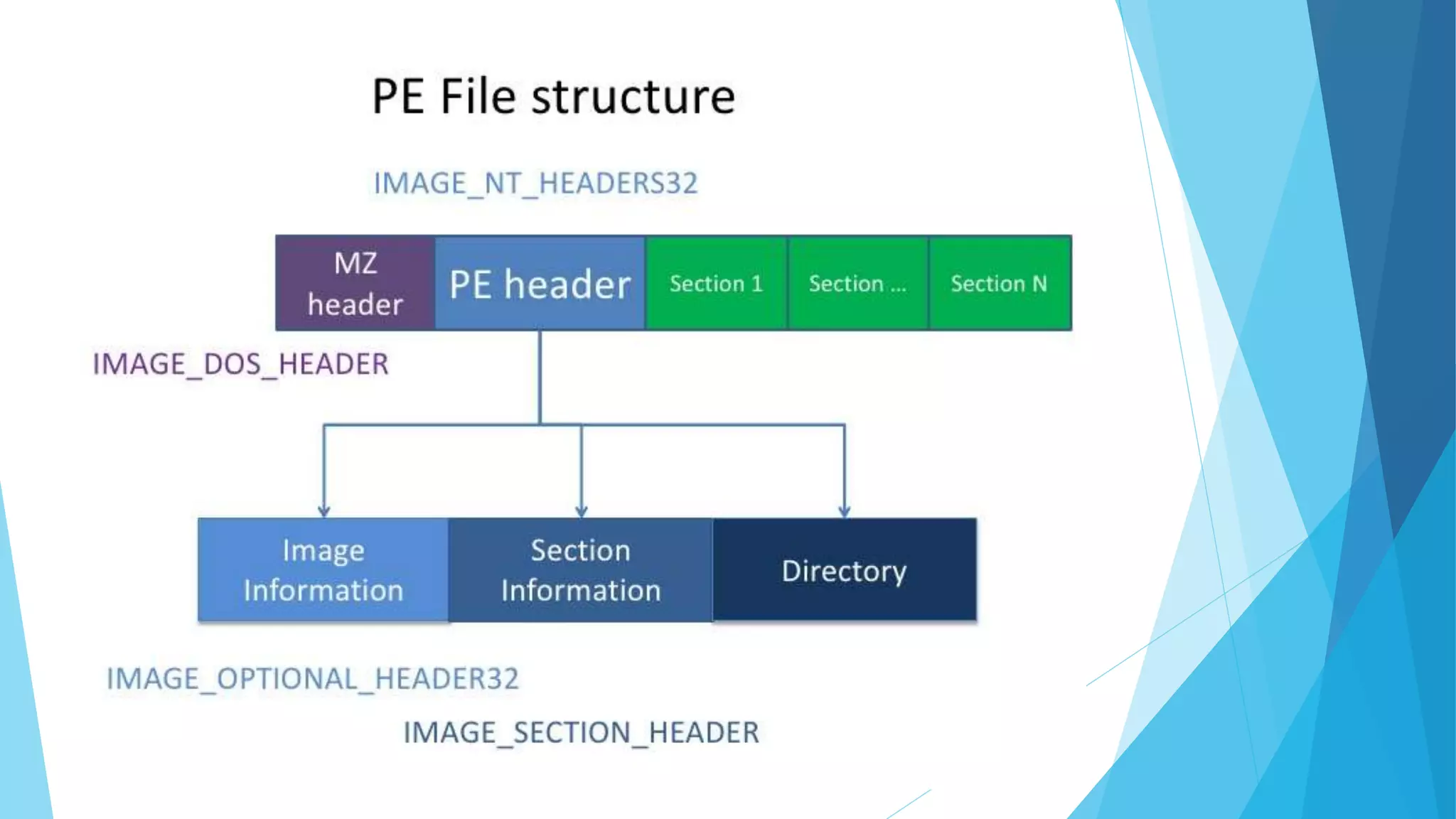
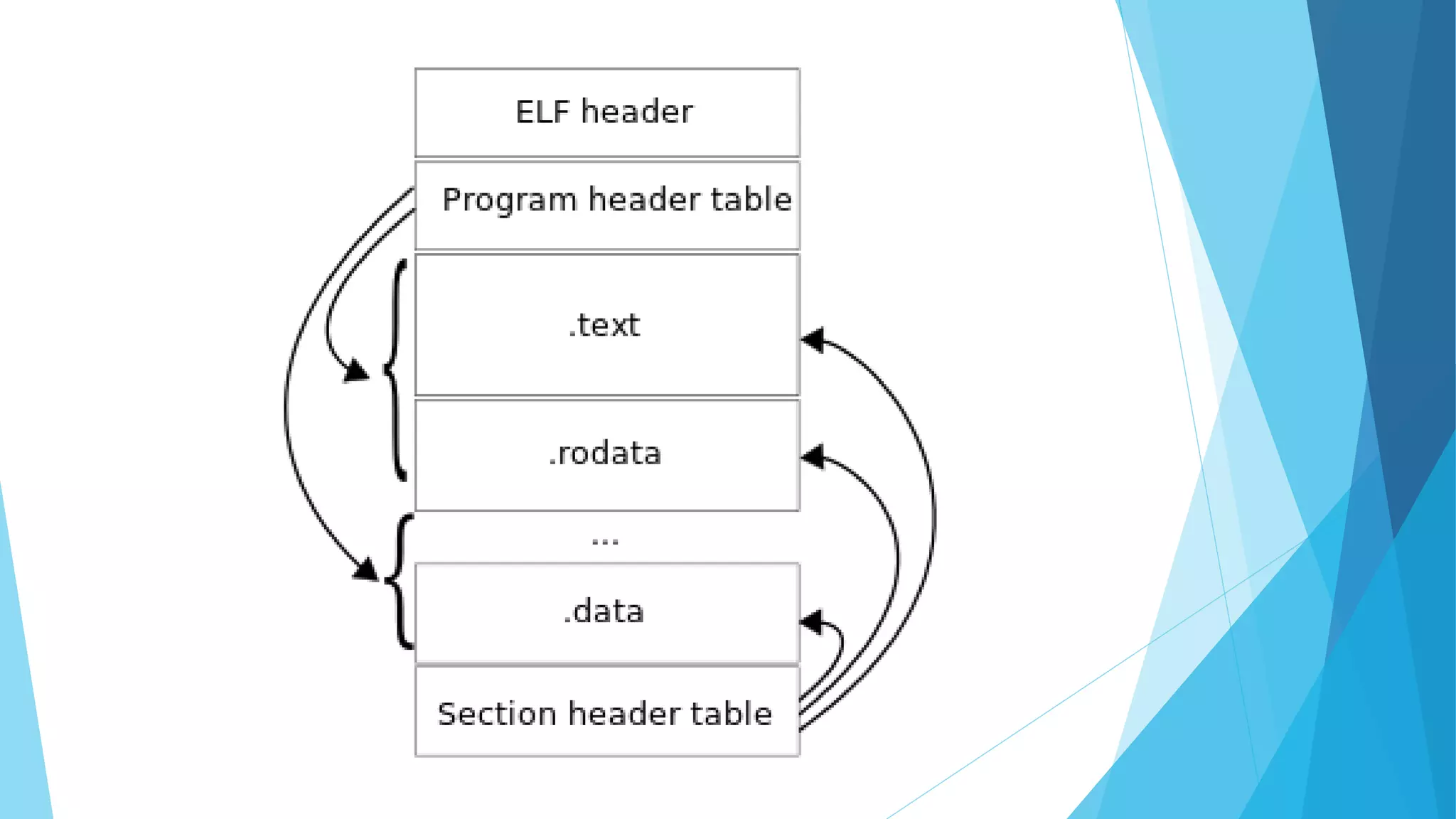
This presentation covers the fundamentals and motivations behind reverse engineering, emphasizing its educational purpose while noting legal implications. It explains key practices such as resource modification, control flow bypass, and code caving, as well as essential tools like hex editors, disassemblers, and debuggers. The document highlights the design patterns and programming language considerations involved in reverse engineering processes.