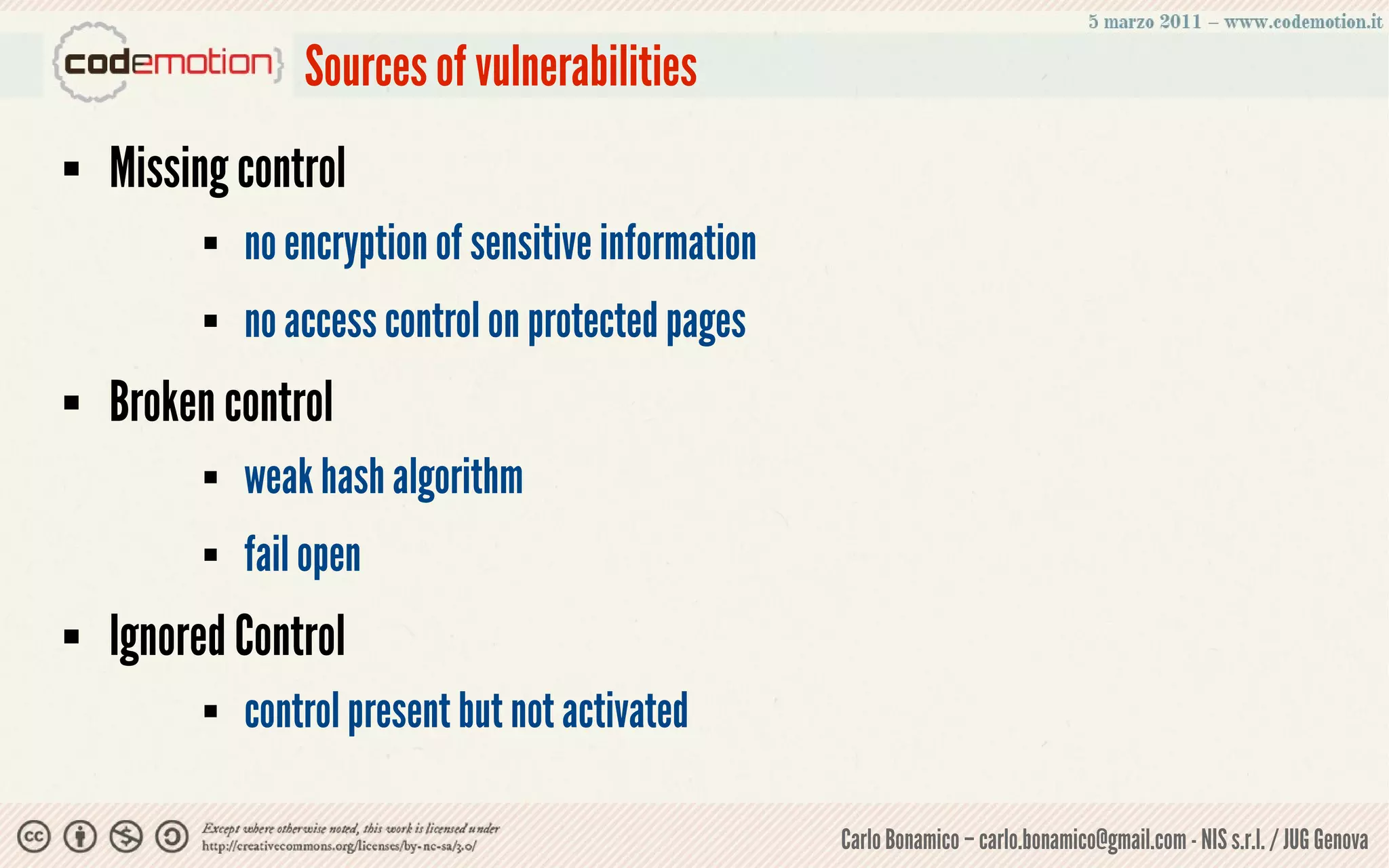
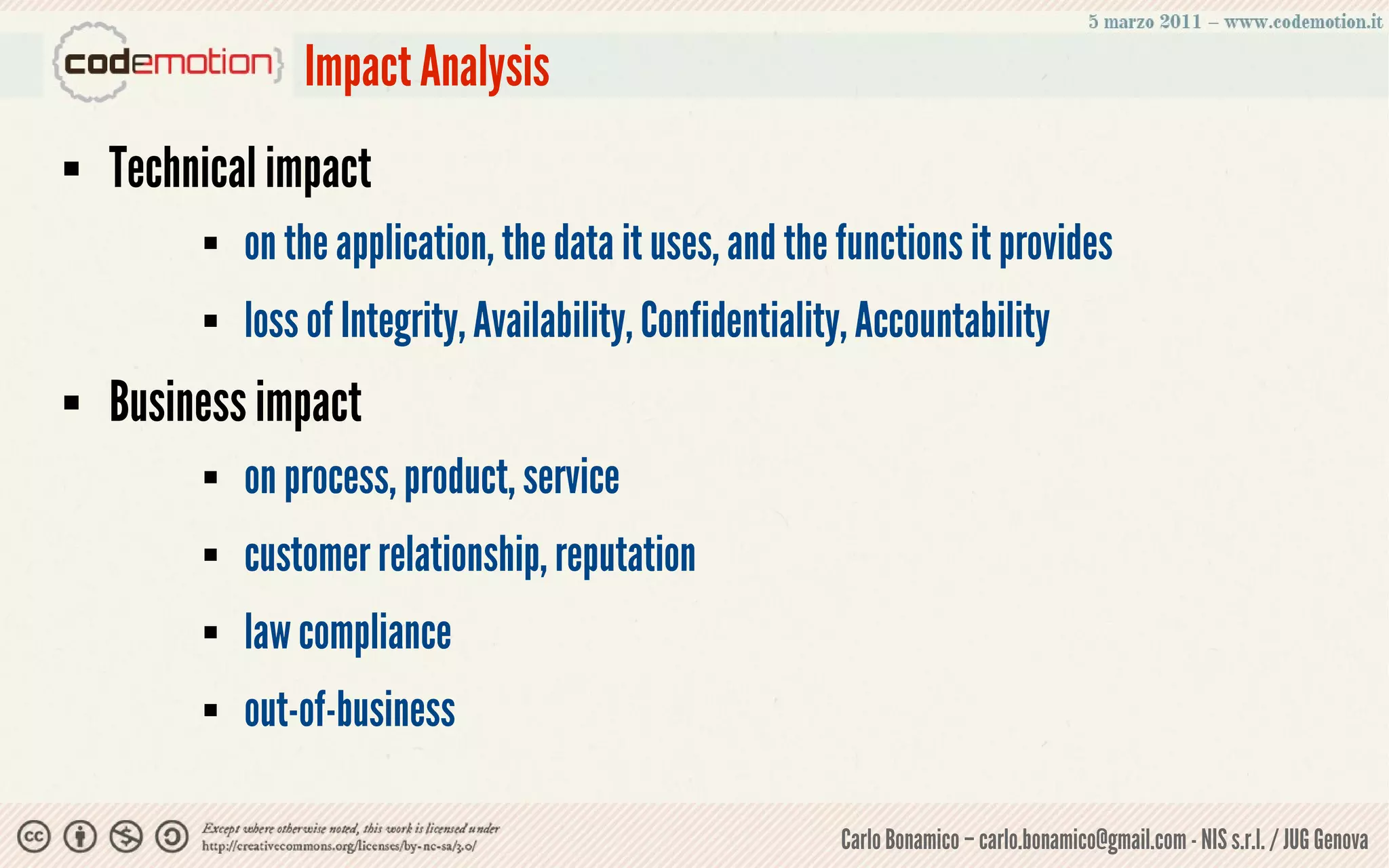
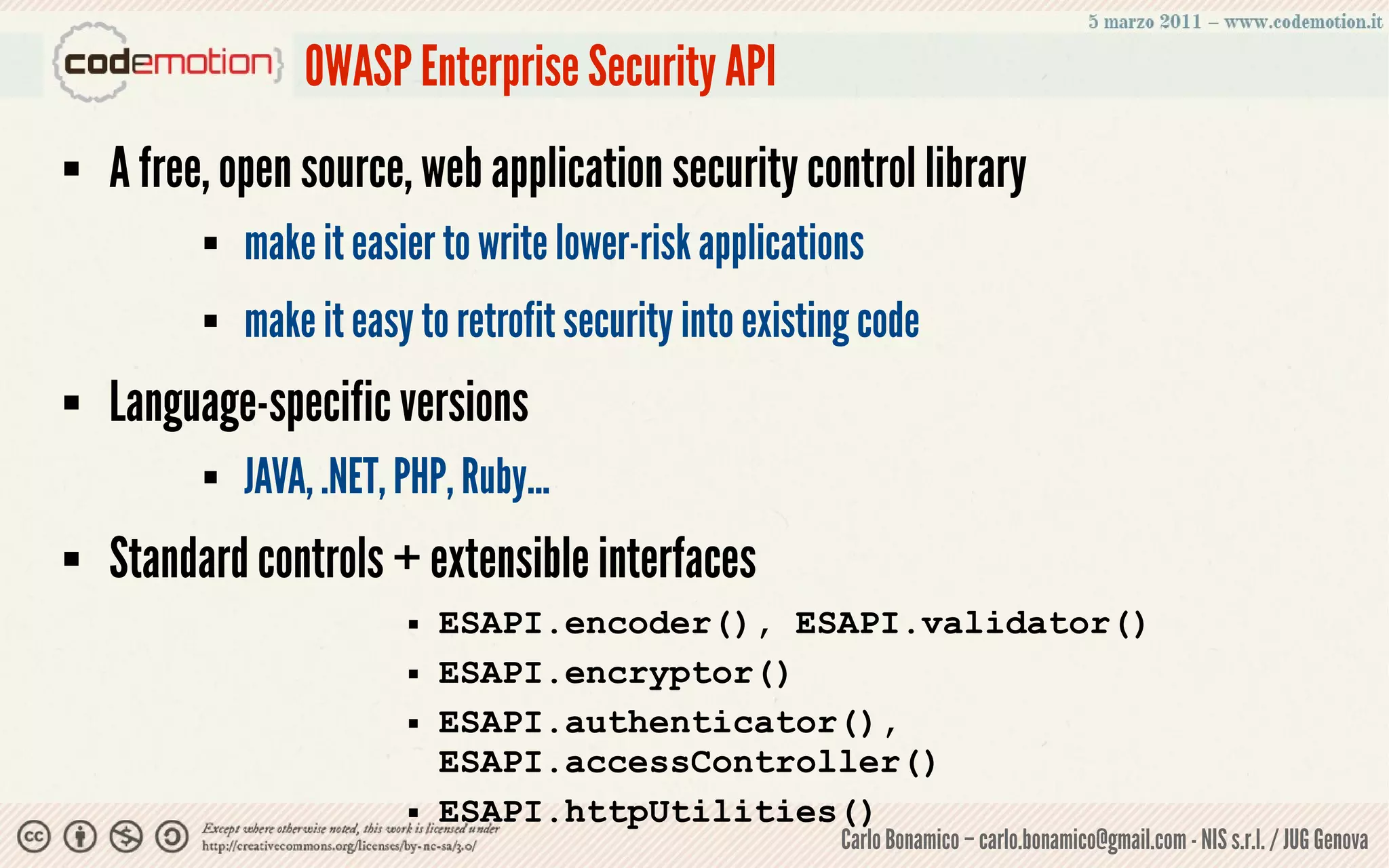
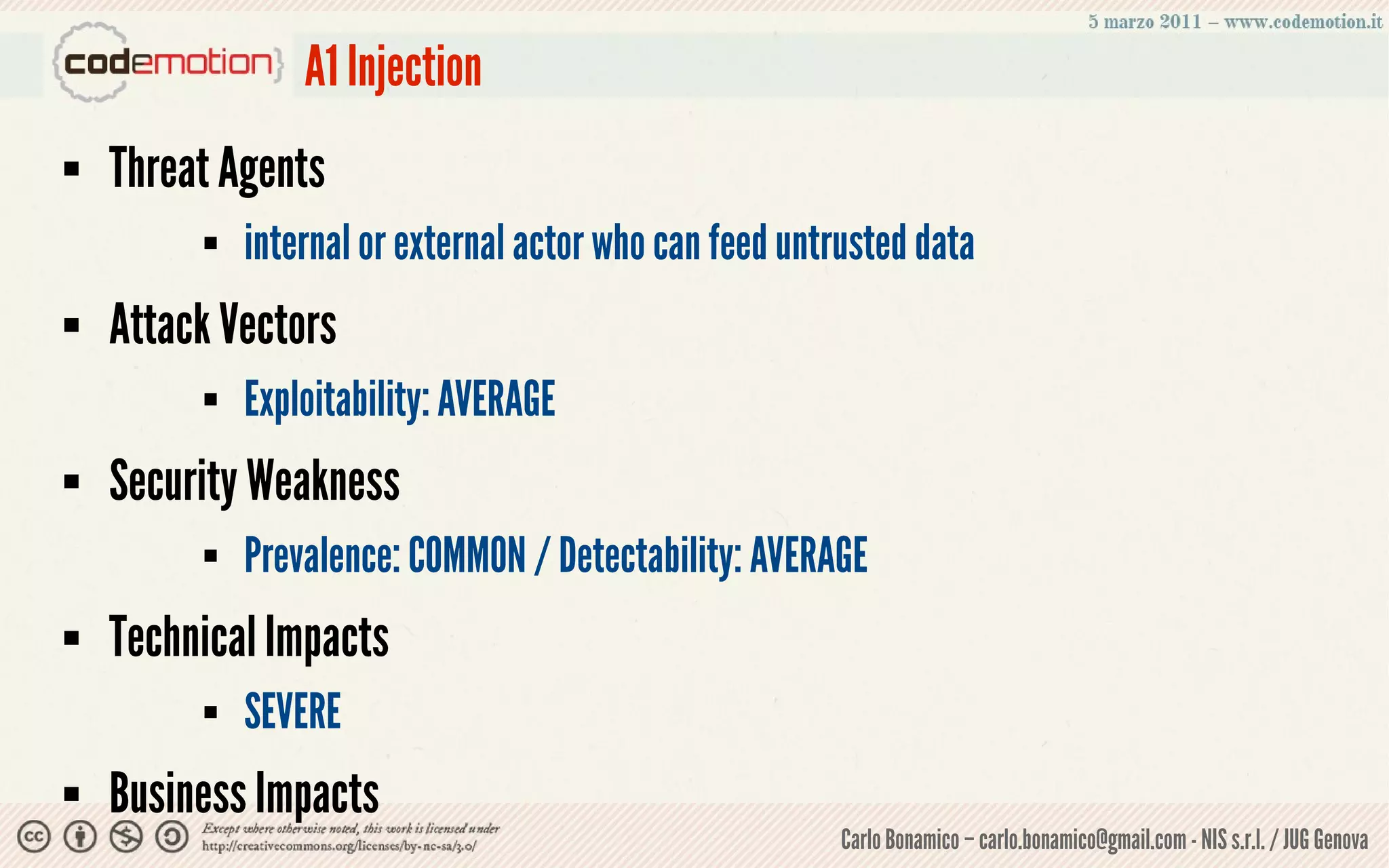
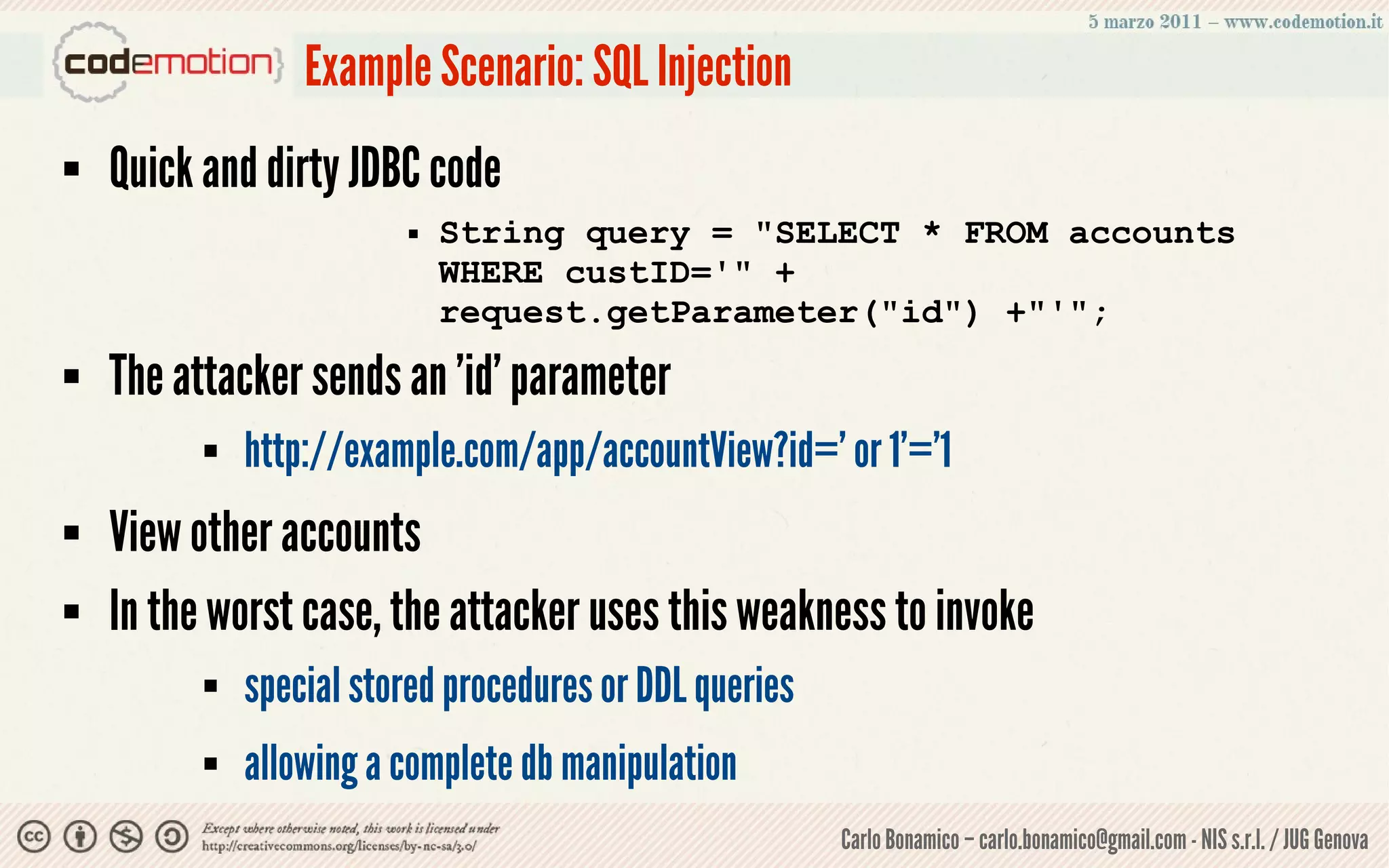
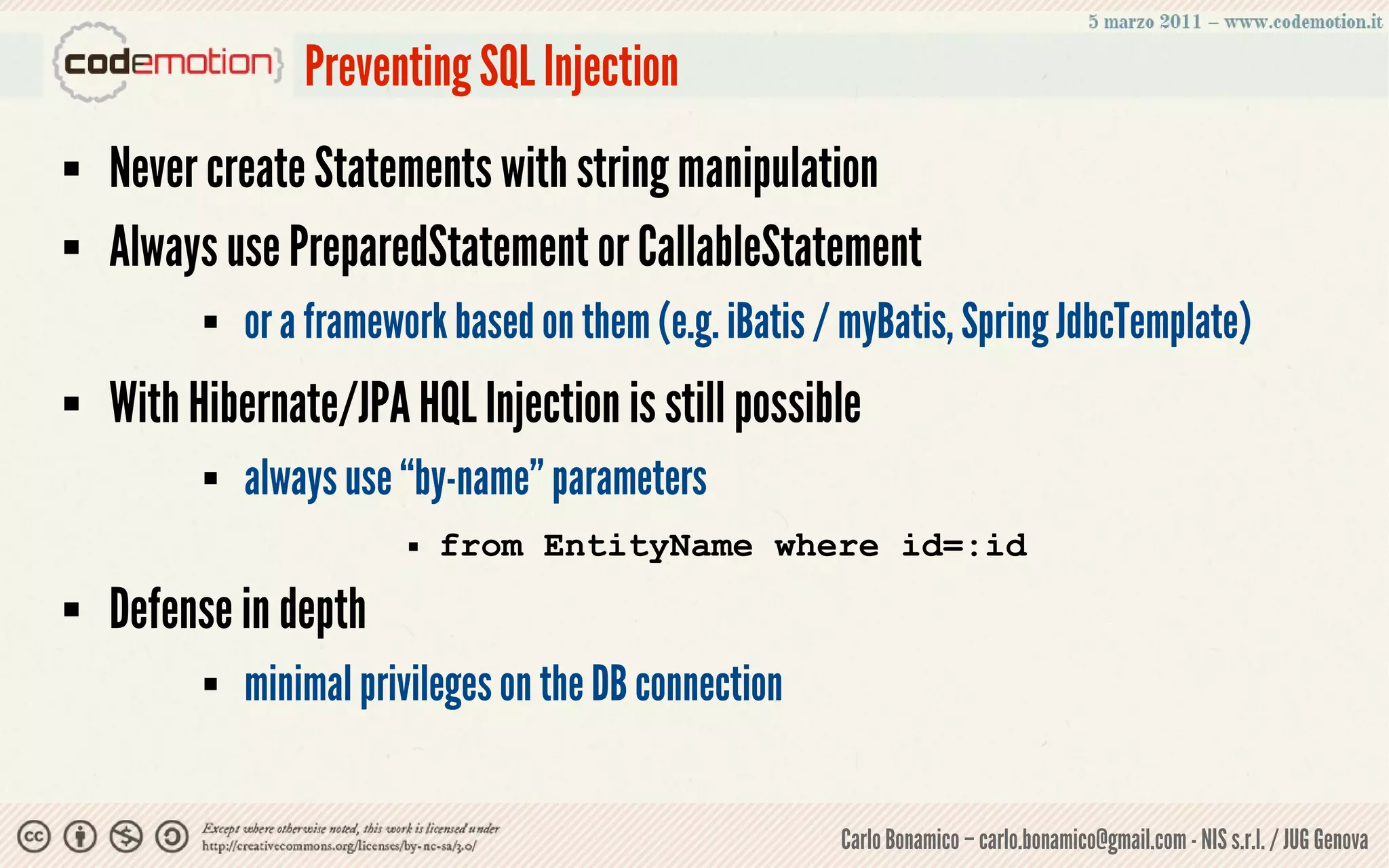
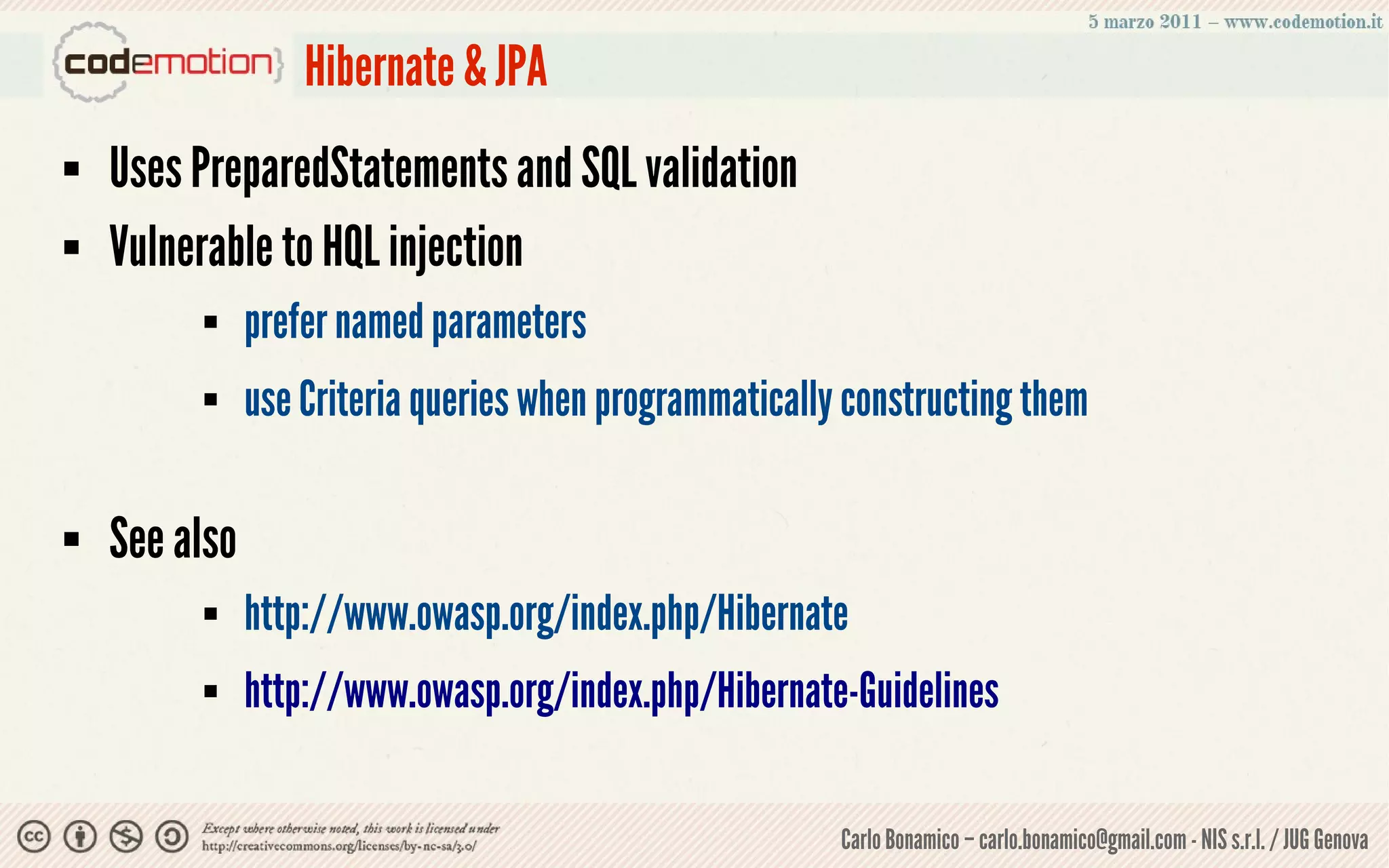
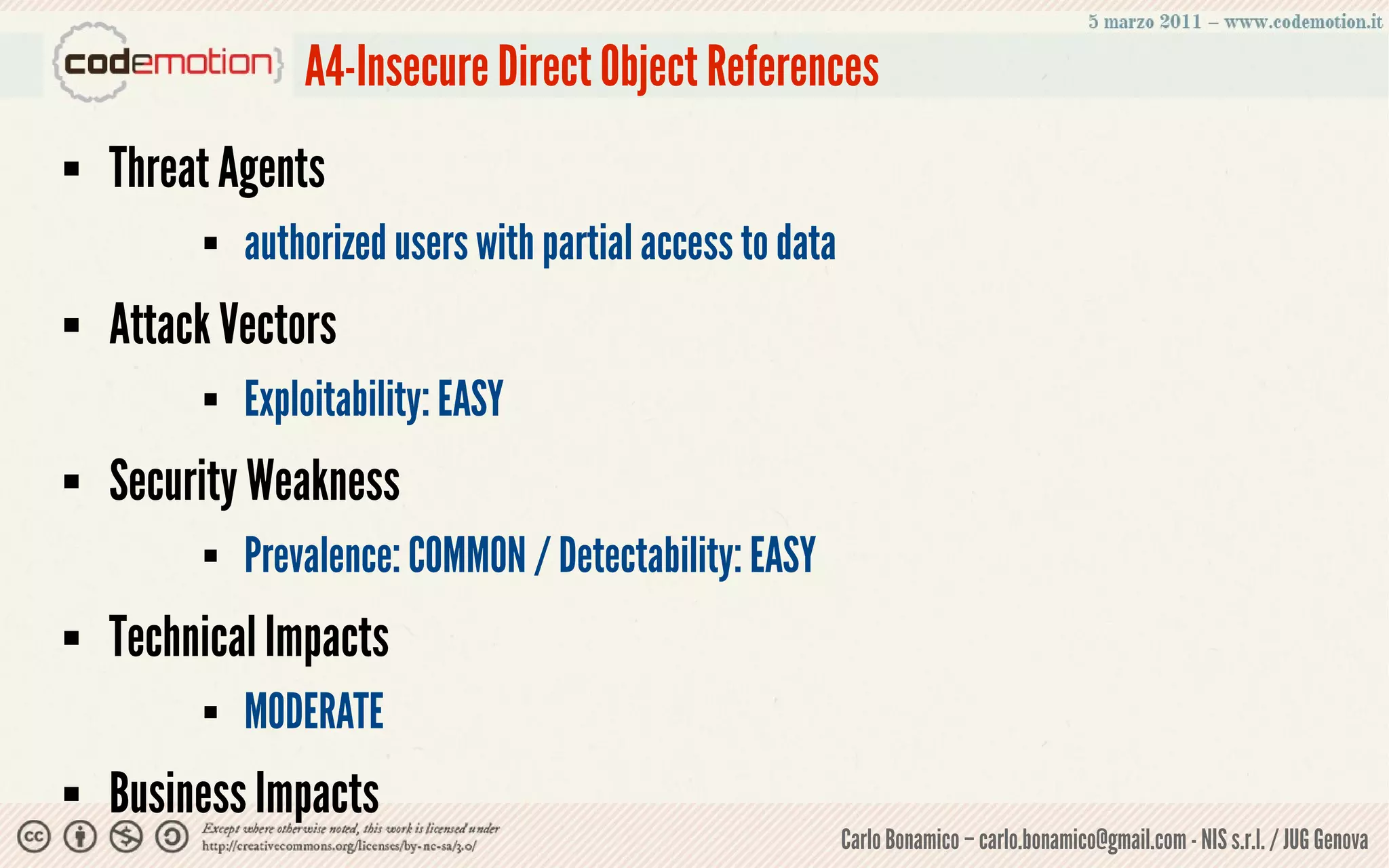
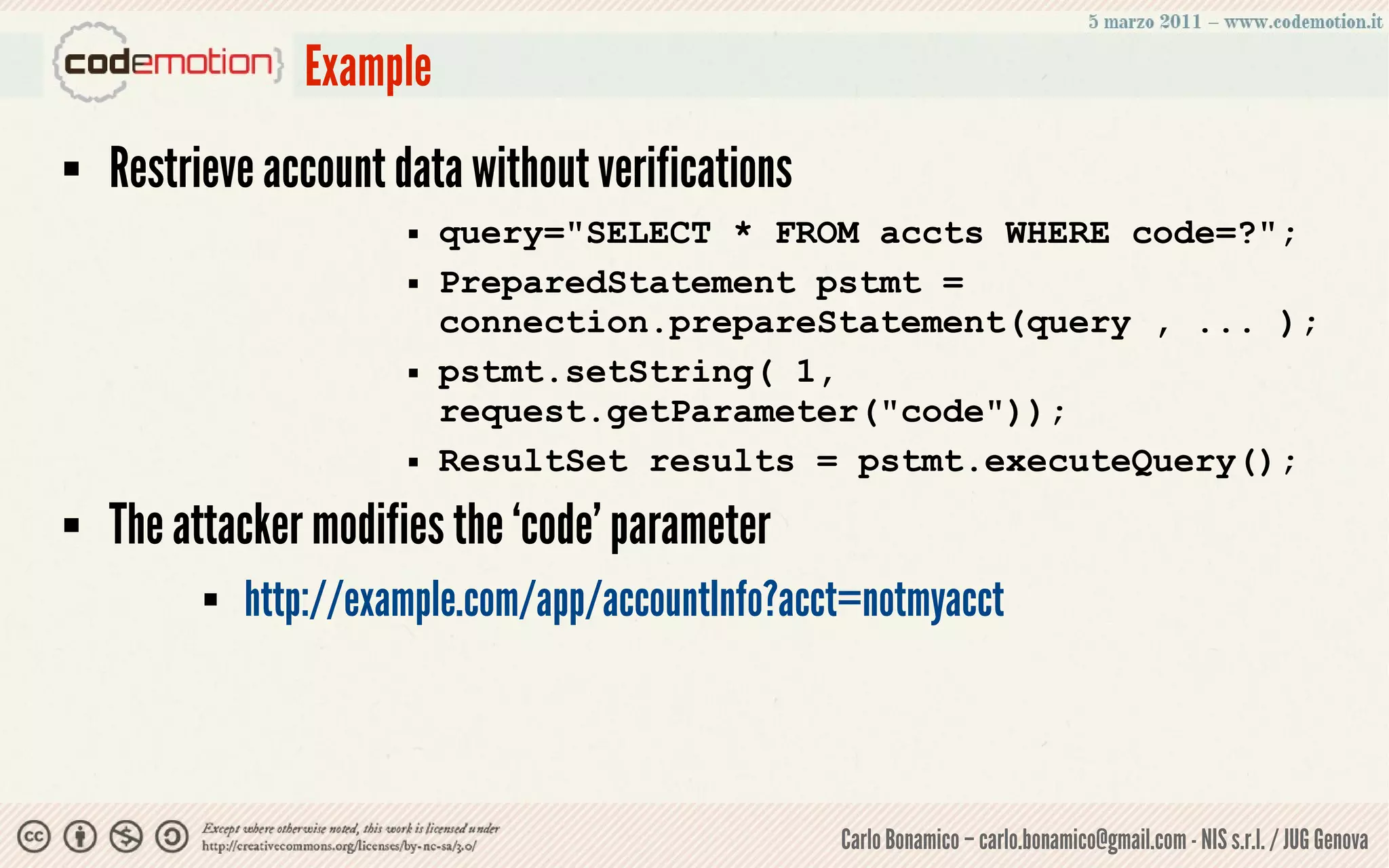
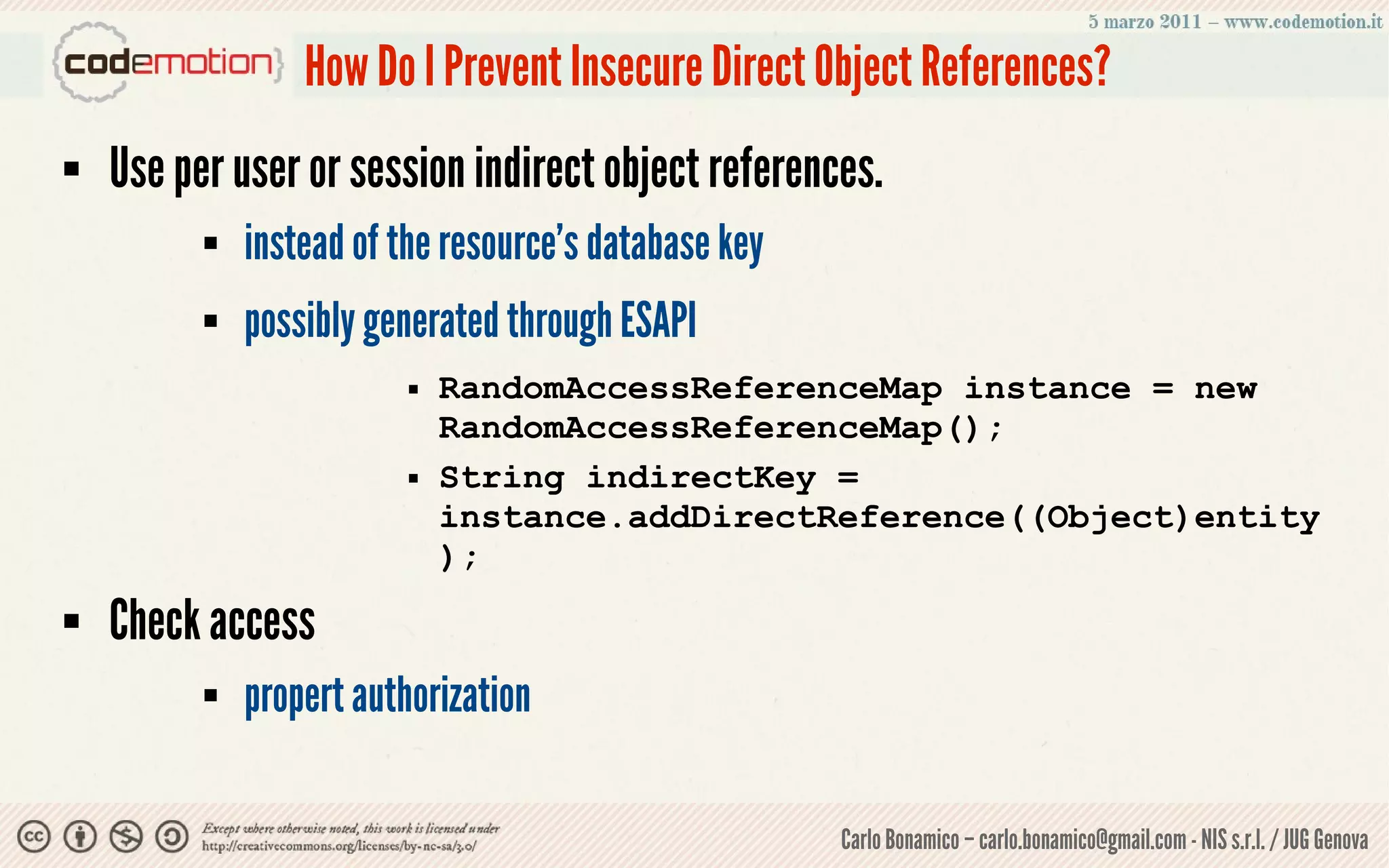
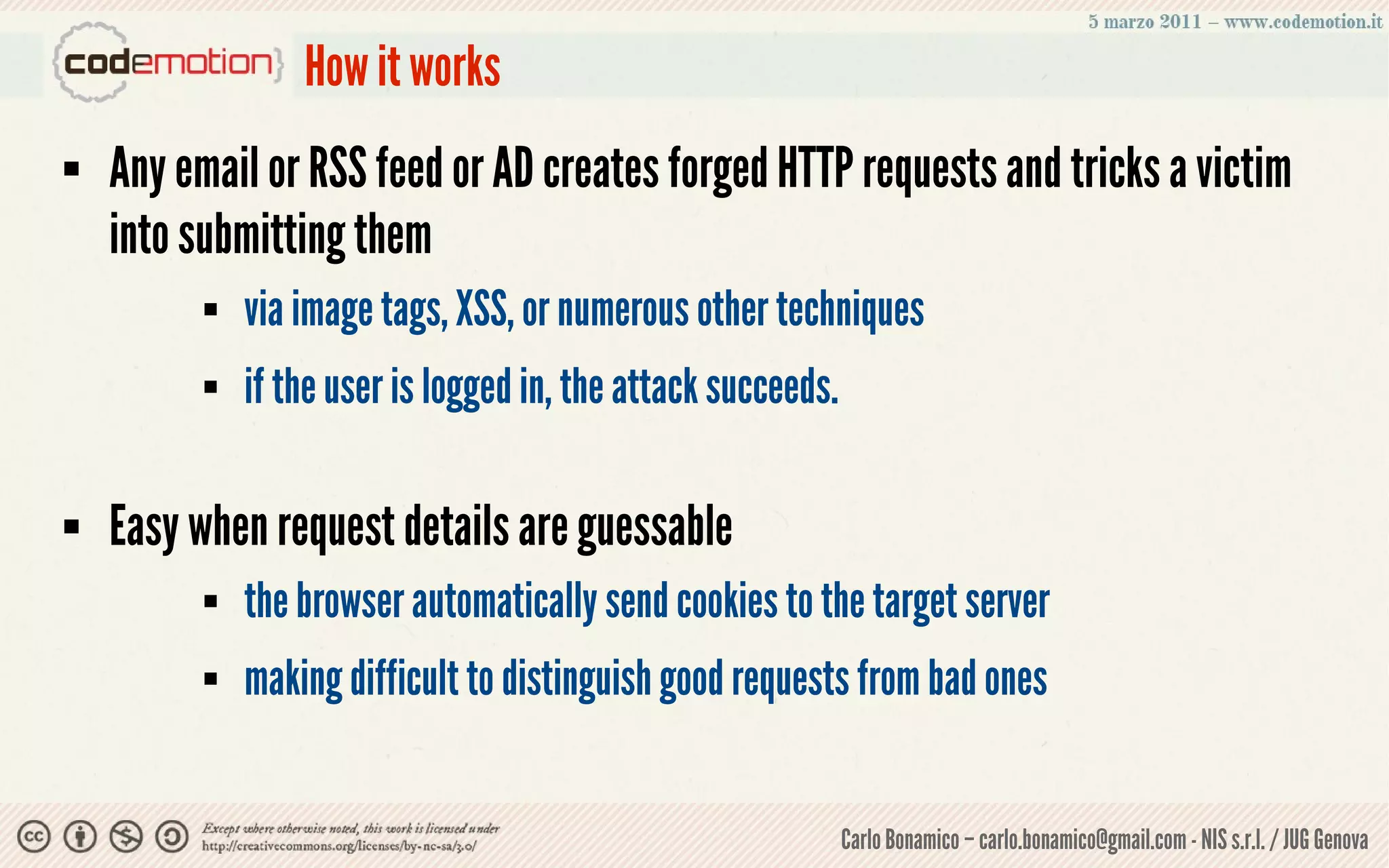
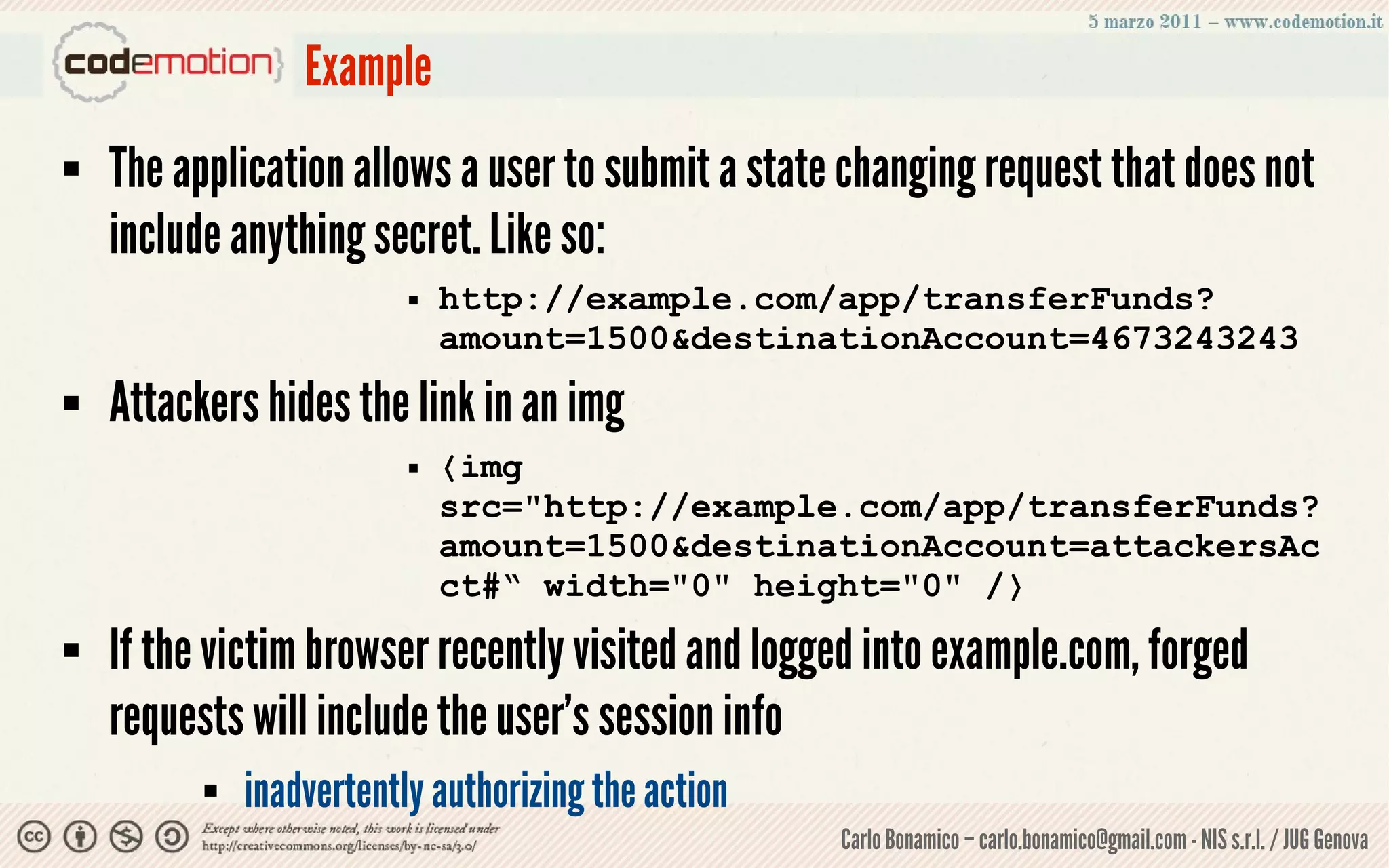
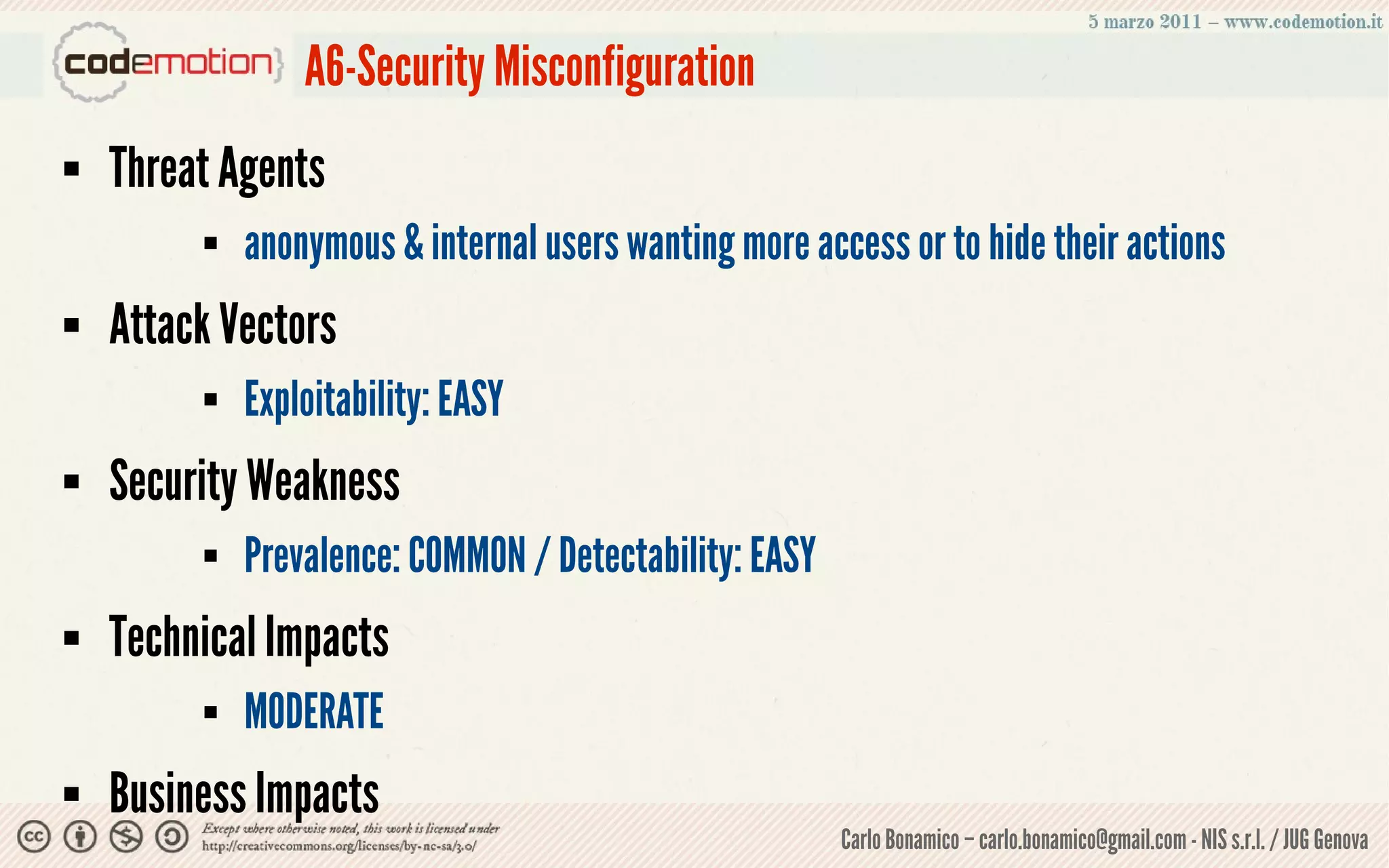
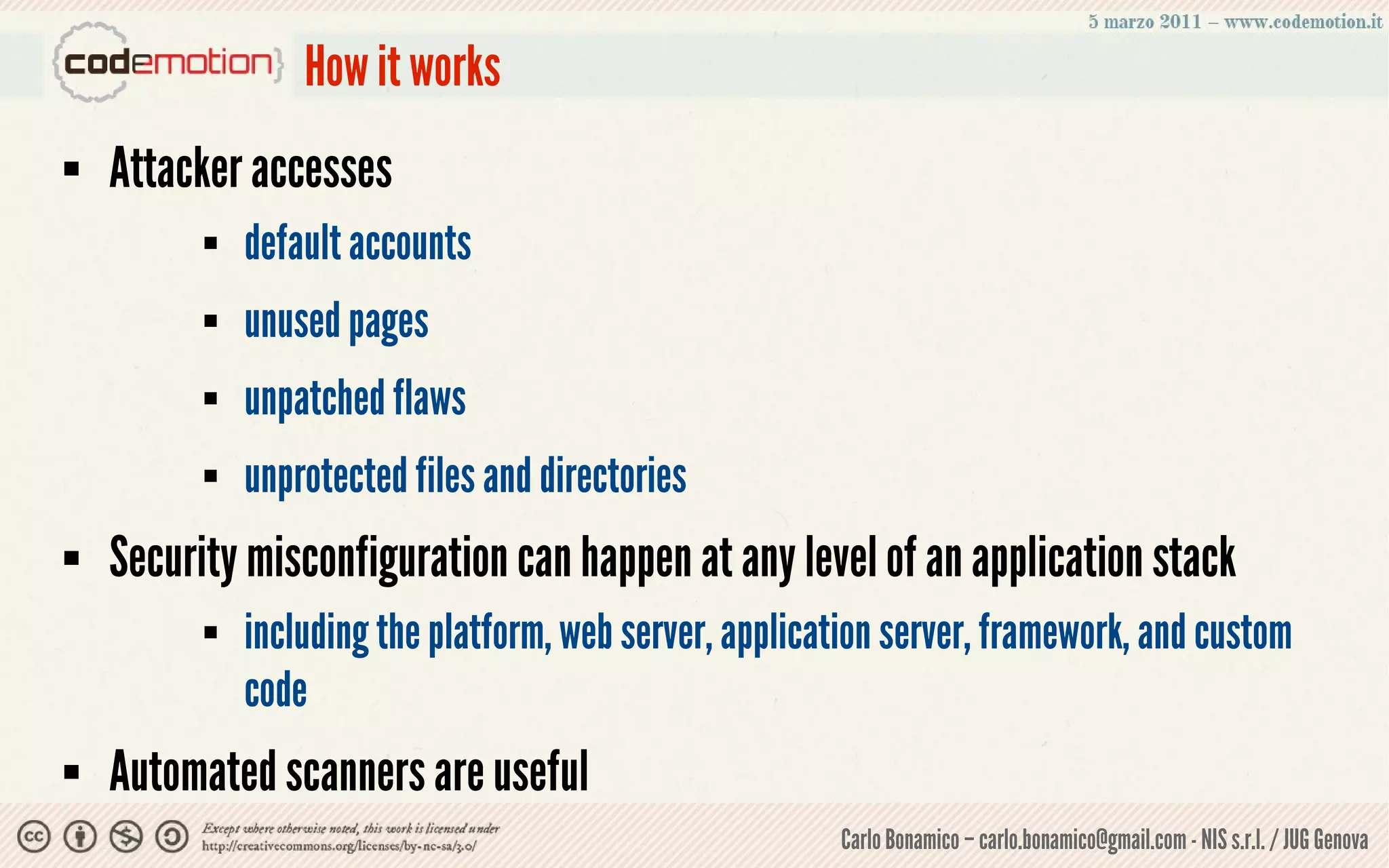
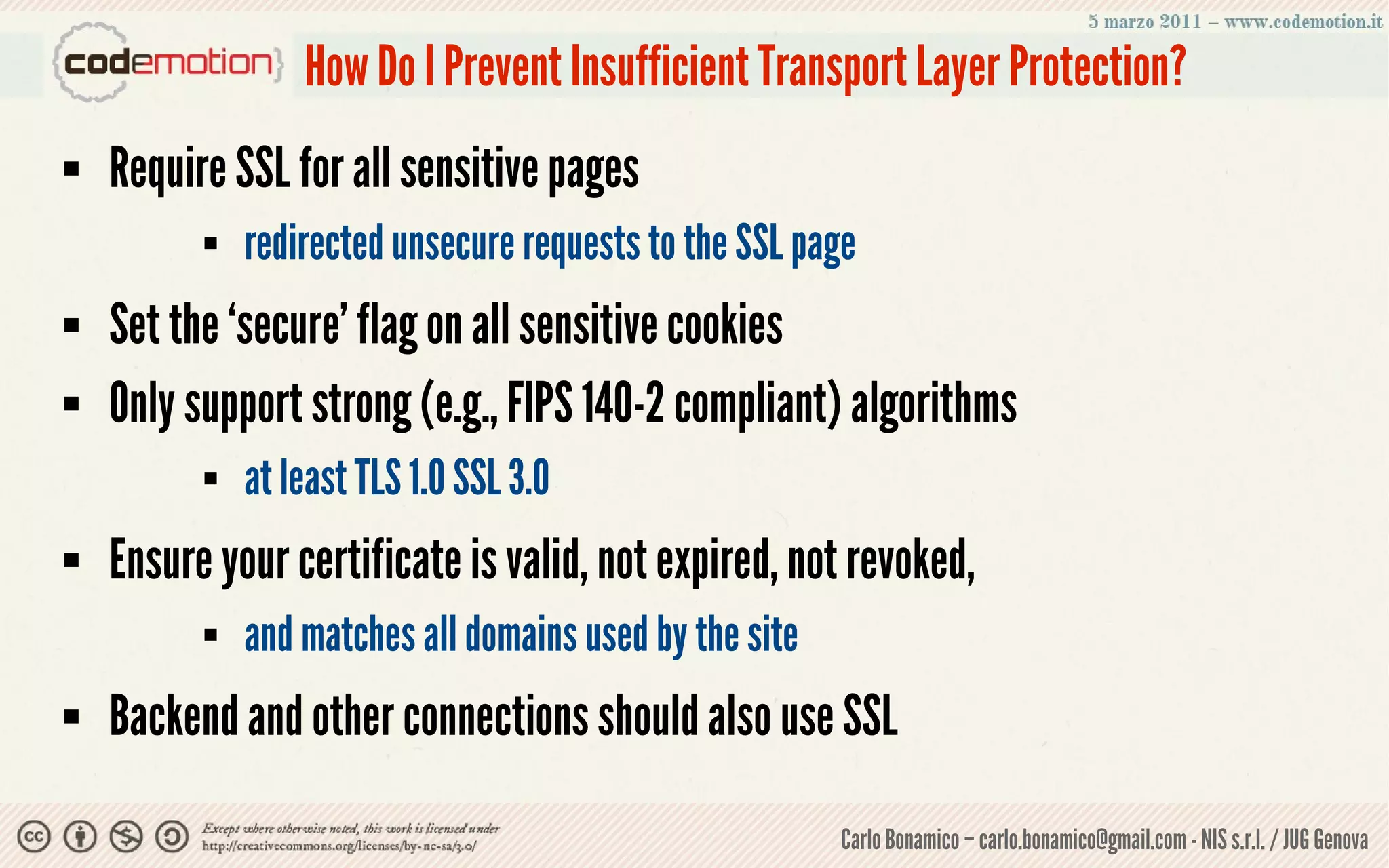
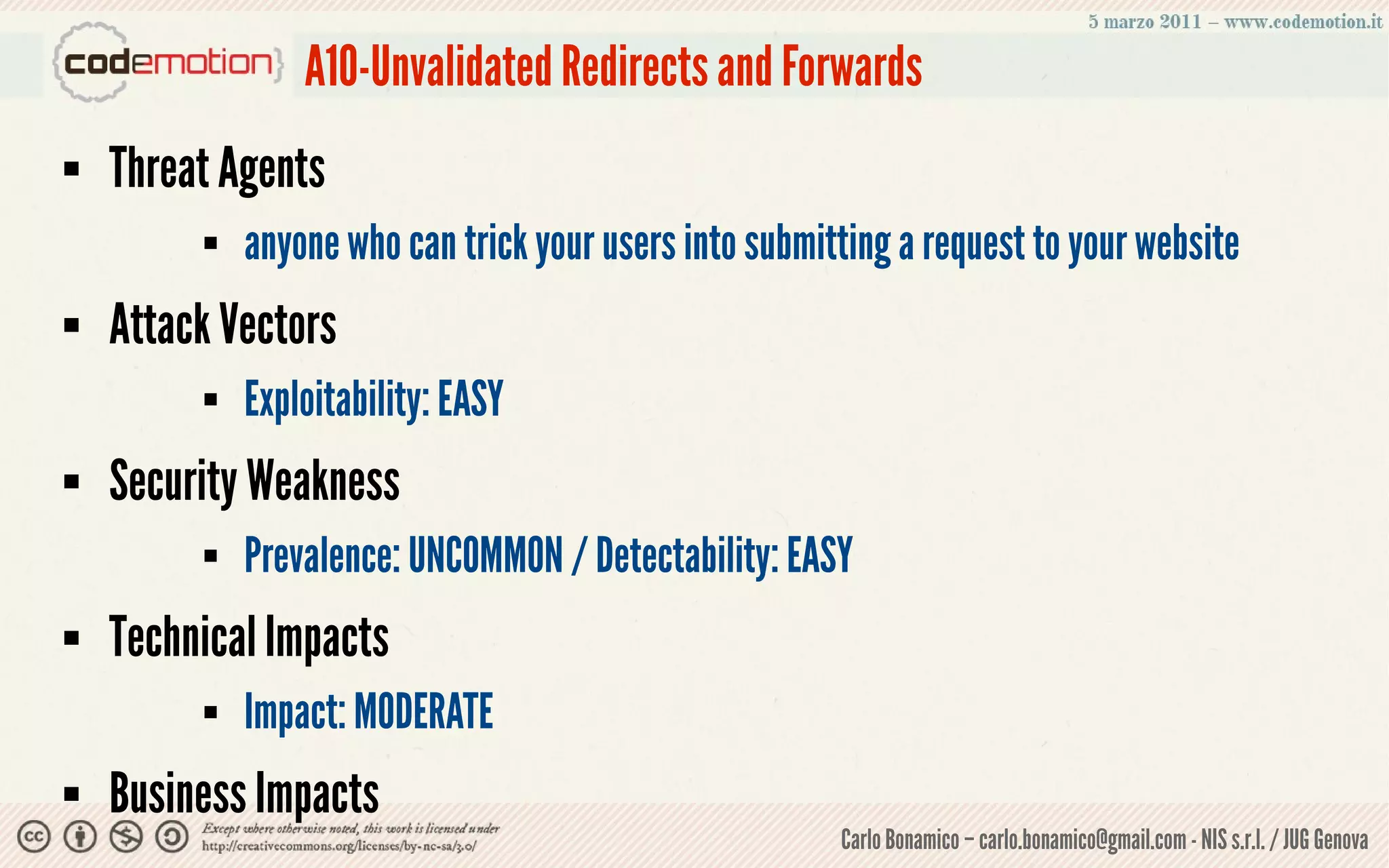
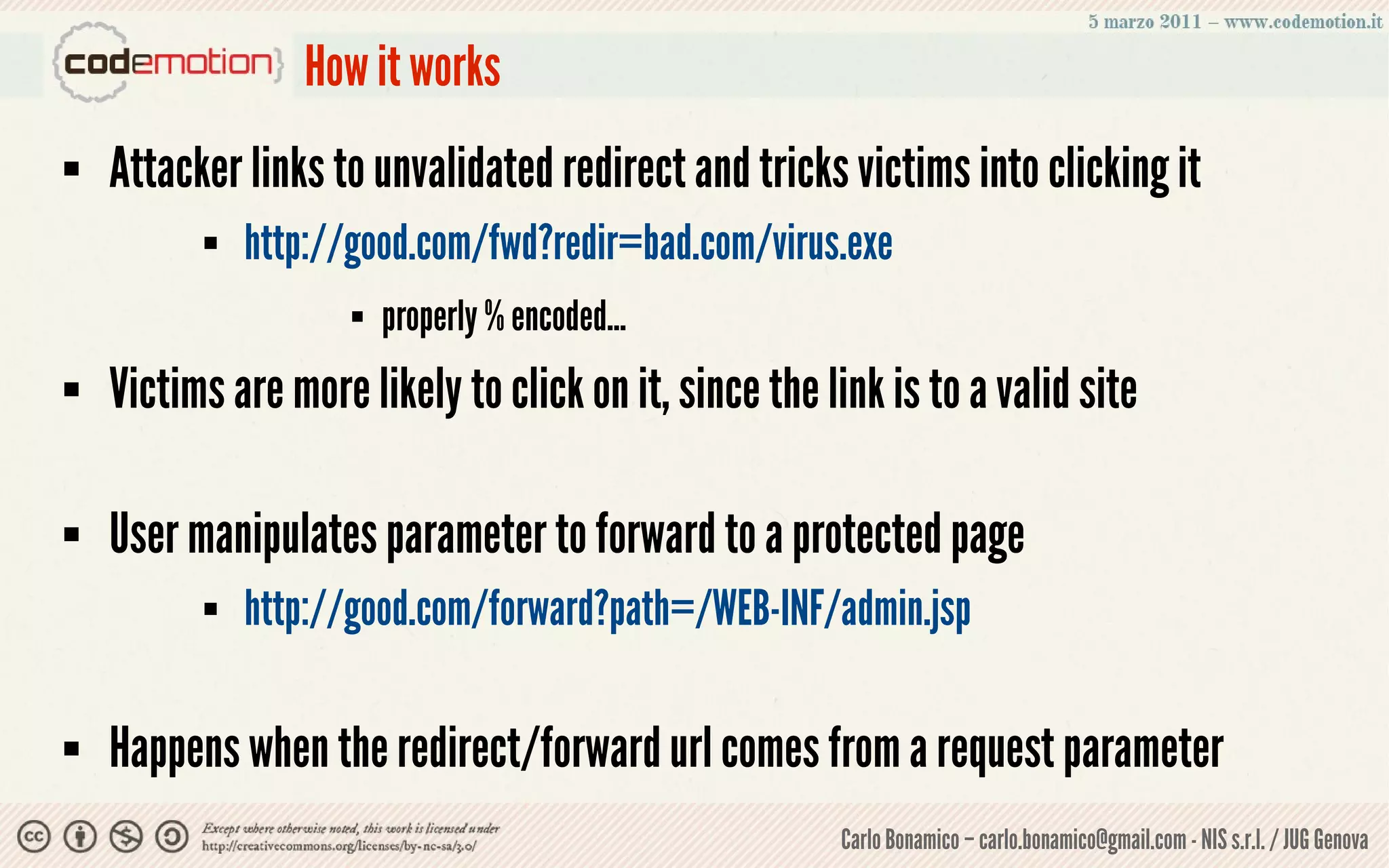
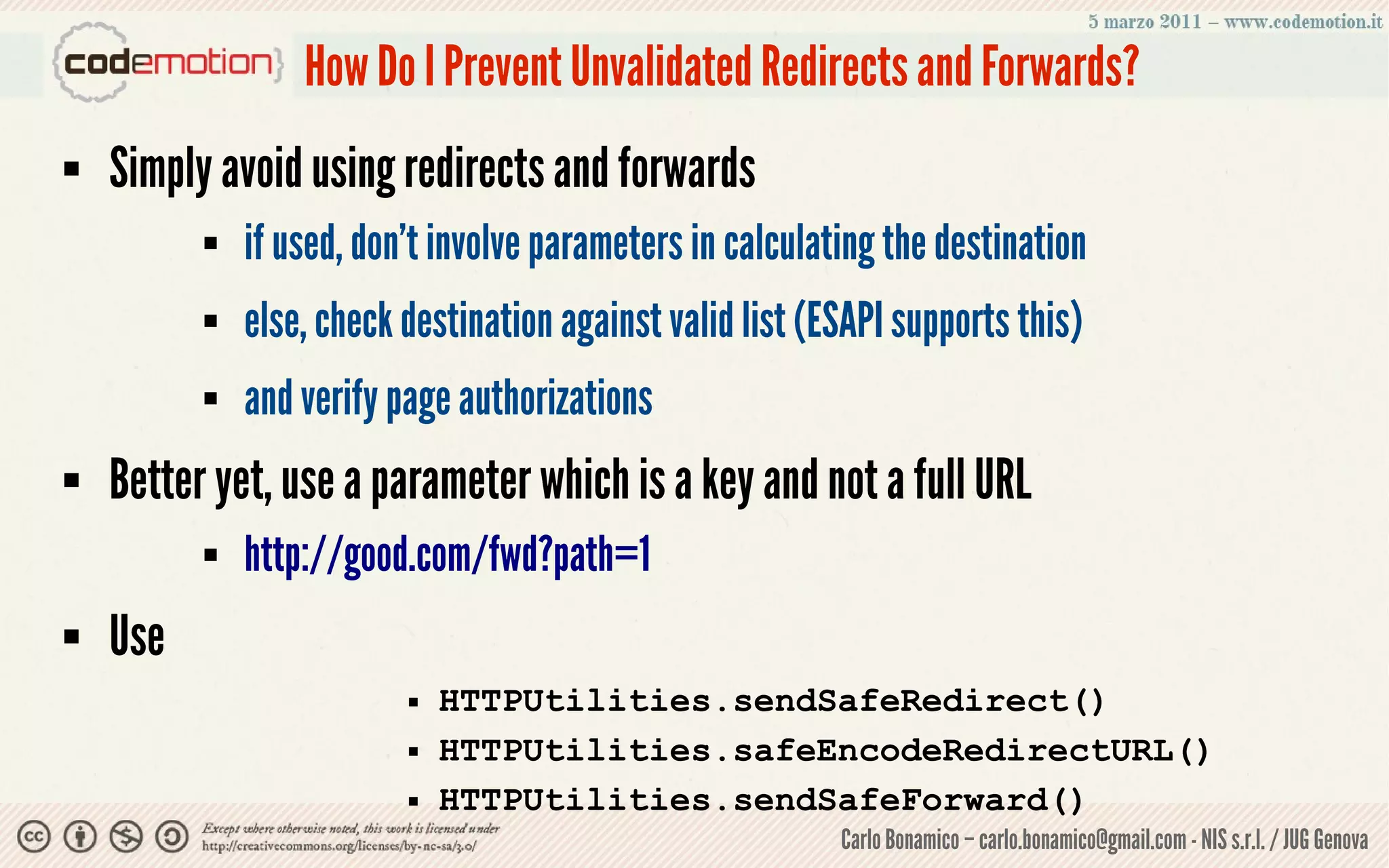
This document summarizes a presentation on web application security risks. It discusses how most web applications are not securely developed by default and are vulnerable to attacks like injection and cross-site scripting. It introduces the OWASP Top 10 project, which identifies the top 10 security risks faced by web applications. The presentation focuses on the risks of injection and cross-site scripting attacks, and approaches for mitigating these risks, including using frameworks like Spring Security and the OWASP Enterprise Security API.