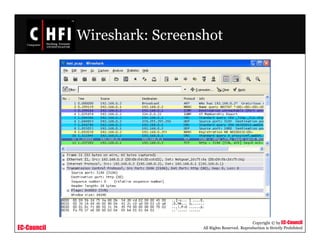
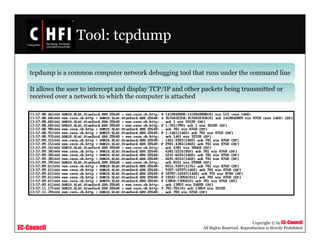
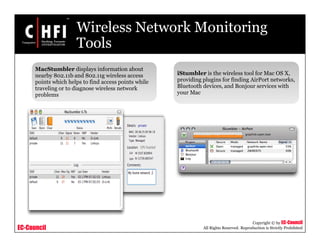
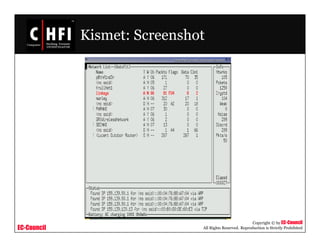
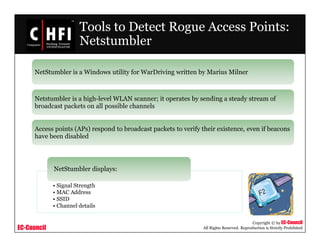
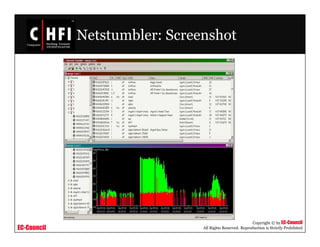
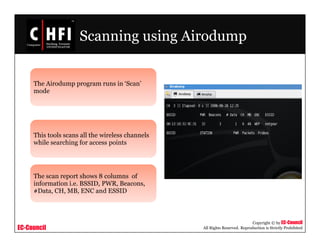
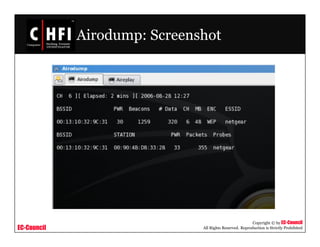
The document discusses investigating wireless networks and attacks. It covers topics like wireless networking technologies, wireless attacks like wardriving and warflying, passive attacks like eavesdropping, active attacks like denial of service attacks and man-in-the-middle attacks. It also discusses steps to investigate wireless networks like obtaining a warrant, documenting the scene, identifying wireless devices, detecting wireless connections using tools like NetStumbler, capturing wireless traffic using Wireshark and tcpdump, and analyzing the data.