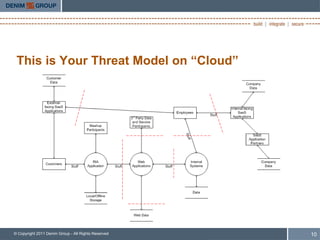
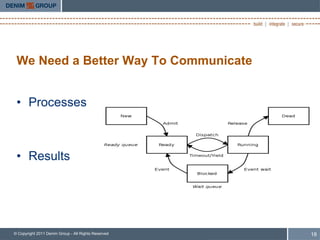
The document emphasizes the importance of open source security standards in mobile and cloud environments, highlighting the risks and benefits associated with mobile applications and cloud deployments. It discusses the challenges faced by organizations in assessing software security, the need for better communication of security assurance, and recent developments in security standards such as OWASP's Application Security Verification Standard and Penetration Testing Execution Standard. Ultimately, it calls for improved collaboration between application providers and consumers to ensure a better understanding of security requirements and risks.