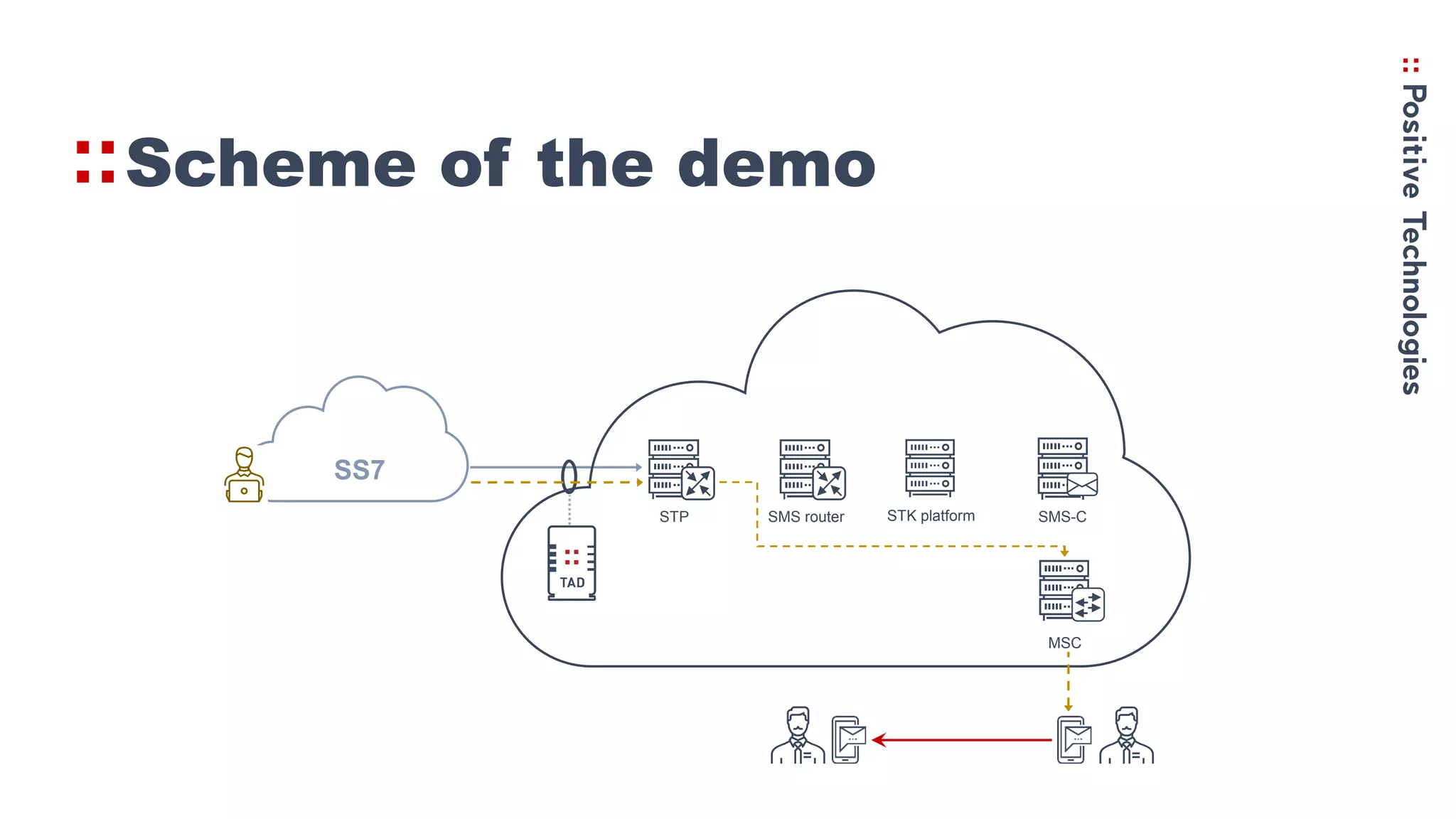
Simjacker is a vulnerability that allows hackers to exploit SMS commands to gain control of mobile devices. The document discusses:
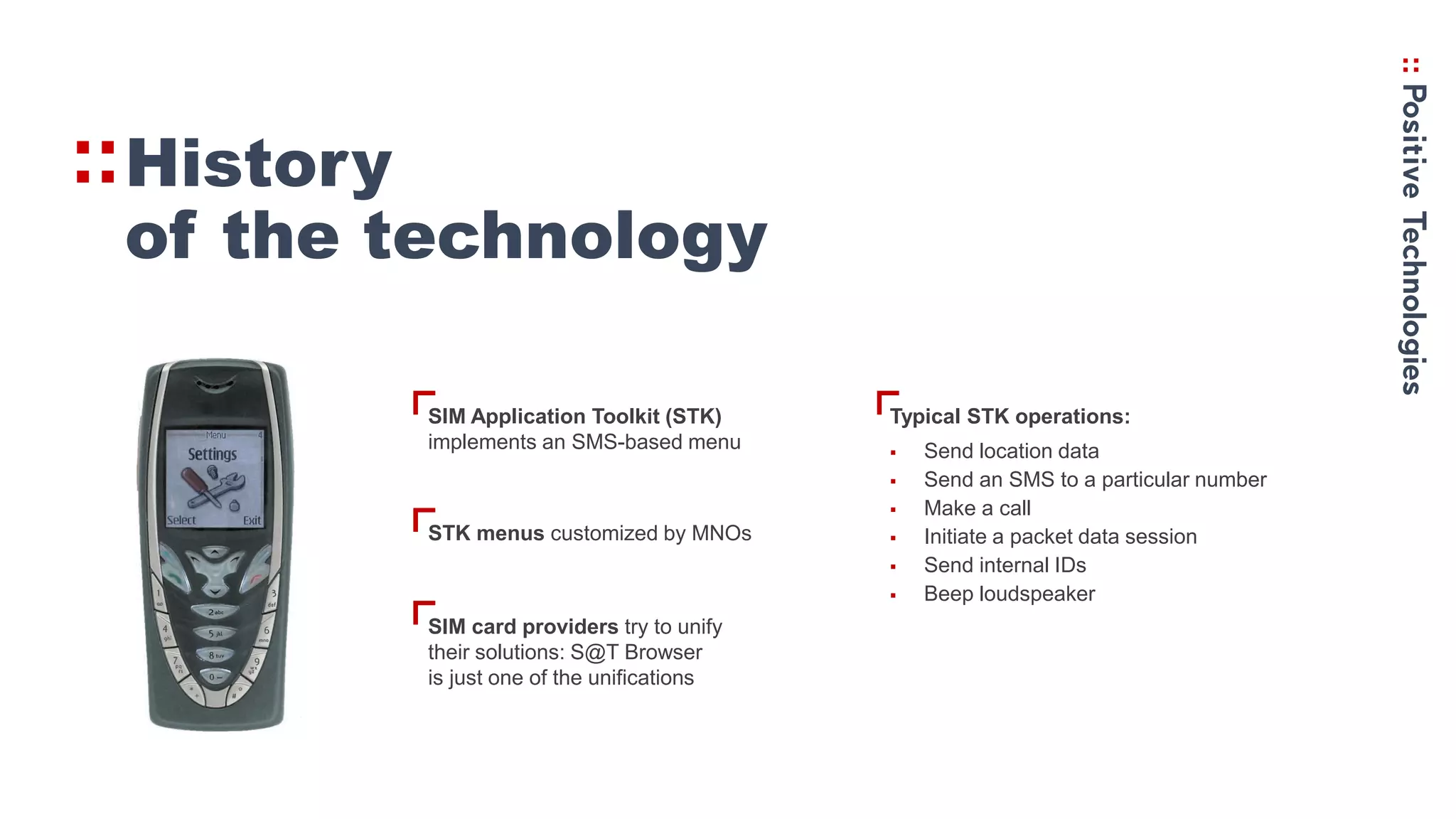
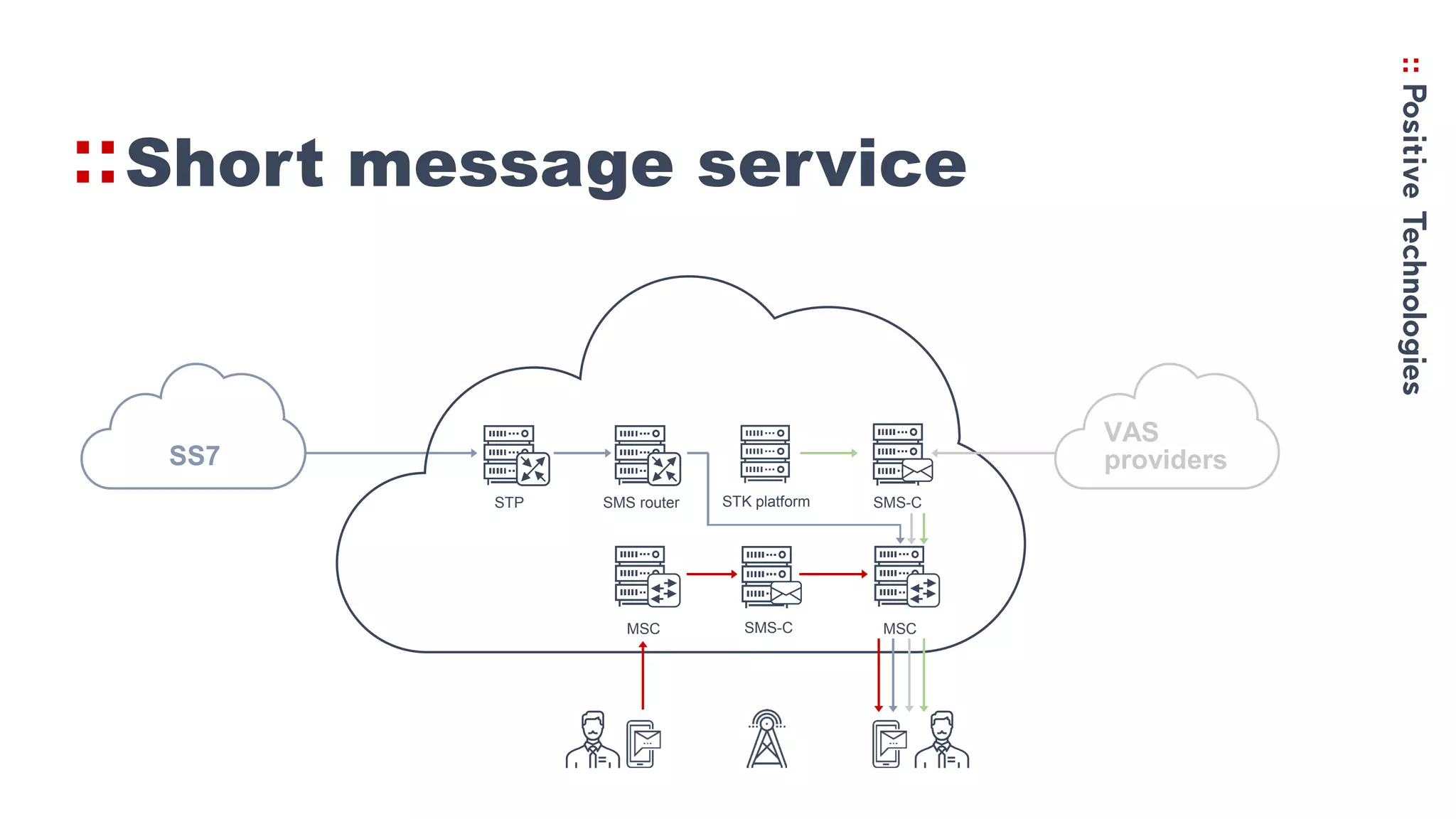
1. The history of STK and how it allows SMS-based menus and commands to be sent to SIM cards, including sending location data and making calls.
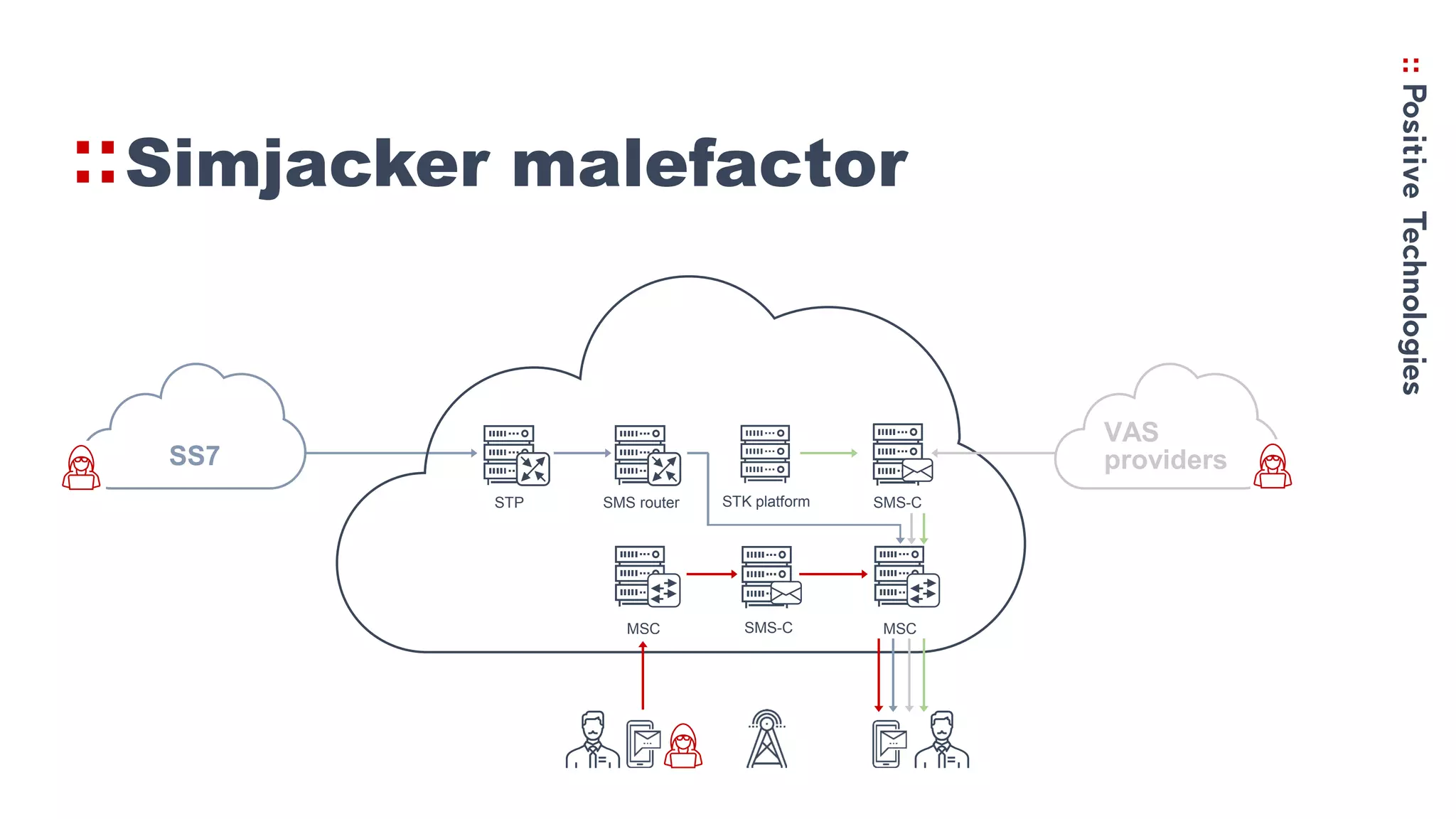
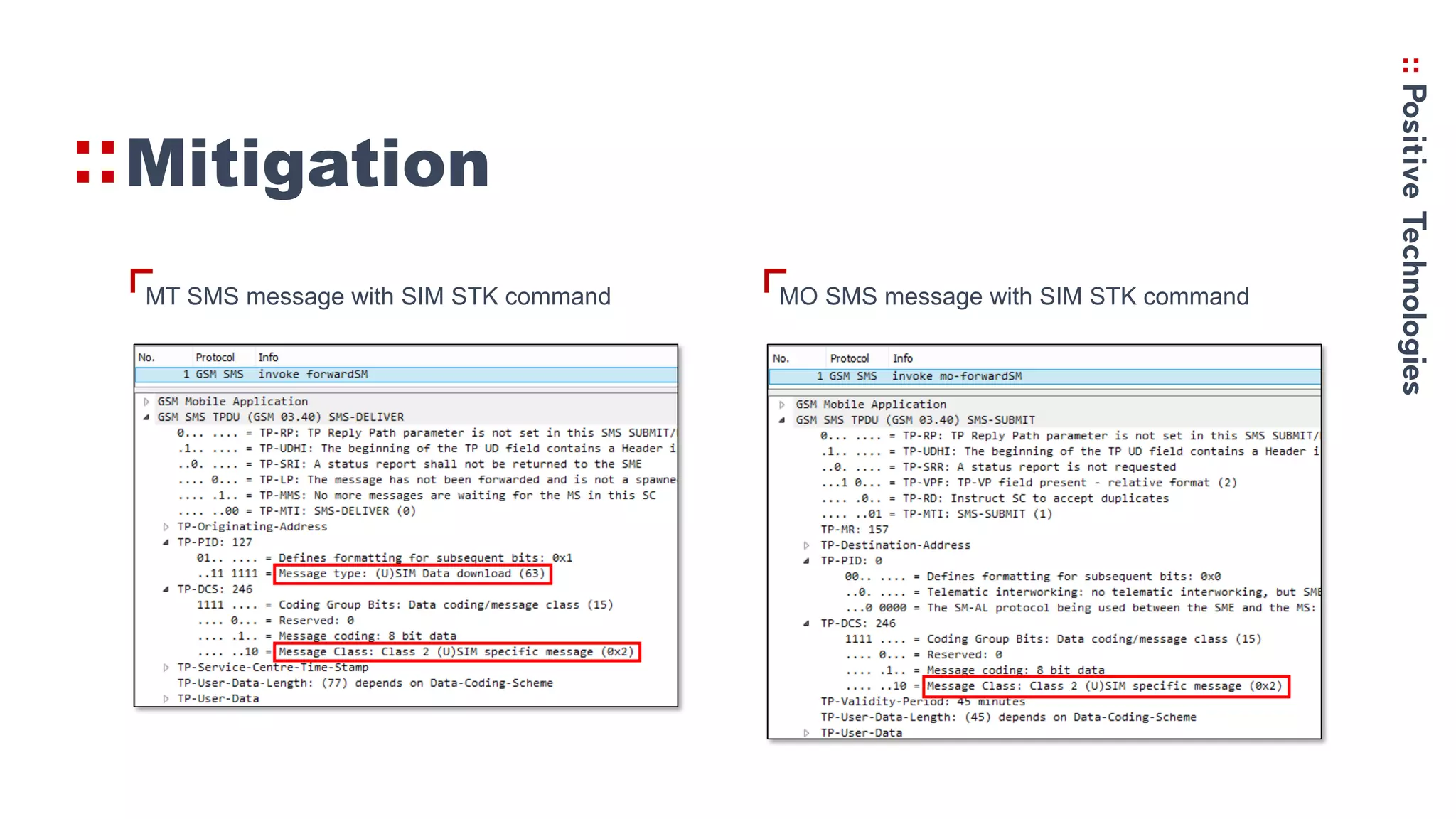
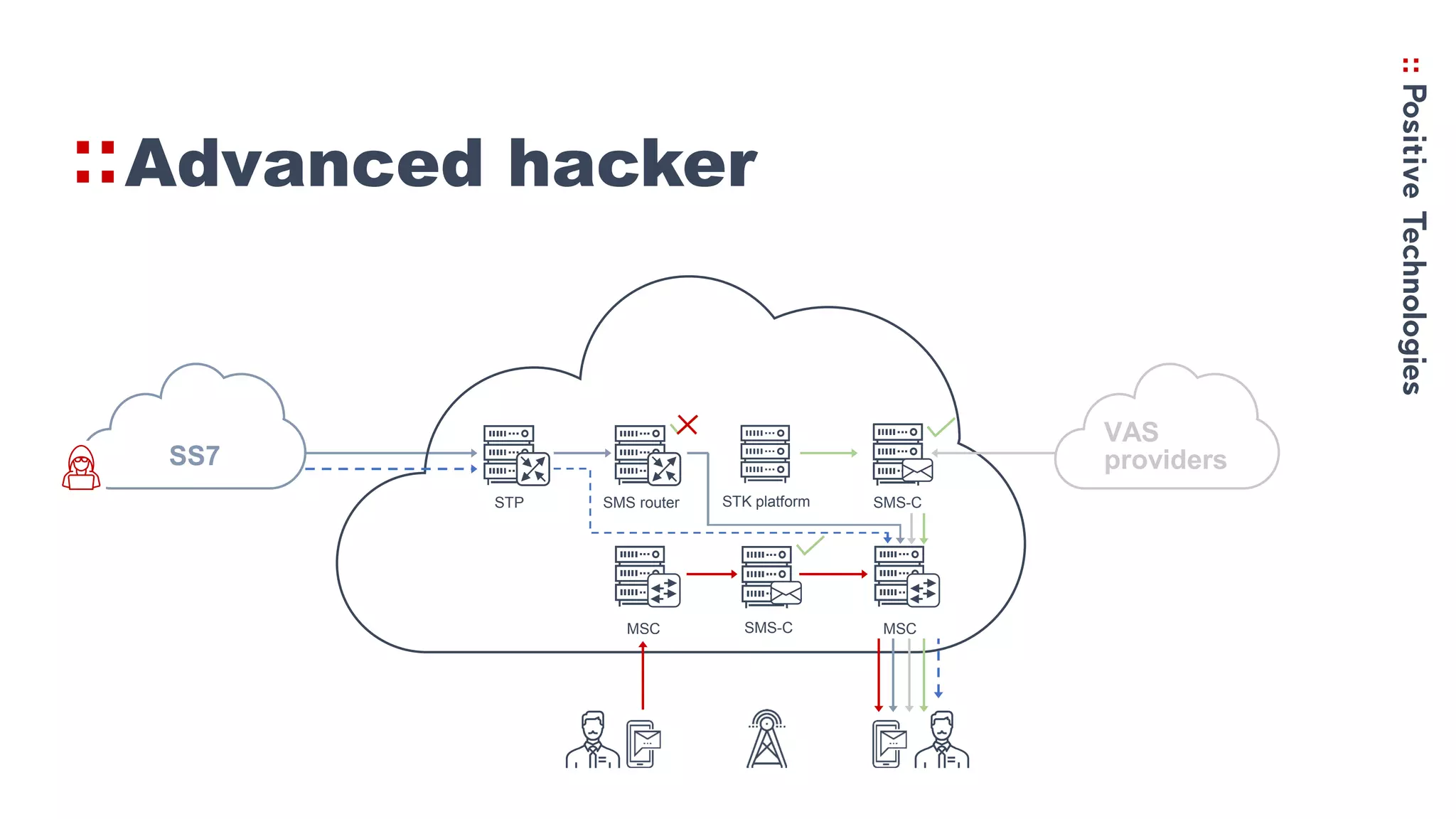
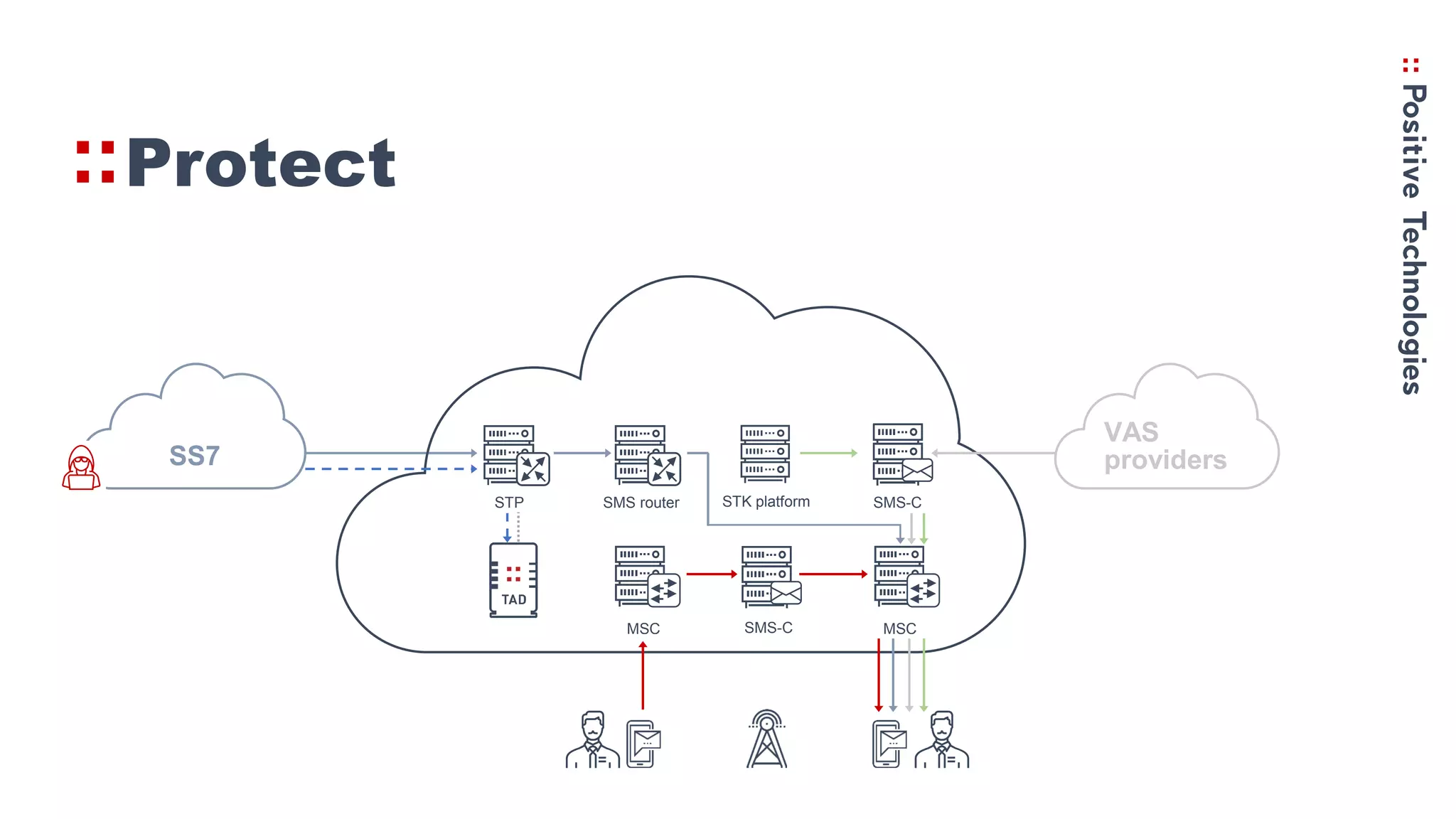
2. How the Simjacker vulnerability works by sending SMS commands from an unauthorized number or platform to exploit the STK functionality.
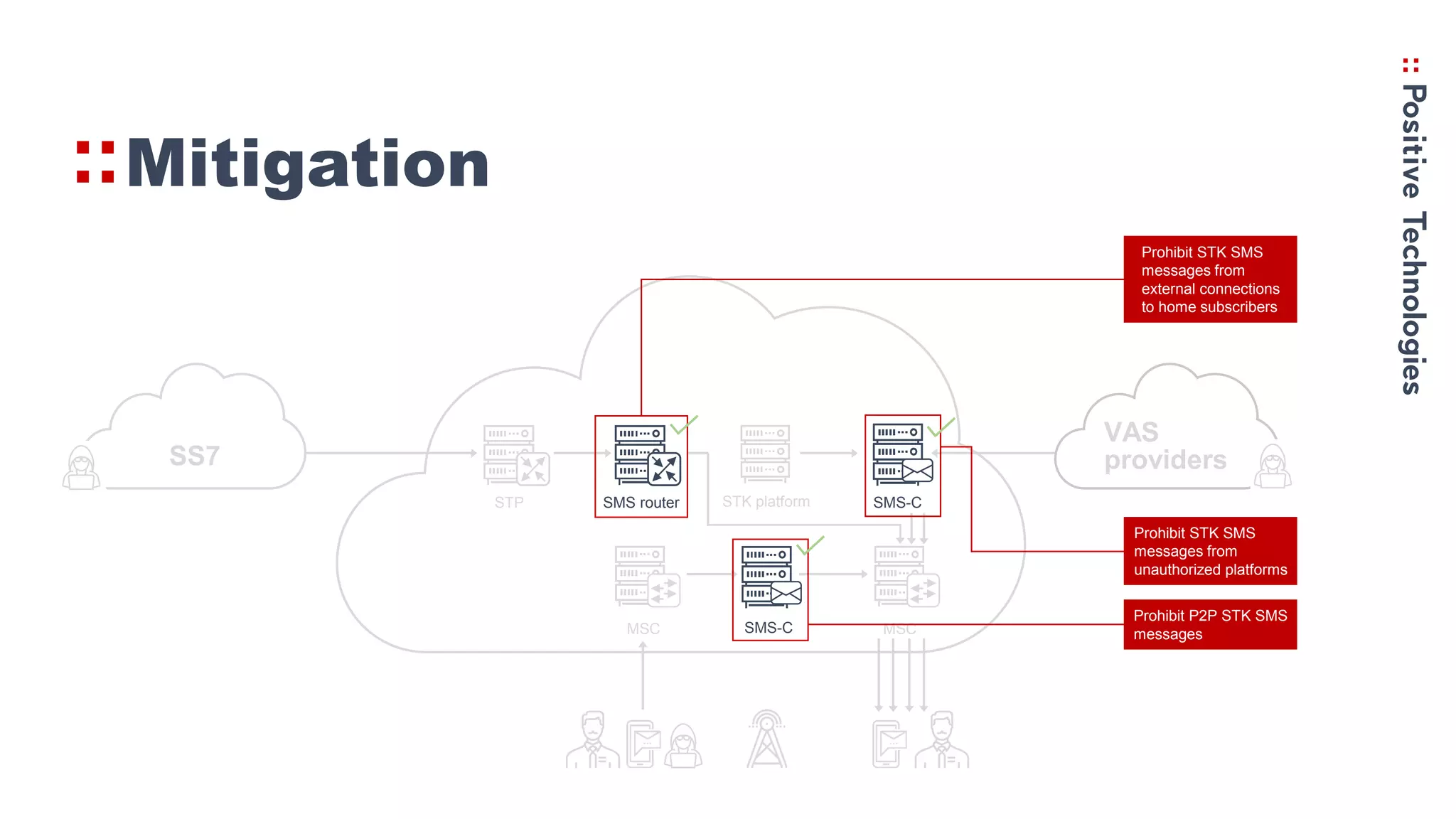
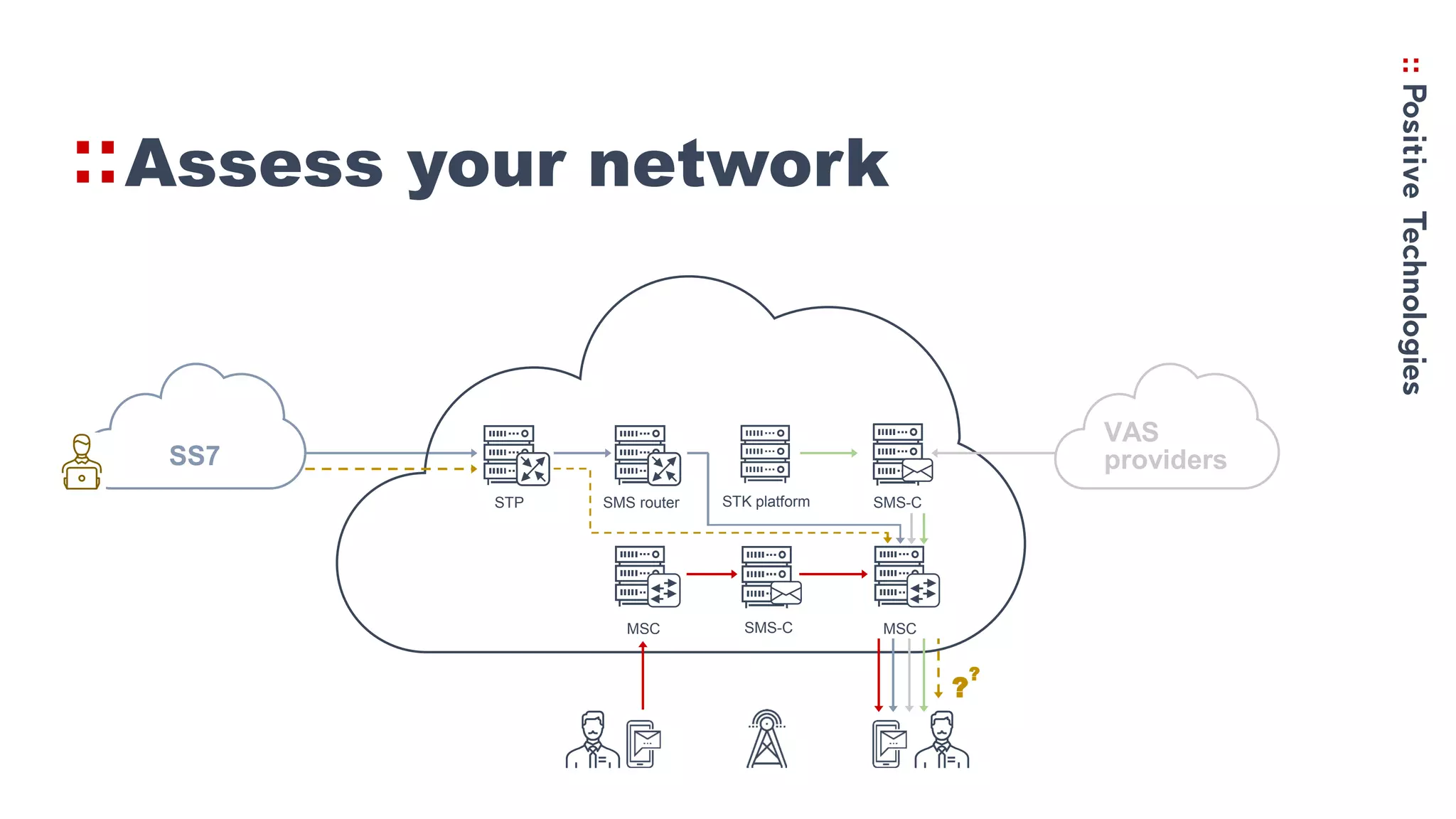
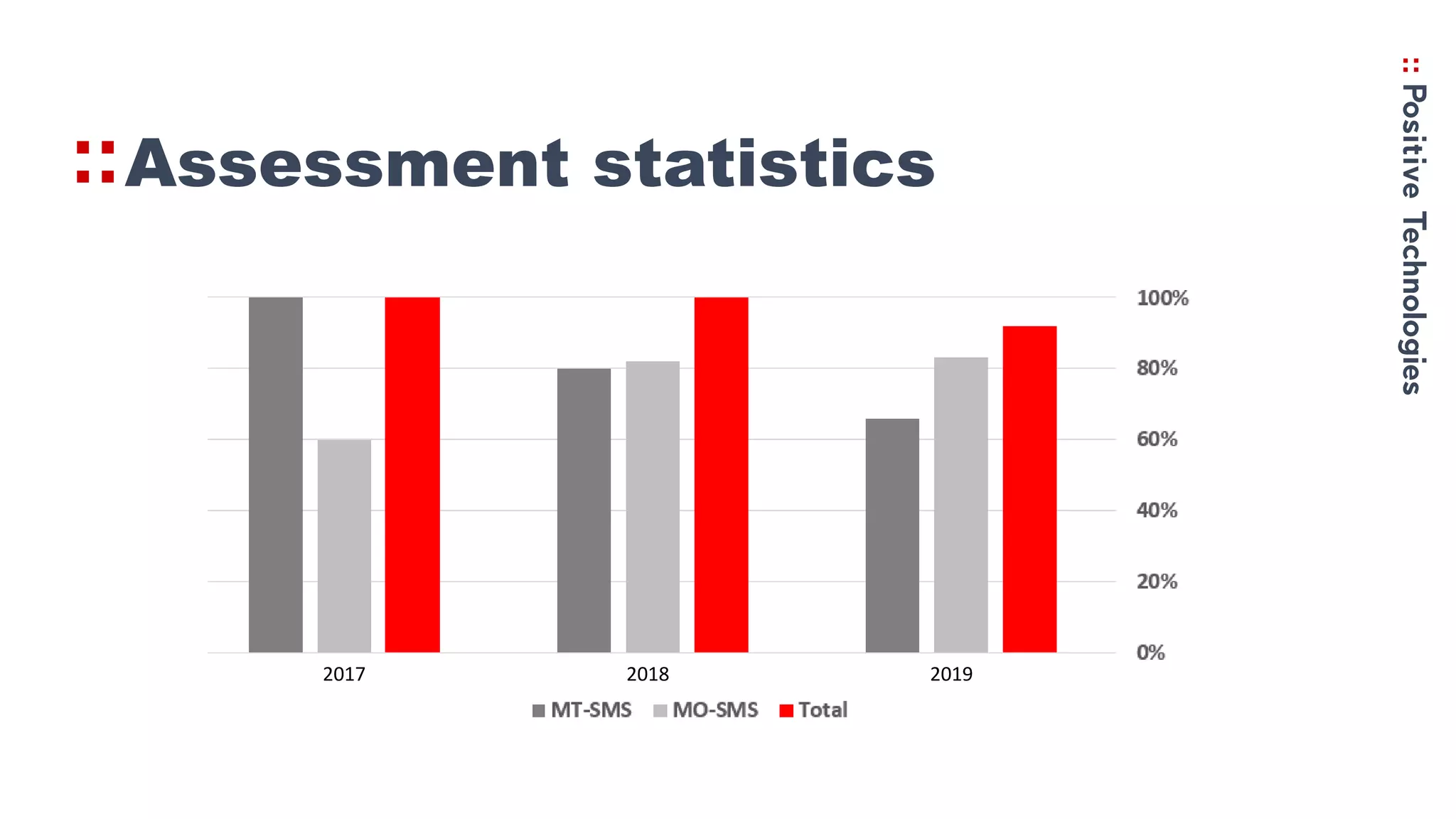
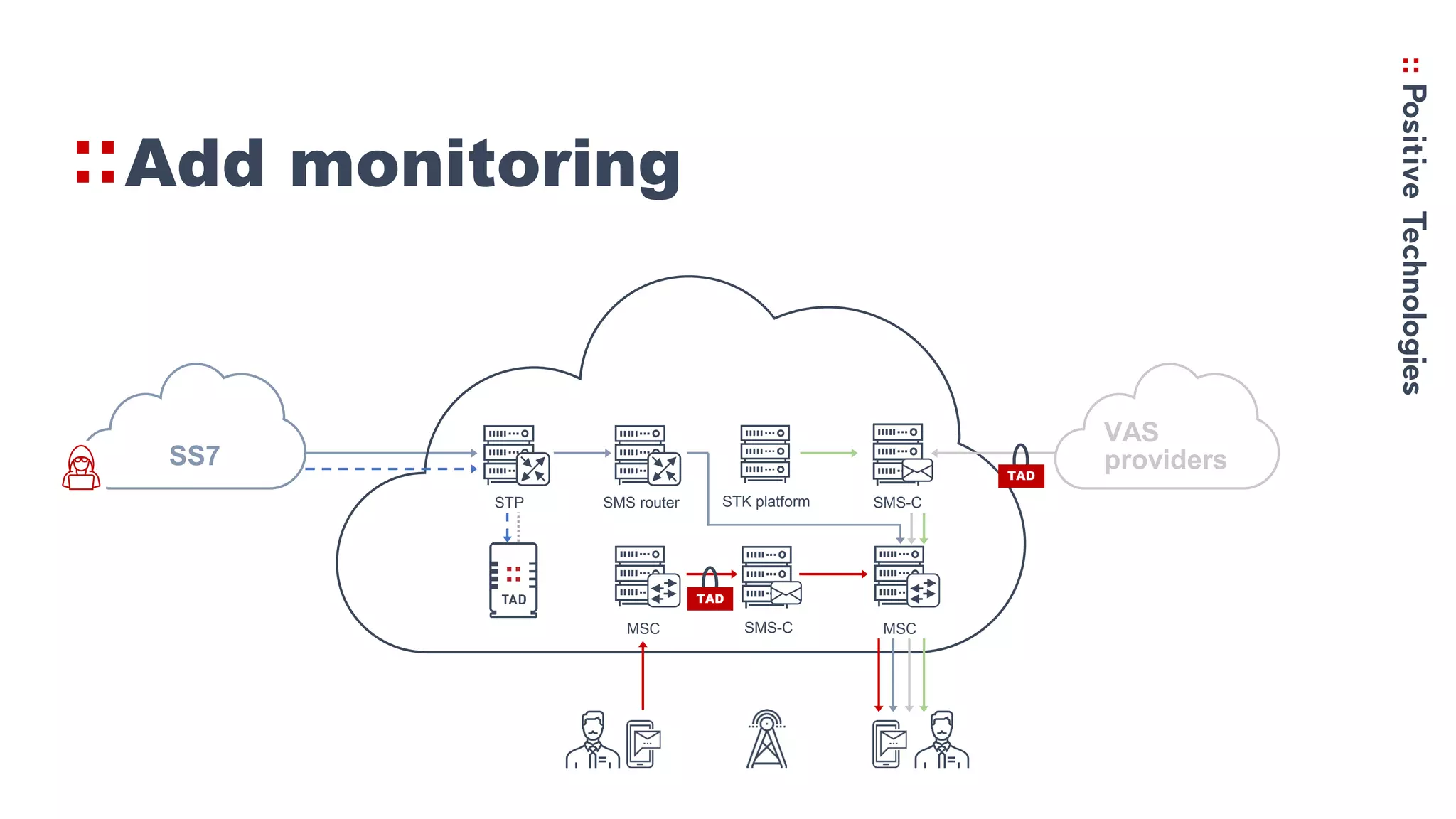
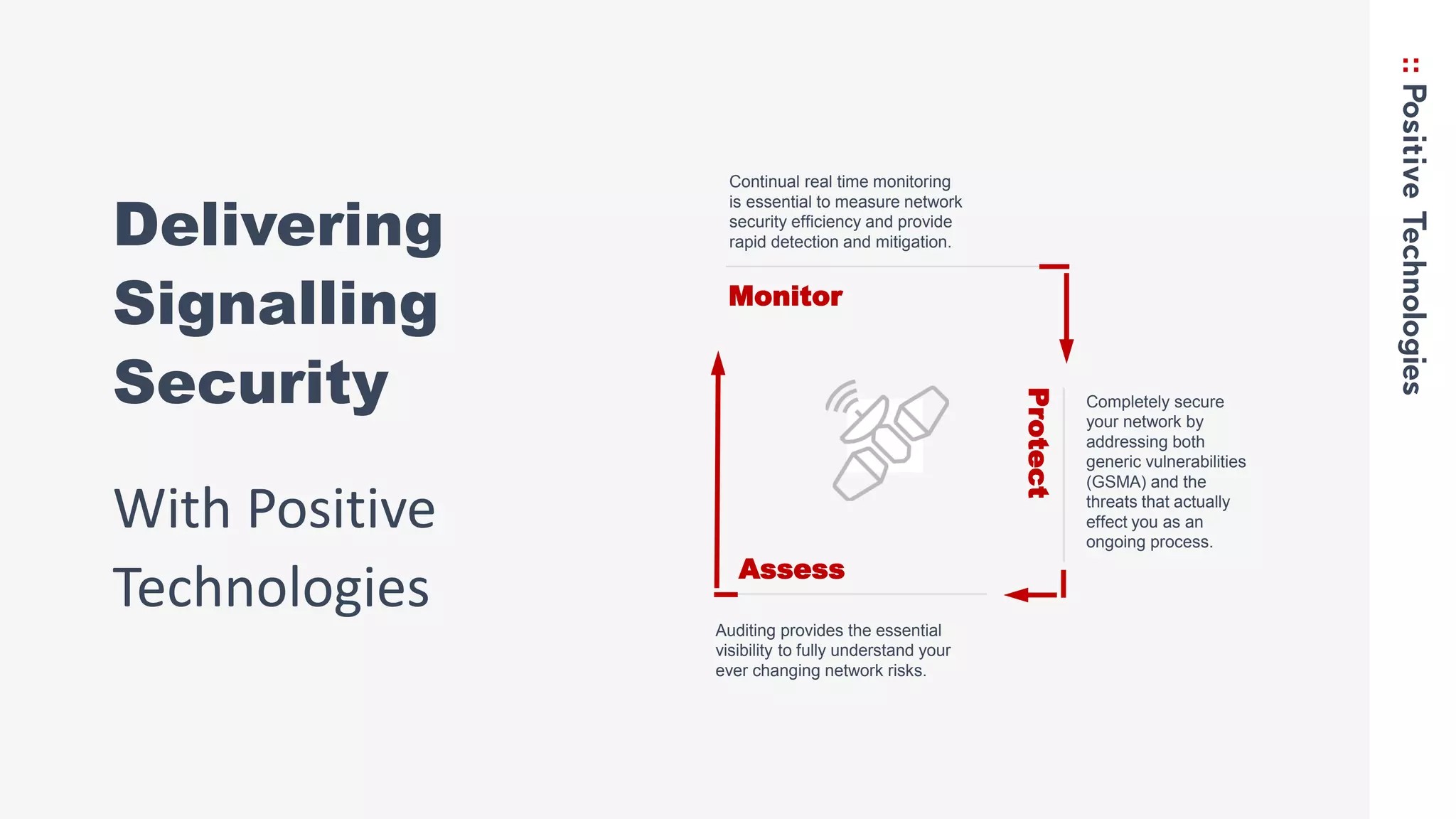
3. Recommendations for networks to protect against Simjacker like prohibiting direct STK SMS messages and continually monitoring and assessing networks for vulnerabilities.