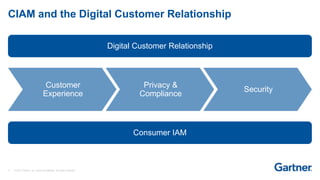
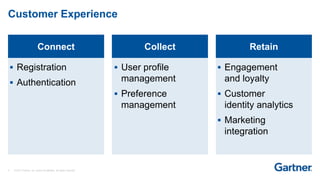
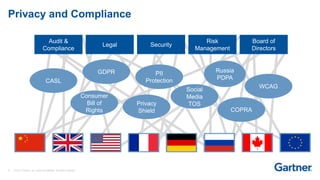
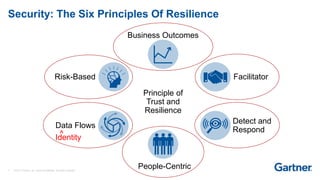
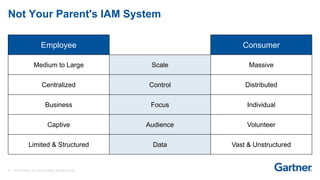
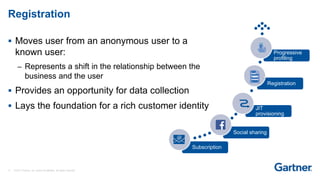
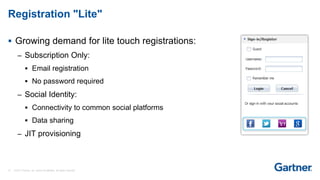
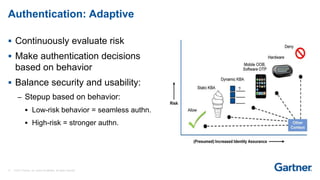
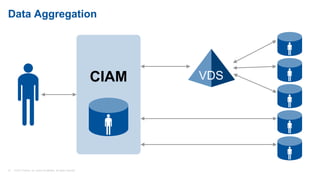
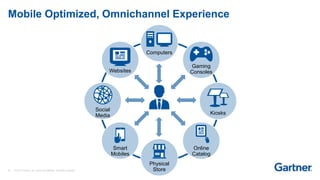
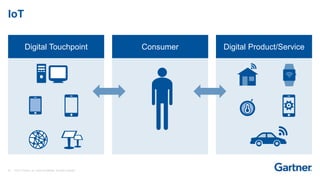
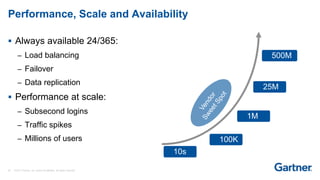
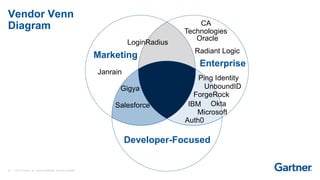
This presentation discusses consumer identity and access management (CIAM) and its importance in digital transformation. CIAM enables digital customer experiences by allowing customers to register and authenticate across channels while protecting privacy and security. The presentation covers key CIAM features like registration, authentication, user profile management and their architectural considerations. It also provides an overview of the CIAM market landscape.