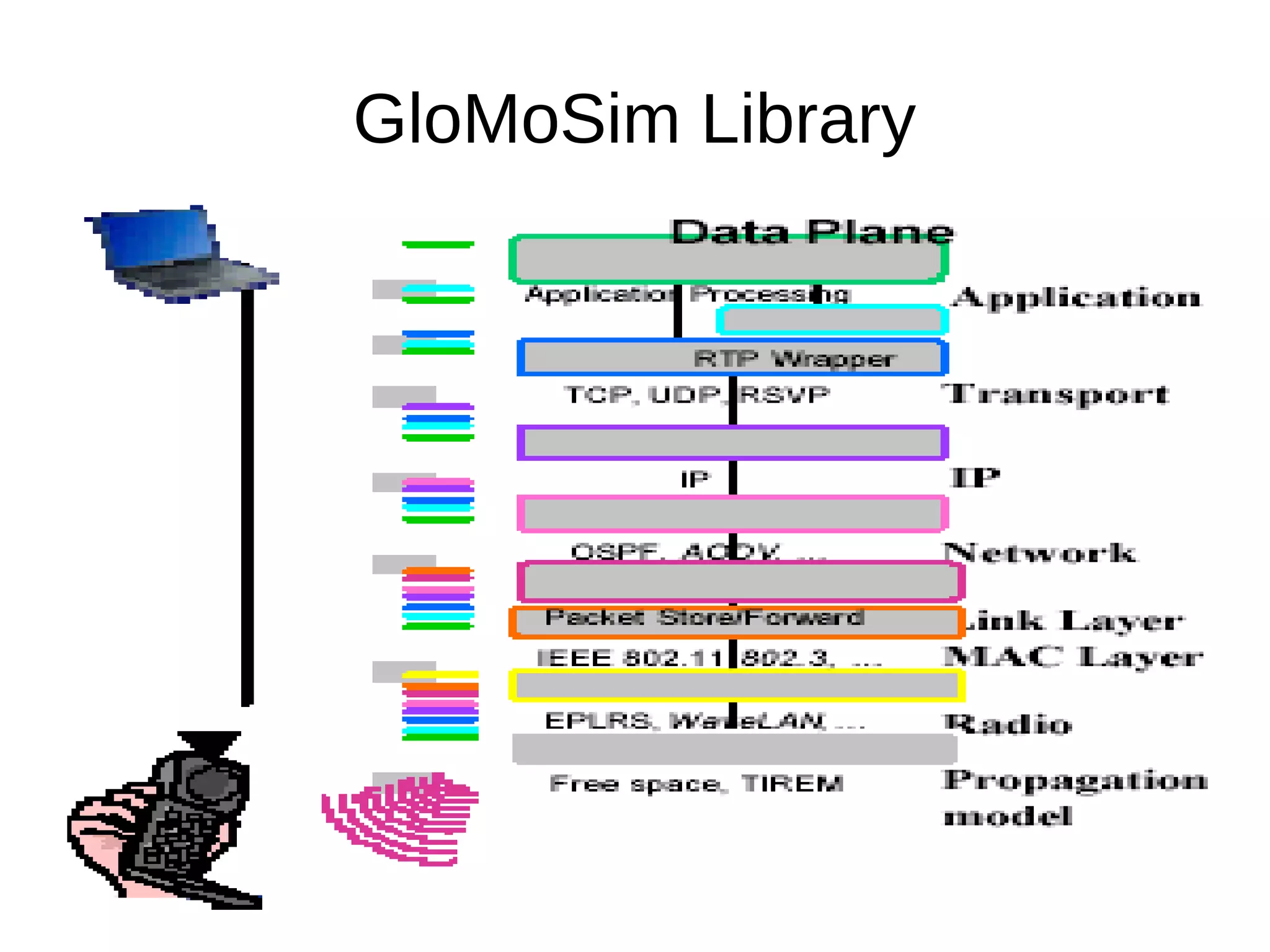
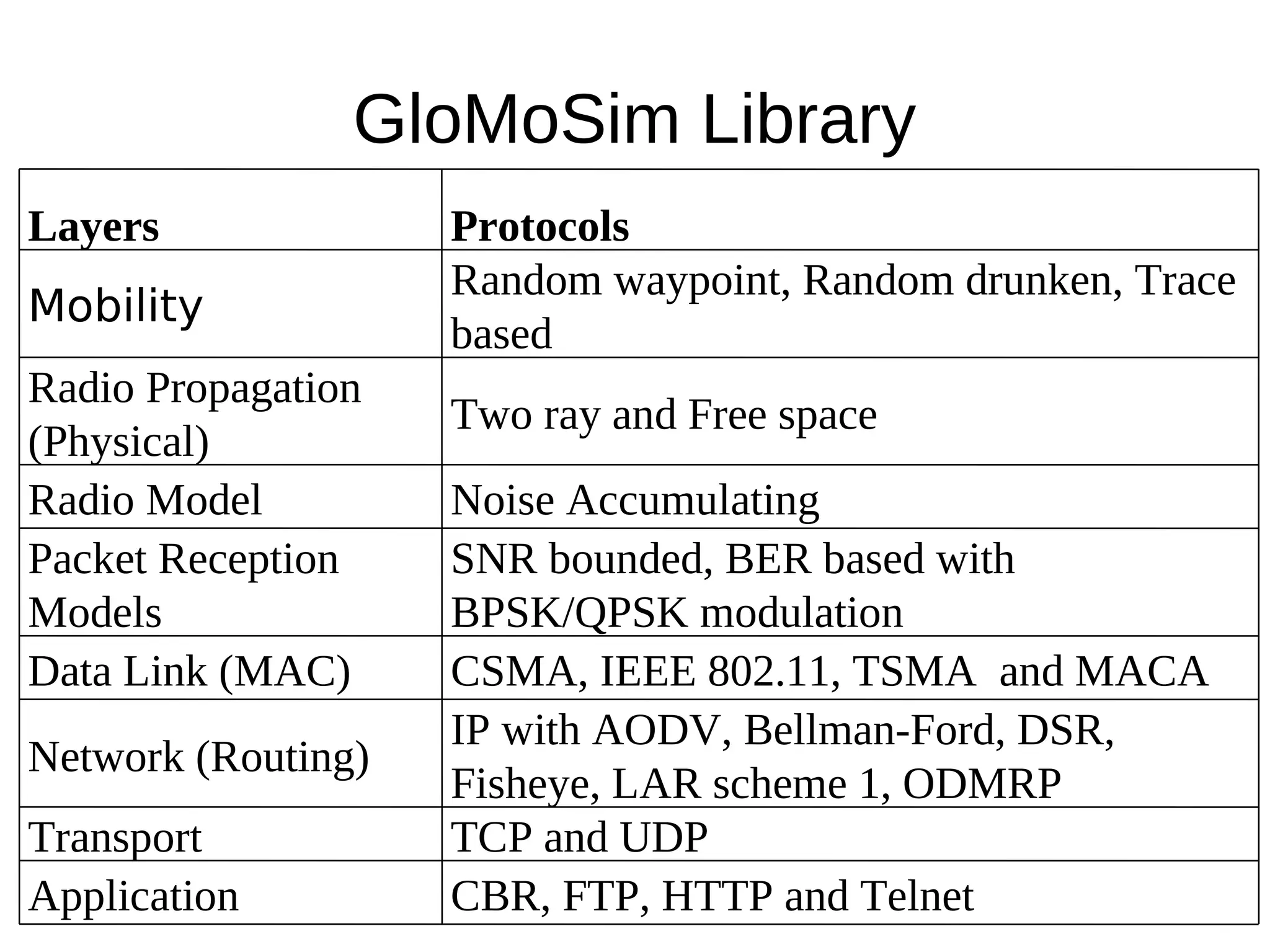
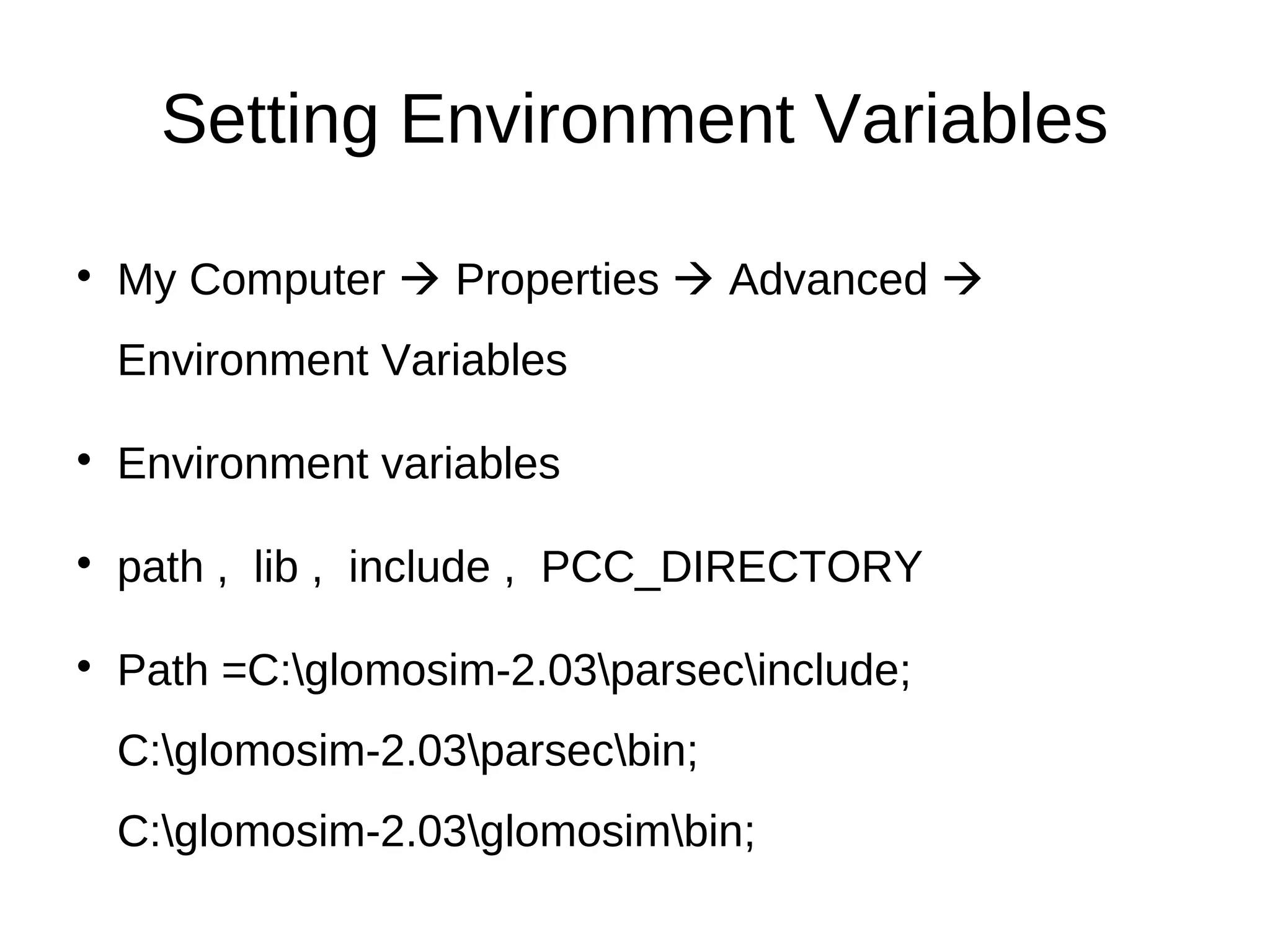
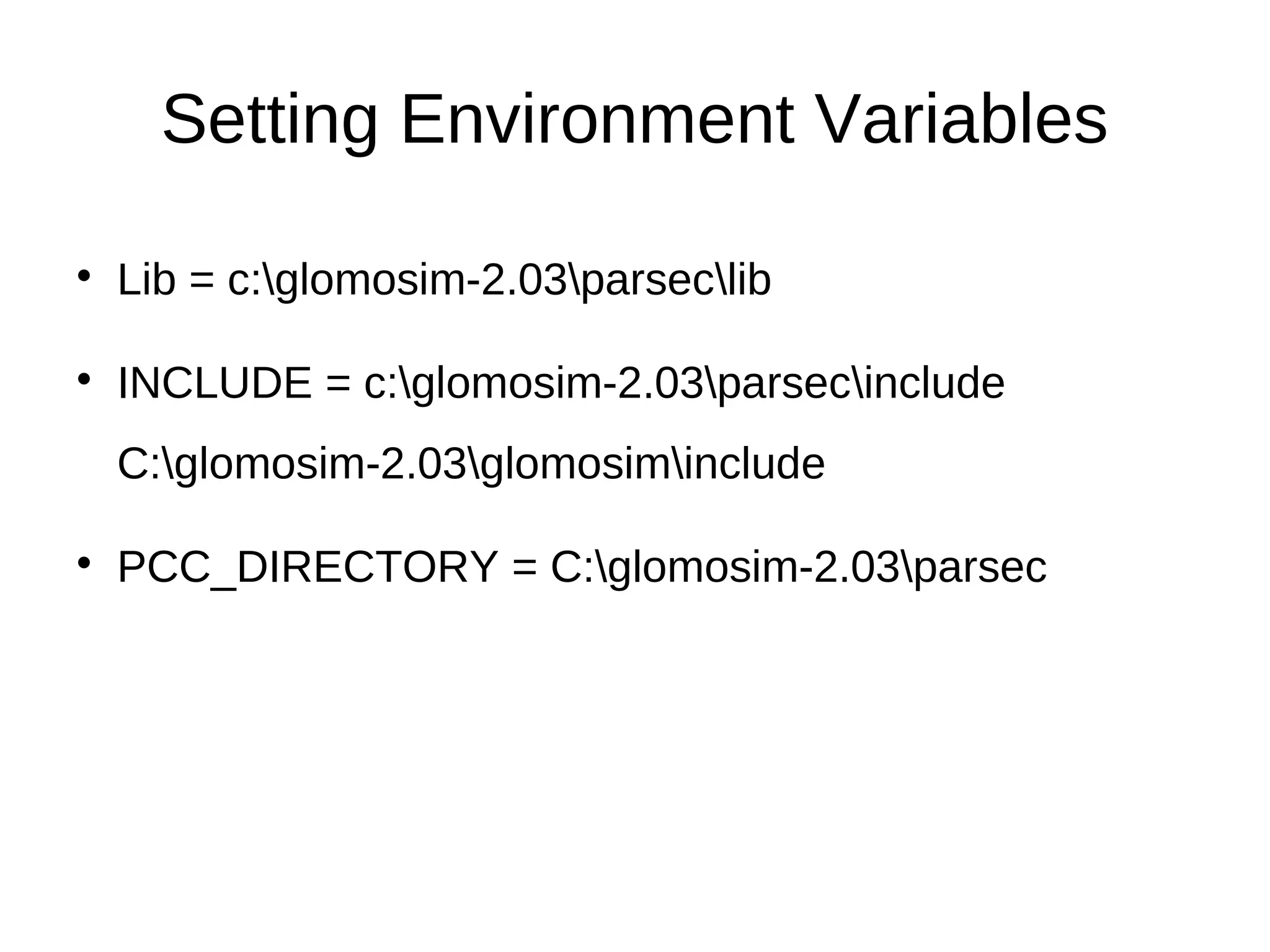
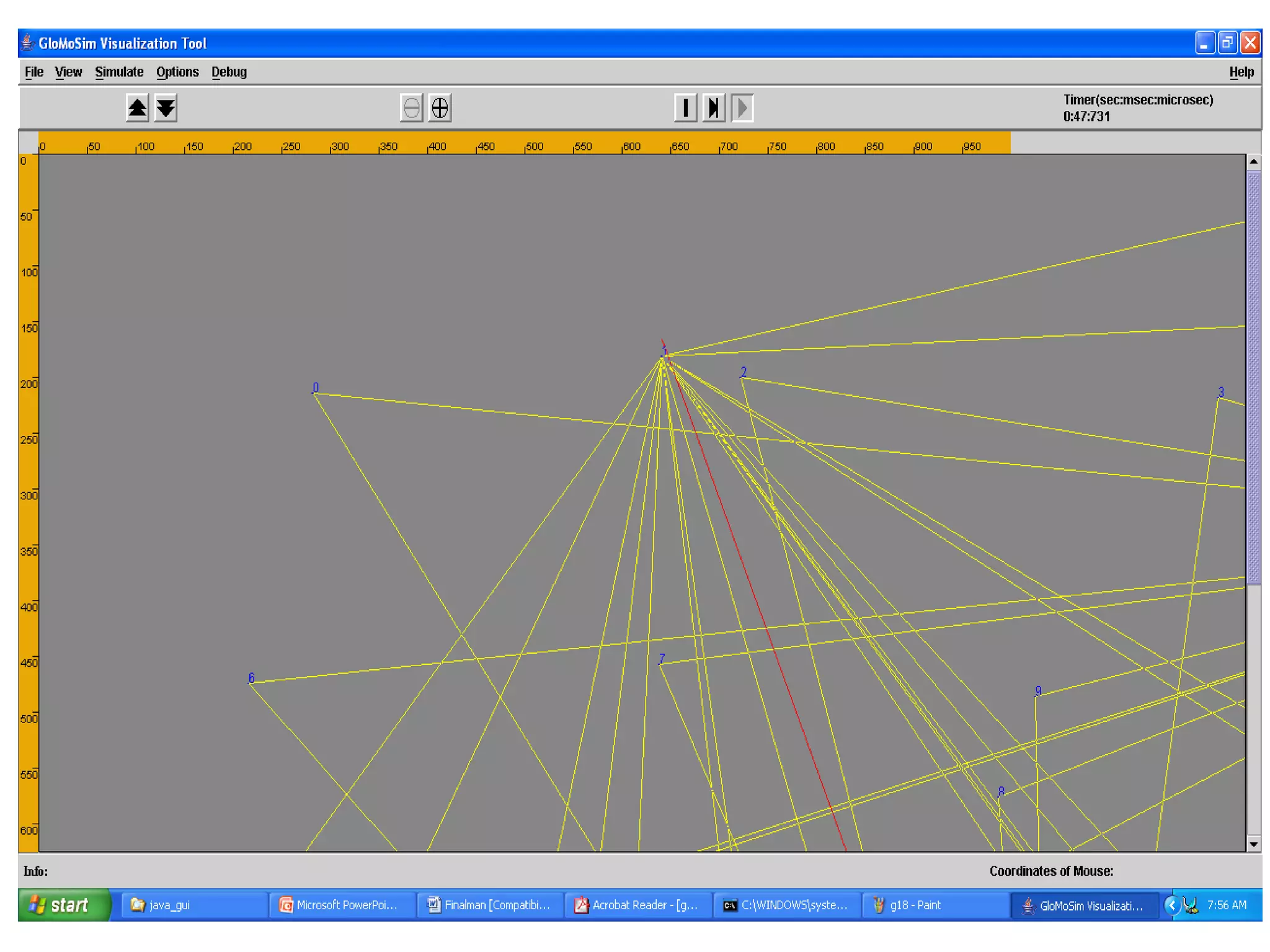
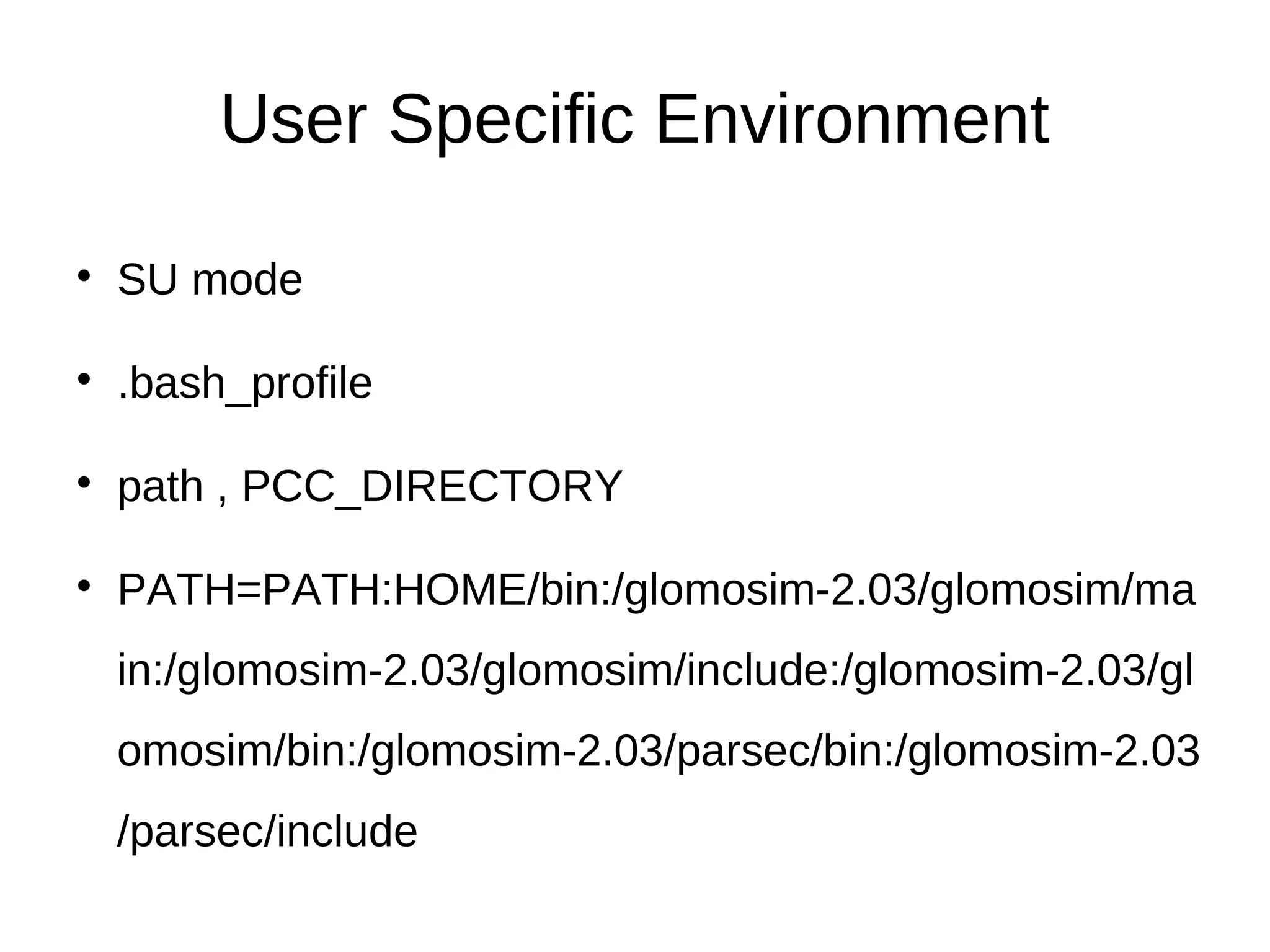
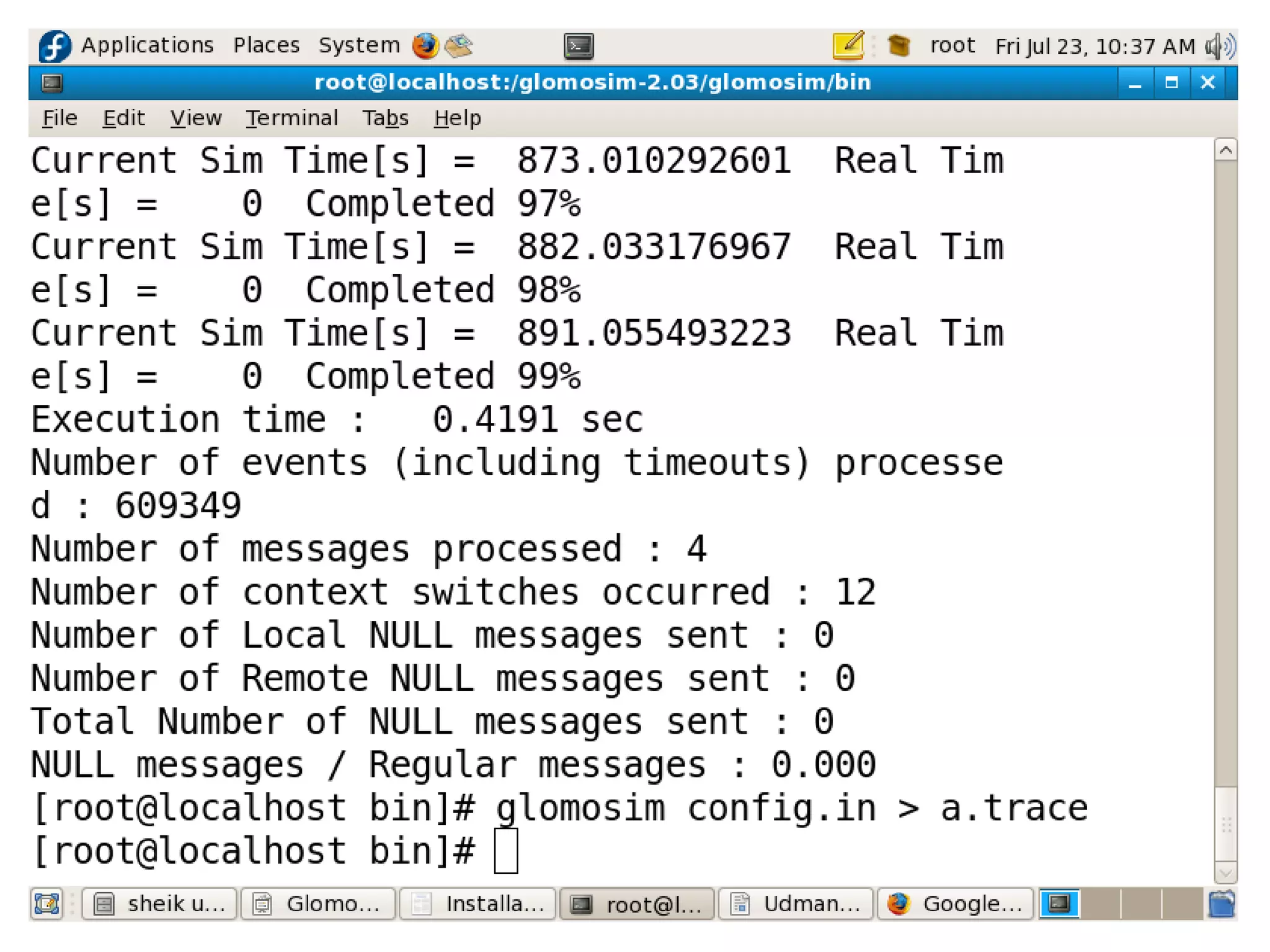
This document provides information about installing and using GloMoSim, a scalable simulation environment for large wireless and wired communication networks. It describes the key layers in GloMoSim including radio, MAC, network, transport and application layers. It also outlines the modular GloMoSim library and supported protocols. The document explains how to install GloMoSim on Windows by setting environment variables and extracting files, and on Unix/Linux by customizing environment variables and running make files.