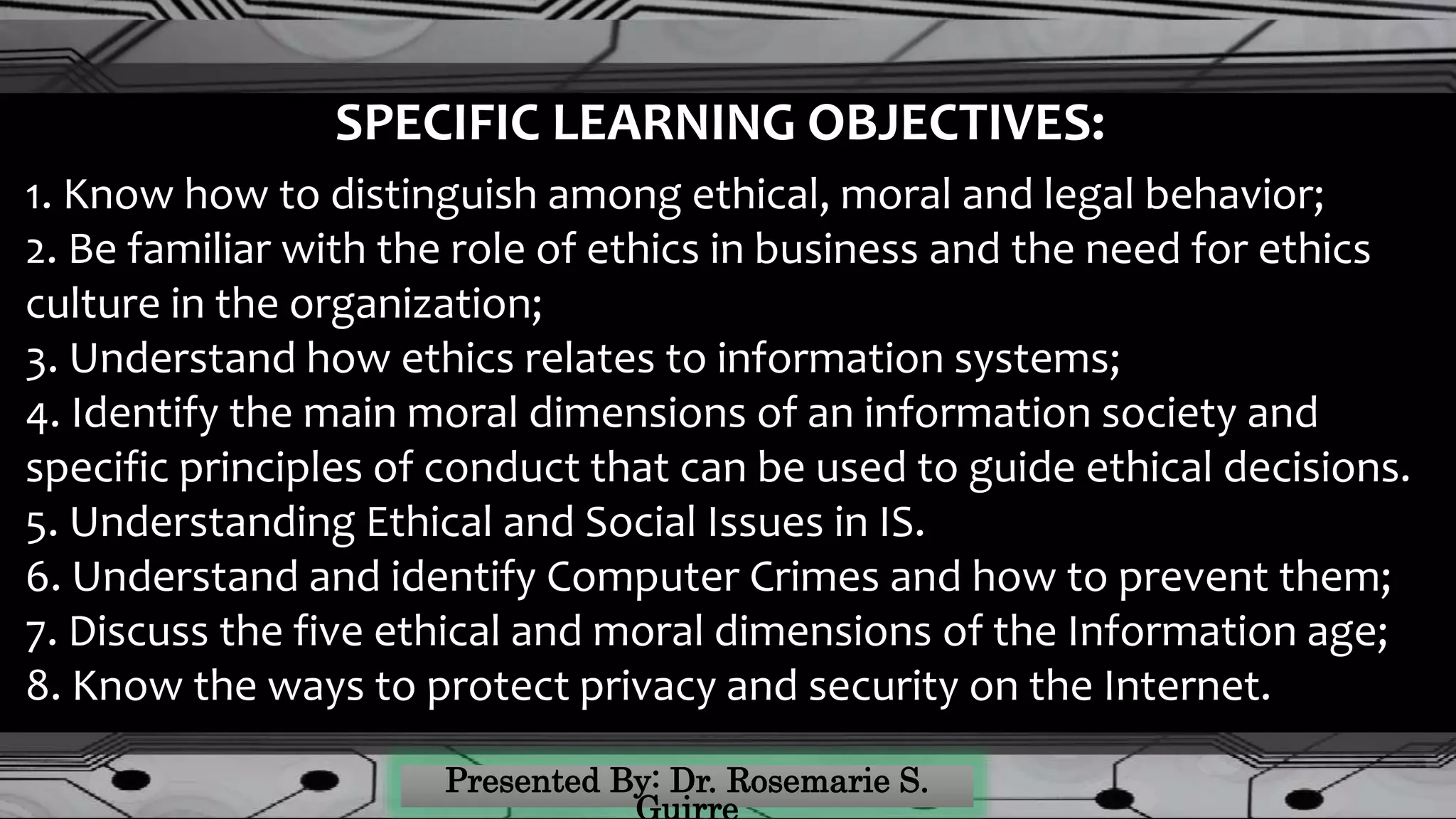
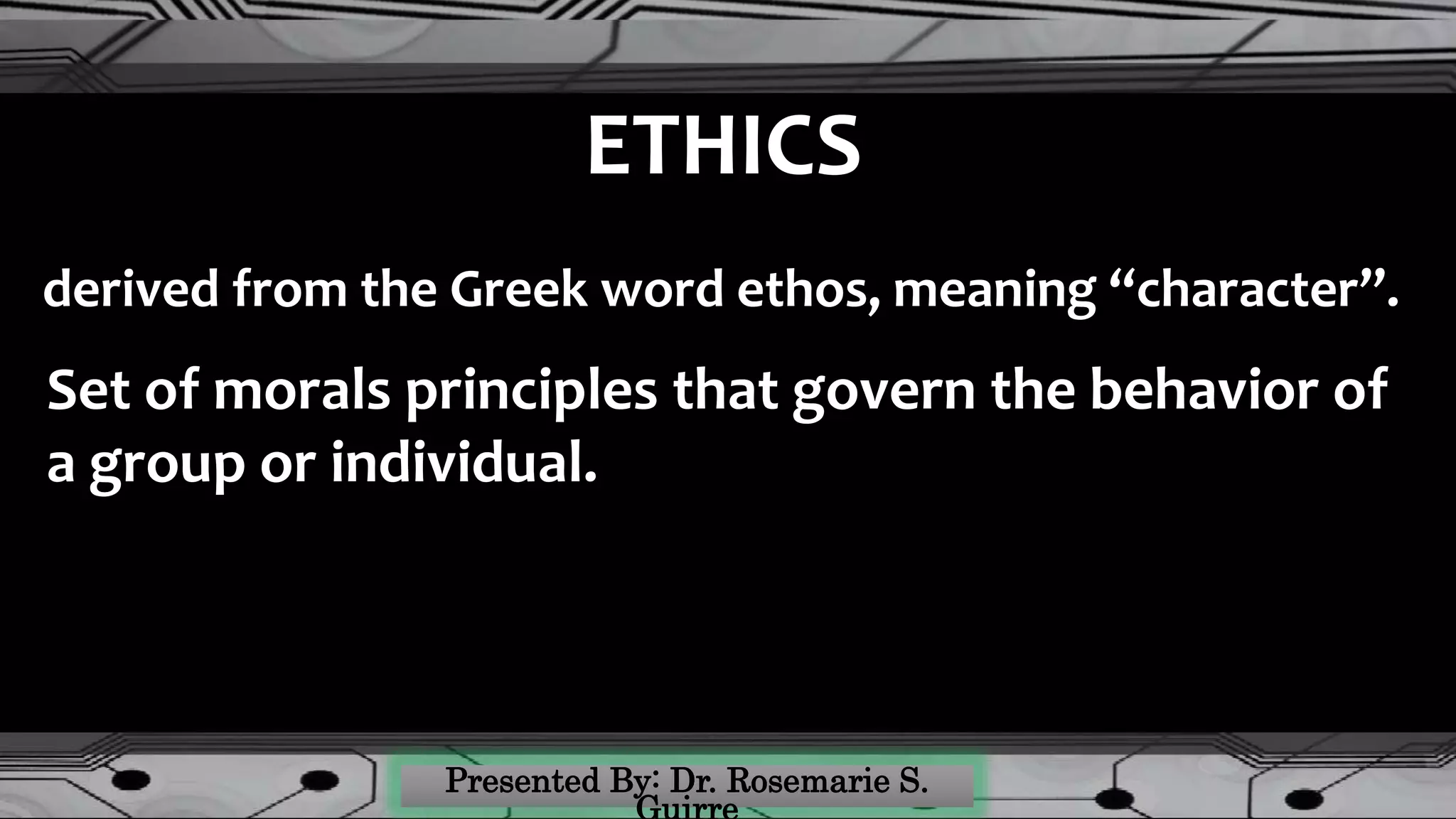
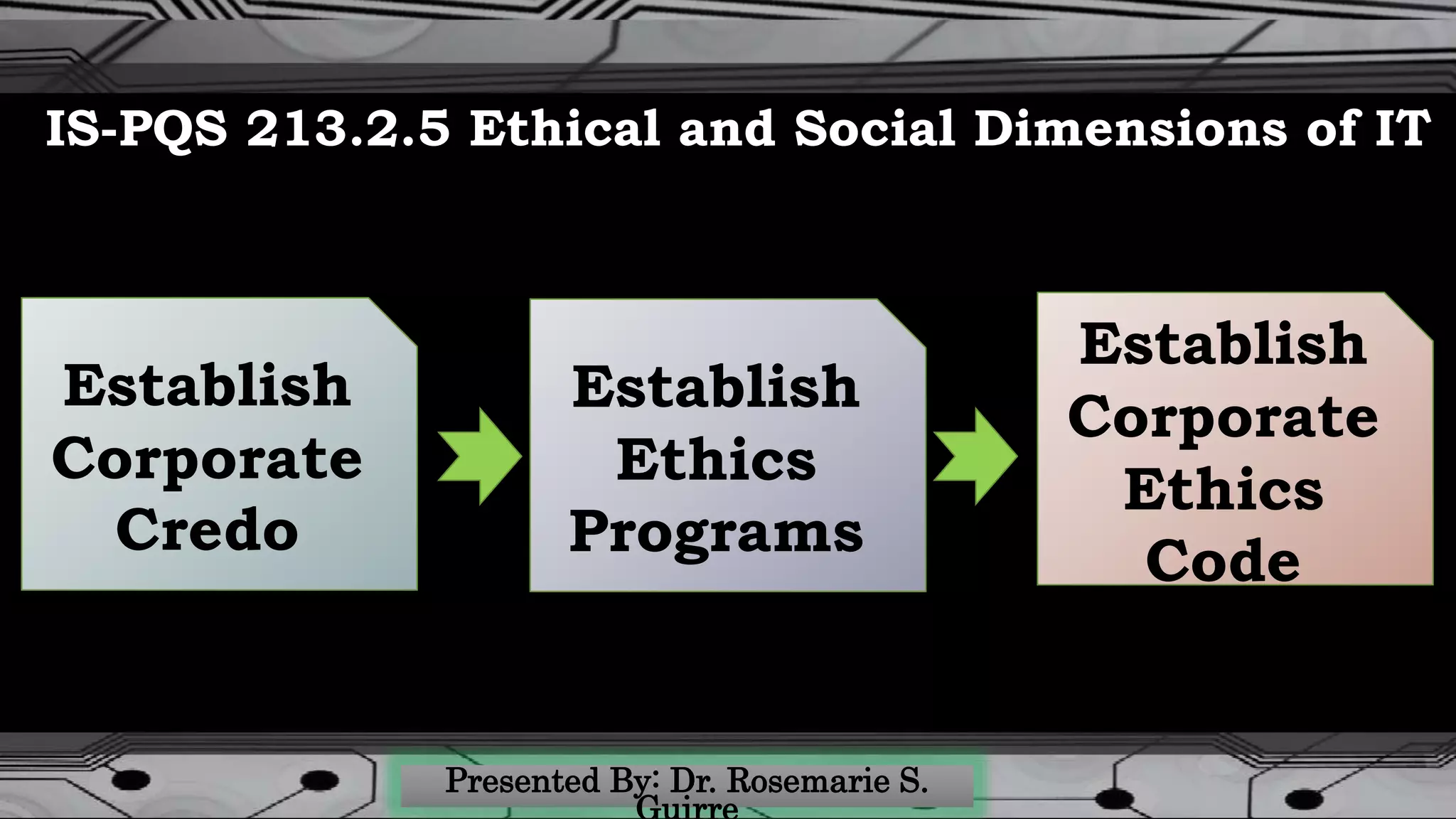
The document covers the ethical dimensions of information systems, emphasizing the distinction between ethical, moral, and legal behaviors, and highlighting the importance of an organizational ethics culture. It also addresses privacy, accuracy, property rights, and accessibility in the digital age, while providing guidelines for protecting personal information online. Additionally, it outlines commitments to various stakeholders within organizations and identifies common internet privacy issues and solutions.