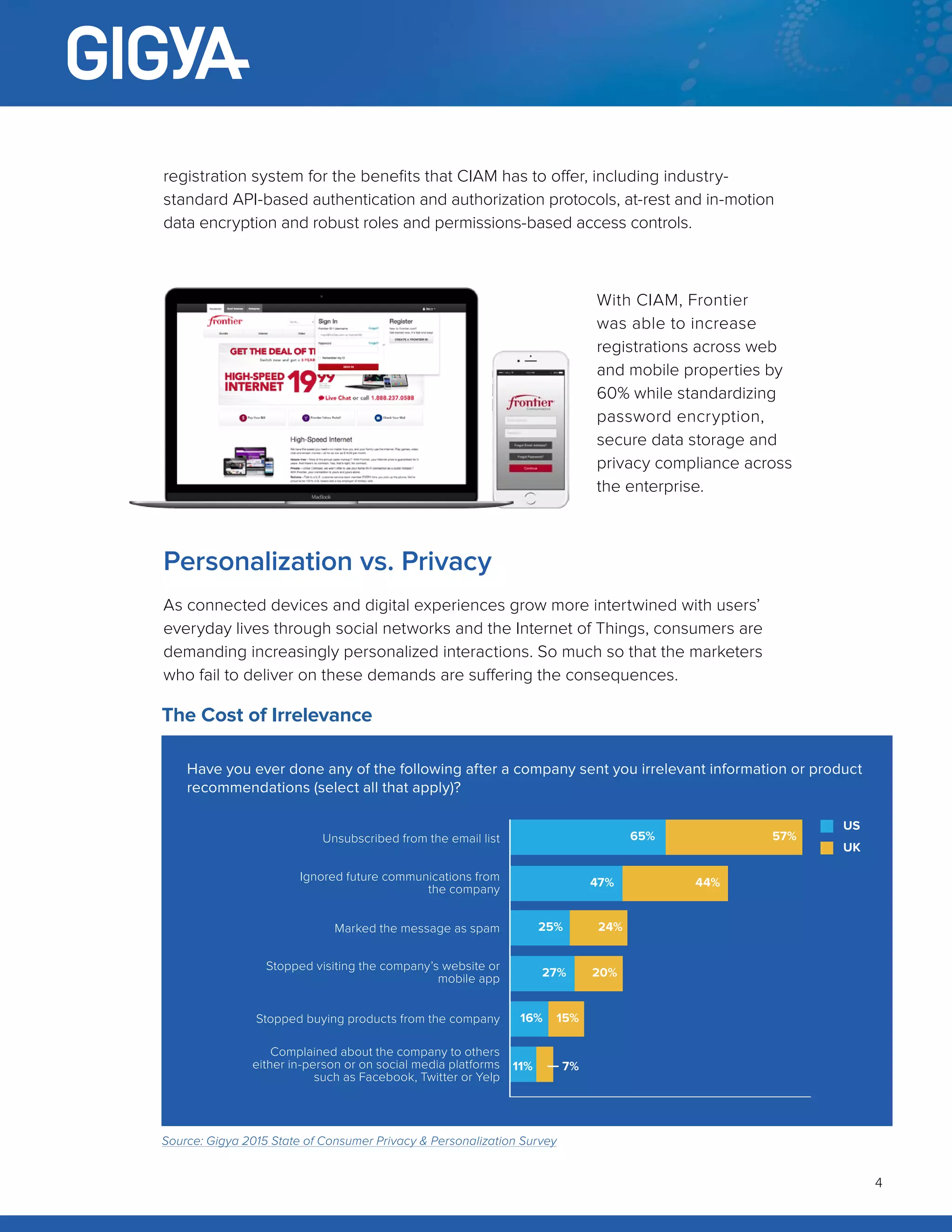
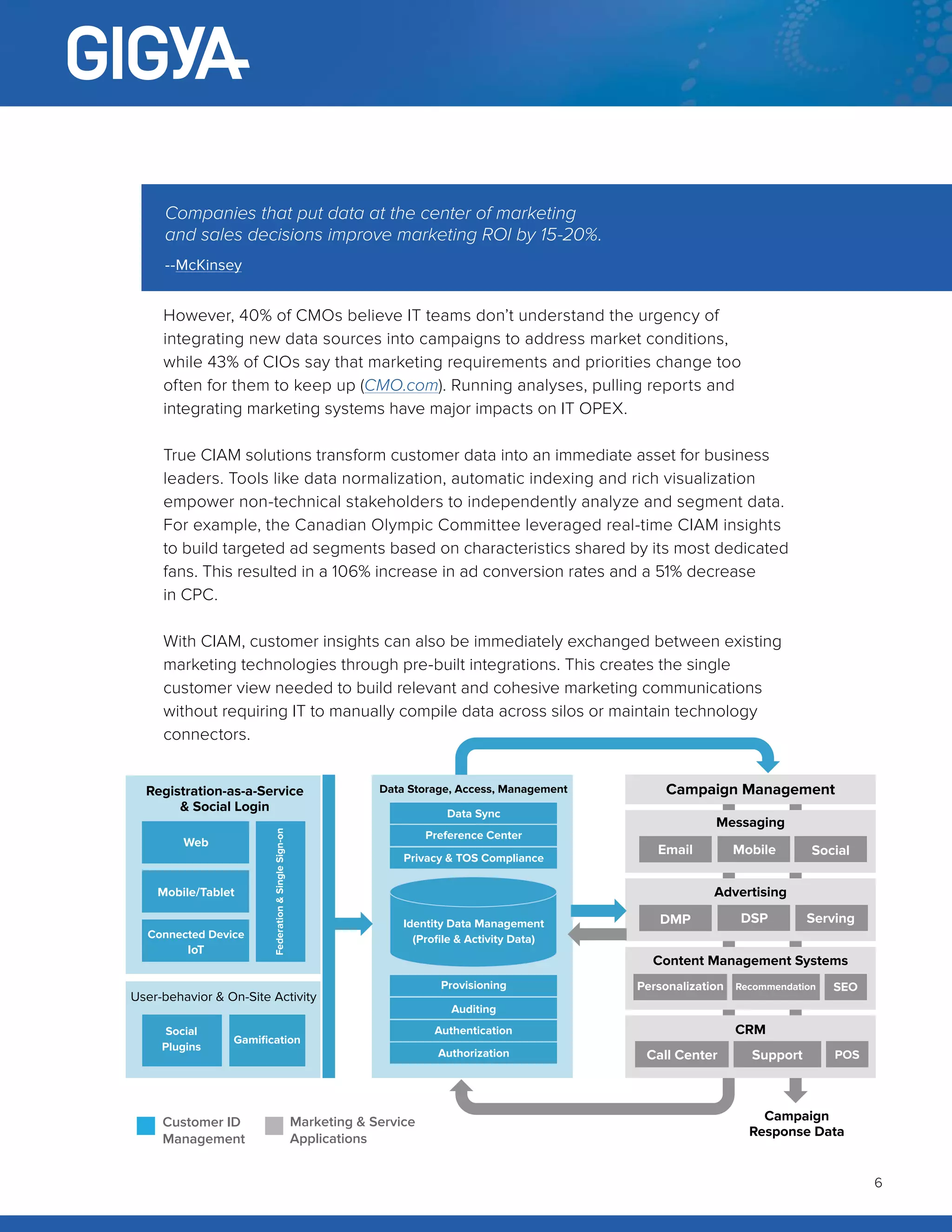
The document discusses the need for collaboration between marketing and IT through Customer Identity and Access Management (CIAM) to enhance customer engagement while addressing usability, privacy, and agility in a secure manner. It highlights the challenges both departments face in managing customer data and ensuring privacy compliance, emphasizing CIAM as a solution that balances personalization and security. By leveraging CIAM, businesses can improve customer experiences and marketing effectiveness, ultimately driving growth and innovation.