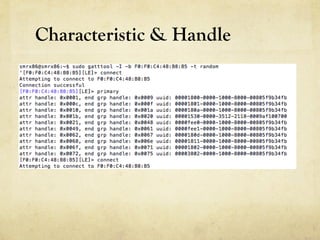
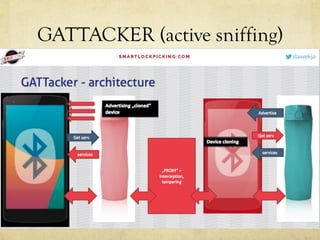
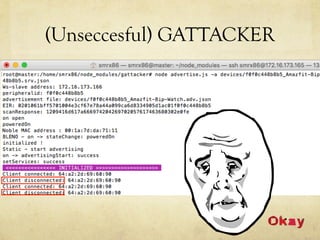
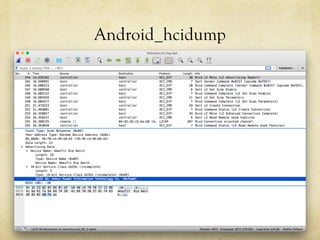
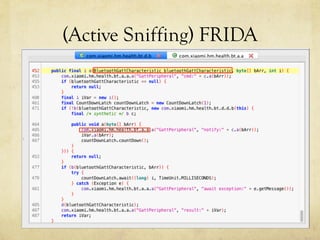
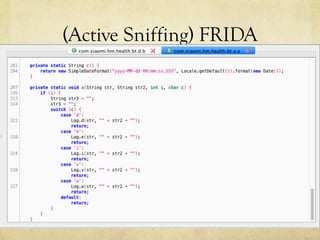
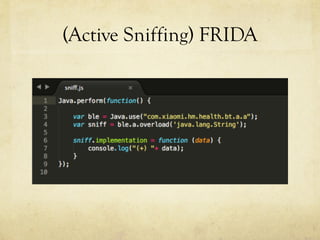
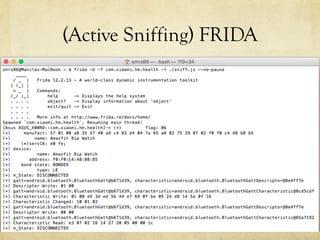
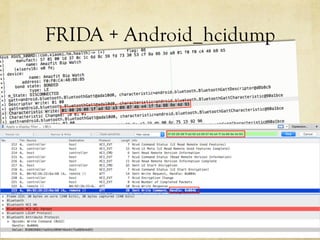
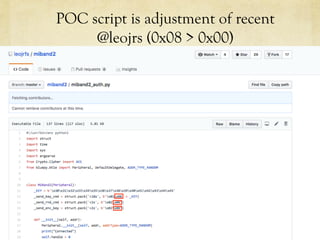
This document summarizes a presentation about hacking an Amazfit BIP smartwatch. It includes an agenda that covers basic BLE concepts, relevant research on BLE authentication, and exploiting the authentication of the Amazfit BIP. The speaker is introduced as an independent security researcher who enjoys challenging clients. Research papers on Mi Band 2 authentication and reversing BLE from Android apps are referenced. The presentation covers BLE communication layers, using GATTACKER and Android hcidump for active sniffing, and Frida to find the characteristic UUID and handle for authentication mapping. A proof of concept script is shown that adjusts a recent approach to change the authentication value.