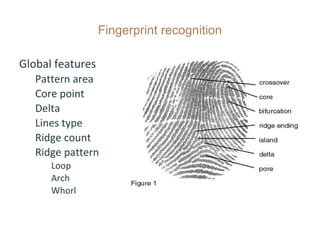
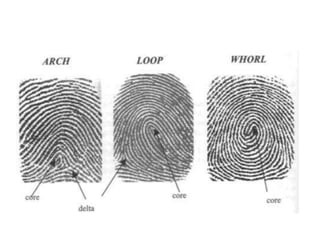
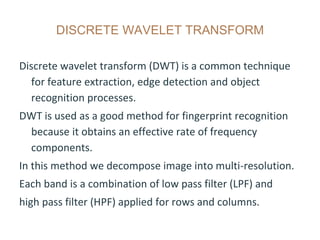
The document discusses an effective fingerprint recognition approach utilizing double fingerprints, emphasizing the importance of biometric systems for individual verification. It details the fingerprint recognition process, including data collection, preprocessing, enhancement, and feature extraction using discrete wavelet transform. The findings indicate that hybridizing features from different fingerprints significantly improves recognition accuracy and processing time.