This document discusses various identifiers used in GSM networks, including:
- The International Mobile Station Equipment Identity (IMEI) uniquely identifies mobile devices.
- The International Mobile Subscriber Identity (IMSI) identifies subscribers and includes information like mobile country code, network code, and subscriber number.
- The Mobile Subscriber ISDN Number (MSISDN) is the phone number assigned to a subscriber's SIM card.
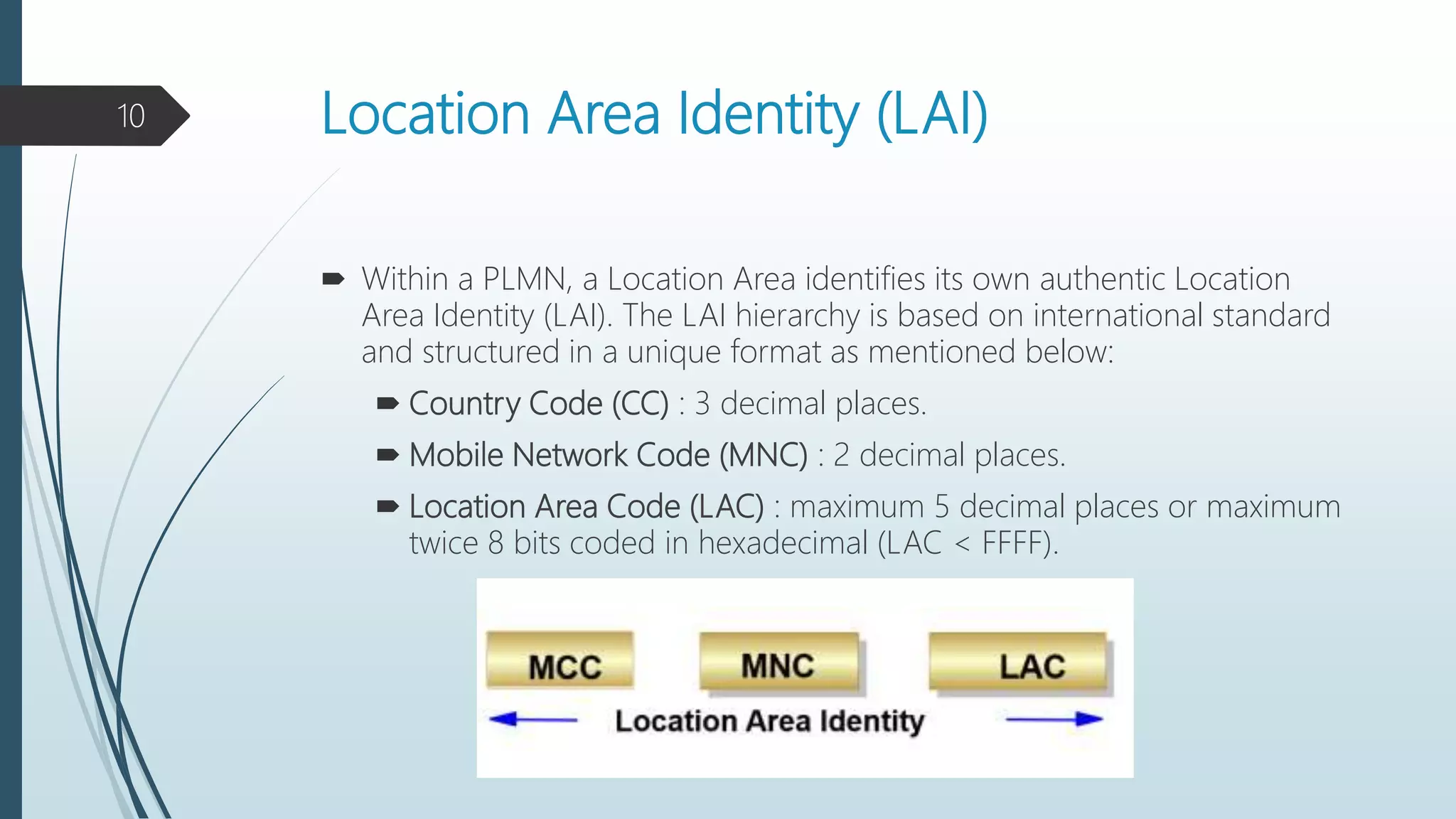
It also covers temporary identifiers assigned for mobility like the Temporary Mobile Subscriber Identity (TMSI) and location identifiers like the Location Area Identity (LAI) and Cell Identifier (CI).