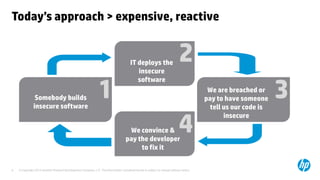
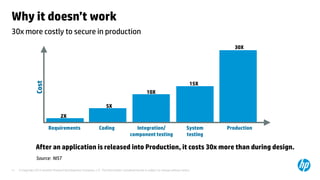
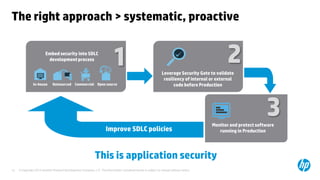
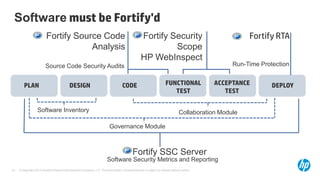
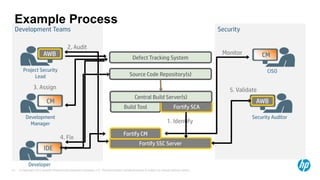
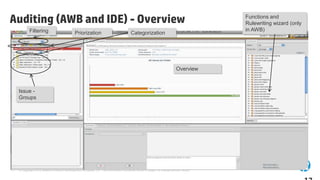
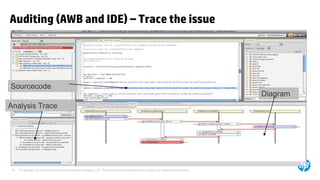
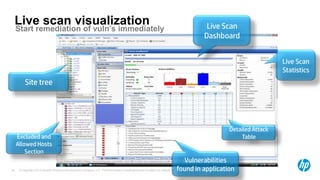
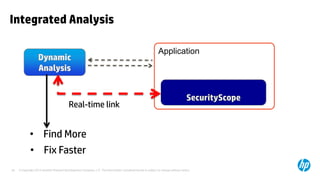
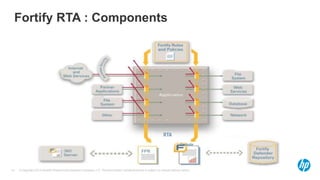
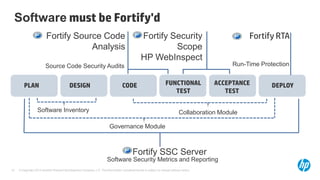
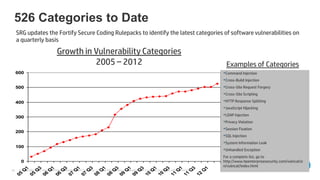
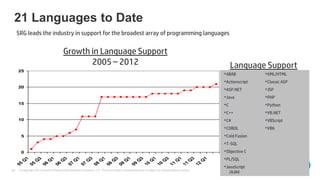
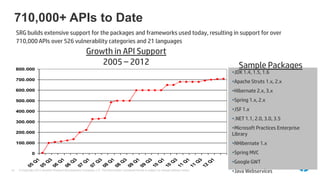
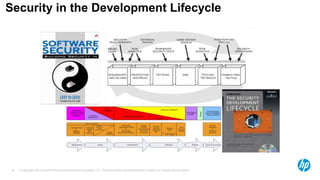
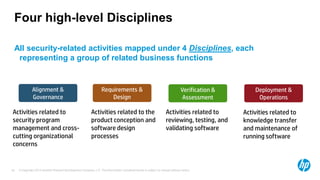
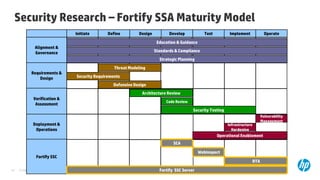
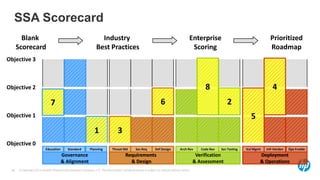
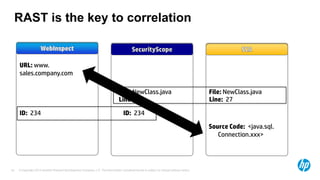
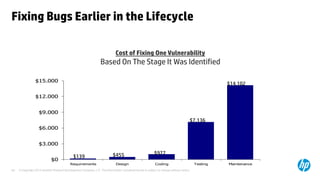
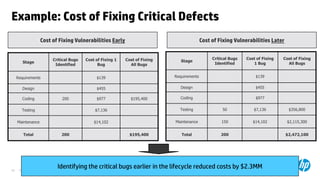
The document emphasizes the importance of integrating security into the software development lifecycle (SDLC) to reduce vulnerabilities and costs associated with software breaches. It discusses the shifting trends in security practices, highlighting the need for proactive measures such as continuous monitoring and the use of tools like HP Fortify for source code analysis and dynamic application security testing. The content also outlines best practices for software security assurance, aiming for reduced risks and improved security in both existing applications and new releases.