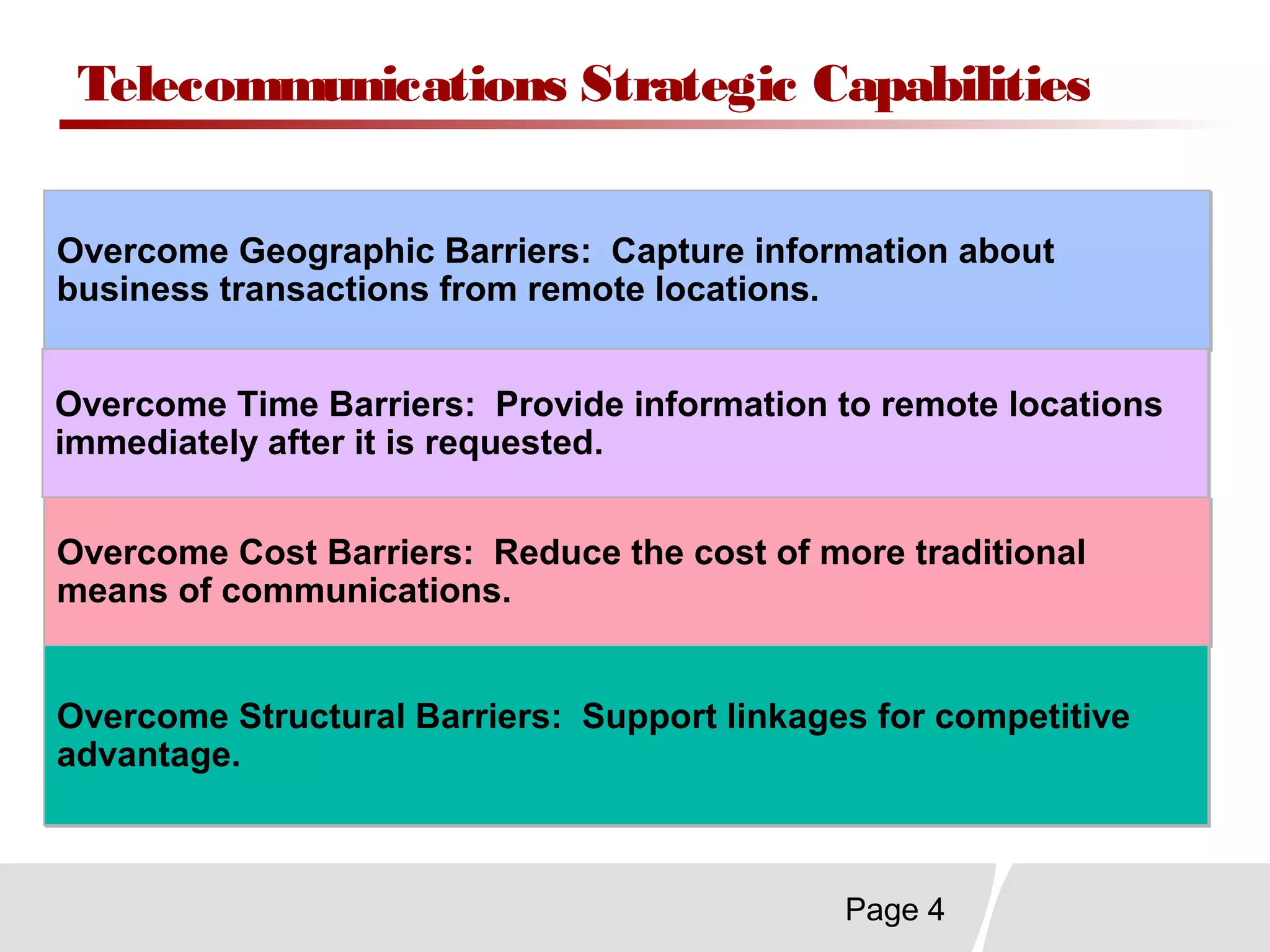
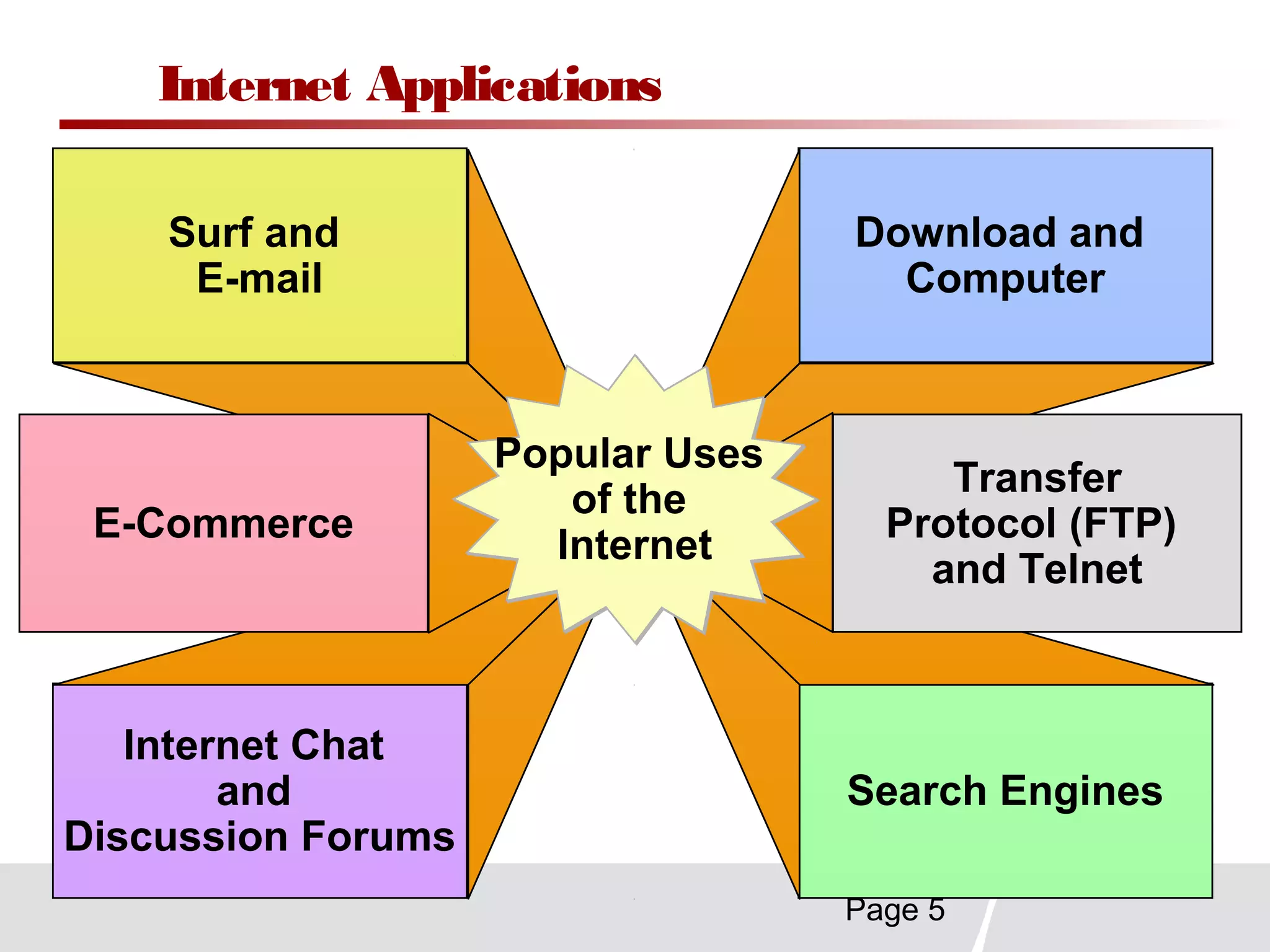
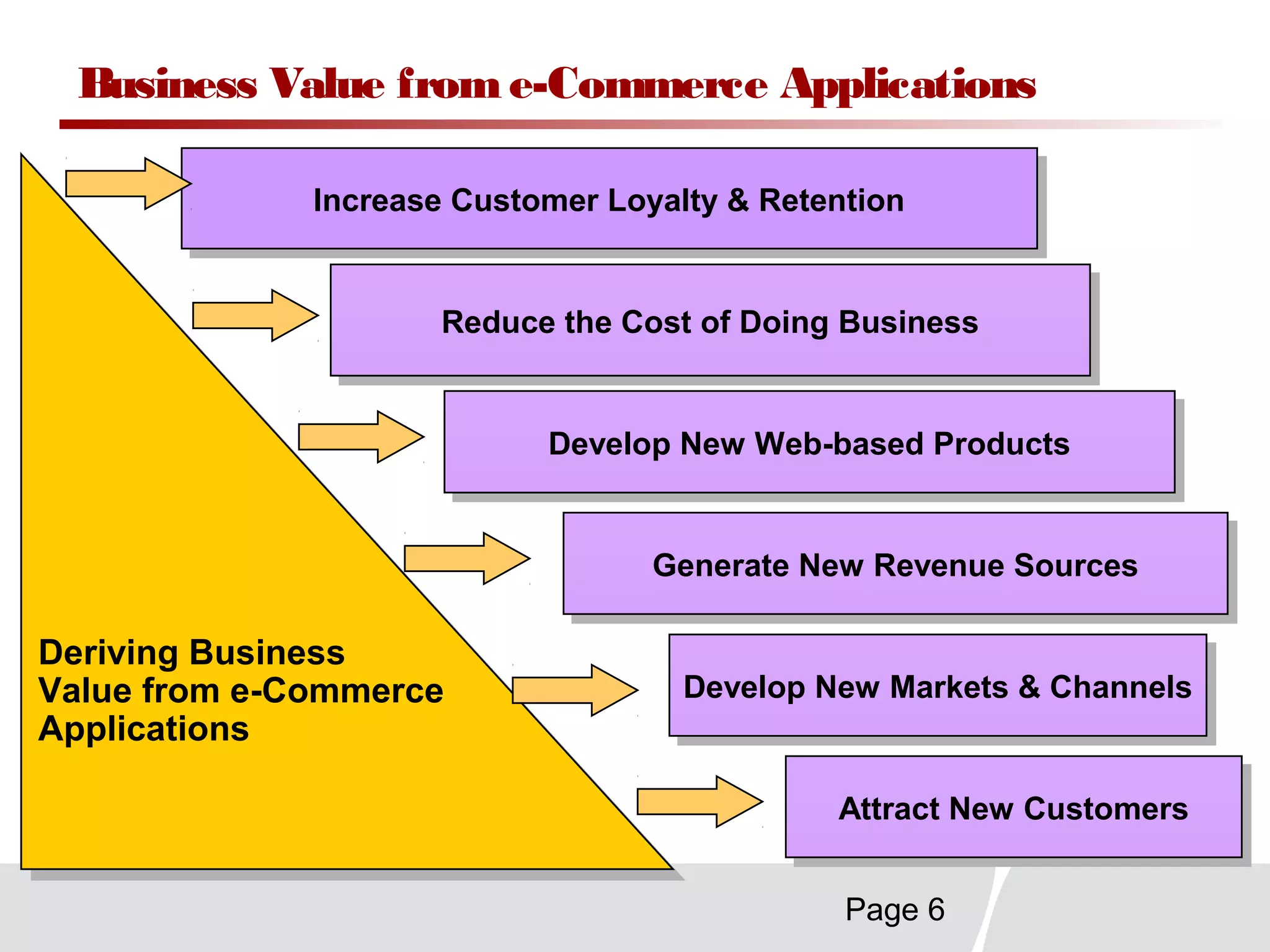
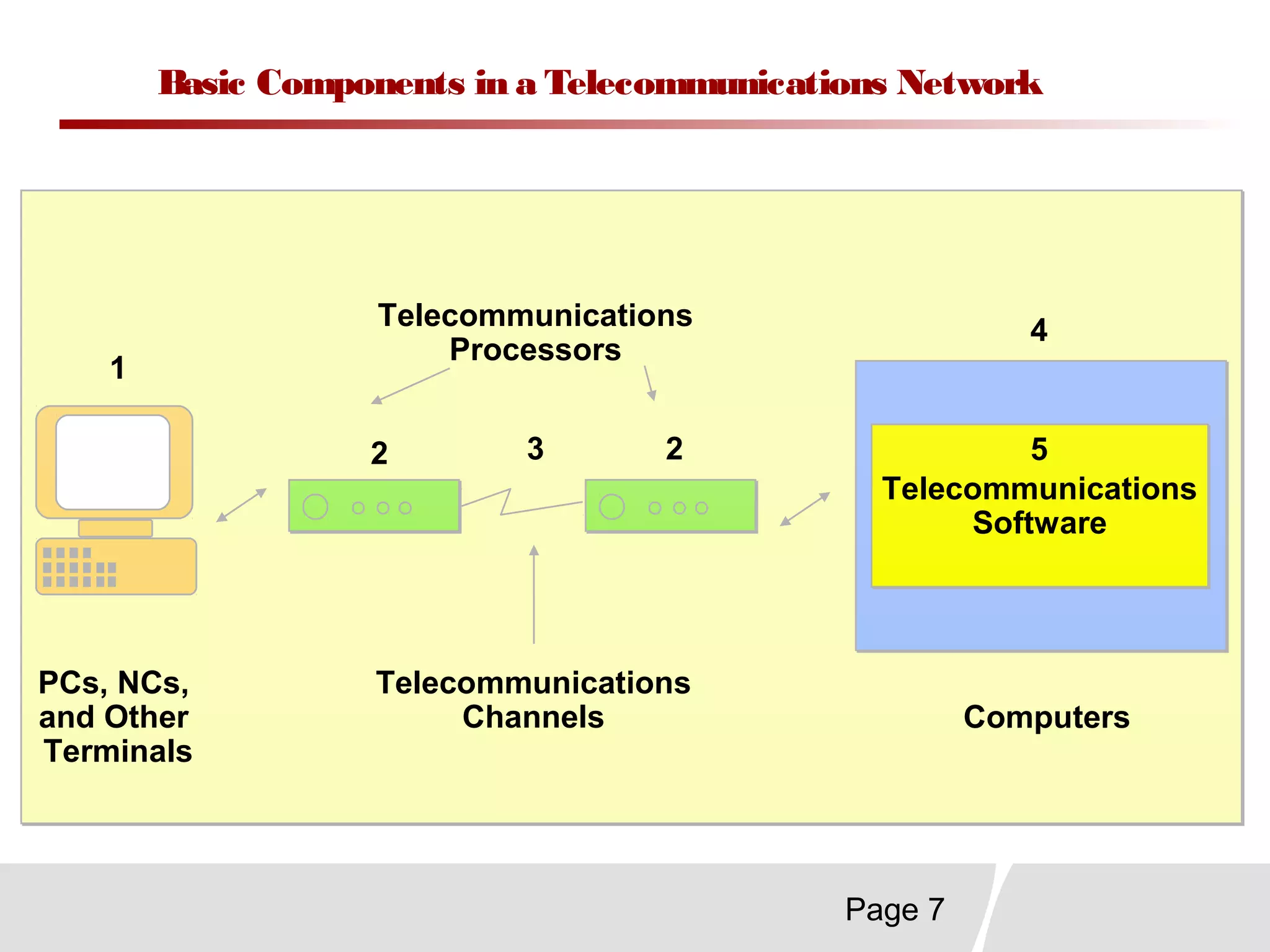
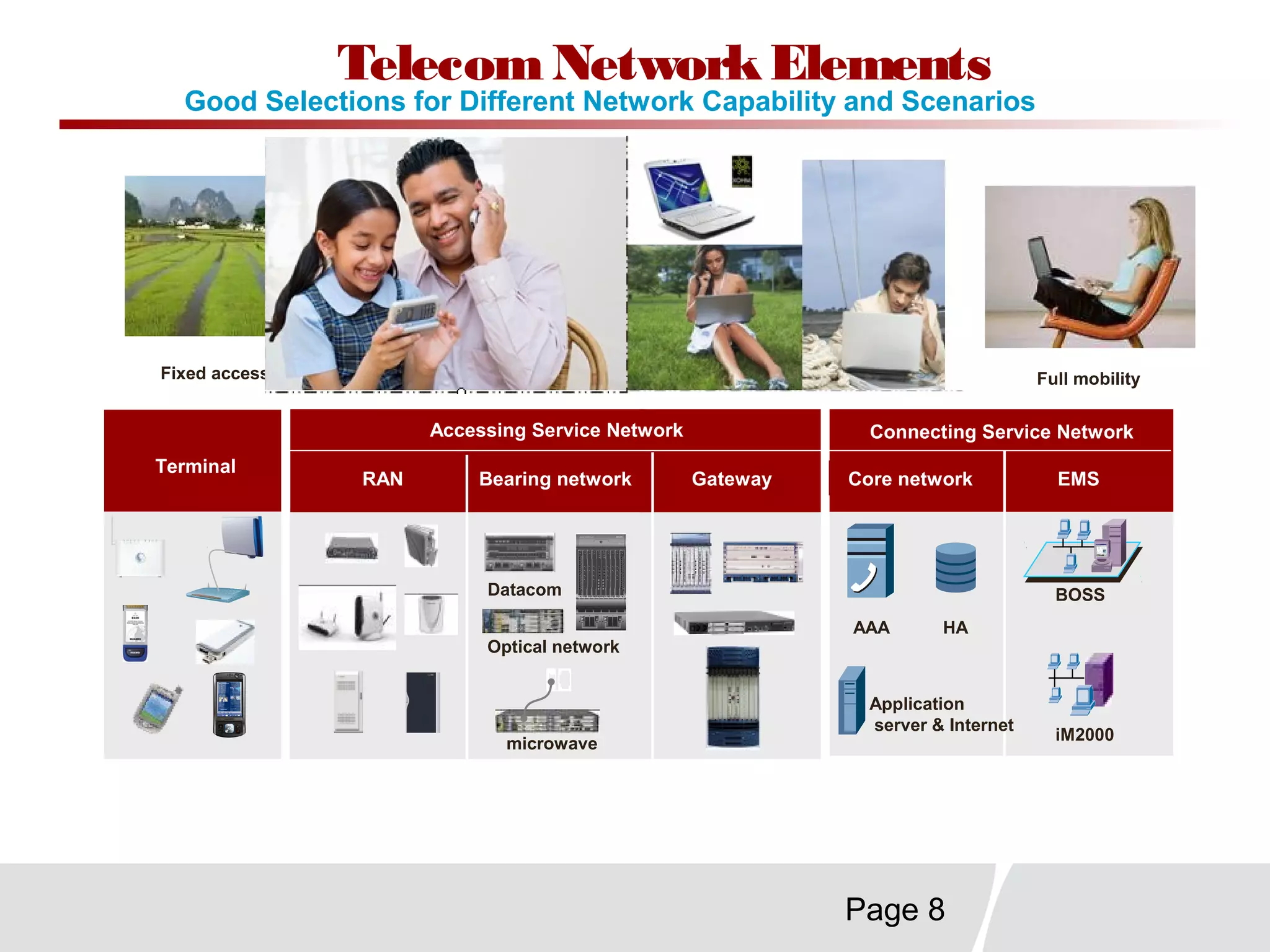
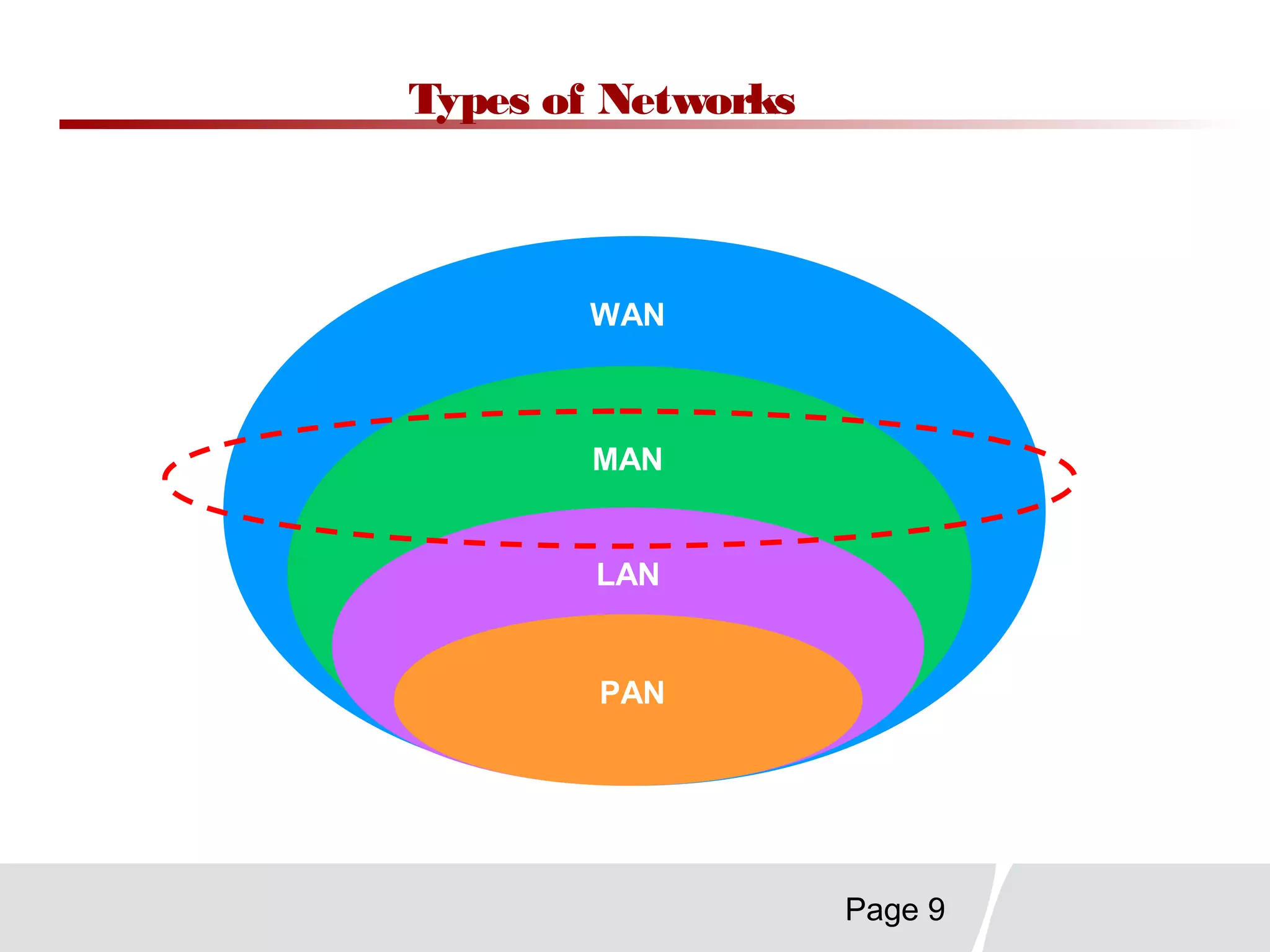
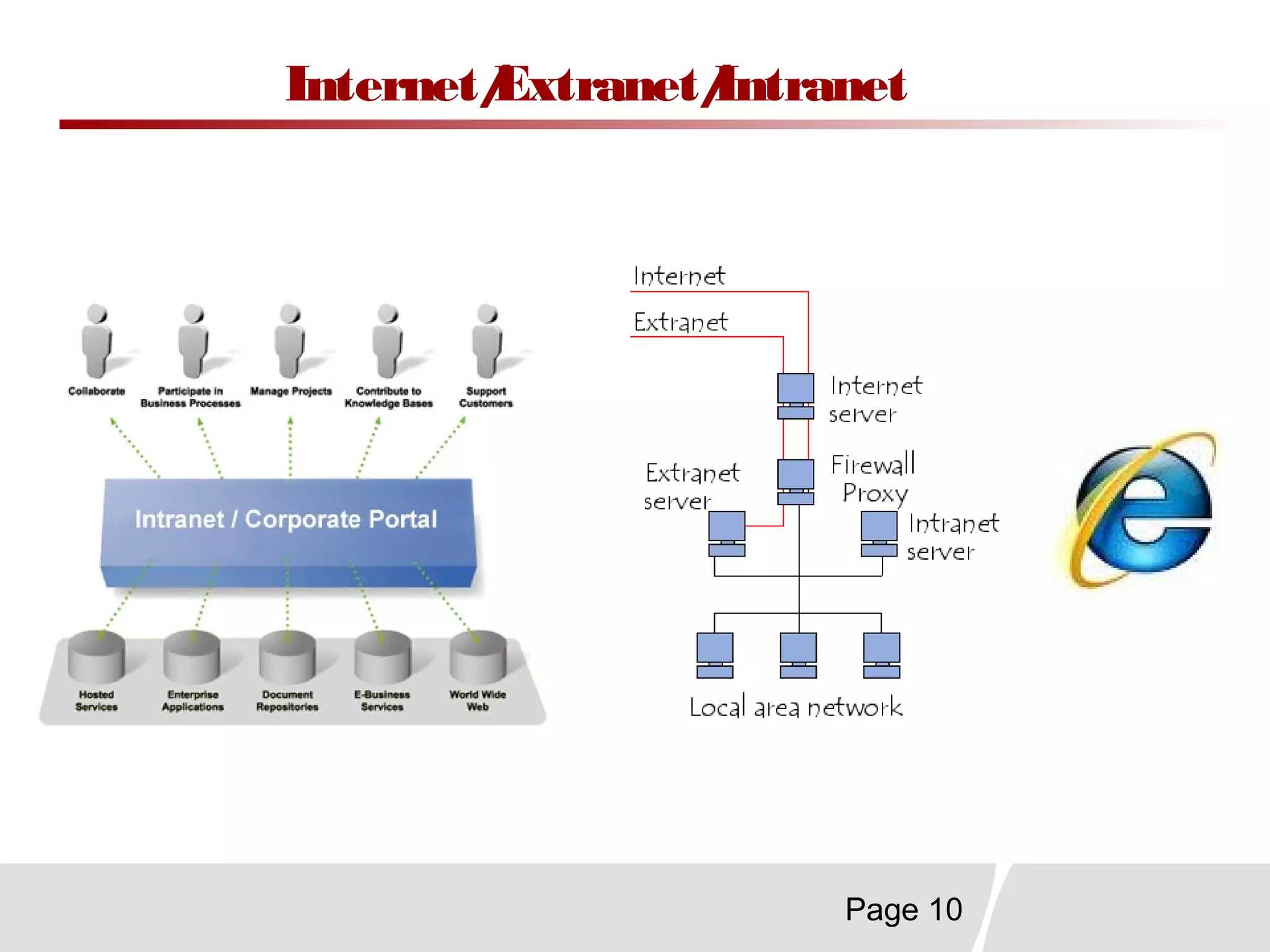
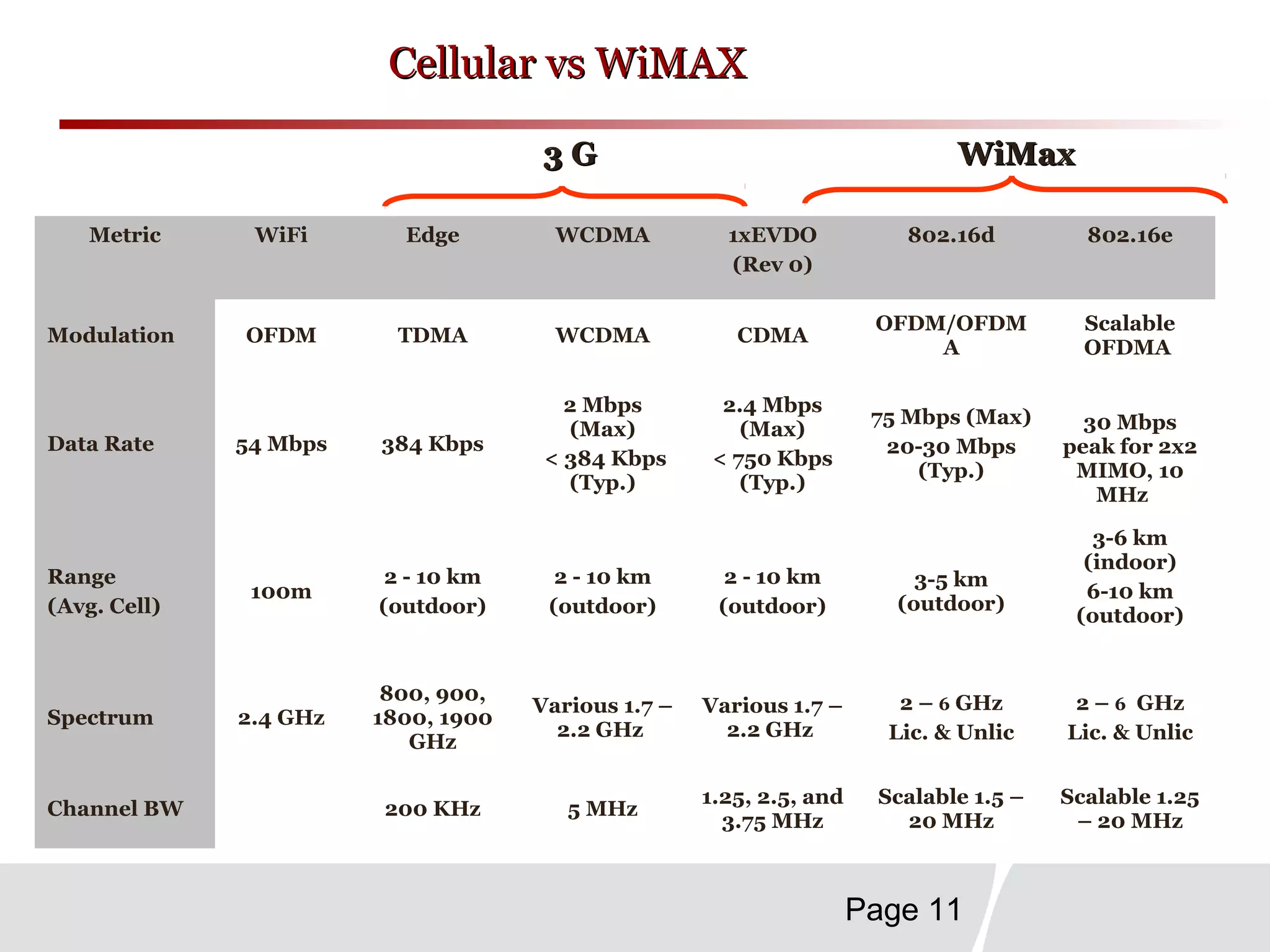
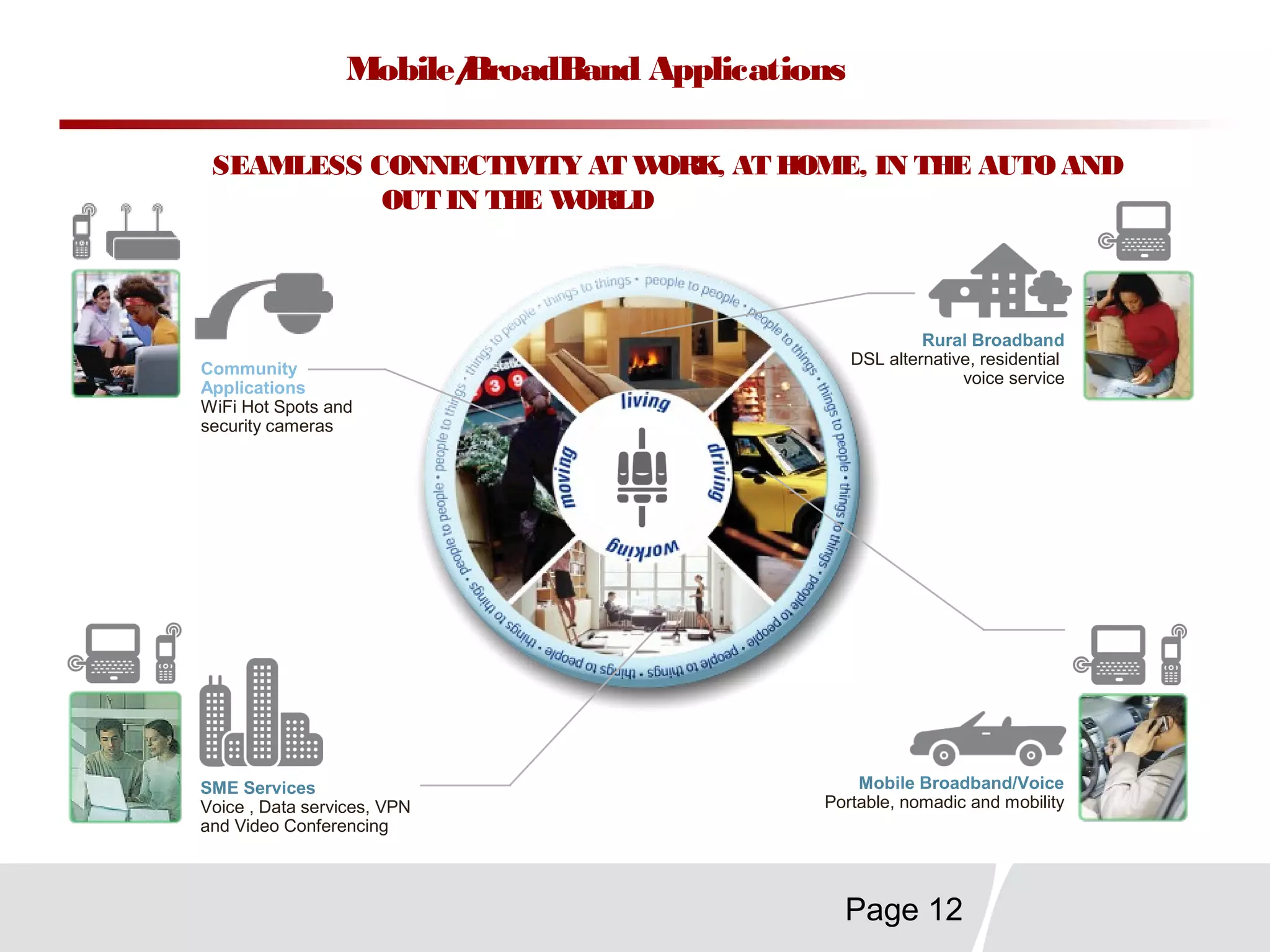
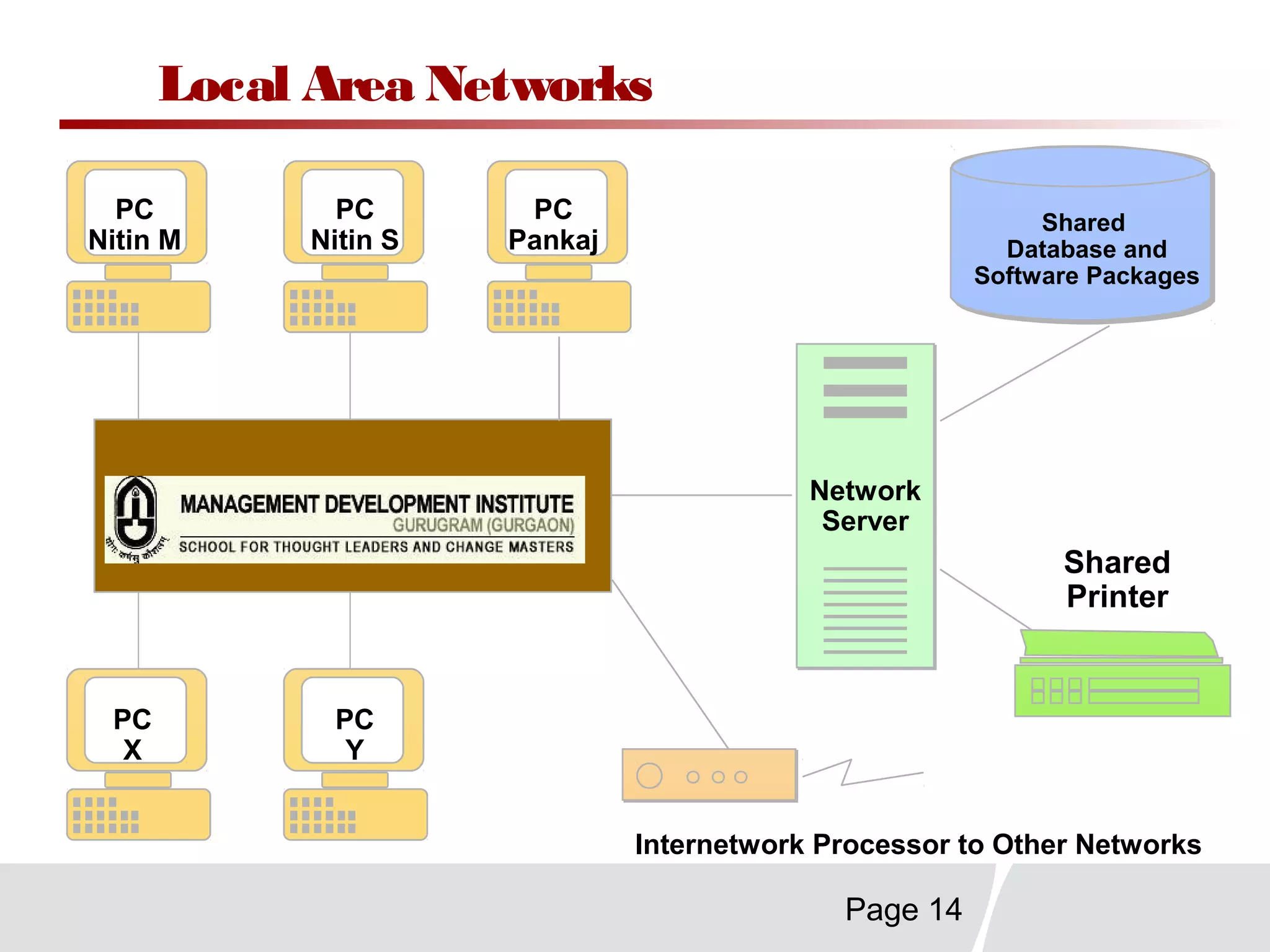
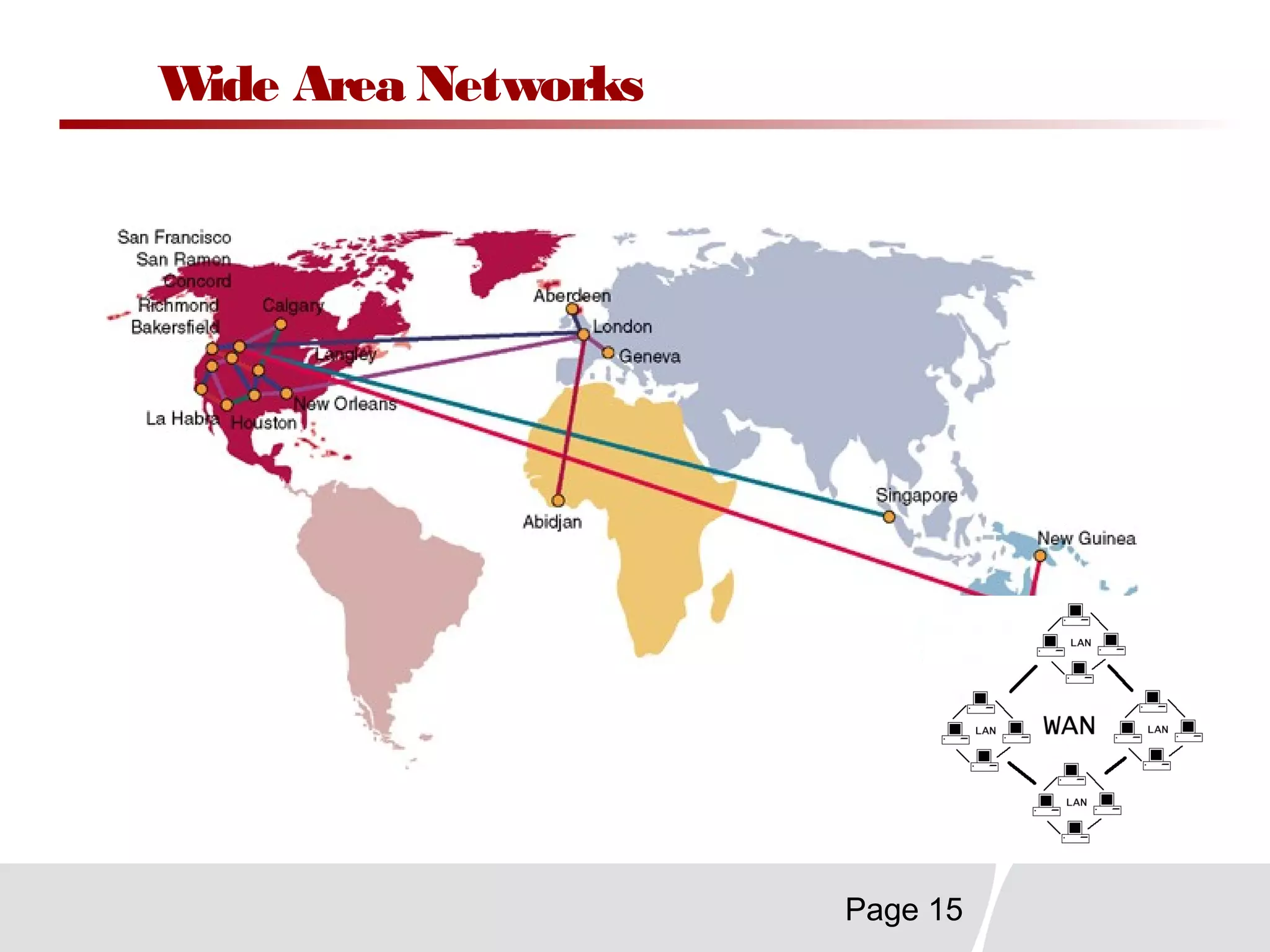
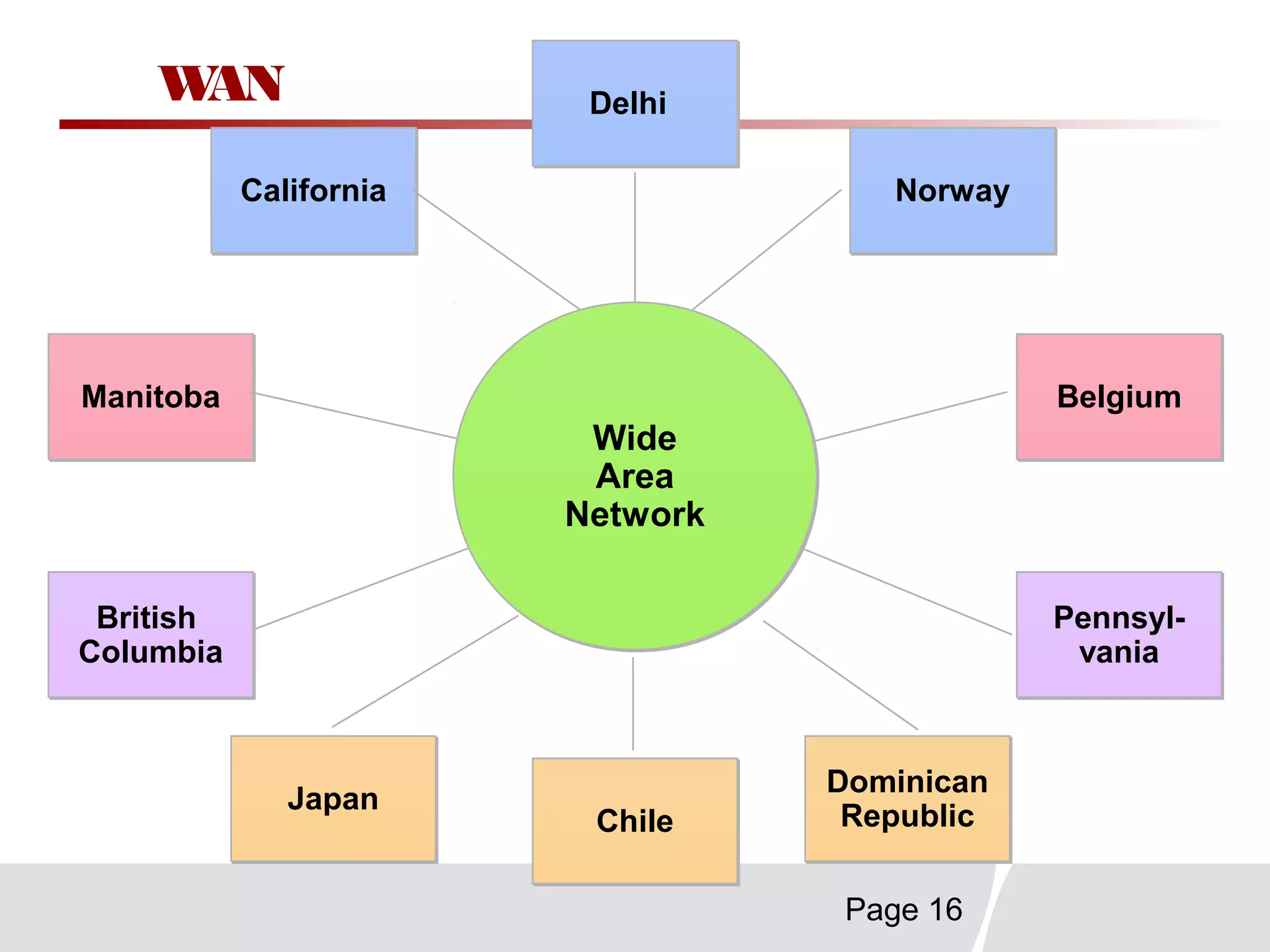
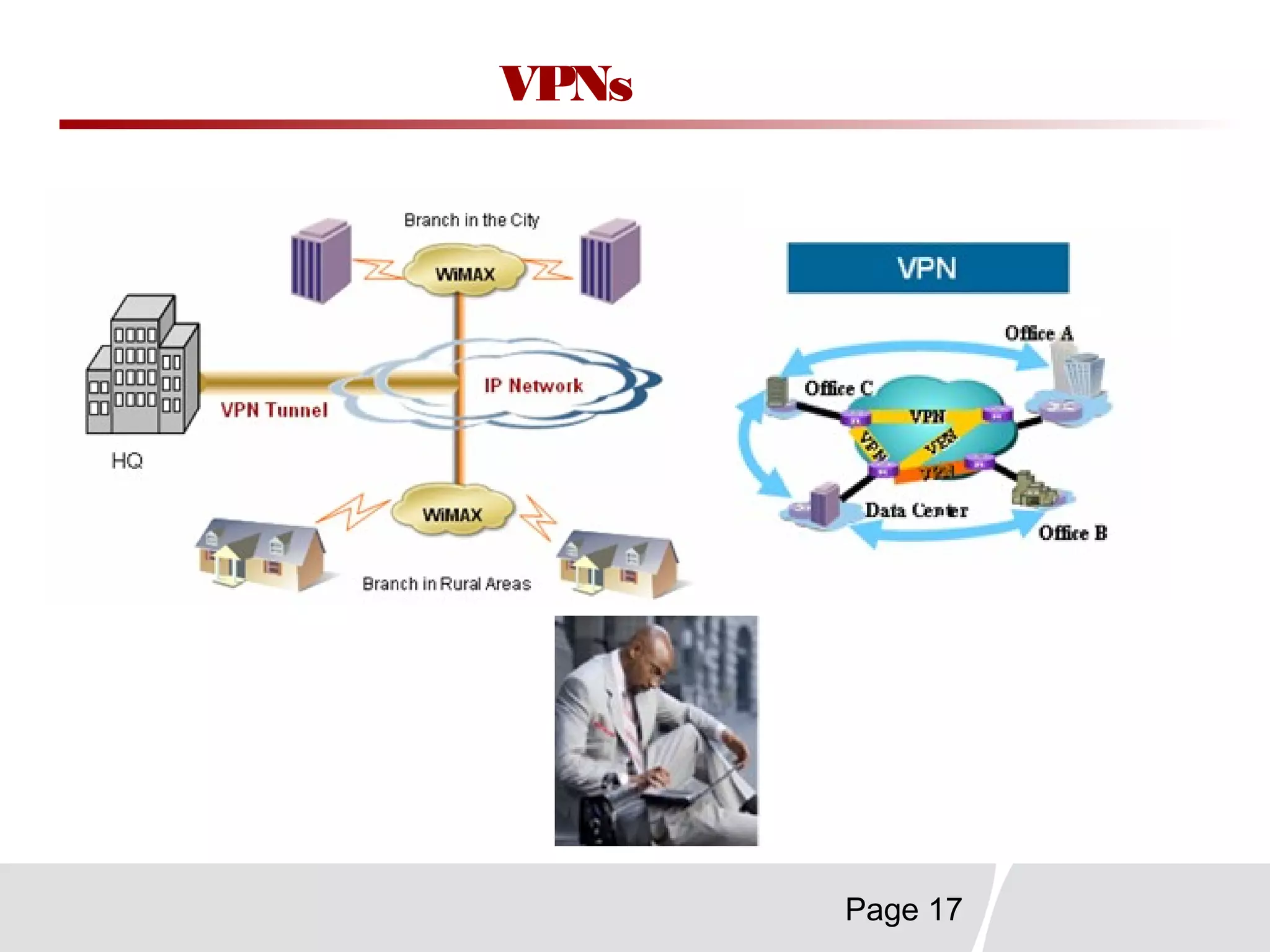
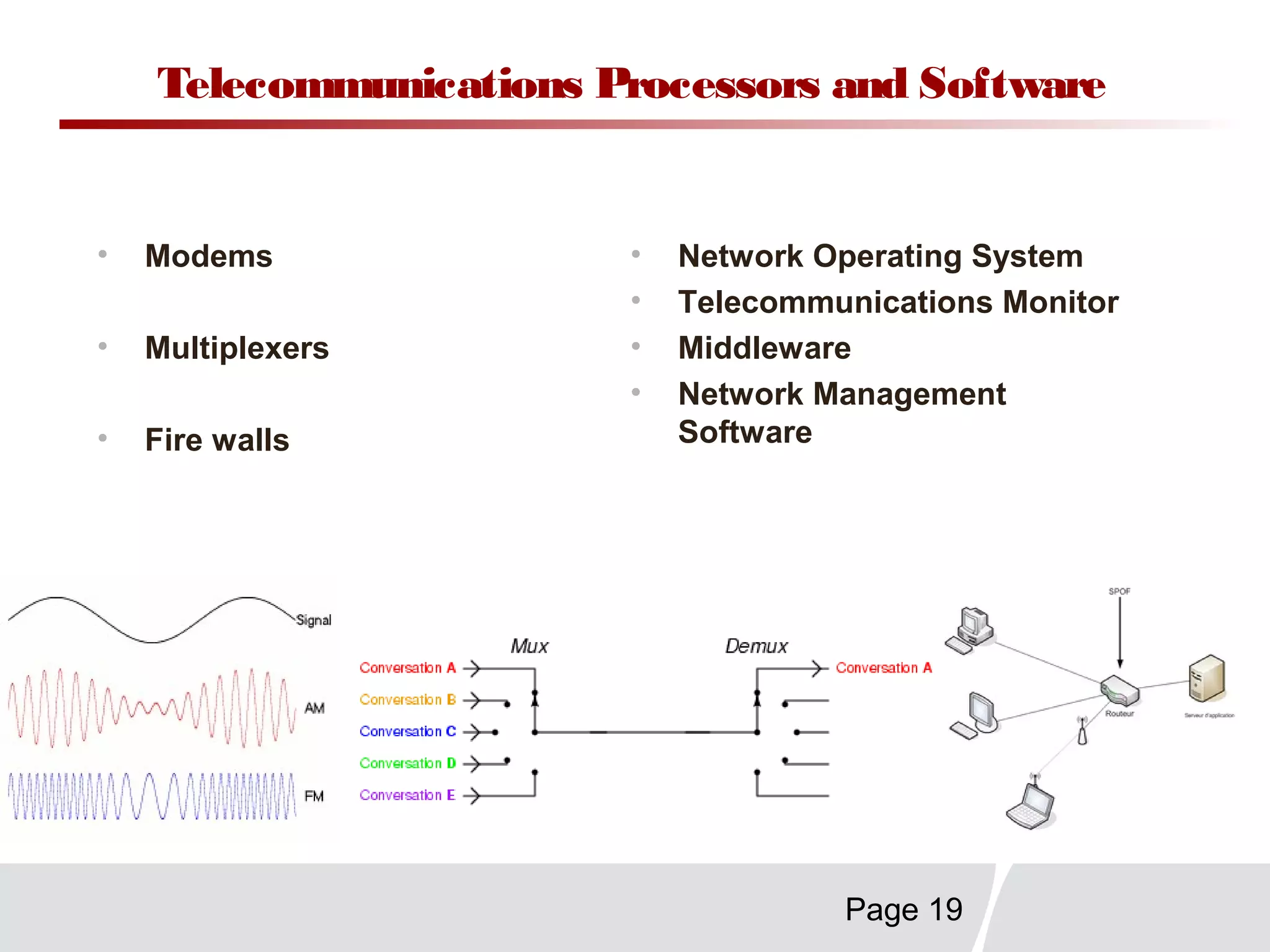
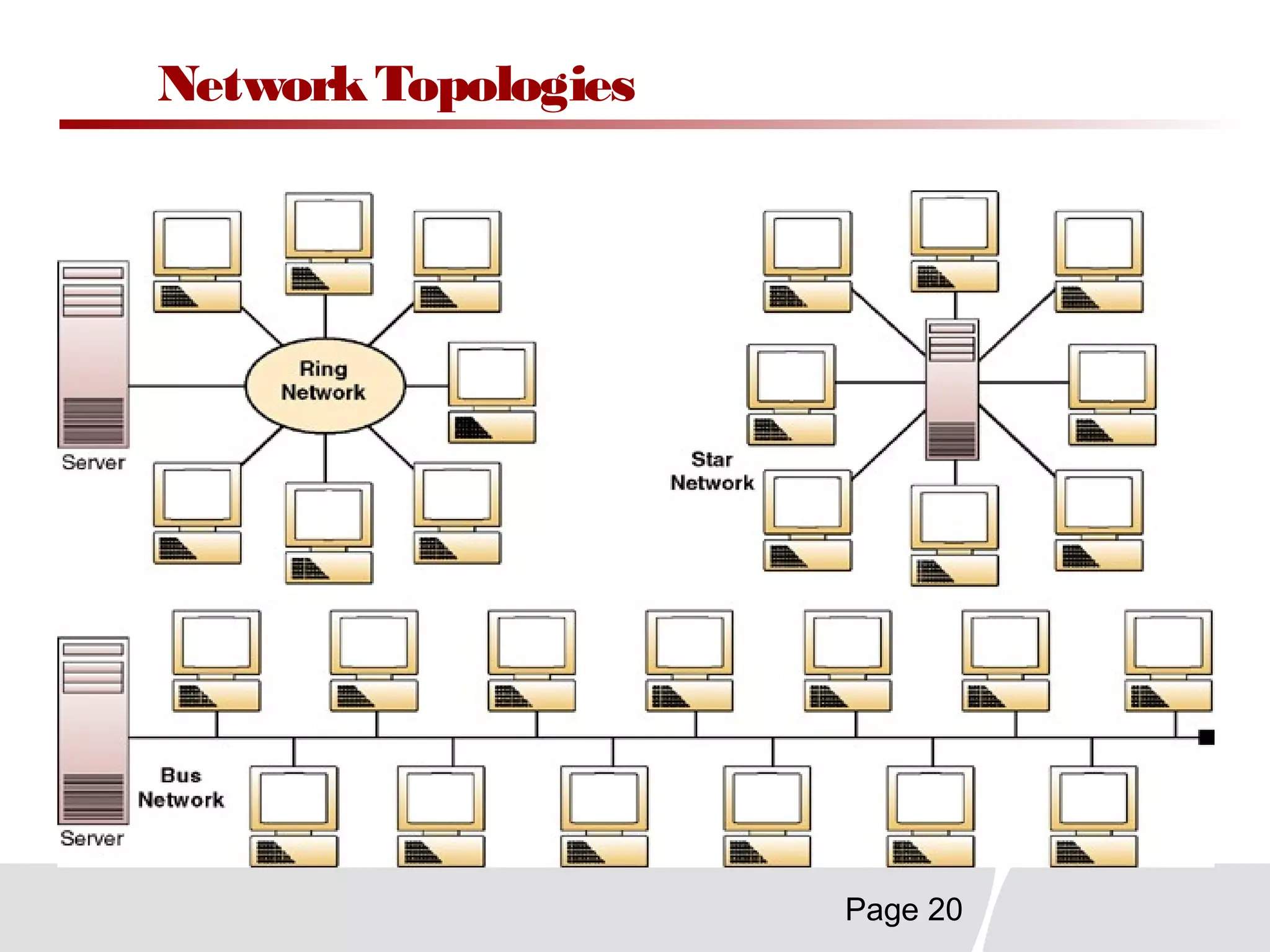
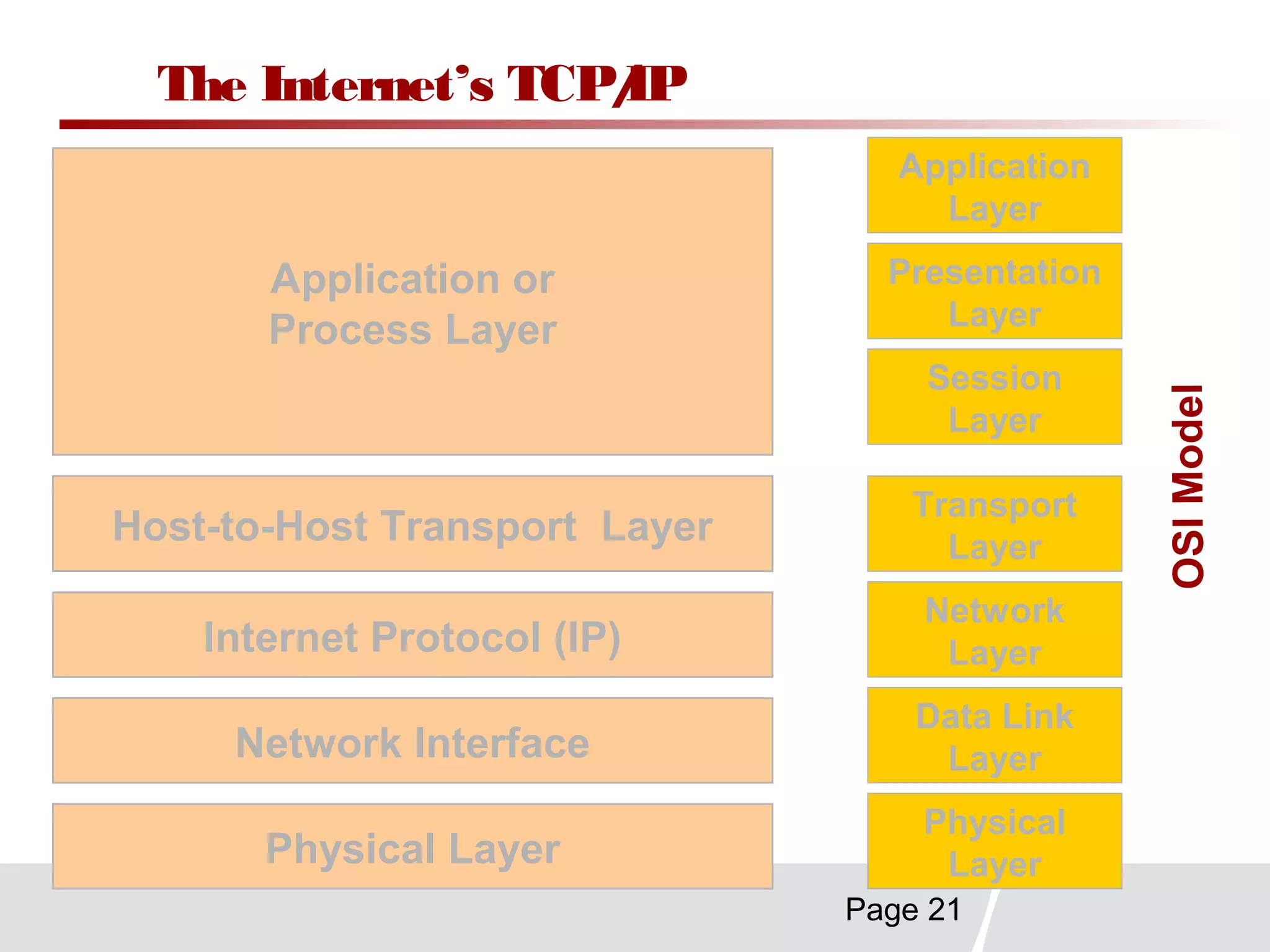
This document discusses trends in telecommunications and networks. It identifies major developments like increased e-commerce and online business operations. Telecommunications networks now use extensive internet and digital networks. The chapter objectives are to identify telecommunications industry, technology, and application trends. It also explains the basic components of telecommunications networks, including terminals, processors, channels, computers and software. Finally, the chapter summary restates that organizations use internet/intranets to support e-business and that telecommunications networks consist of key components and types of networks.