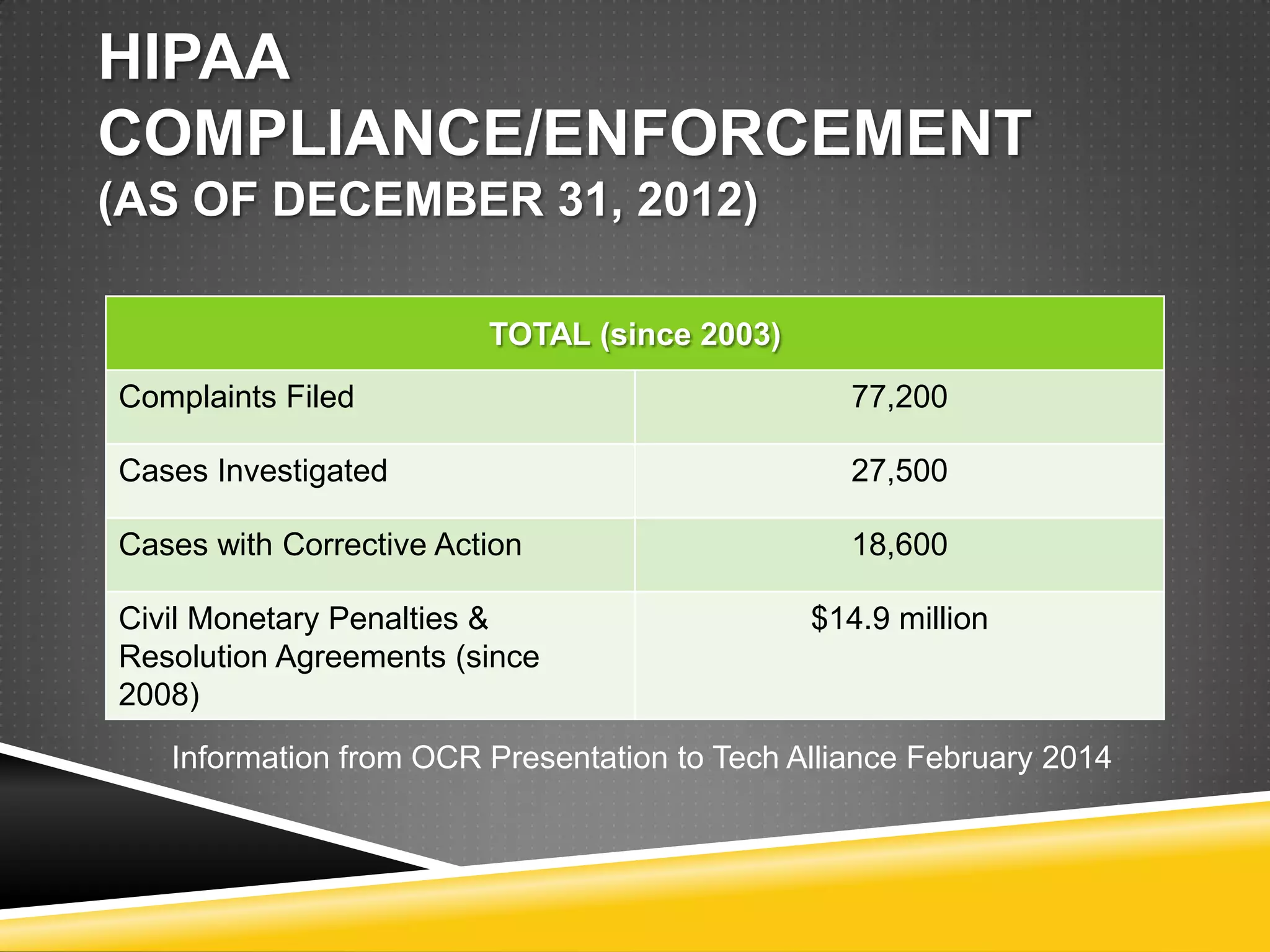
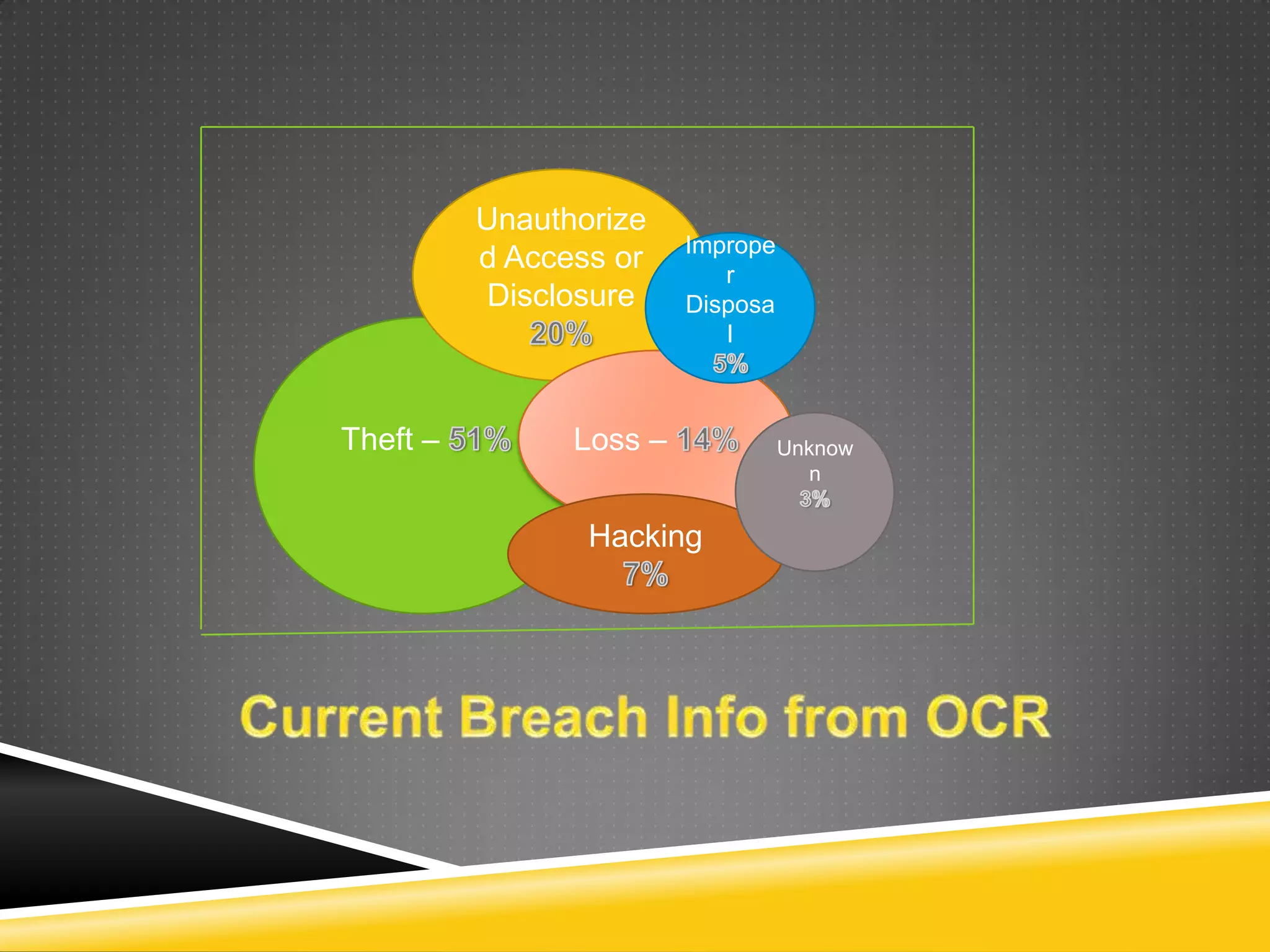
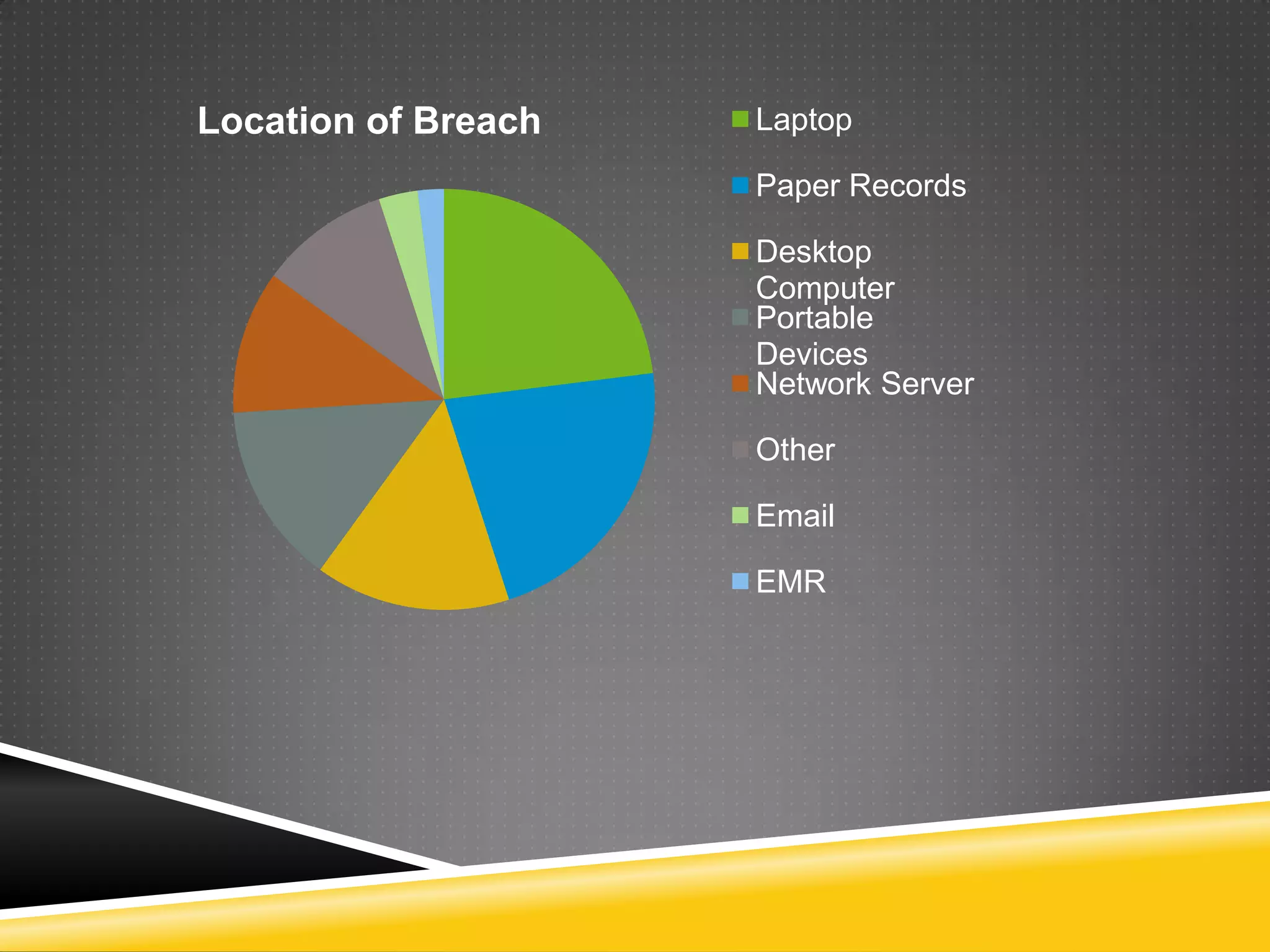
This document provides information on how to implement HIPAA compliance. It begins by explaining what HIPAA is and who it impacts, such as health care providers, health plans, and clearinghouses. It defines protected health information and the obligations of covered entities and business associates. It emphasizes the importance of having business associate agreements, security policies, training programs, and conducting audits. It provides tips for securing data transmission, backups, access controls, and shredding paper records. The document stresses that HIPAA compliance is essential to avoid penalties for violations and data breaches.