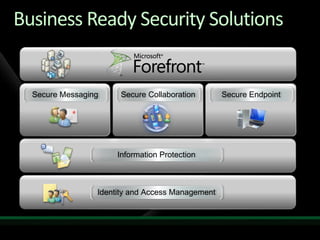
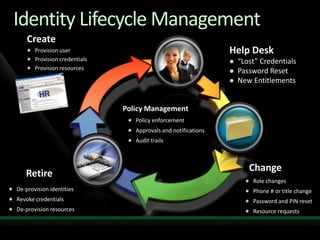
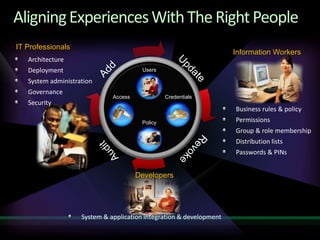
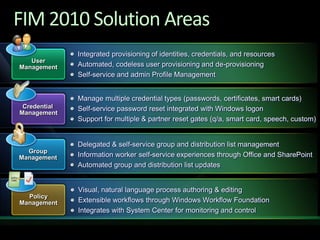
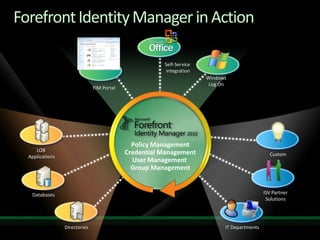
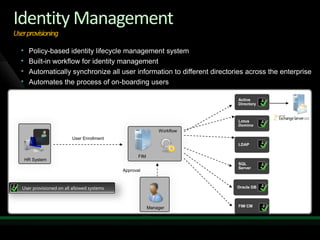
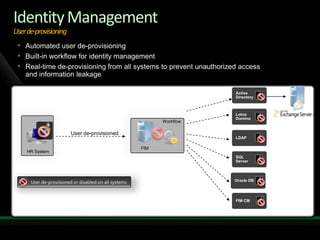
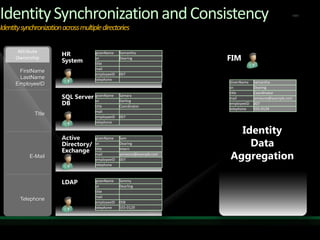
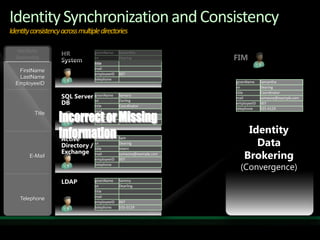
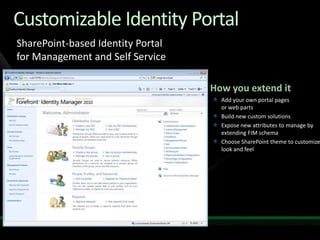
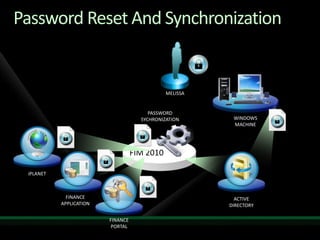
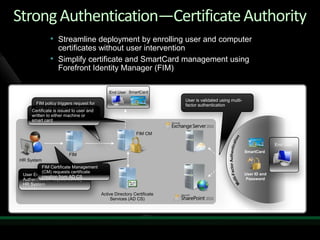
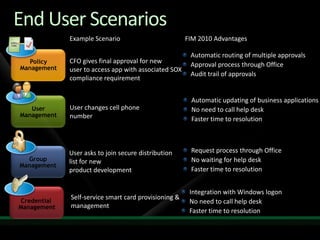
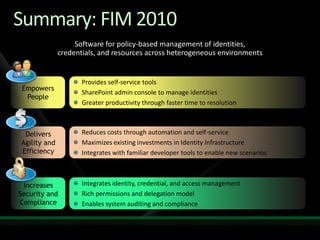
This document discusses identity and access management solutions using Forefront Identity Manager 2010. It describes how FIM 2010 can automate user provisioning and deprovisioning, manage credentials and groups, implement security policies, and provide self-service identity management portals. FIM 2010 integrates with directories, applications, and devices to synchronize identity data and apply policies consistently across heterogeneous environments.