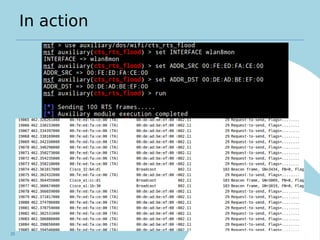
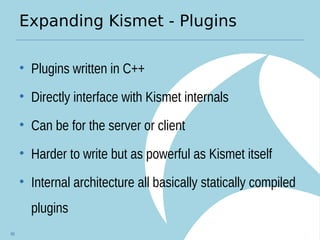
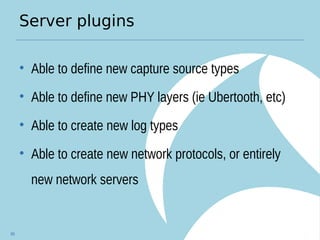
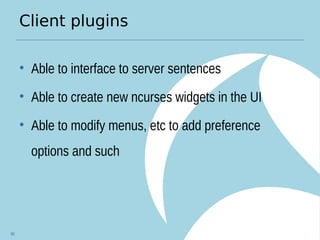
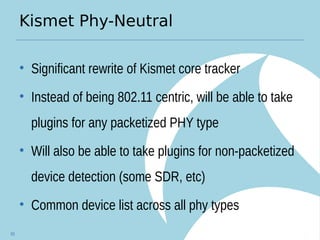
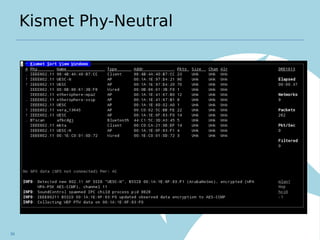
Kismet is an open source wireless intrusion detection system that can be used to monitor wireless networks passively. It detects common attacks like jamming, impersonation, and client hijacking. However, it has limitations in fully secured networks using WPA-EAP and cannot prevent misuse of open networks. Effective wireless security requires using encrypted protocols like WPA2 and educating users, as well as monitoring for threats using tools like Kismet.