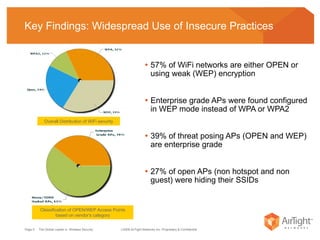
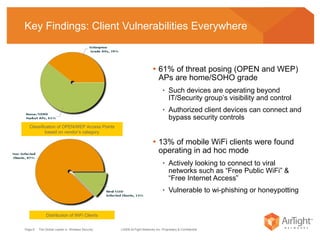
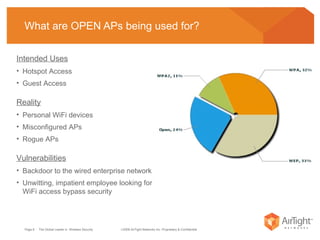
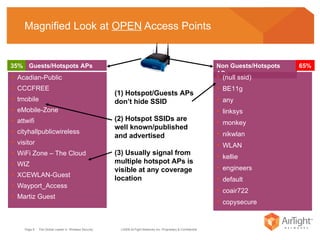
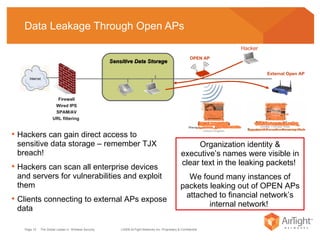
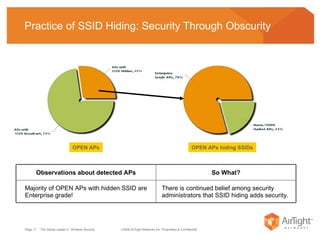
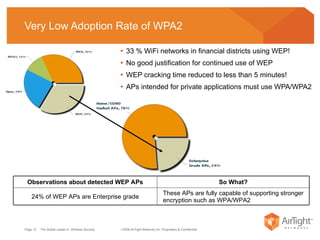
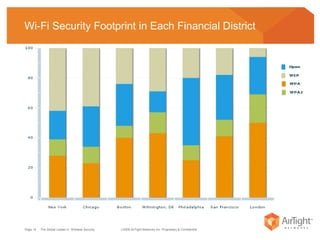
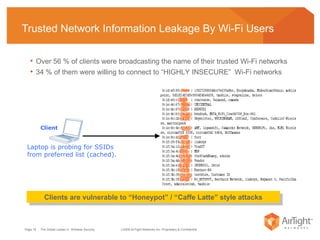
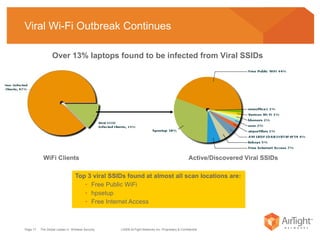
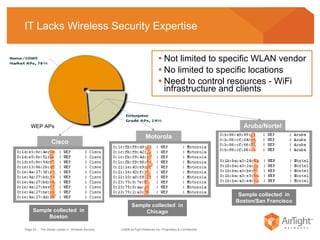
The document summarizes the key findings of a wireless vulnerability study conducted across 7 major financial districts. The study found that 57% of wireless networks used insecure encryption methods like open or WEP. It also found client devices vulnerable to attacks from openly connecting to untrusted networks and 13% actively searching for viral hotspots. The conclusions recommend best practices like implementing wireless intrusion prevention and monitoring, strong authentication and encryption, and securing guest access.