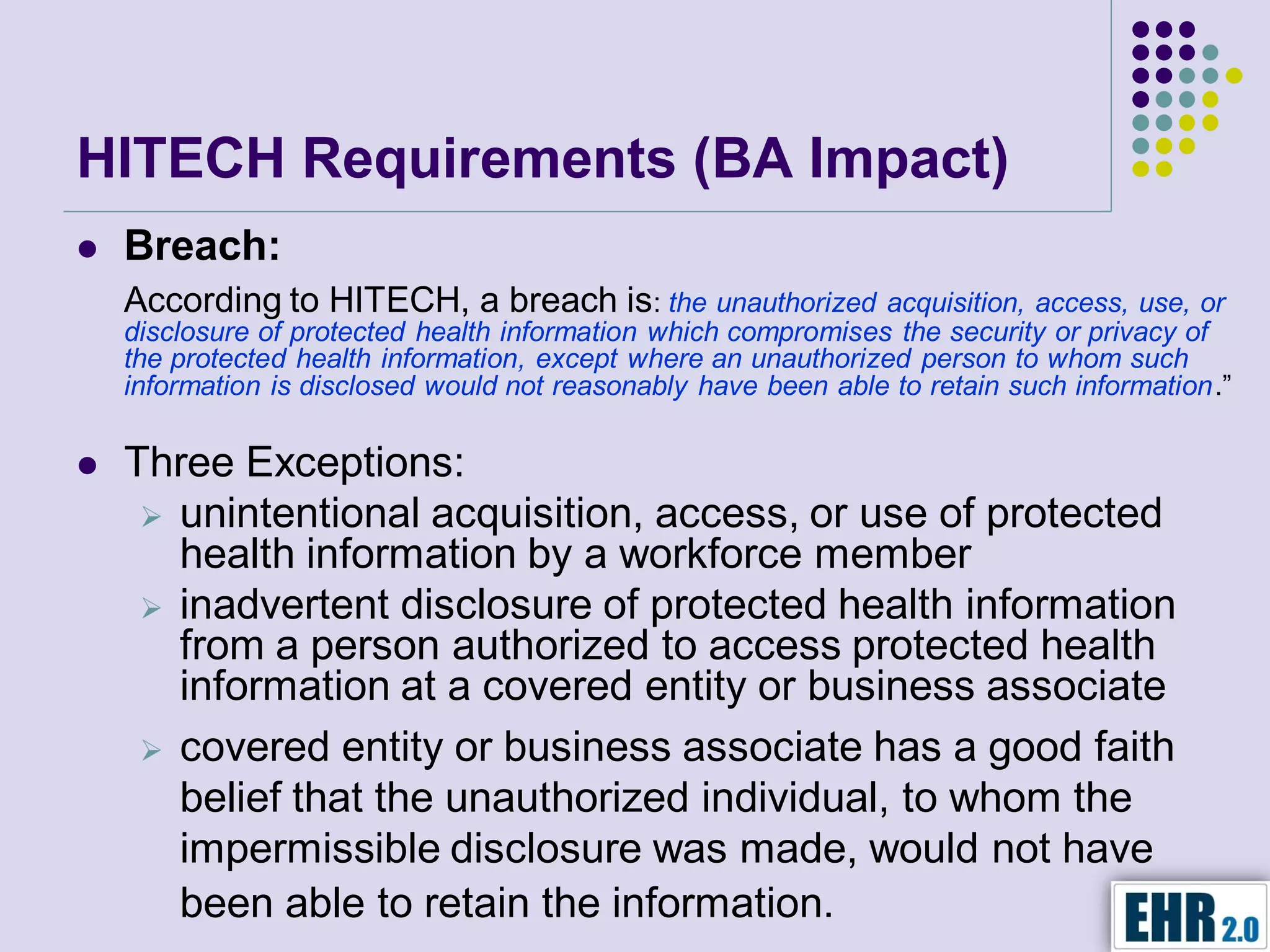
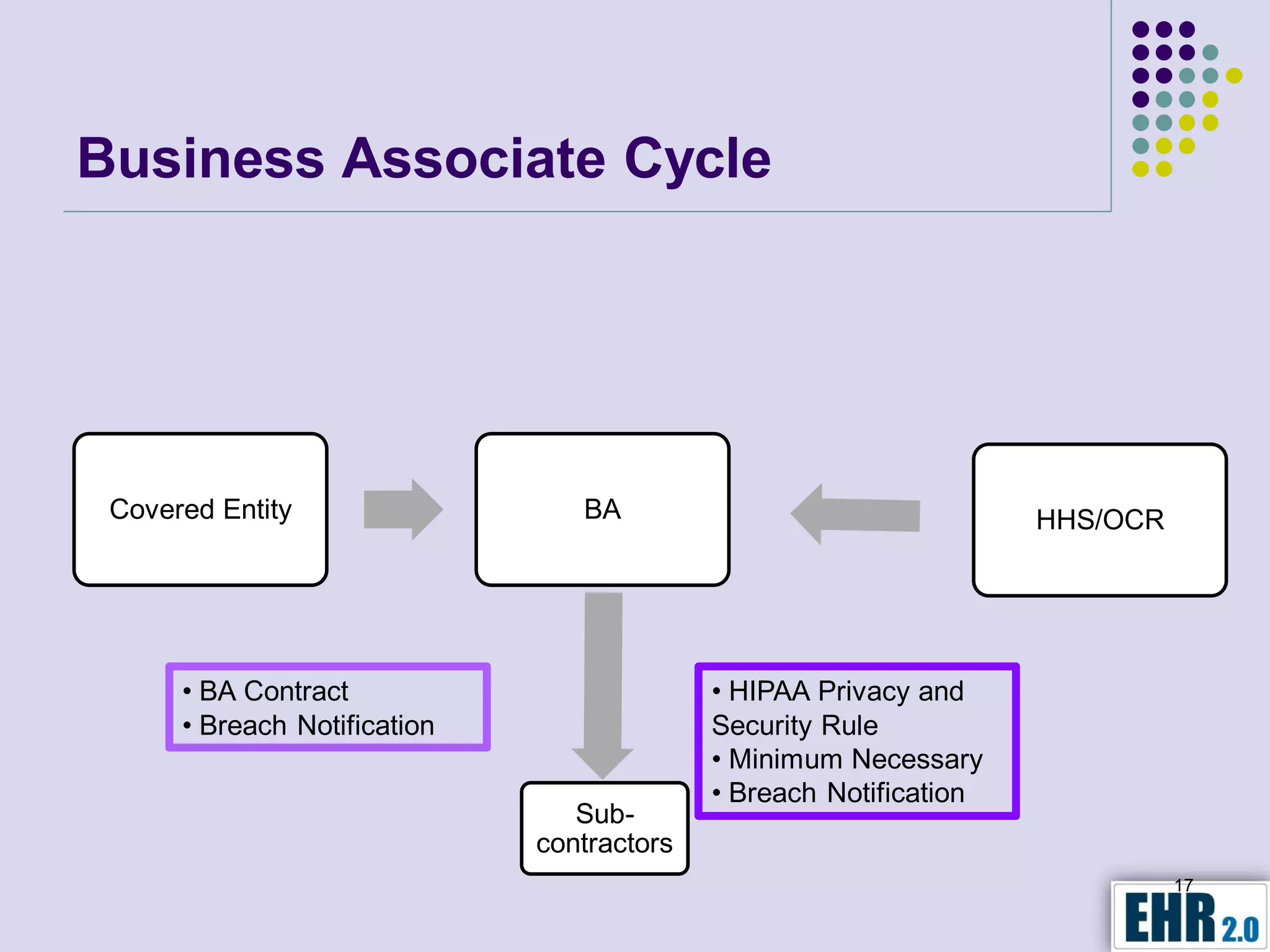
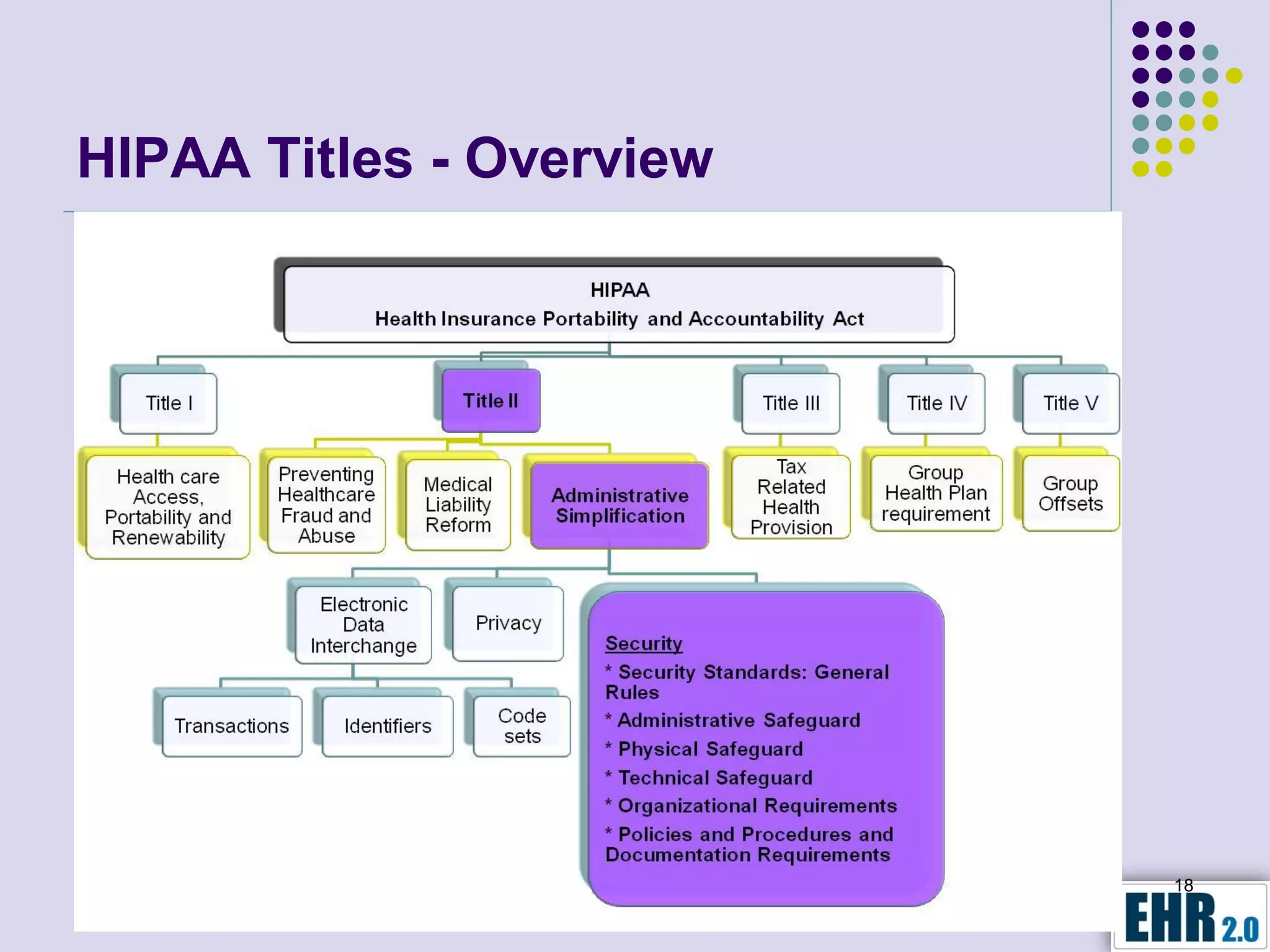
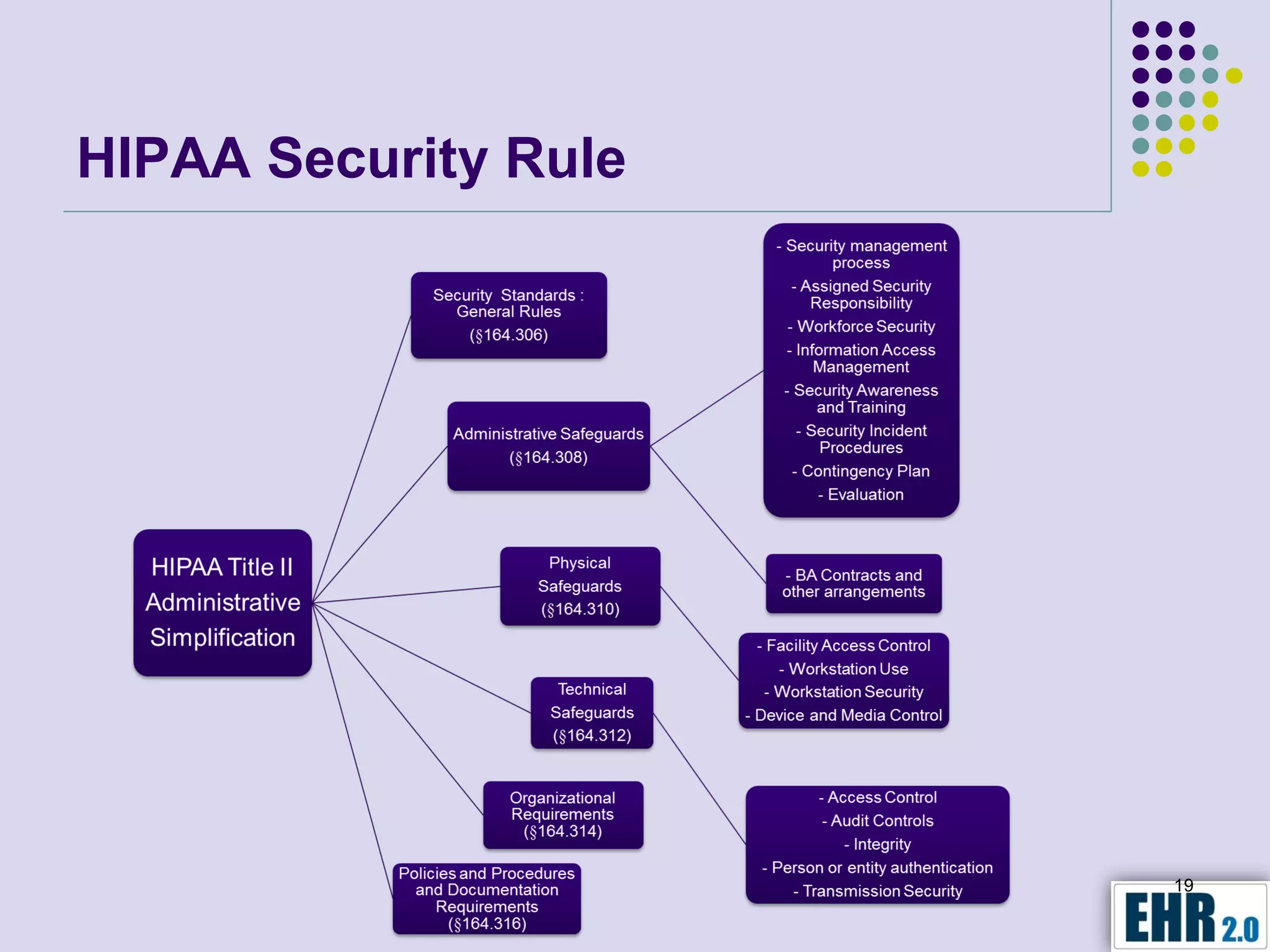
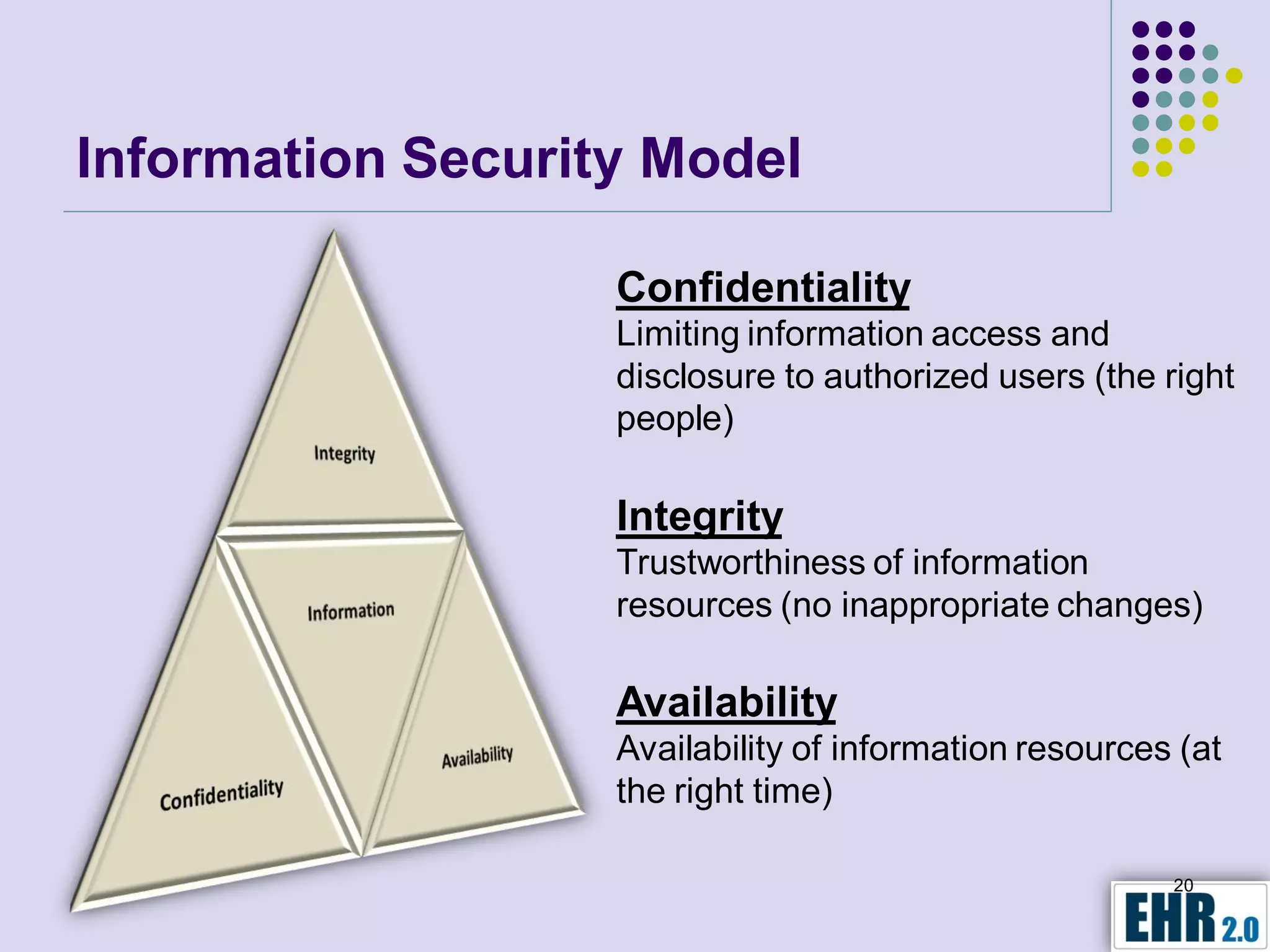
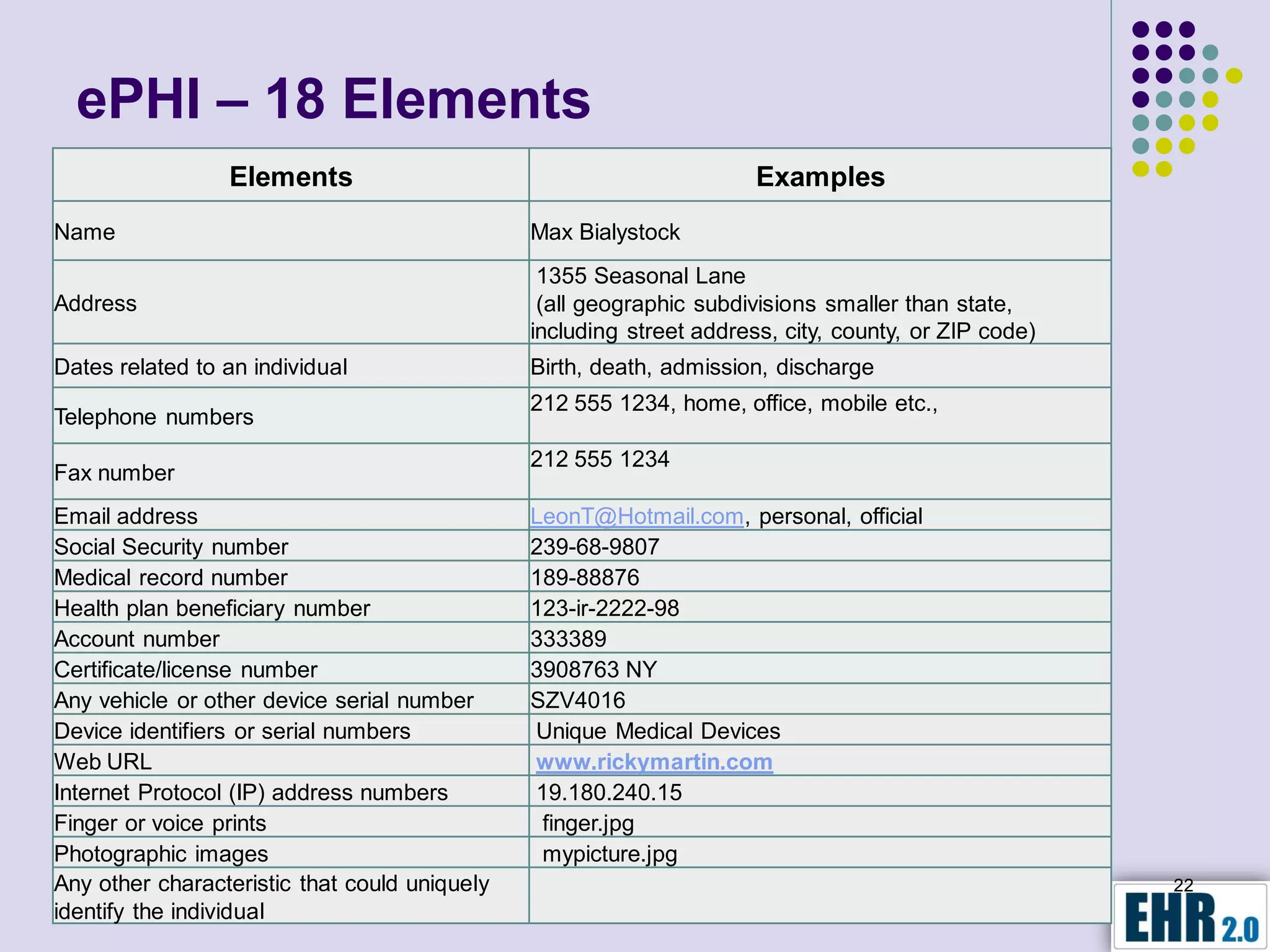
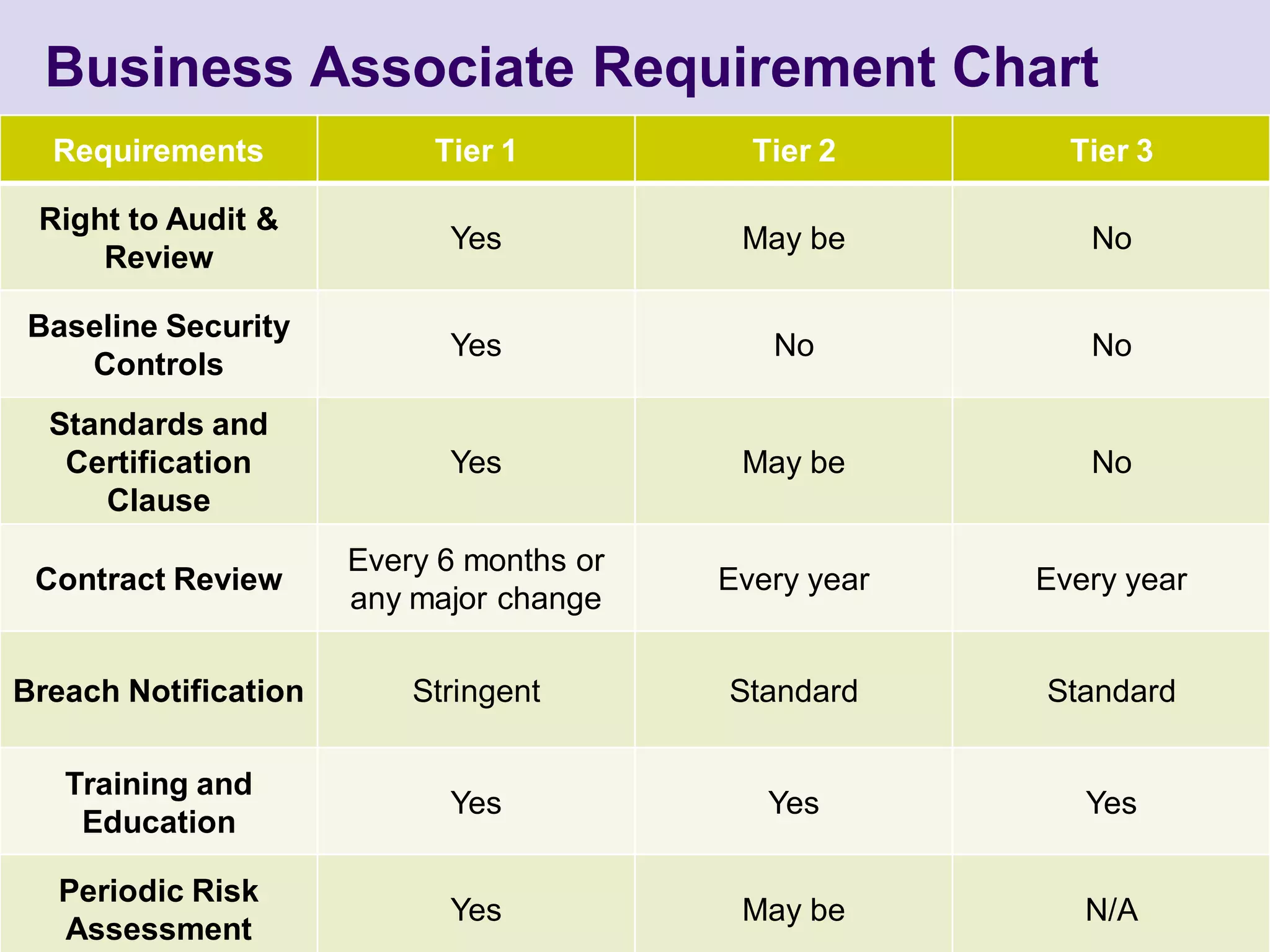
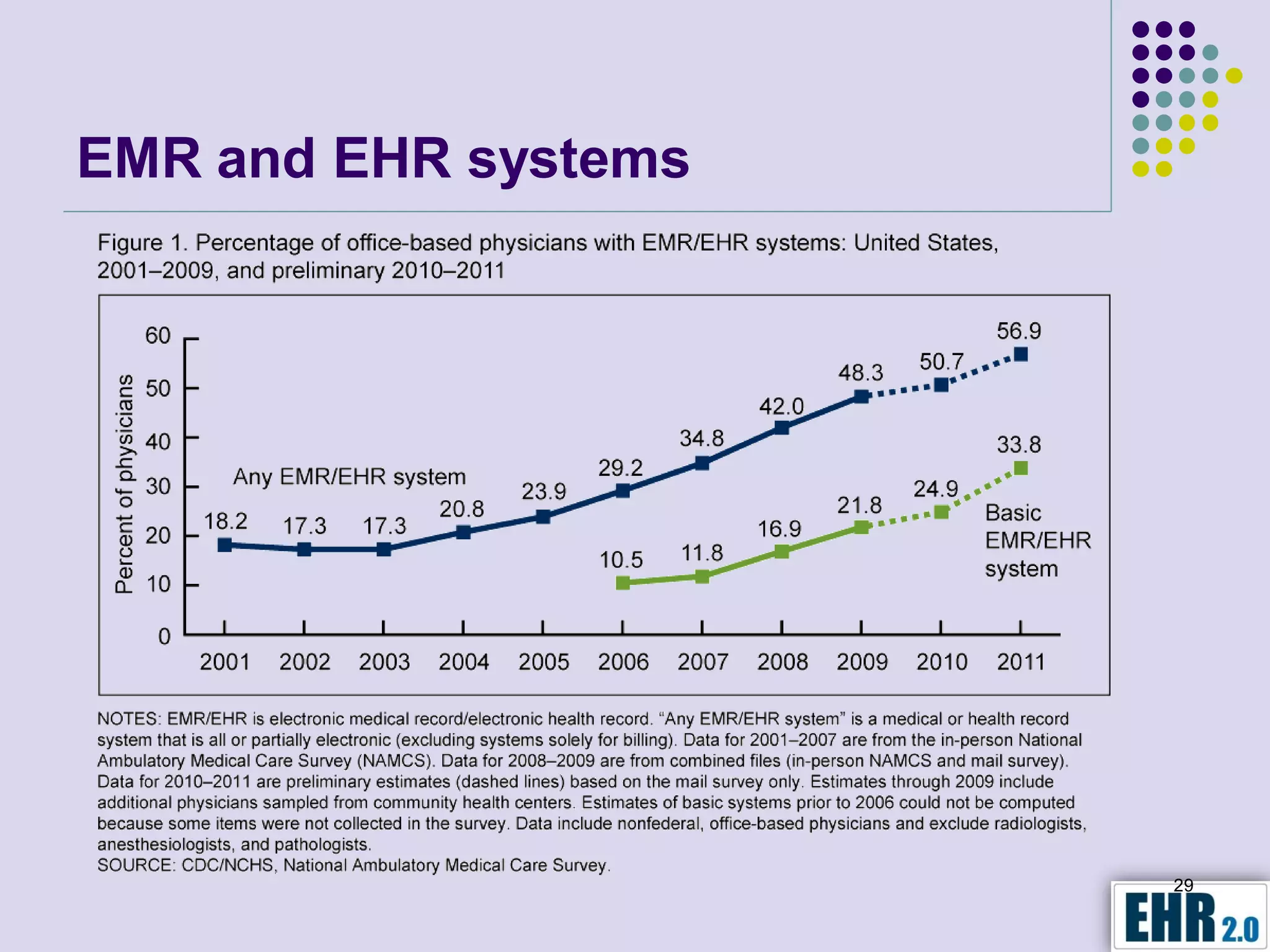
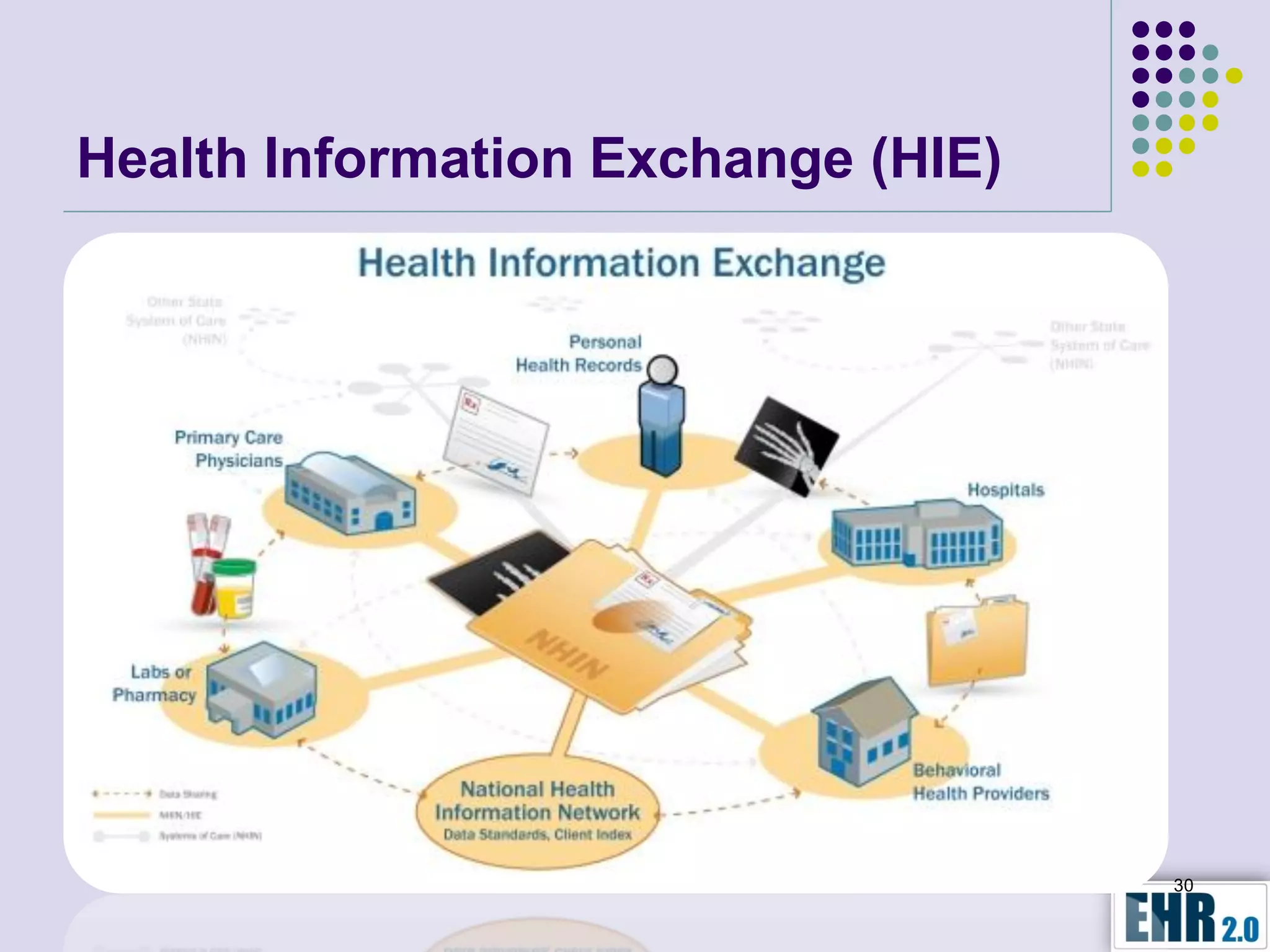
Blair Jerome, PhD, leverages over twenty years of experience in public and private education to assist healthcare organizations in achieving HIPAA and HITECH compliance through education and consulting. The document outlines the responsibilities of business associates, including new privacy requirements and penalties instituted by the HITECH Act, which enforces stricter guidelines for handling protected health information. Key recommendations include implementing encryption, mobile security programs, and periodic reviews of business associate agreements to mitigate risks.