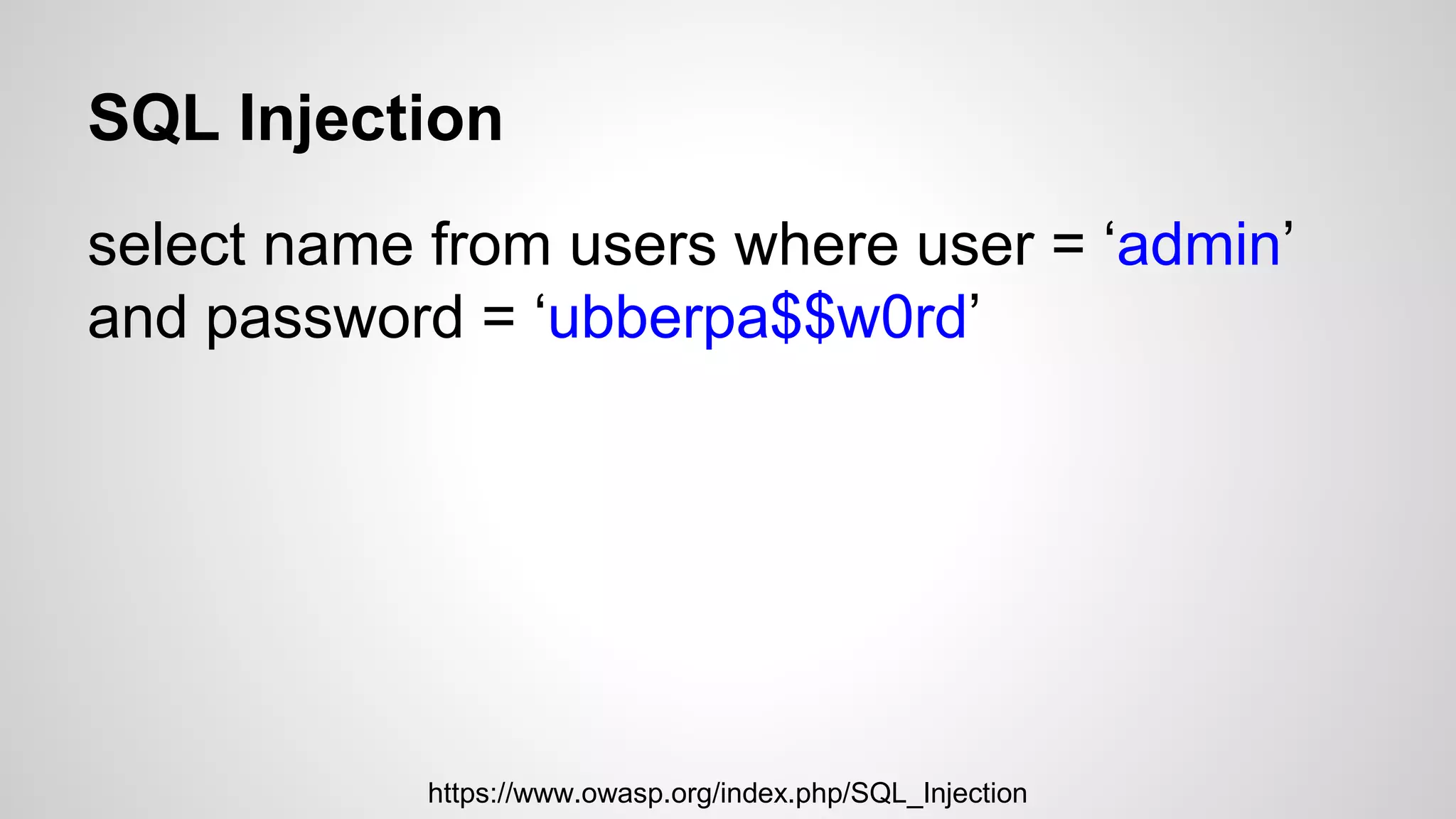
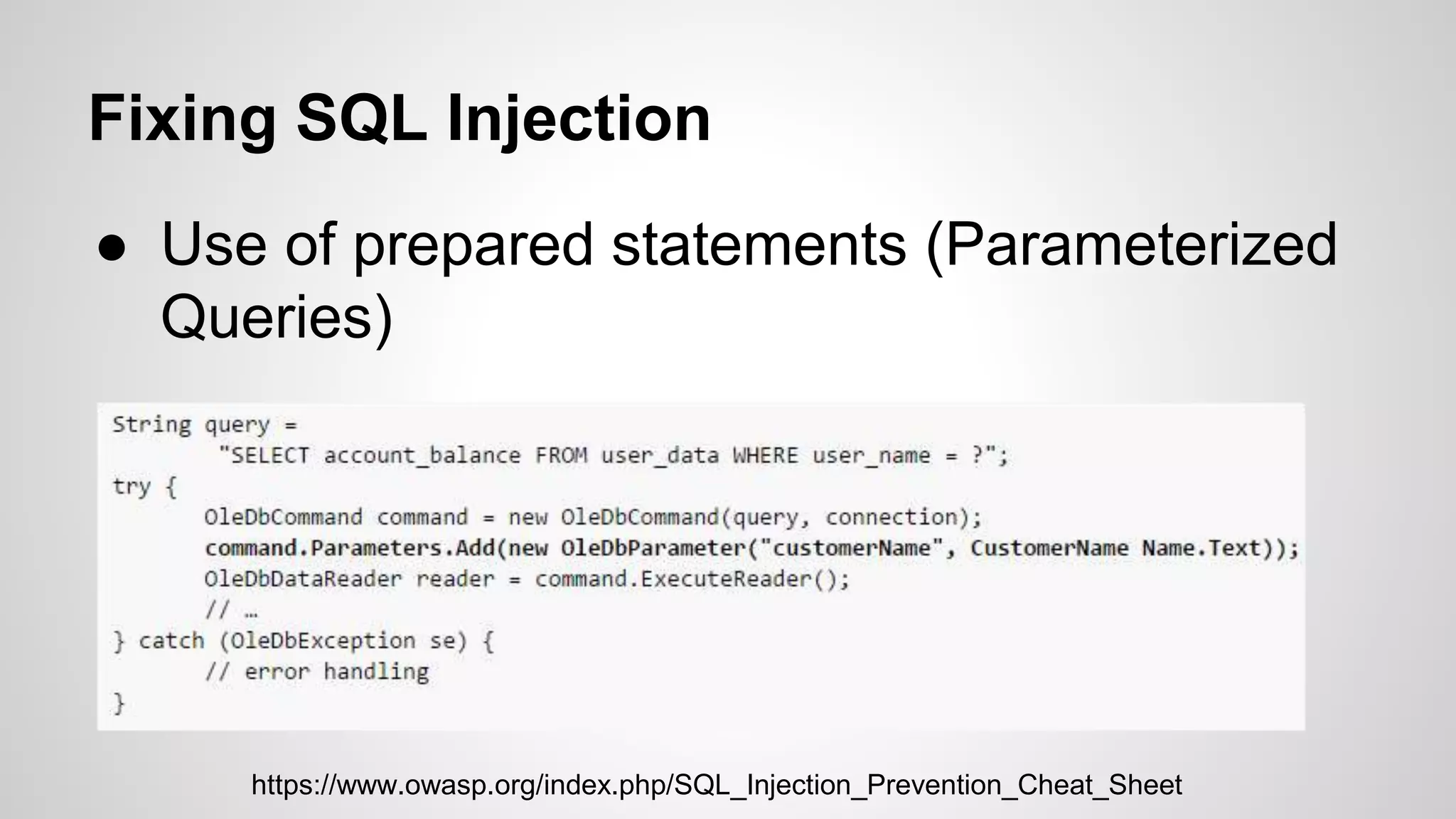
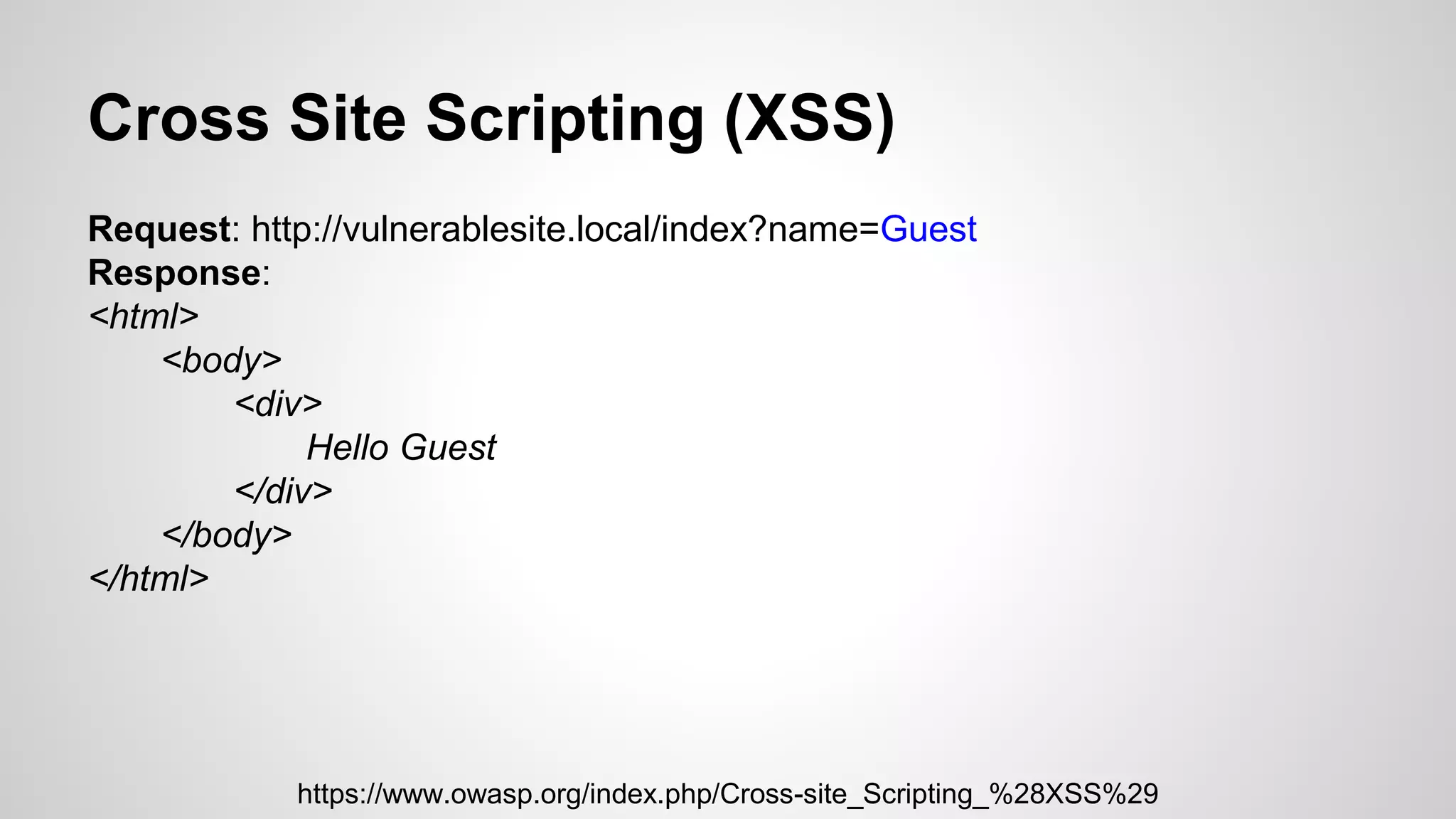
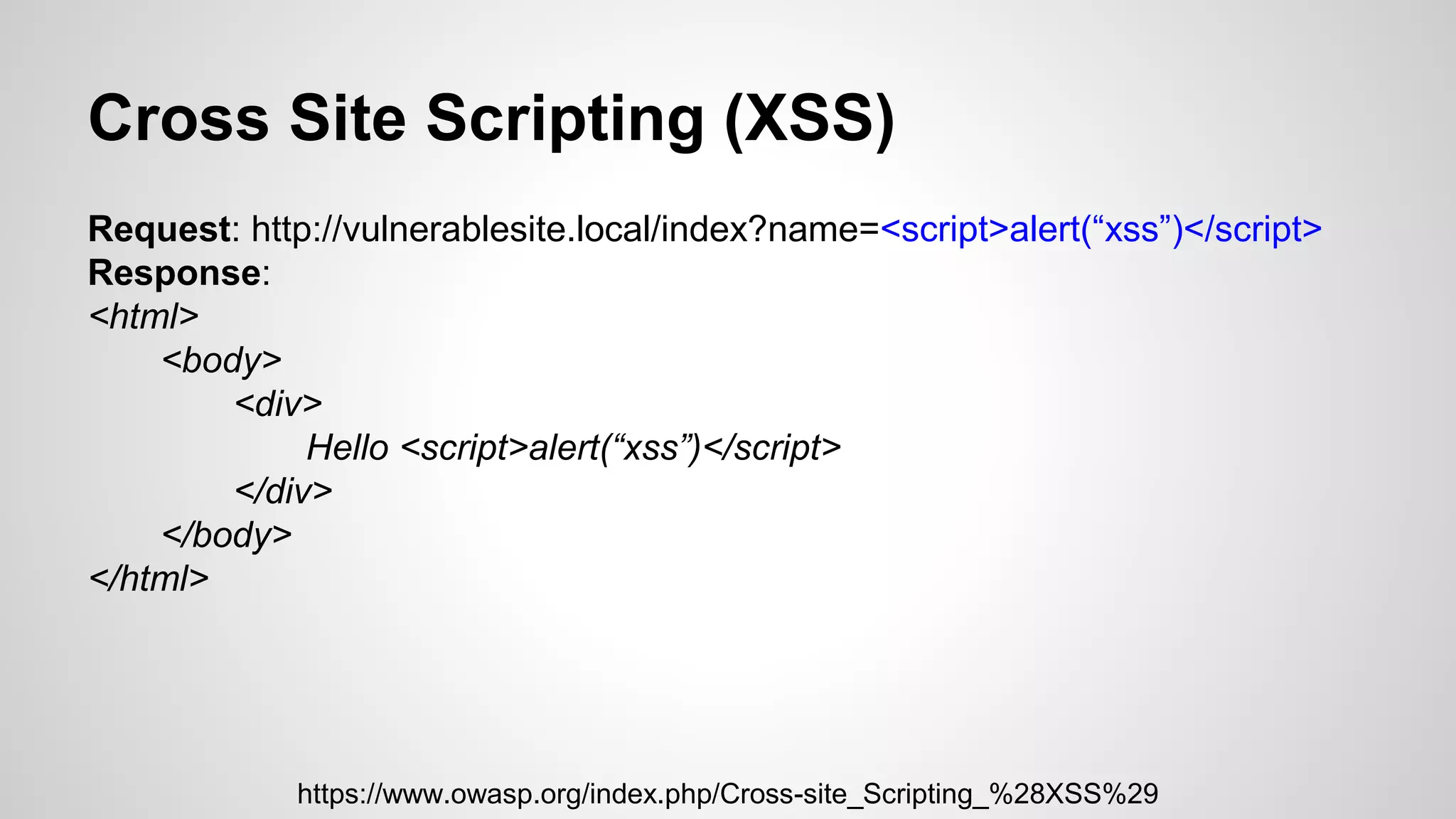
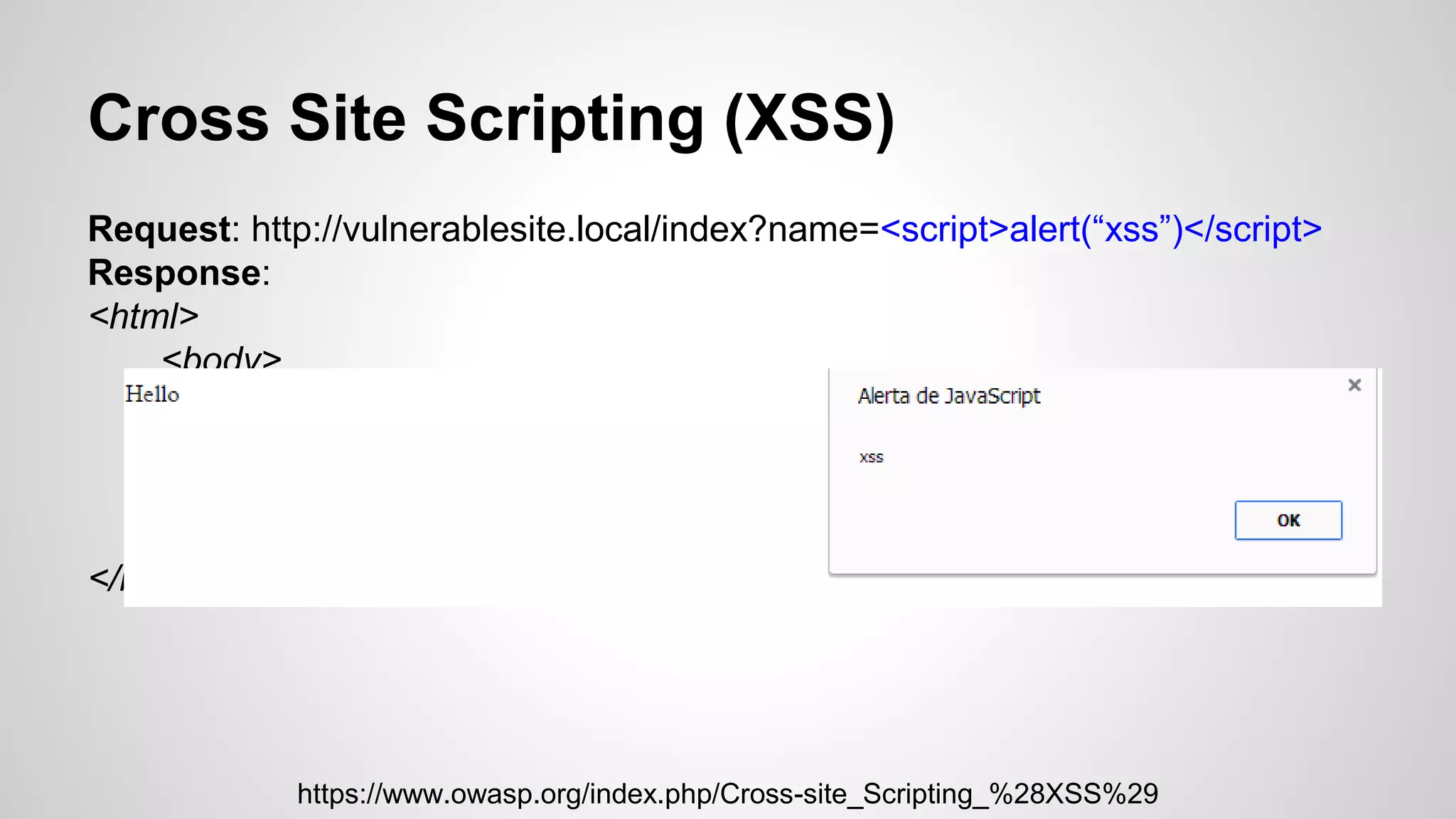
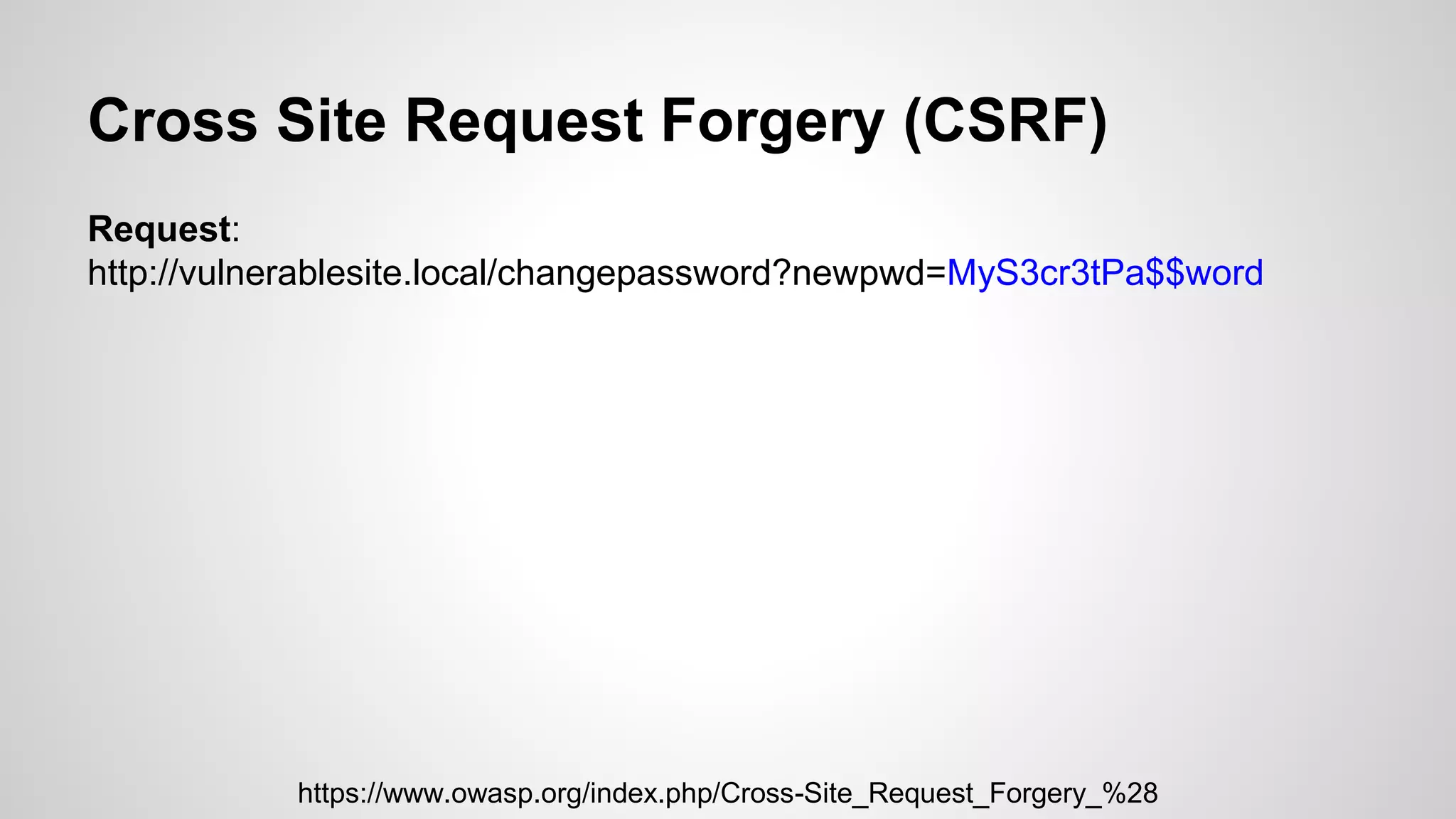
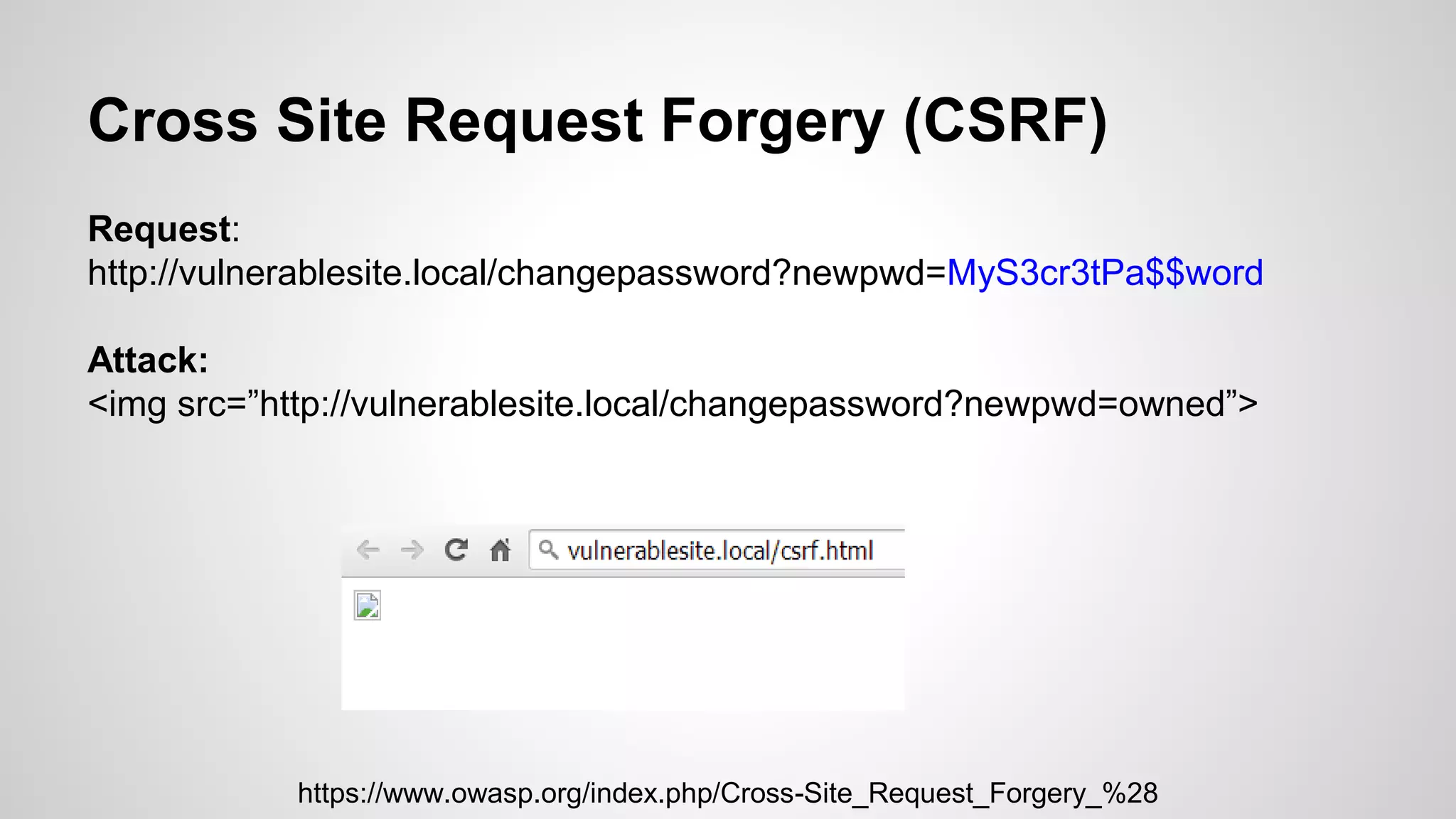
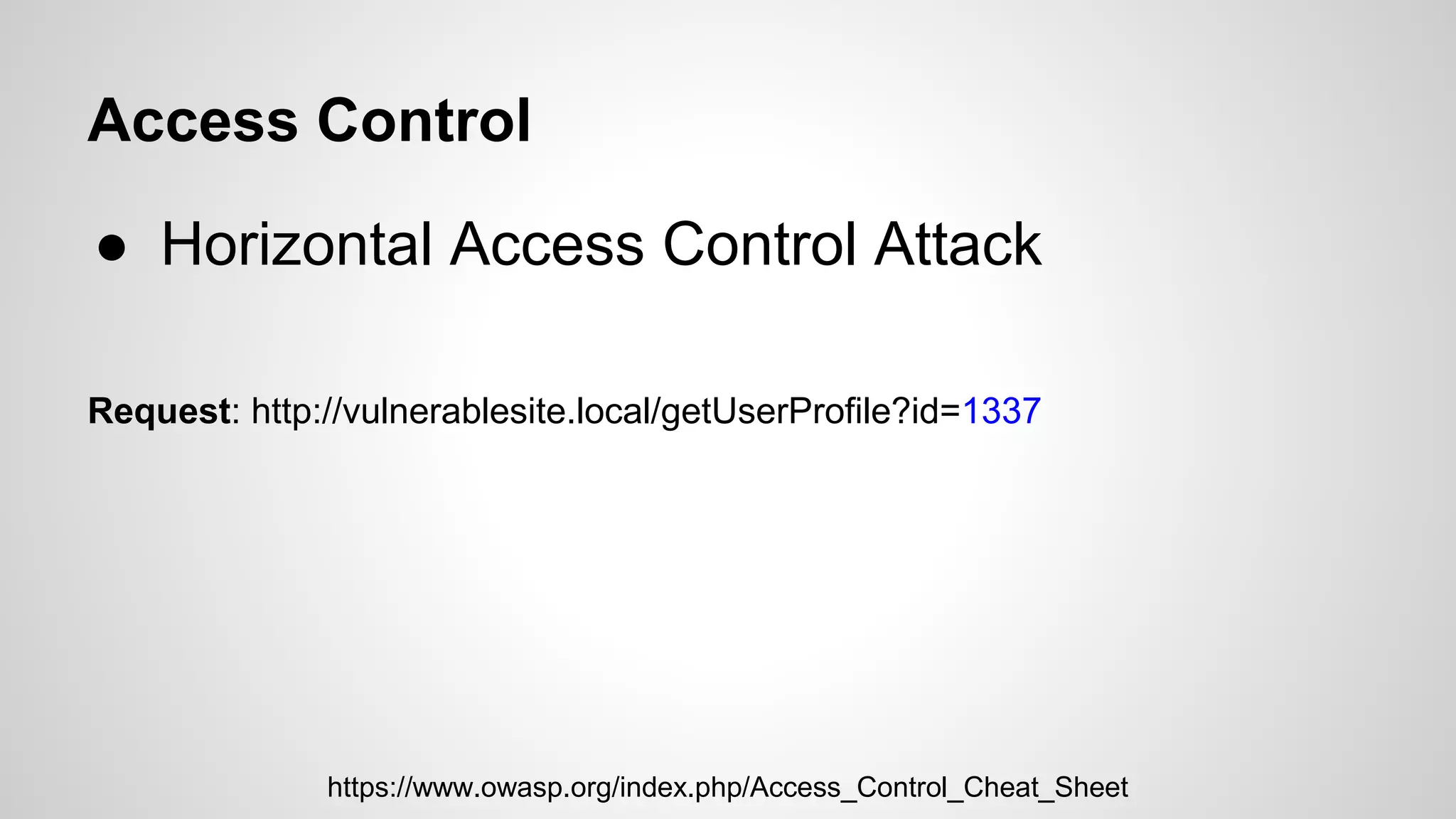
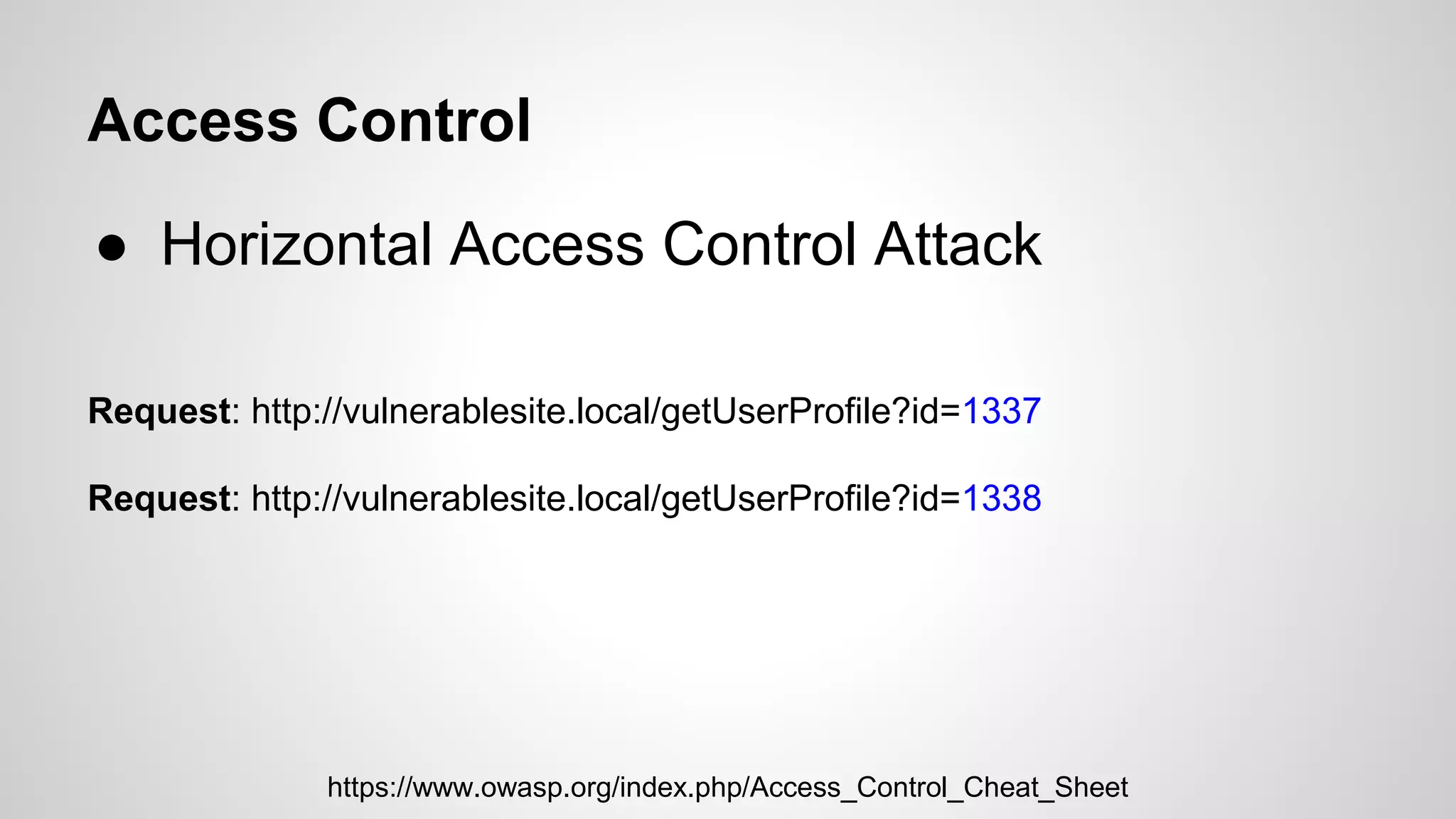
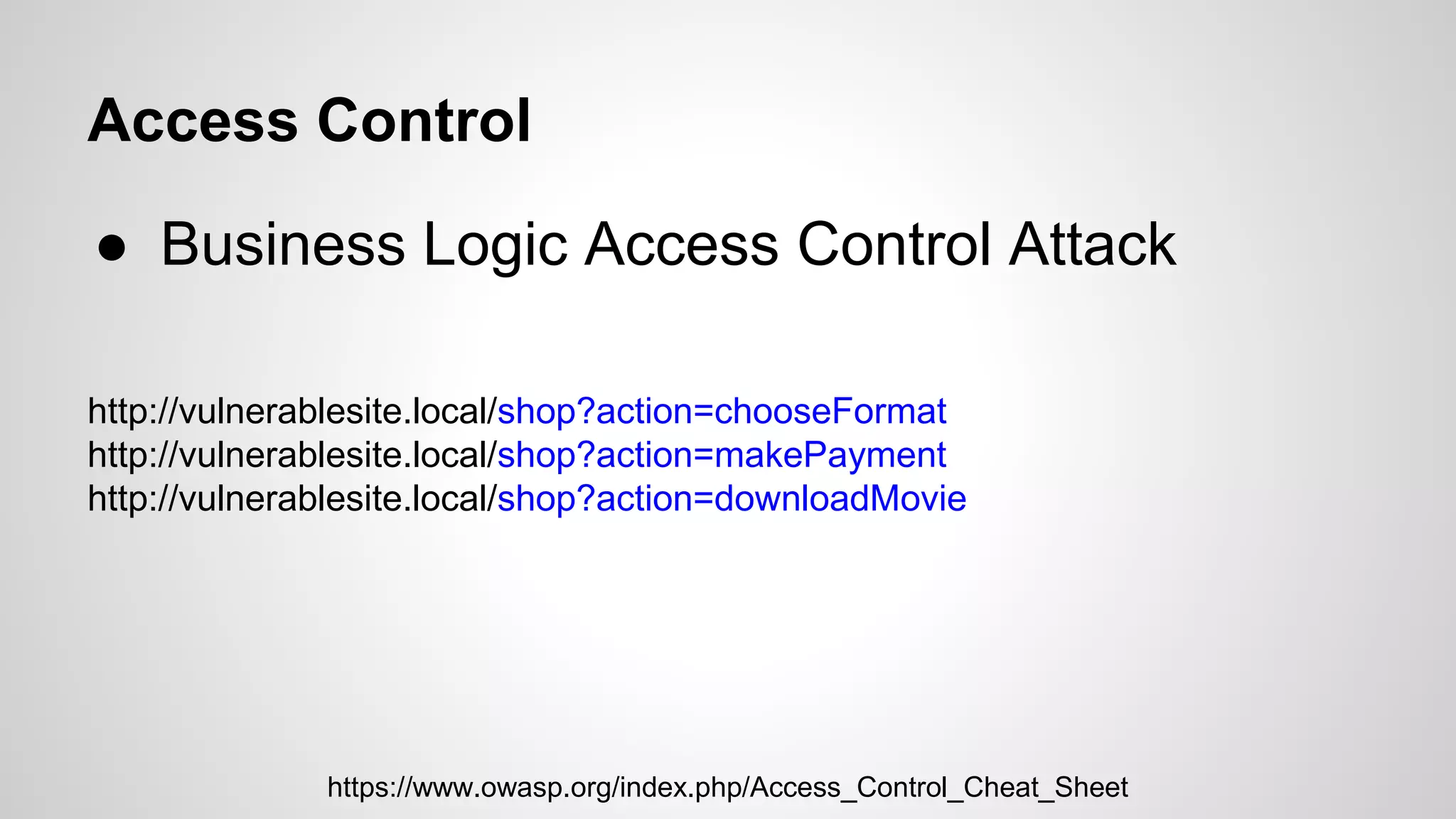
This document discusses common web application vulnerabilities like SQL injection, cross-site scripting (XSS), and cross-site request forgery (CSRF). It provides examples of each vulnerability and demonstrates how they can be exploited. The document also recommends best practices for authentication, authorization, and access control to prevent security issues. It introduces resources from the Open Web Application Security Project (OWASP) like the Top 10 list of vulnerabilities and a directory of vulnerable web applications for testing. The document promotes the use of tools like Burp Suite to aid in security testing of web applications.