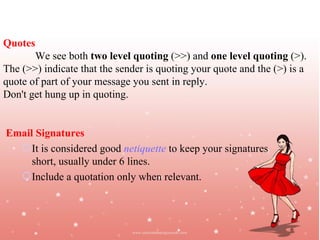
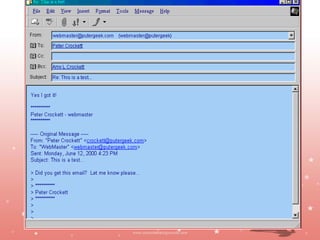
The document discusses email etiquette and proper email drafting. It provides tips for writing concise emails, such as getting to the point quickly without leaving out important details. It also recommends replying to emails within 24 hours and asking permission before attaching files due to virus risks. The document advises avoiding all-caps text, which can come across as shouting, and limiting email signatures to under 6 lines. Proper email etiquette is important to avoid miscommunication and make good impressions through written correspondence.










![ Do not use the following as subjects:
[blank]
Hi, Hey, Hello, How are you?
FW: FW: Re: [Old subject line]
Write short and catchy headlines in the Subject to
entice people to read the e-mail.
When no subject is included, some e-mail services
deliver the message to junk mail
Jayanth Jagadeesh
Asst. Director – Outreach
ISiM - Mysore](https://image.slidesharecdn.com/email-120709000601-phpapp02/85/Email-12-320.jpg)