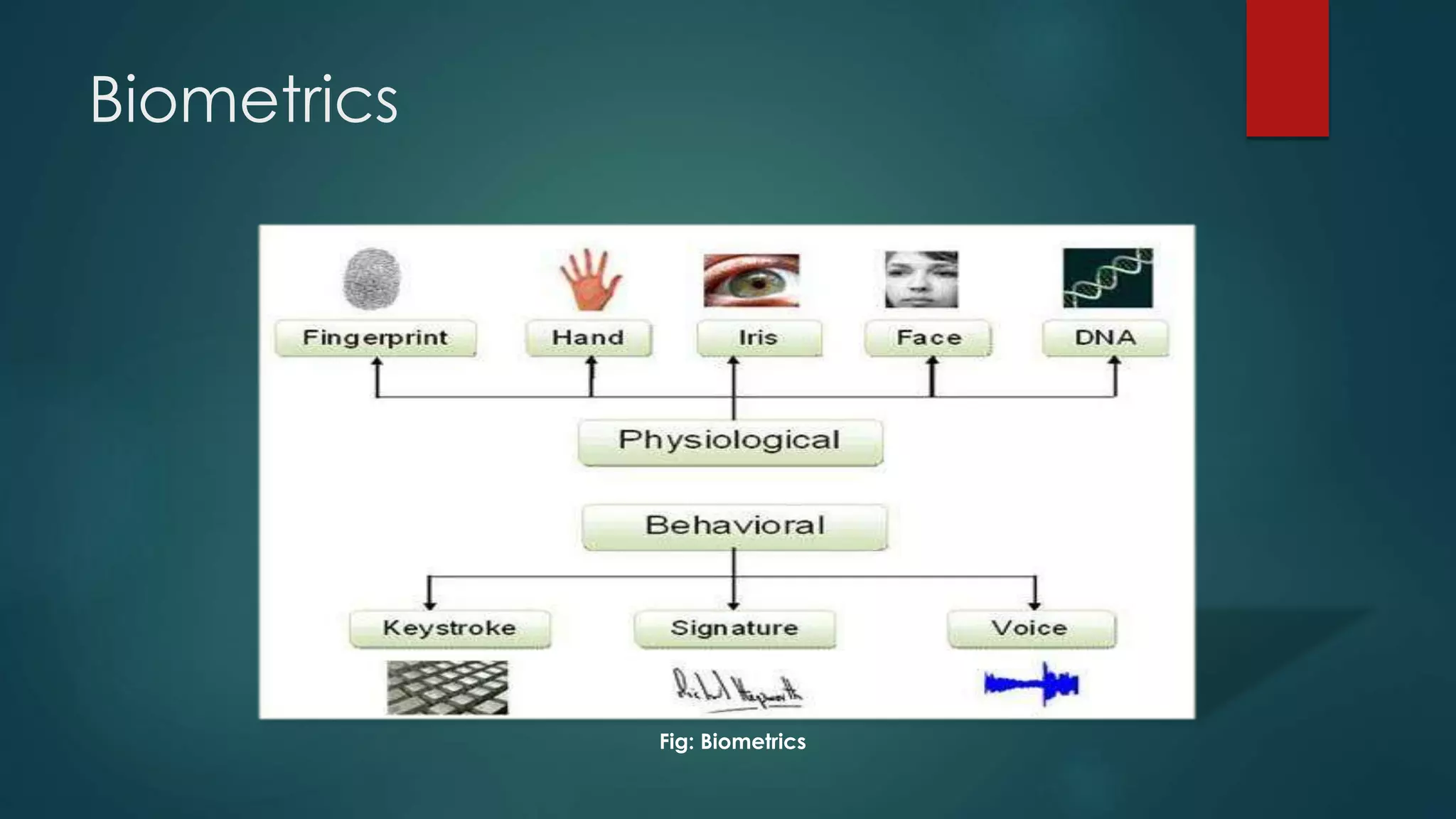
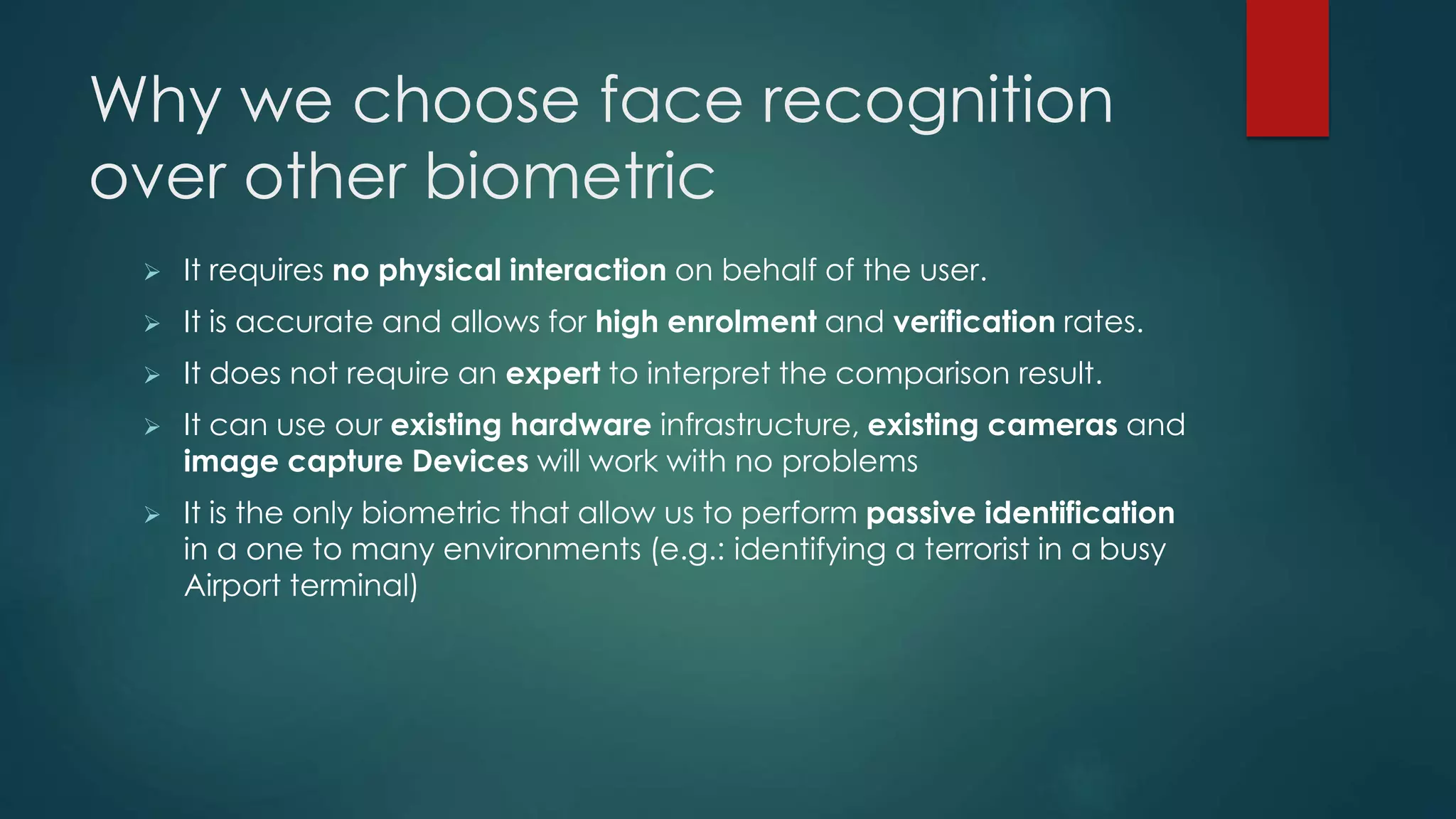
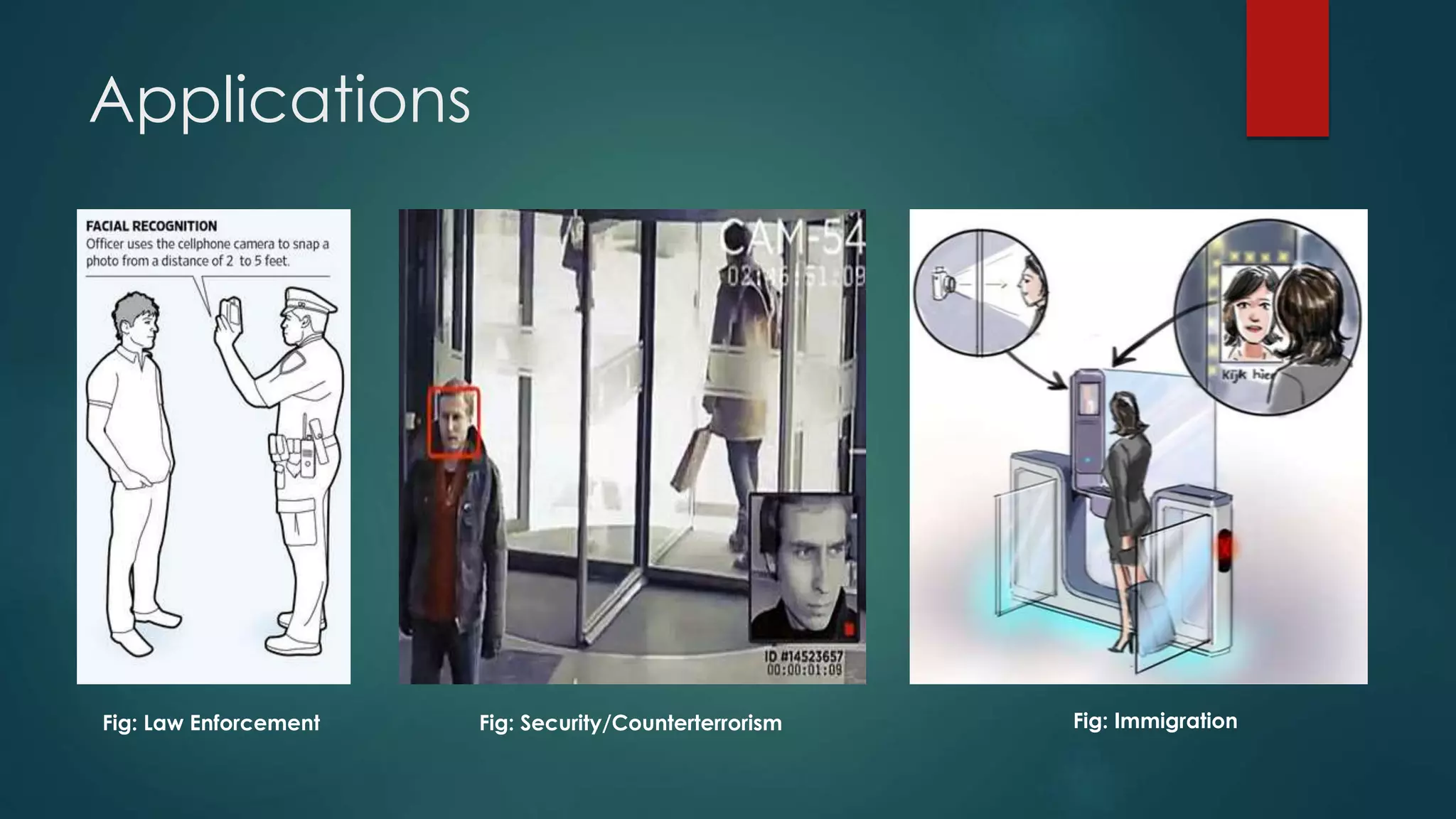
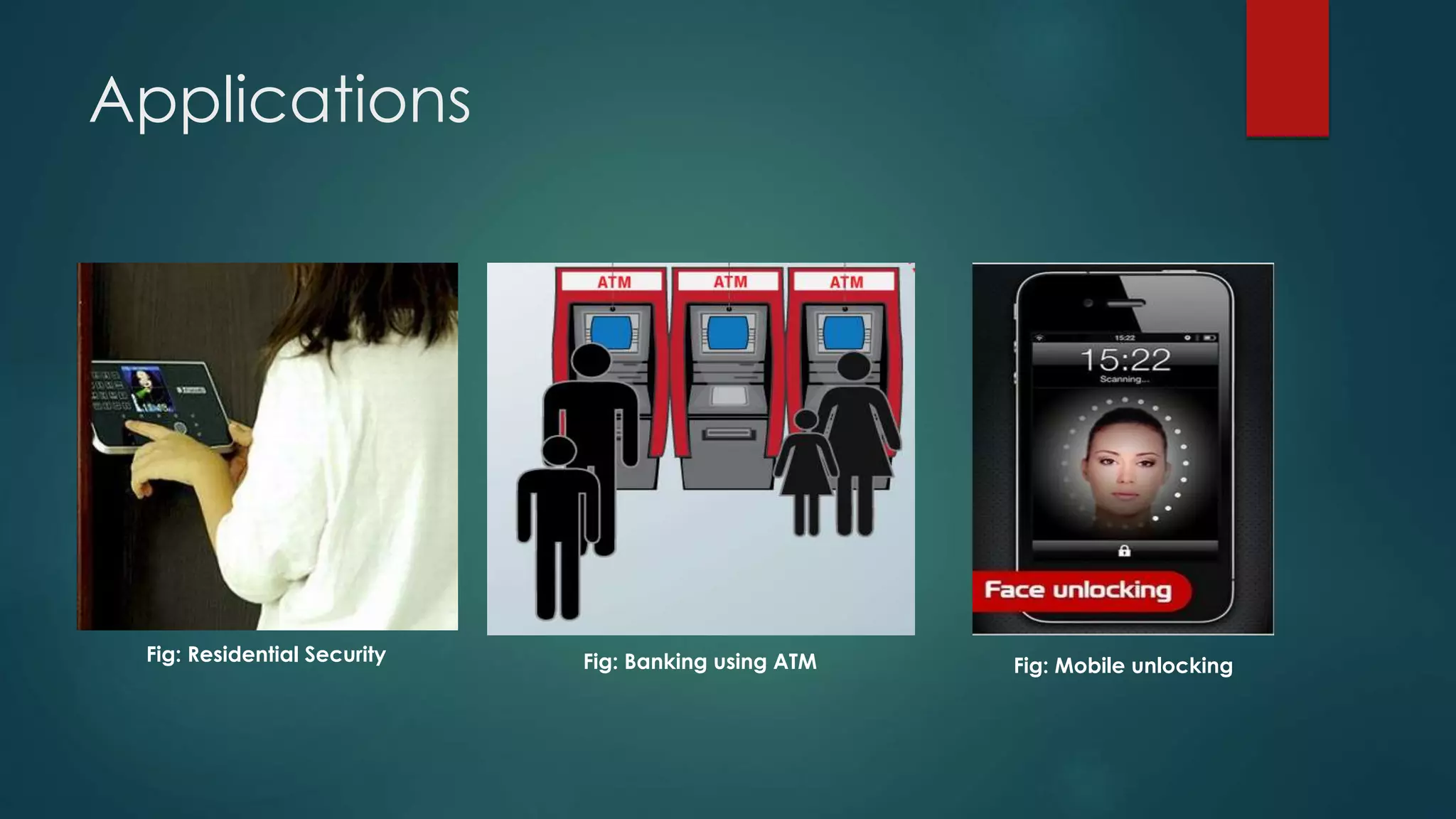
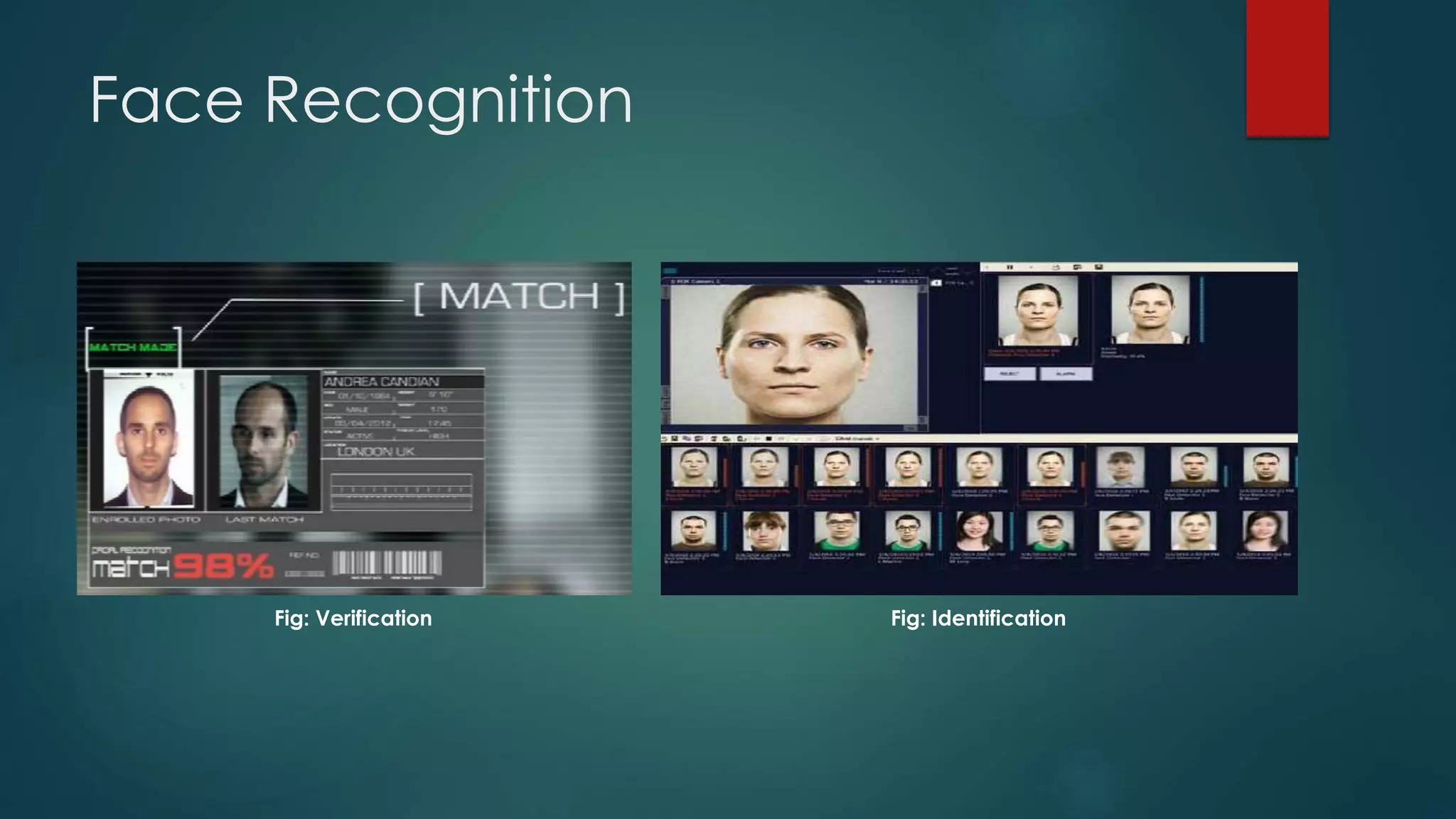
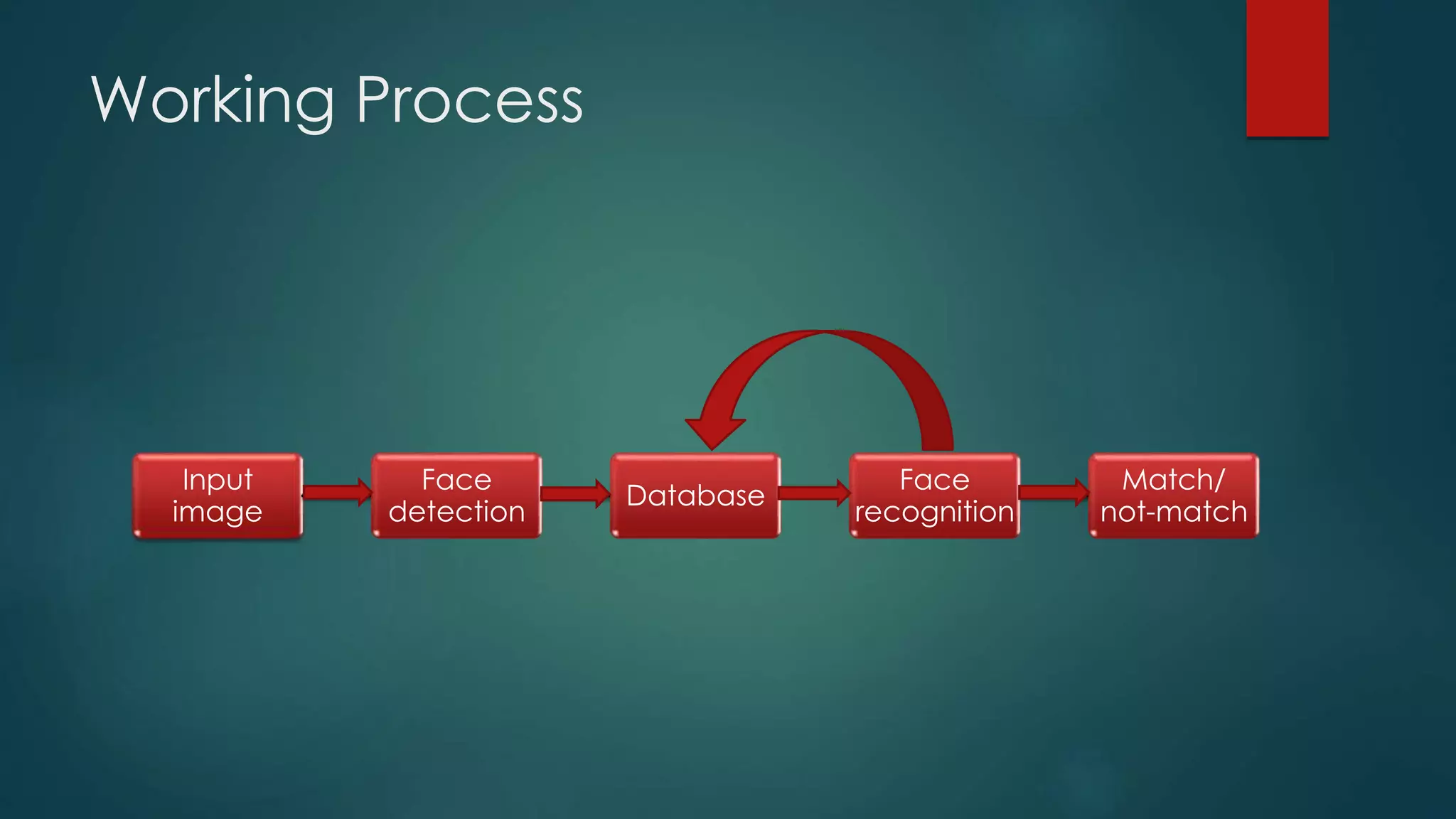
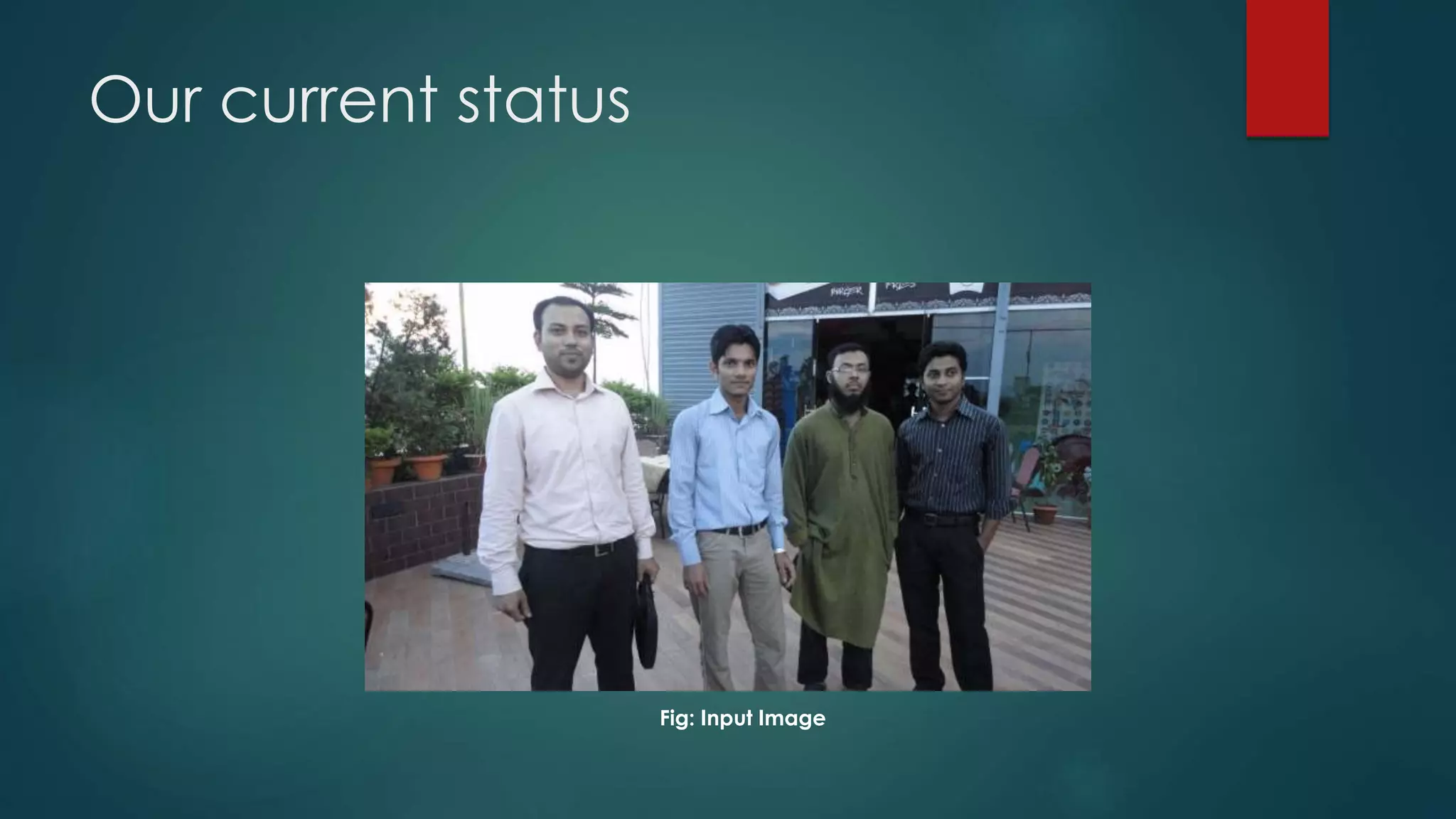
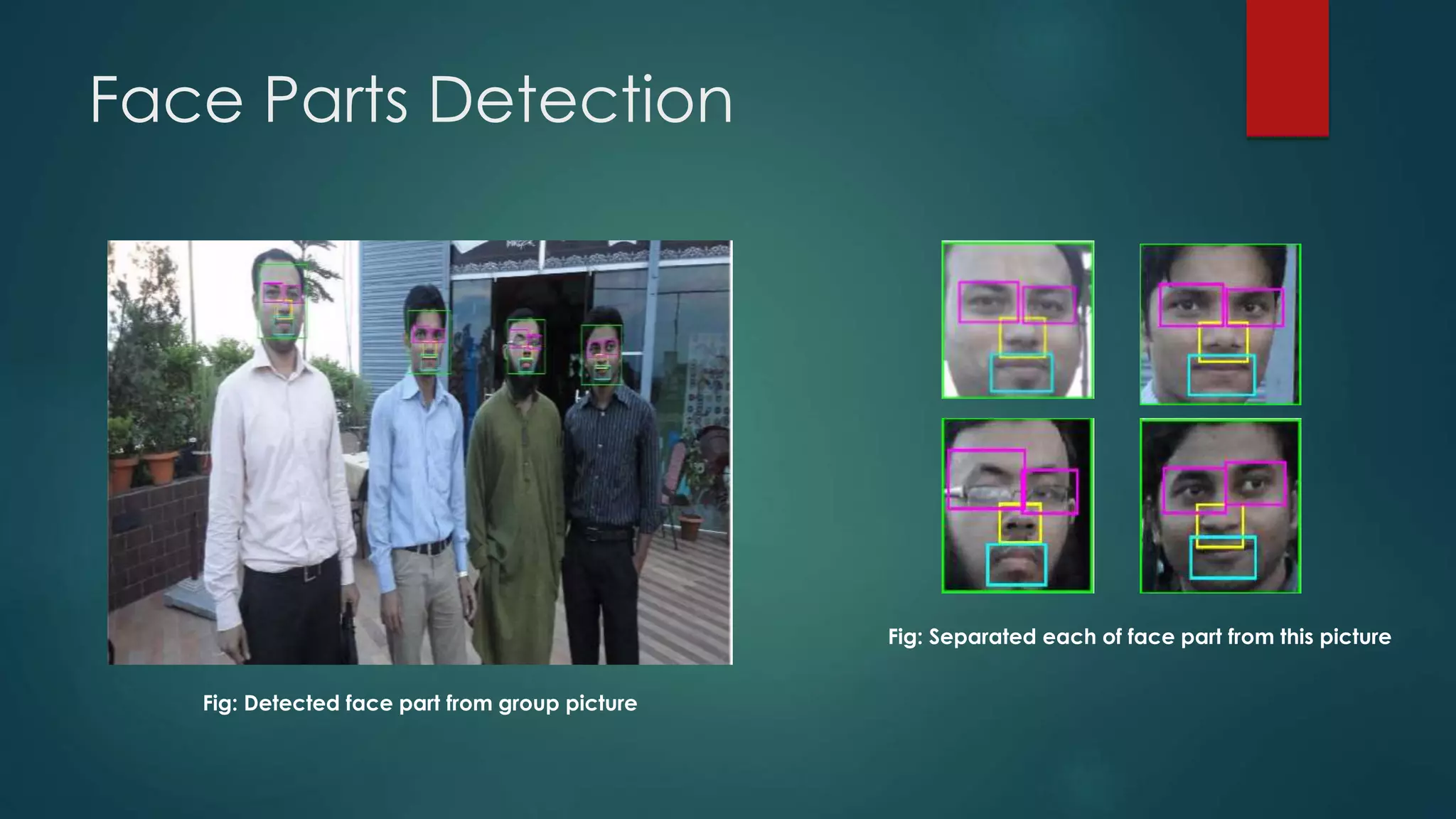
This document outlines a project on face recognition. It discusses biometrics and why face recognition was chosen over other methods. Applications of face recognition are presented for law enforcement, security, immigration, residential security, banking, and mobile unlocking. The working process of face recognition involves inputting an image, detecting the face, and recognizing the face by matching it to a database. The current progress includes detecting faces and face parts using a modified Viola-Jones algorithm. Future work will involve matching detected faces to images in a created database for recognition. Advantages of face recognition include convenience and limitations include inability to distinguish identical twins.