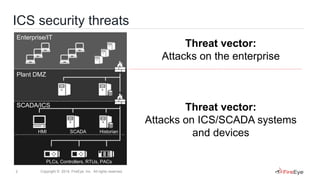
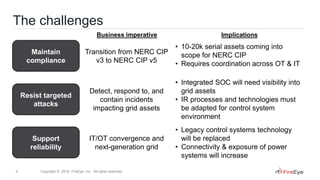
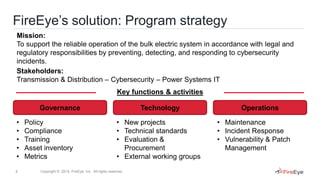
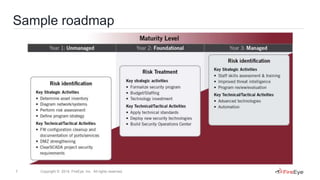
This document discusses two case studies involving industrial control systems security:
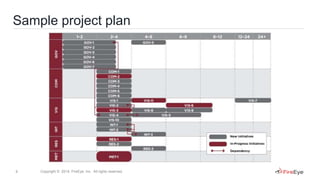
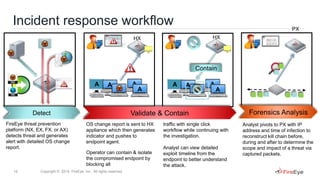
1) A case study of an ICS operator that used Mandiant Security Consulting Services to build a comprehensive cyber security program across both IT and operational technology.
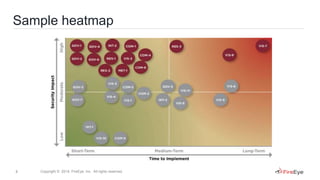
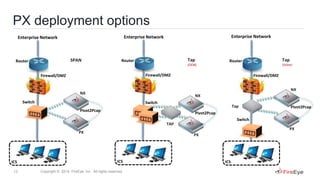
2) A case study of how another ICS operator used passive network monitoring with FireEye PX to identify flaws in their SCADA network configuration and validate network segmentation between the business network and SCADA network.