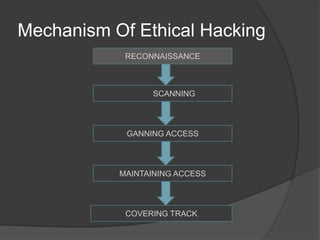
This document discusses ethical hacking. It defines security, hacking, and the different types of hackers including white hat, black hat, and gray hat hackers. It then explains ethical hacking as when computer experts test systems on behalf of owners to find vulnerabilities. The key stages of ethical hacking are reconnaissance, scanning, gaining access, maintaining access, and covering tracks. Benefits include increased security, while risks include hackers using knowledge for malicious purposes. Ethical hacking is in high demand in industries like national security, freelancing, and information technology companies.