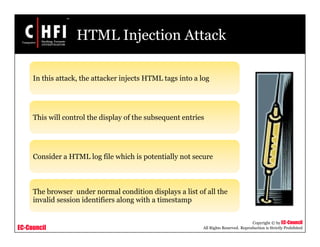
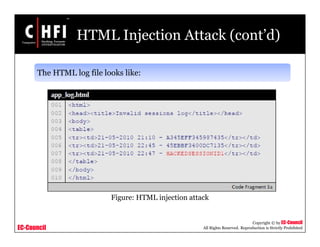
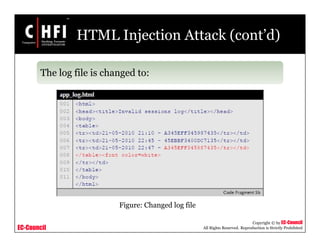
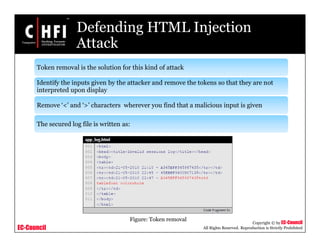
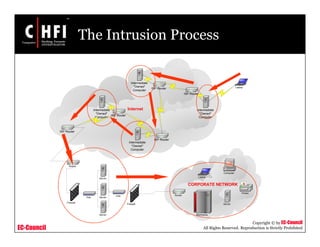
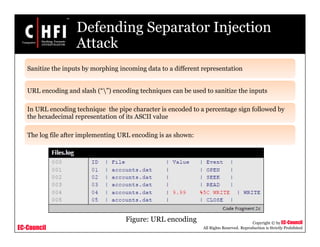
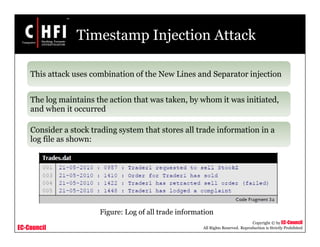
This document discusses network forensics and investigating logs. It covers topics such as where to find evidence like logs from firewalls, routers, servers and applications. It also discusses analyzing logs, handling logs as evidence, and different types of log injection attacks like new line injection, separator injection and defending against them. The document provides guidance on ensuring log file authenticity and integrity when investigating security incidents.













![EC-Council
Copyright © by EC-Council
All Rights Reserved. Reproduction is Strictly Prohibited
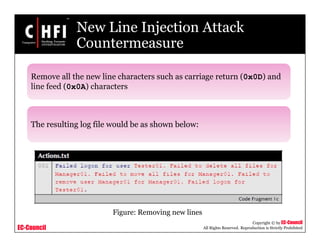
New Line Injection Attack
(cont’d)
The attacker changes the log file source code by inserting
[LINEBREAK] and changing the user name “Tester01” to say
“Manager01”
The log file after attack:
Figure: New lines inserted by attackers](https://image.slidesharecdn.com/file000139-140617045453-phpapp01/85/File000139-22-320.jpg)
![EC-Council
Copyright © by EC-Council
All Rights Reserved. Reproduction is Strictly Prohibited
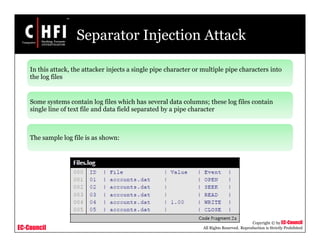
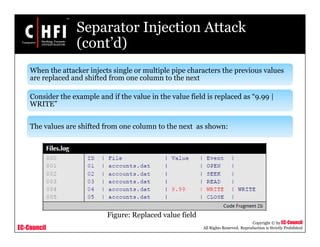
Timestamp Injection Attack
(cont’d)
The new line input injection may look like:
• “AccountY[LINEBREAK] 21-05-2010 : 1002 : Trader1 has
retracted sell order”
The log output is as follows:
Figure: New line input injection](https://image.slidesharecdn.com/file000139-140617045453-phpapp01/85/File000139-29-320.jpg)




![EC-Council
Copyright © by EC-Council
All Rights Reserved. Reproduction is Strictly Prohibited
Defending Word Wrap Abuse
Attack (cont’d)
The log file entry after splitting looks like:
Here [CR] indicates that login software has inserted a carriage return
The disadvantage of this method is integrity of entries may be compromised](https://image.slidesharecdn.com/file000139-140617045453-phpapp01/85/File000139-35-320.jpg)