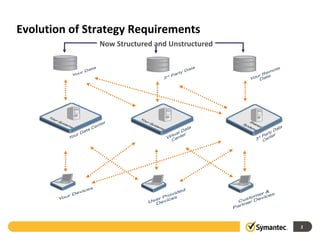
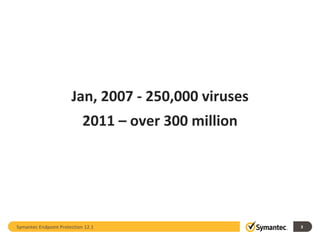
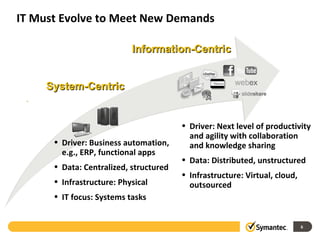
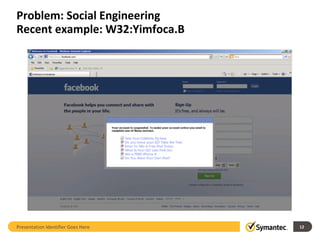
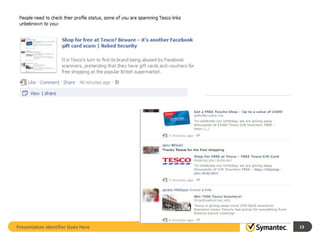
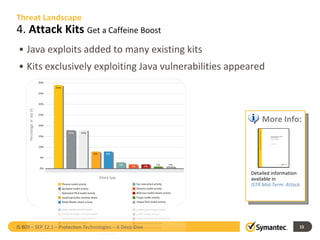
The document outlines the evolution of IT security in response to increasingly sophisticated attacks and changing infrastructure needs. It highlights key trends from 2011, such as the rise of targeted attacks, the integration of social networking into social engineering tactics, and vulnerabilities posed by mobile devices. Symantec's Endpoint Protection 12.1 is discussed as a strategic evolution in protection technologies to address these threats.