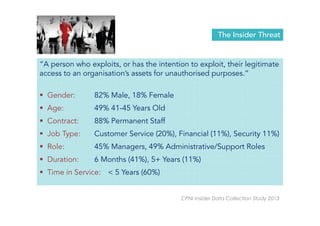
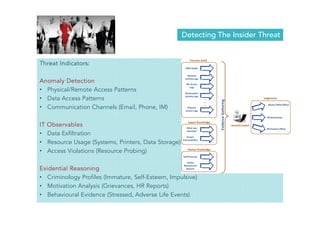
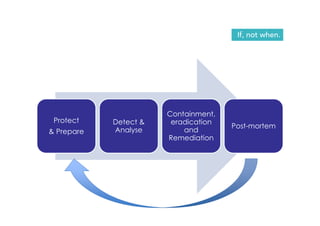
David Crozier discusses the vision for establishing a global innovation hub in cyber security, emphasizing the need for enhanced value creation and capacity building in the industry. The document outlines various cyber threats, their motivations, and profiles of potential insider threats, as well as the importance of compliance beyond basic standards. It also highlights the growth potential of the cybersecurity market and the need for collaborative industry-government initiatives to improve situational awareness and incident reporting.