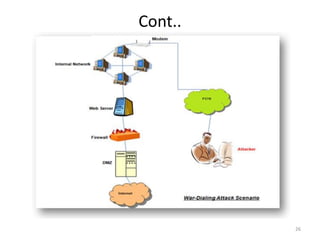
This document discusses various topics in advanced network security including:
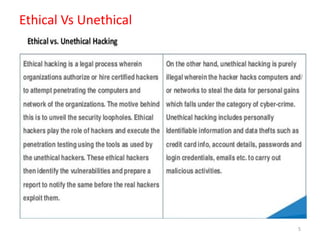
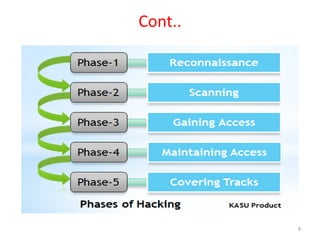
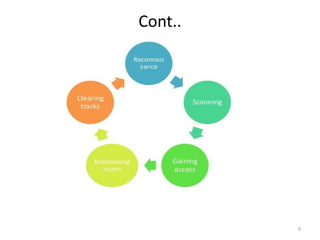
1) Ethical hacking and the phases of hacking including reconnaissance, scanning, gaining access, maintaining access, and erasing clues.
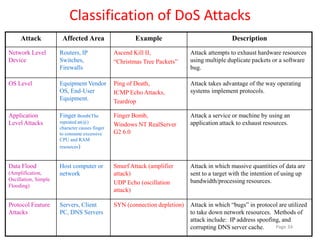
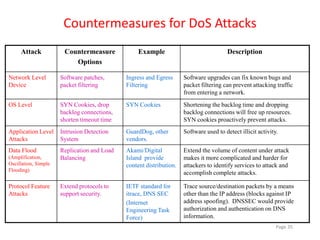
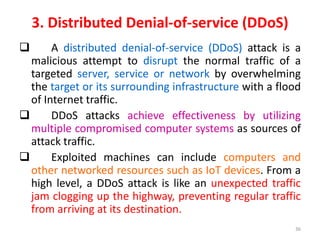
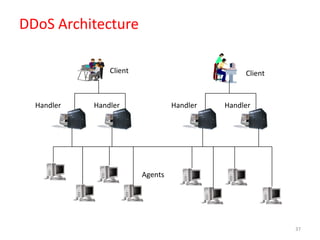
2) Denial of service (DoS) attacks and distributed denial of service (DDoS) attacks which aim to disrupt services by overwhelming targets.
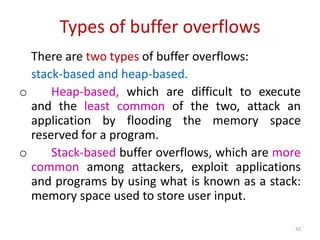
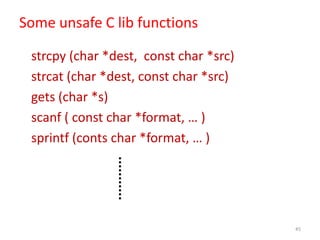
3) Buffer overflow attacks which can corrupt or overwrite data when a program attempts to store more data than a buffer can hold.