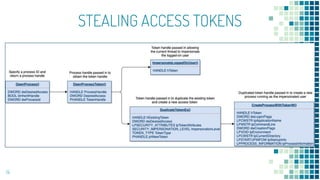
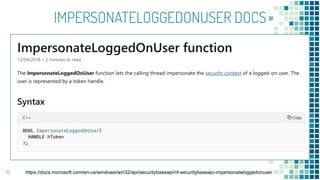
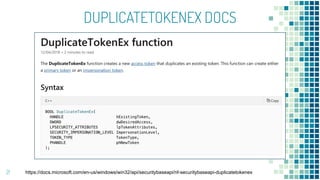
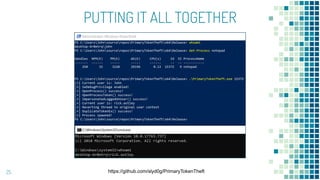
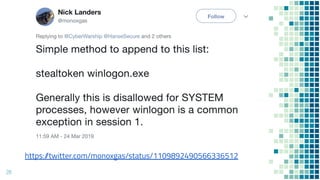
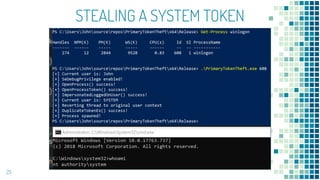
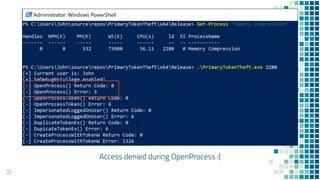
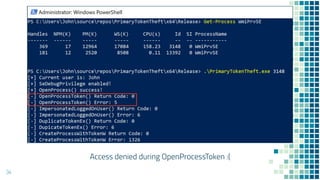
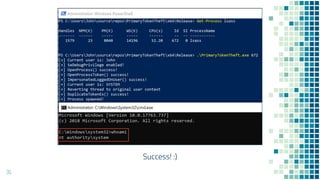
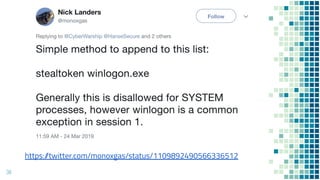
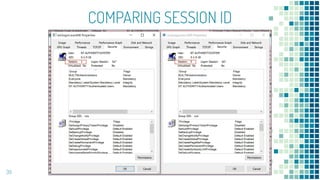
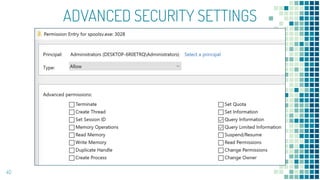
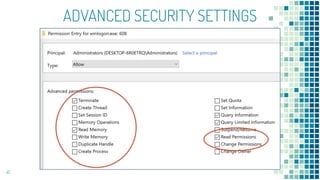
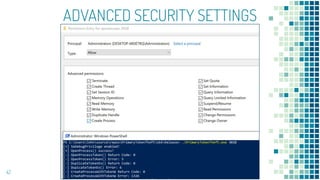
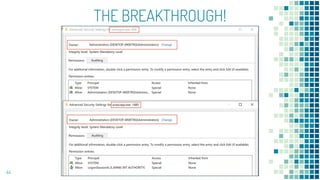
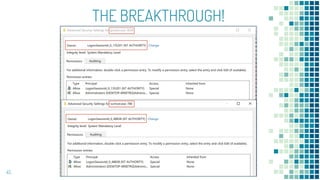
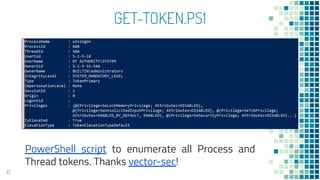
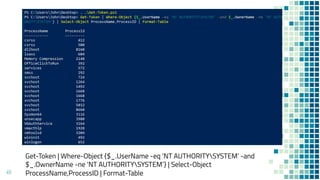
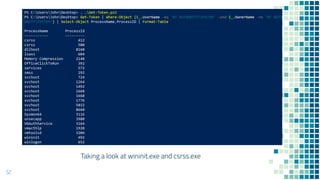
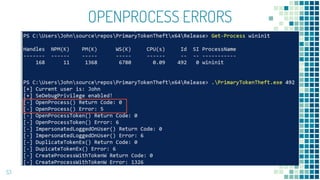
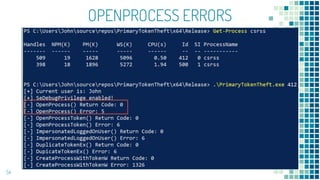
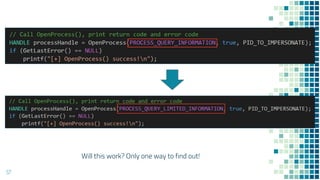
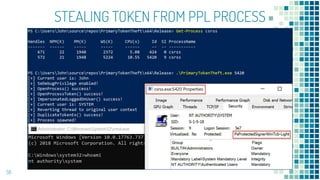
This document discusses Windows access token manipulation. It begins by explaining what access tokens are and how they are used for authentication and access control in Windows. It then covers how to steal access tokens by opening processes, obtaining their tokens, and using the tokens to impersonate users or launch new processes. The document explores techniques for stealing the SYSTEM access token as well as finding alternative processes besides winlogon.exe that can be used. It determines that processes with certain security permissions on their access tokens can be stolen, while others cannot. The key learnings provide insights into Windows security principles and how access token theft can enable privilege escalation.