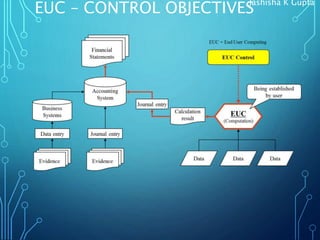
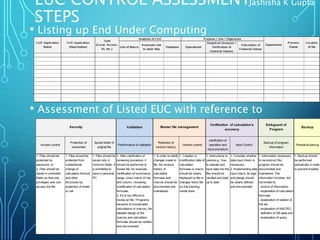
This document discusses challenges around end-user computing (EUC) applications and provides guidance on controlling and managing them. It notes that while EUCs provide benefits like flexibility, they can be difficult to manage and control effectively. It then provides objectives for EUC control, such as maintaining an inventory of applications and appropriately managing security, development, and data validation for critical applications. Finally, it outlines steps for assessing EUC control, including reviewing areas like validation, access control, backup procedures, and input controls. The overall purpose is to help organizations better govern user-developed applications and safeguard the reliability of information and financial reporting.