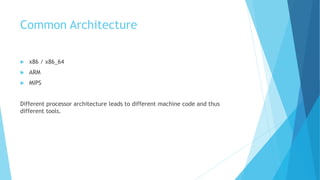
The presentation provides an overview of firmware reverse engineering, emphasizing its educational purpose and the legal implications of reverse engineering copyrighted material. It explains the difference between bare-metal and full firmware, outlines common steps in the reverse engineering process, and lists tools used for information gathering, extraction, and analysis. The session focuses on full firmware, detailing elements such as bootloaders, kernels, and applications involved in the reverse engineering ecosystem.