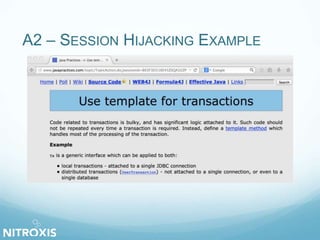
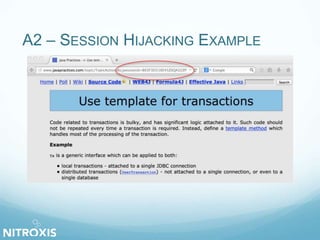
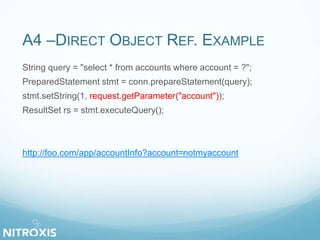
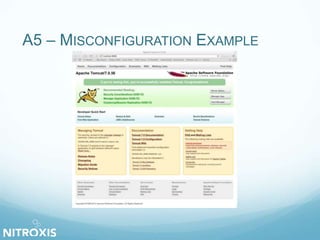
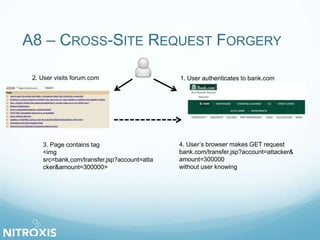
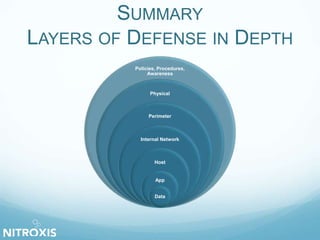
The document outlines a seminar on web application security, addressed by Olivier Houyoux from Nitroxis, emphasizing the importance of securing web applications against vulnerabilities. It covers the OWASP Top 10 security flaws, including injection, broken authentication, and cross-site scripting, along with real-life examples and mitigation strategies. The seminar aims to enhance awareness and provide resources for improving security in web applications.