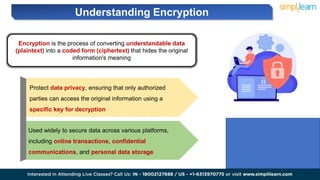
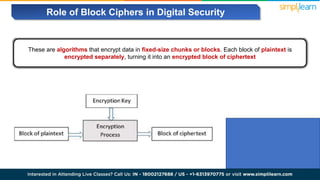
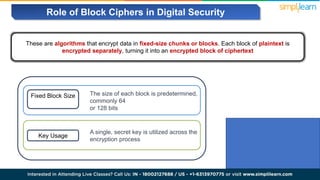
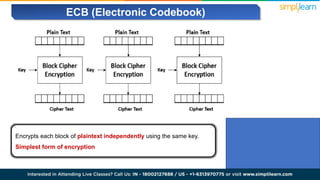
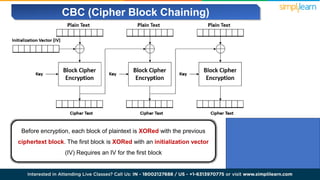
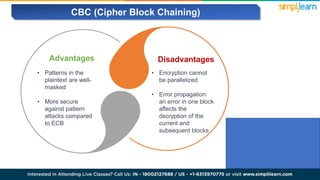
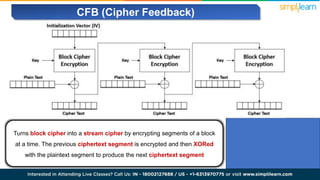
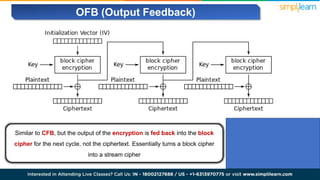
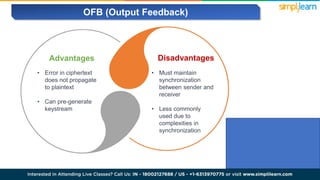
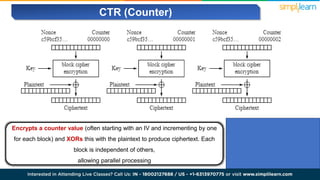
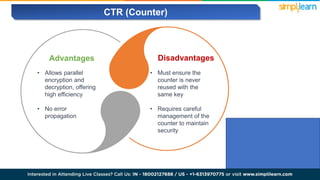
The document explains encryption, emphasizing its role in securing data by converting plaintext into ciphertext using algorithms called block ciphers. It details the importance of understanding different modes of operation, such as ECB, CBC, CFB, OFB, and CTR, each offering unique advantages and disadvantages in processing and security. The text also highlights the necessity of employing specific key sizes and methods to enhance data privacy and prevent unauthorized access.