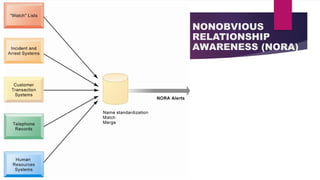
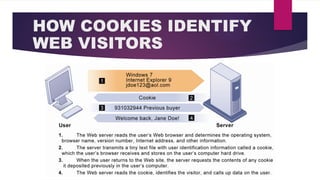
The document discusses the ethical and social issues arising from information systems, particularly in the context of the internet and electronic commerce. It outlines the five moral dimensions of the information age, challenges to privacy, and the implications of key technology trends on personal data and intellectual property rights. The document also emphasizes the need for ethical analysis frameworks to address the evolving landscape of information rights, accountability, and the societal impacts of technology.