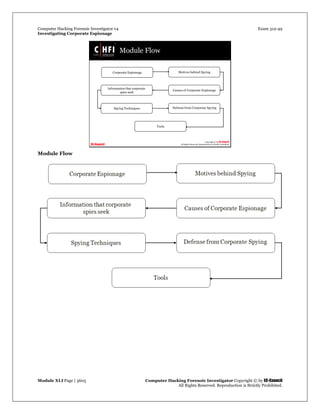
The document discusses various techniques used in corporate espionage, including hacking computers and networks, social engineering, dumpster diving, whacking (wireless hacking), phone eavesdropping, network leakage, and cryptography. It provides examples of social engineering techniques used by spies, such as unwittingly answering questions or bragging to coworkers. The document also notes that aggregation of information in one location can increase risks of insider or outsider attacks enabling espionage.




















![Computer Hacking Forensic Investigator v4 Exam 312-49
Investigating Corporate Espionage
Module XLI Page | 3622 Computer Hacking Forensic Investigator Copyright © by EC-Council
All Rights Reserved. Reproduction is Strictly Prohibited.
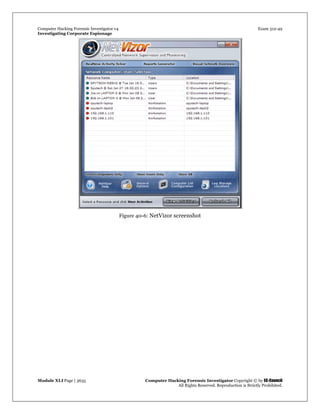
Netspionage
Source: http://www.pimall.com/
“Netspionage is defined as network enabled espionage, and in our information systems world, it is an
exciting way of …extending the old practice of competitive intelligence gathering. This new, computerized,
and information-dependent world is heavily dependent on the web, networks, and software technology.
The information gatherers of this new age are exploiting [our] dependency on technology for personal,
corporate, and national gain.”
Corporate espionage is an old practice but the advent of the Internet has made it easier, faster, and much
more anonymous. Netspionage enables the spies to steal sensitive corporate information without
physically entering into the company.](https://image.slidesharecdn.com/file000095-140617045017-phpapp02/85/File000095-24-320.jpg)




![Computer Hacking Forensic Investigator v4 Exam 312-49
Investigating Corporate Espionage
Module XLI Page | 3631 Computer Hacking Forensic Investigator Copyright © by EC-Council
All Rights Reserved. Reproduction is Strictly Prohibited.
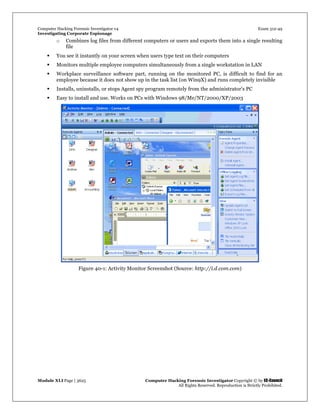
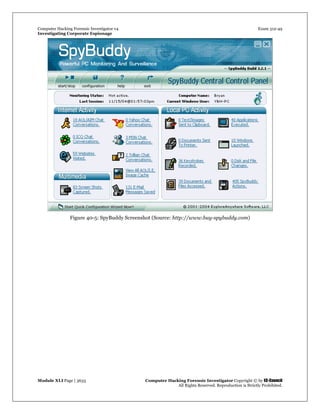
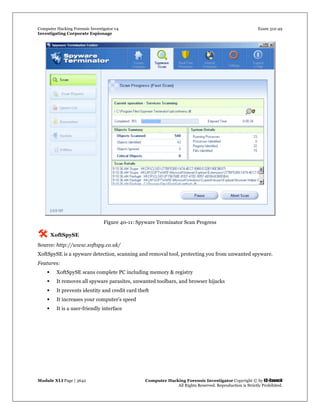
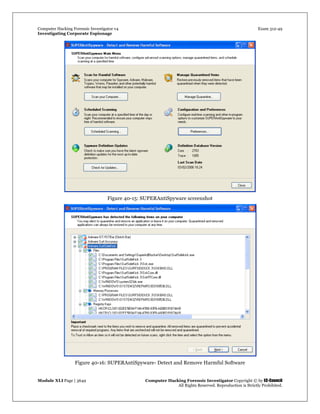
Spy Tool: SpyBuddy
Source: http://www.exploreanywhere.com/
SpyBuddy is a powerful spy software and computer monitoring product for monitoring spouses, children,
co-workers, or just about anyone else. It enables you to monitor all areas of your PC, tracking every action
down to the last keystroke pressed or the last file deleted. SpyBuddy is equipped with the functionality to
record all AOL/ICQ/MSN/AIM/Yahoo chat conversations, all websites visited, all windows opened and
interacted with, every application executed, every document printed, every file or folder renamed and/or
modified, all text and images sent to the clipboard, every keystroke pressed, every password typed, and
more.
Features:
Internet Conversation Logging: Logs both sides of all chat and instant message conversations for
AOL/ICQ/MSN/AIM/Yahoo Instant Messengers.
Disk Activity Logging: Records all changes made to your hard drive and external media.
Window Activity Logging: Captures information on every window that was viewed and interacted
with.
Application Activity Logging: Tracks every application/executable that was executed and
interacted with.
Clipboard Activity Logging: Captures every text and image item that was copied to the clipboard.
AOL/Internet Explorer History: Views All AOL and Internet Explorer websites visited before
SpyBuddy was installed, and when SpyBuddy was not recording.
Printed Documents Logging: Logs specific information on all documents that were sent to the
printer spool.
Keystroke Monitoring: Tracks all keystrokes pressed [including hidden system keys] and which
windows they were pressed in. Keystrokes can also be passed through a formatter for easy
viewing/exporting.
Websites Activity Logging: Logs all website title and addresses that were visited on the PC.
Screen Shot Capturing: Automatically captures screen shots of the desktop (or the active window)
at set intervals.
Powerful Stealth Mode: Runs SpyBuddy in total stealth - the user will not know that it is running.](https://image.slidesharecdn.com/file000095-140617045017-phpapp02/85/File000095-33-320.jpg)









![Computer Hacking Forensic Investigator v4 Exam 312-49
Investigating Corporate Espionage
Module XLI Page | 3653 Computer Hacking Forensic Investigator Copyright © by EC-Council
All Rights Reserved. Reproduction is Strictly Prohibited.
Case Study: India’s Growing Corporate Spy Threat
Source: http://www.atimes.com/
According to a survey, Indian corporate sector faces the highest threat of fraud, including espionage.
Many cases are recently brought to the surface Indian corporate world; targets are mostly MNC’s. Culprits
are foreign companies and smaller local competitor firms. KPMG global consultancy said that
"Organizations today face a completely different set of challenges - globalization, rapidly evolving
technology, rapid development in industry and business, risks and complexity of information and data
management; the list is endless."
Spying and the extraction of sensitive information using unfair means are new in India but such activities
are limited to government departments, defense establishments, and a few stray instances involving the
business world. "What has changed in recent years," said Ashwin Parikh of Ernst & Young, "is the
involvement of the corporate sector, and the methods used. This practice of using students [for instance]
to pick up competitors' information has become rather rampant now."](https://image.slidesharecdn.com/file000095-140617045017-phpapp02/85/File000095-55-320.jpg)




