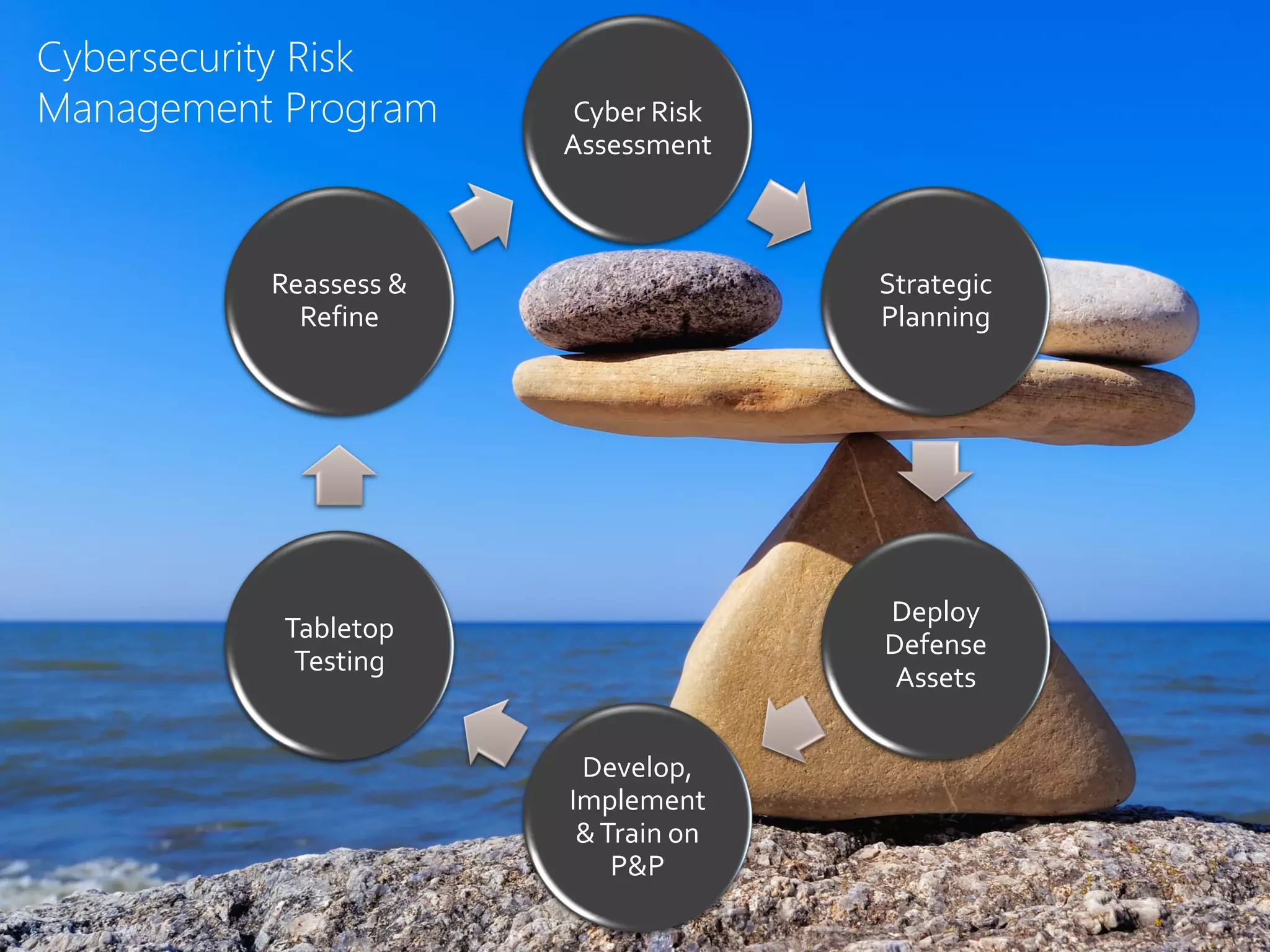
The document emphasizes the inevitability of cyber attacks on companies, particularly small to medium-sized businesses (SMBs), illustrating the significant costs associated with data breaches and highlighting the legal obligations companies face regarding data protection. It discusses best practices for cybersecurity, the legal responsibilities of corporate officers, and the necessity for comprehensive response plans and cyber insurance. The document serves as an educational resource on the importance of proactive cybersecurity measures and legal compliance to mitigate risks and liabilities.






























![www.solidcounsel.com
Officer & Director Liability
“[B]oards that choose to ignore, or minimize, the
importance of cybersecurity oversight responsibility, do
so at their own peril.” SEC Commissioner Luis A. Aguilar, June 10,
2014.
Heartland Payment Systems, TJ Maxx, Target, Home Depot, Wyndham
Derivative claims premised on the harm to the company from data breach.
Caremark Claims:
Premised on lack of oversight = breach of the duty of loyalty and good faith
Cannot insulate the officers and directors = PERSONAL LIABILITY!
Standard:
(1) “utterly failed” to implement reporting system or controls; or
(2) “consciously failed” to monitor or oversee system.](https://image.slidesharecdn.com/dbacorporatecounselslideshare-160503032418/75/Cybersecurity-What-the-GC-and-CEO-Need-to-Know-34-2048.jpg)