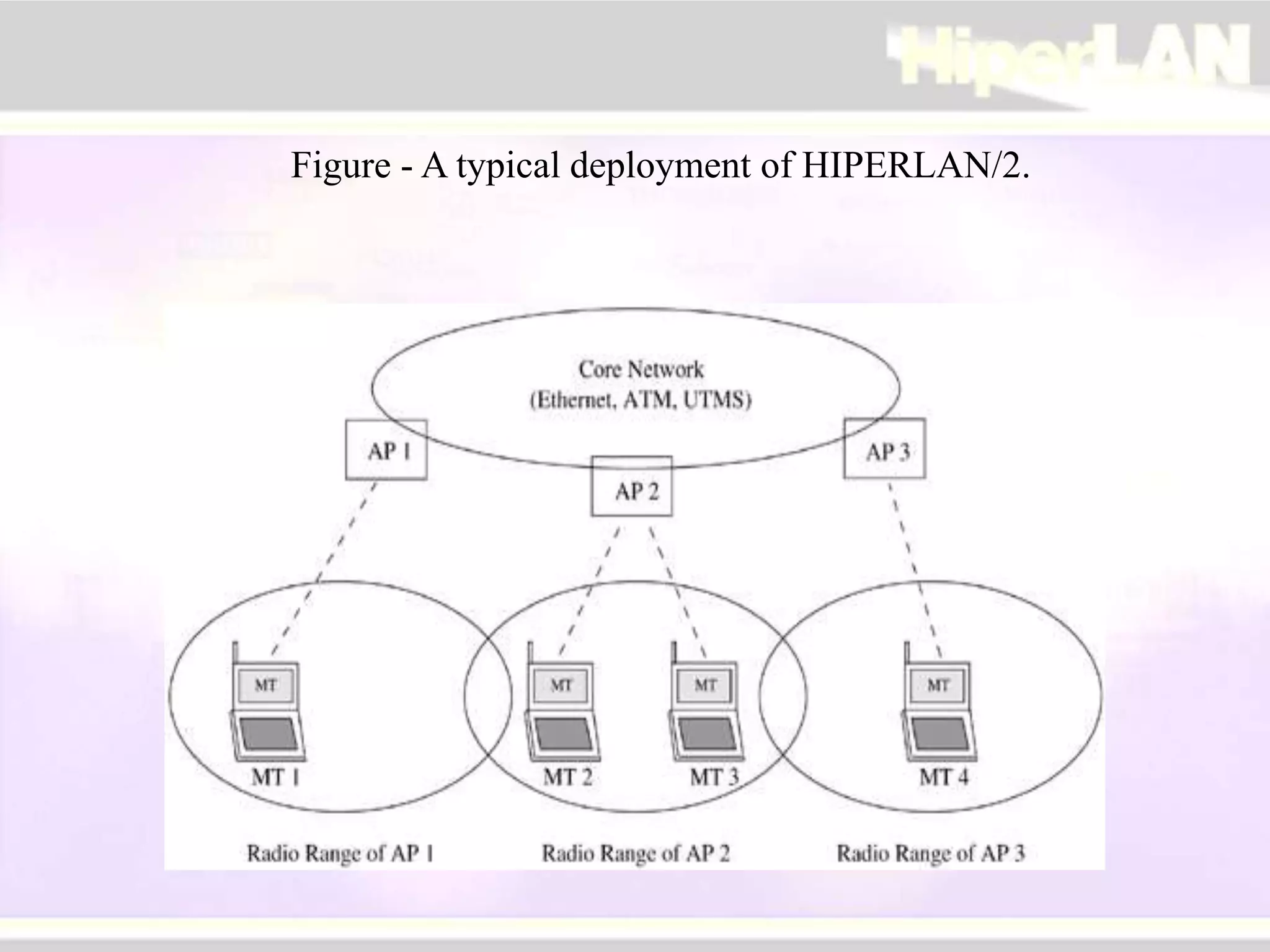
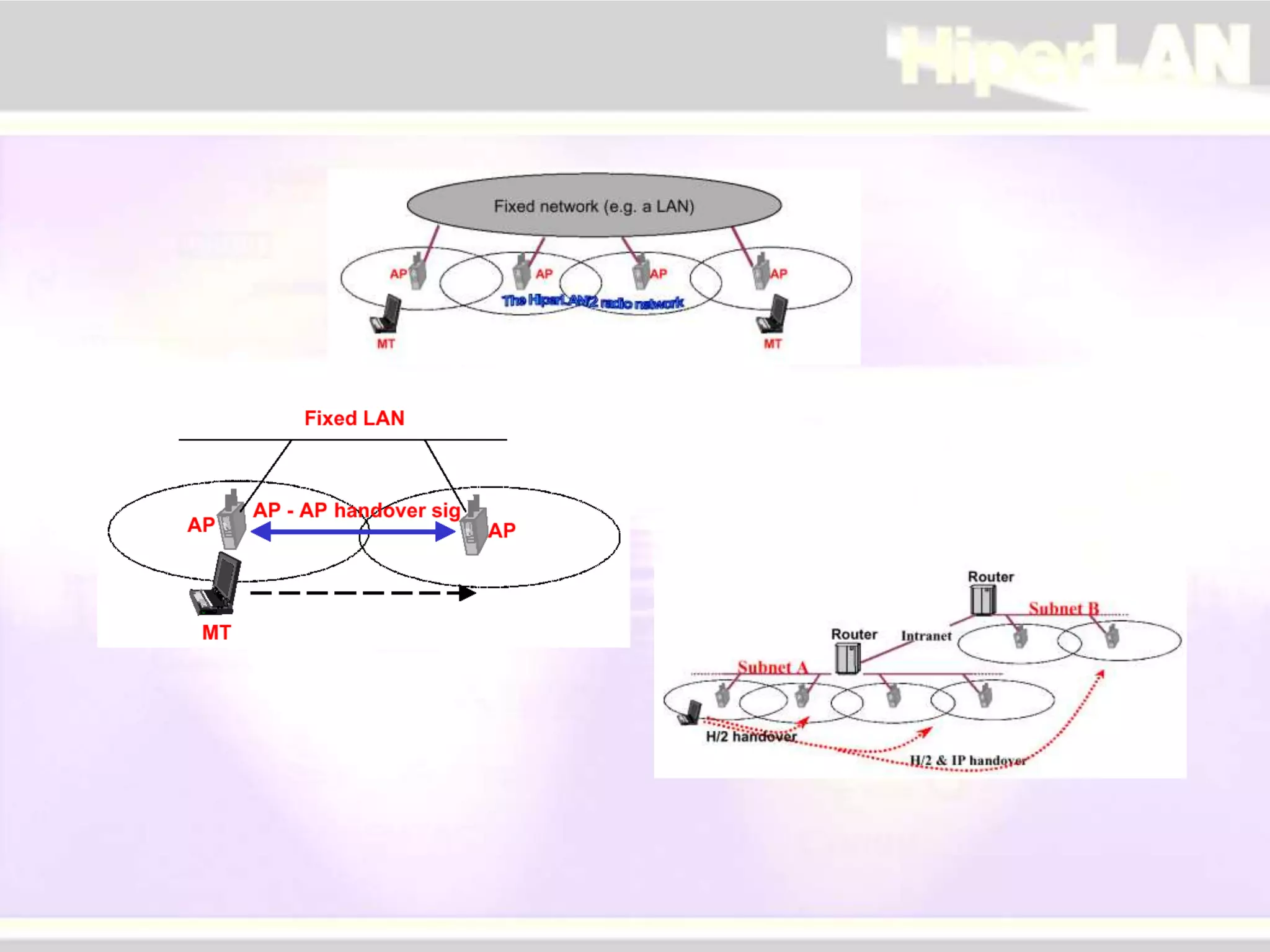
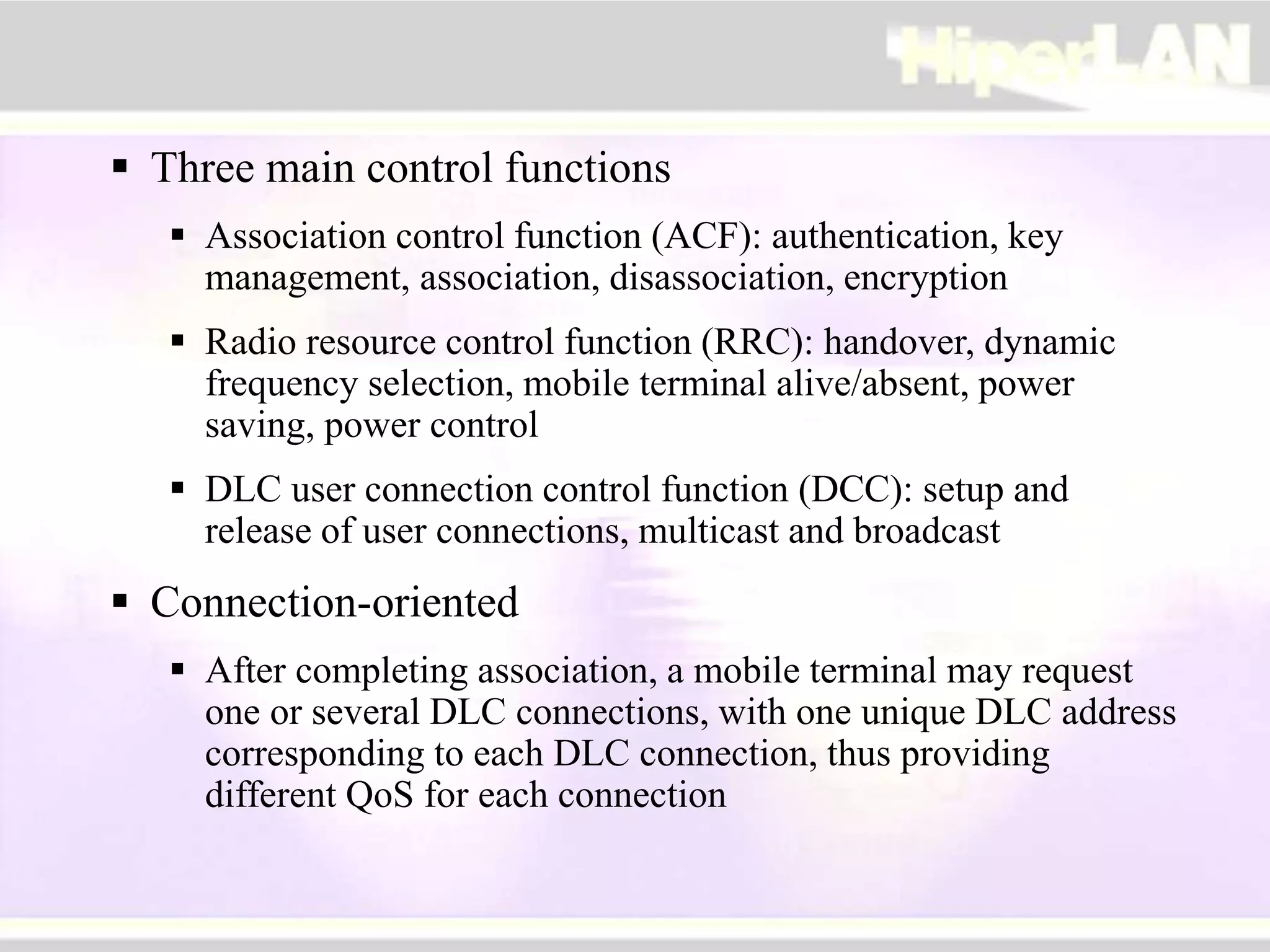
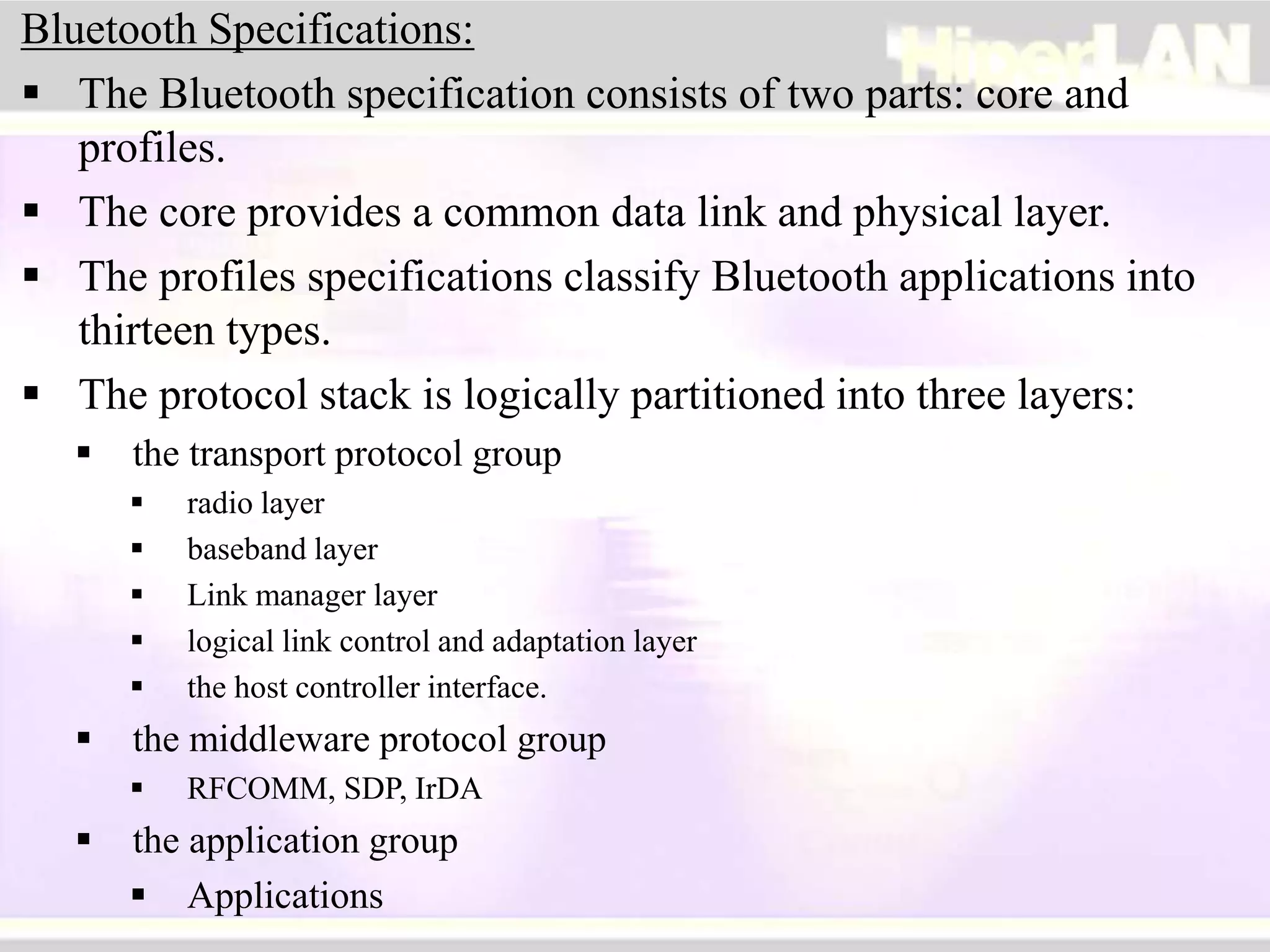
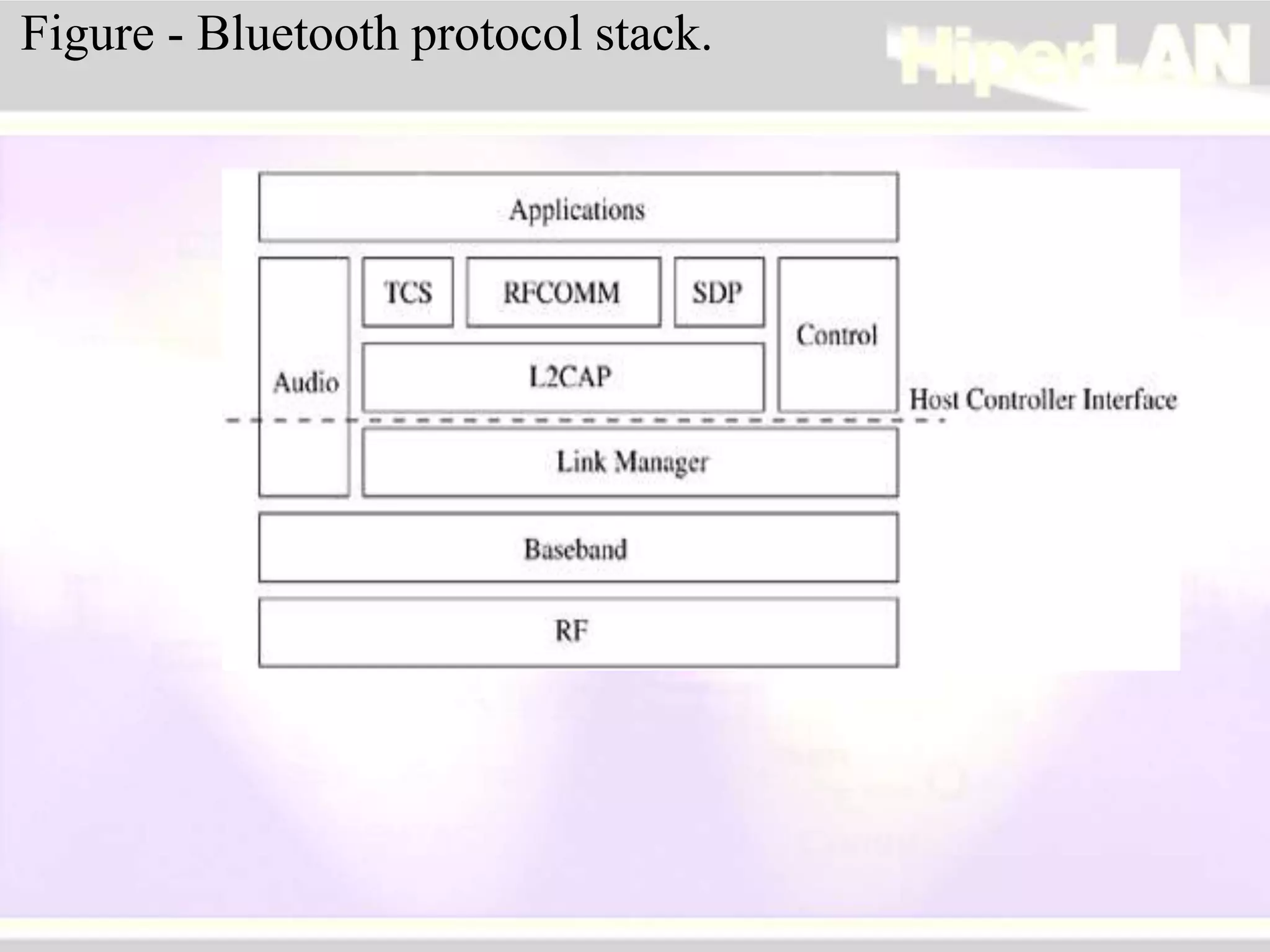
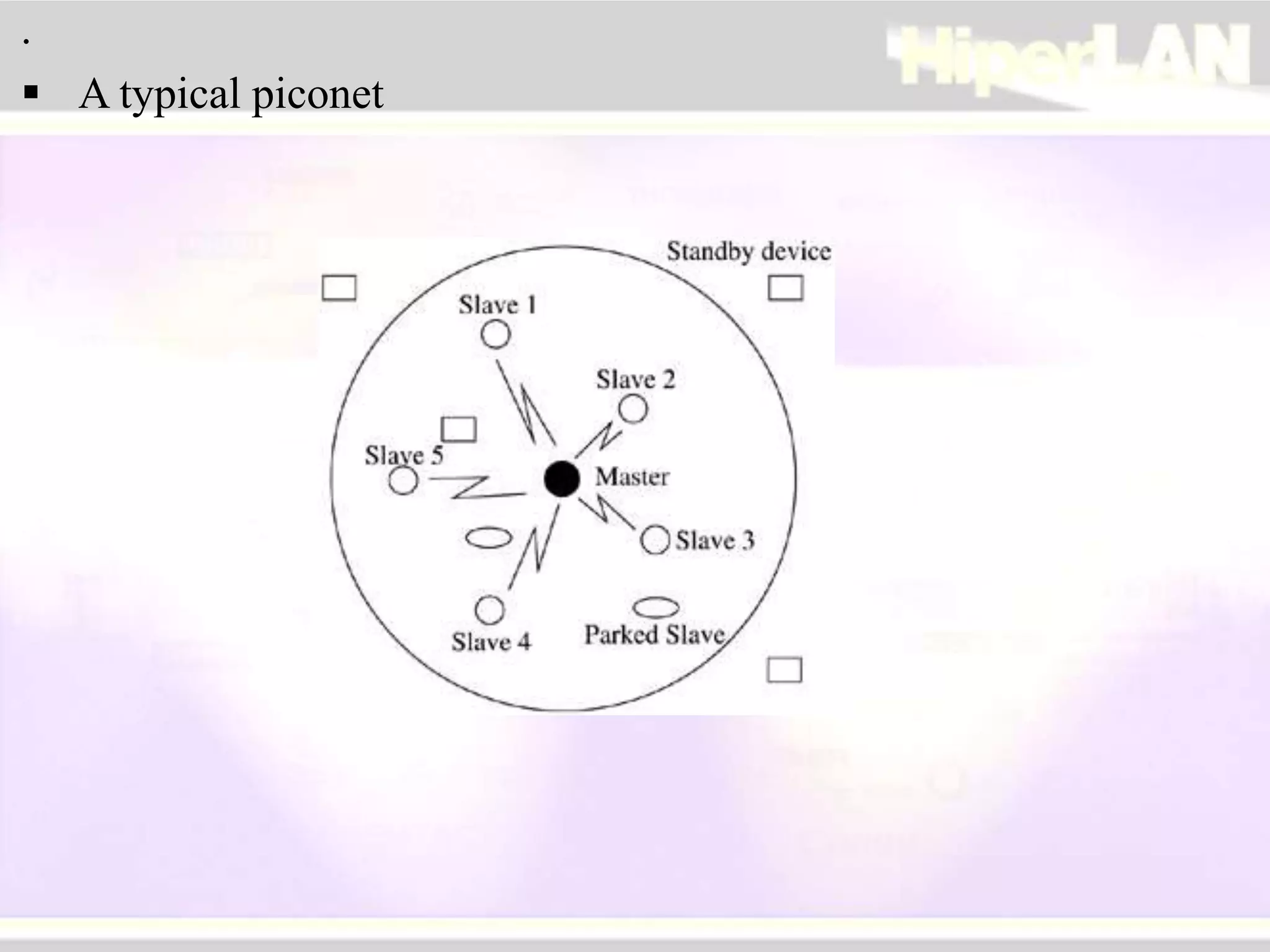
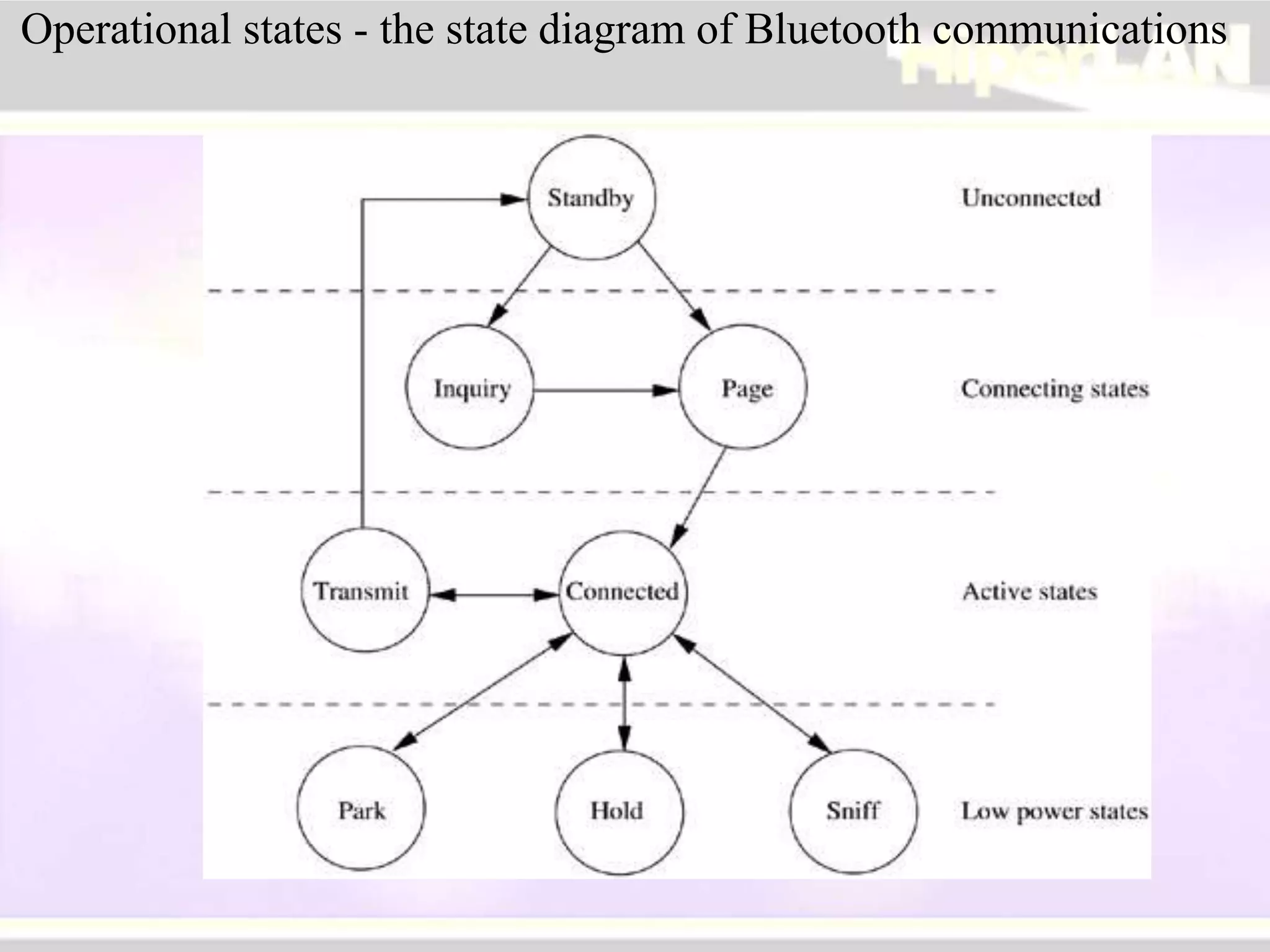
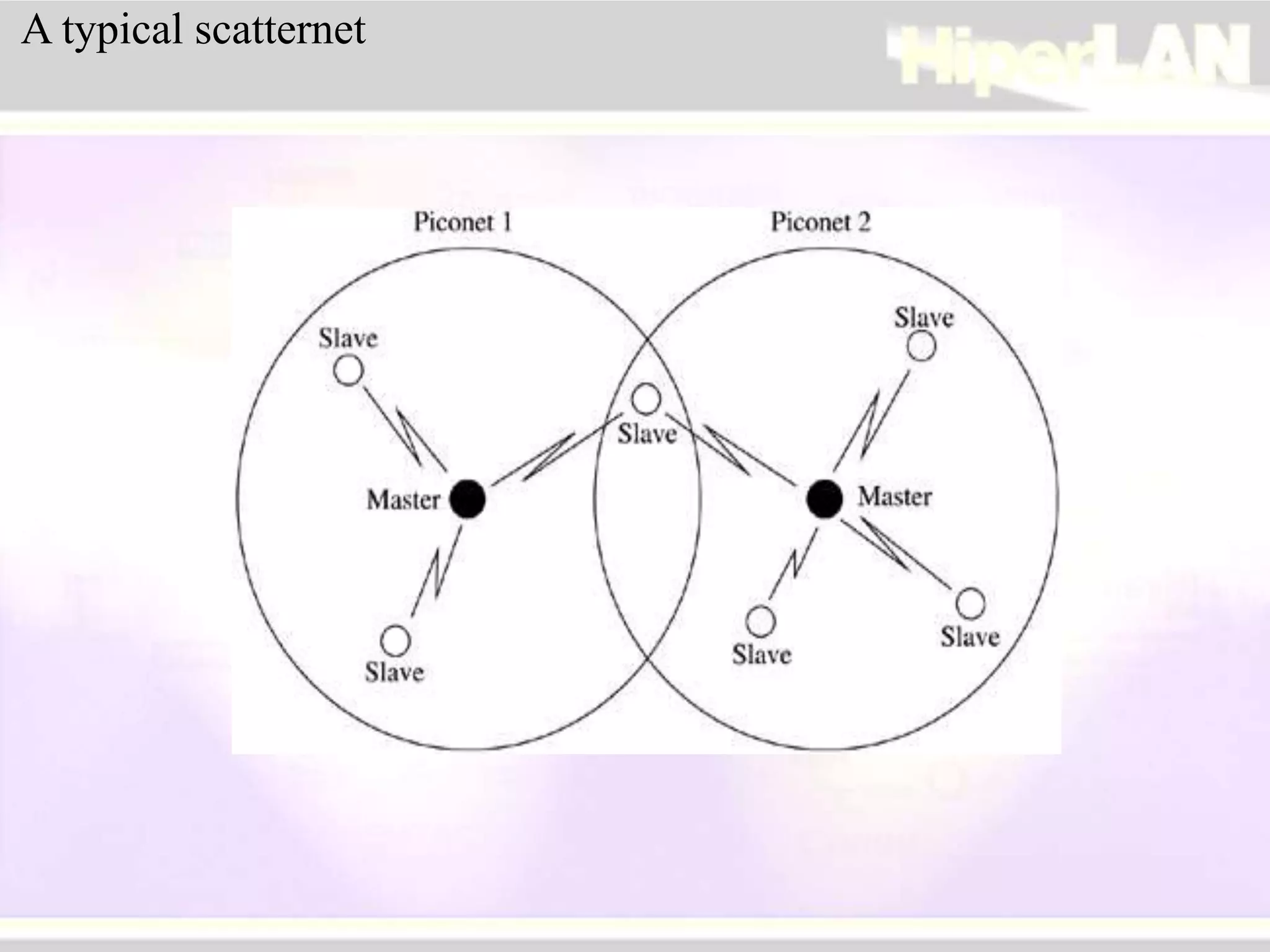
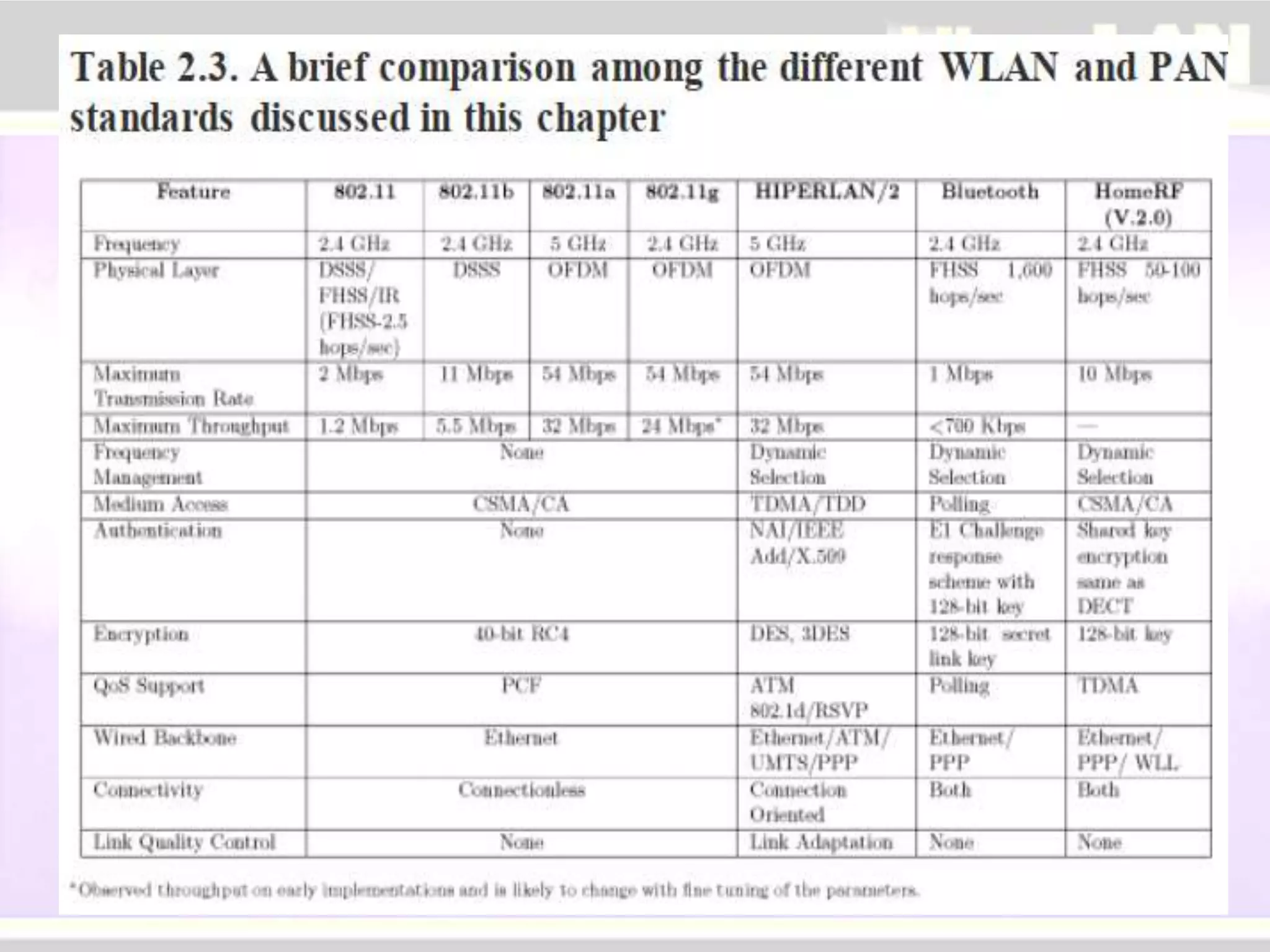
The document provides an overview of HIPERLAN, a wireless local area network standard developed by ETSI. It describes the two types of HIPERLAN (Type 1 and Type 2), their key features and differences. These include operating frequencies, data rates, supported network types, quality of service capabilities, and security features. The document also compares HIPERLAN to other wireless network standards like IEEE 802.11 and discusses use cases and applications.