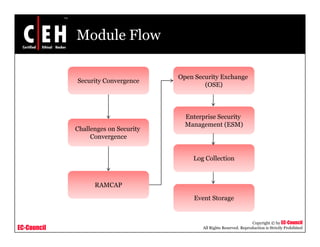
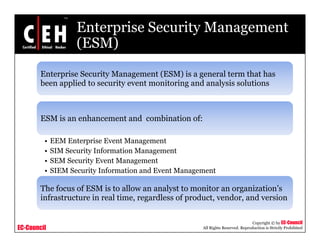
Security convergence involves integrating security functions and information across an IP network to improve security performance. It addresses interdependencies between business functions. RAMCAP is a DHS program for security policy based on global risk assessment. Enterprise Security Management (ESM) integrates security event monitoring and analysis. The IPMI standard supports monitoring and managing computer systems out-of-band.