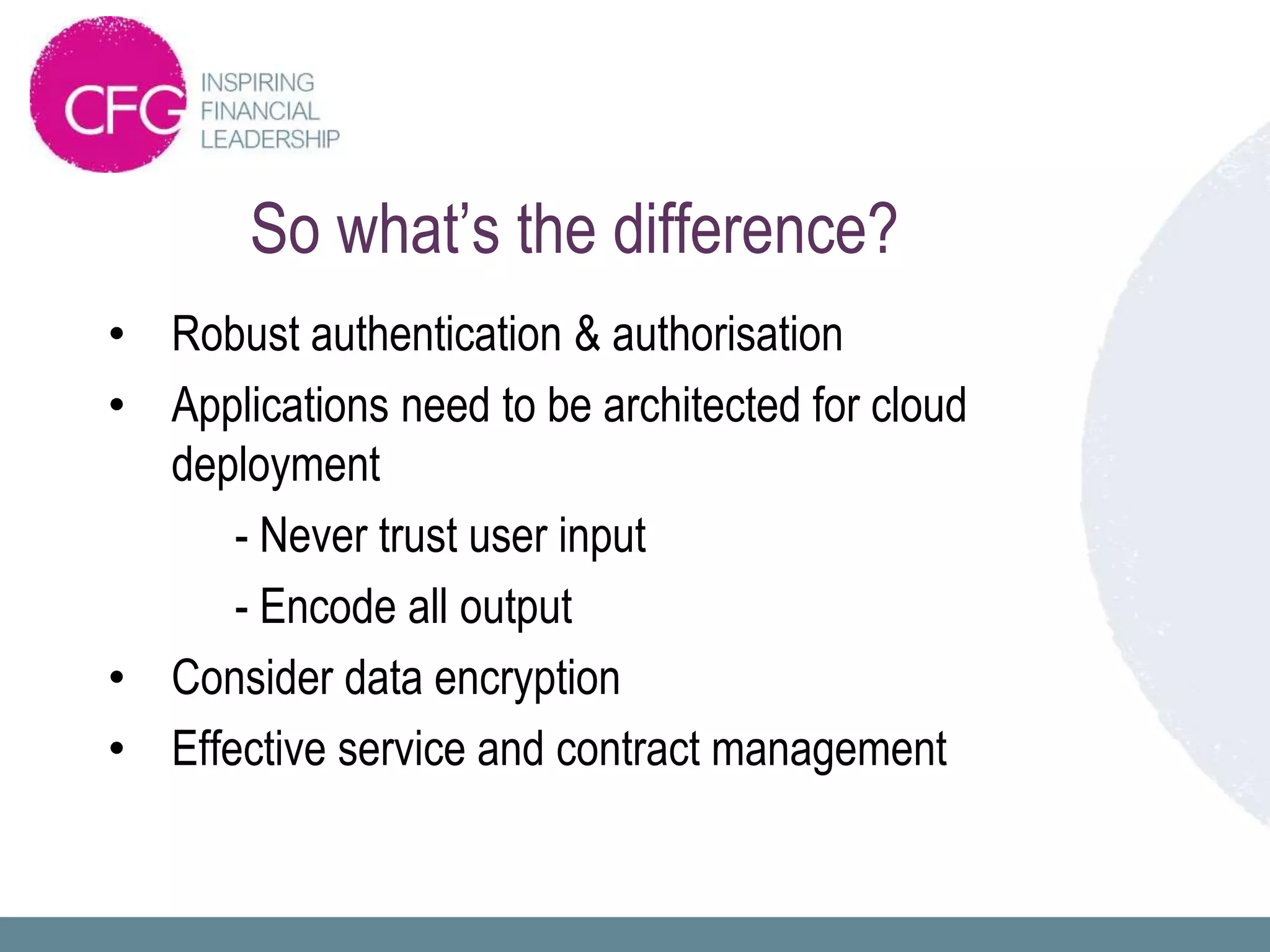
This document discusses cloud security and addresses common concerns organizations have in moving to the cloud. It begins by defining cloud computing and its key characteristics like on-demand access to resources and rapid elasticity. It then asks what could go wrong with cloud security and lists some scepticisms organizations have around security, complexity, and resistance to change. However, it notes cloud usage is still rising significantly. It raises questions around who is managing services after hours and whether security models and risk understanding are sufficient. The document advocates that professionally built cloud services can offer more robust security that is designed in from the start and benefits from expert ongoing management.

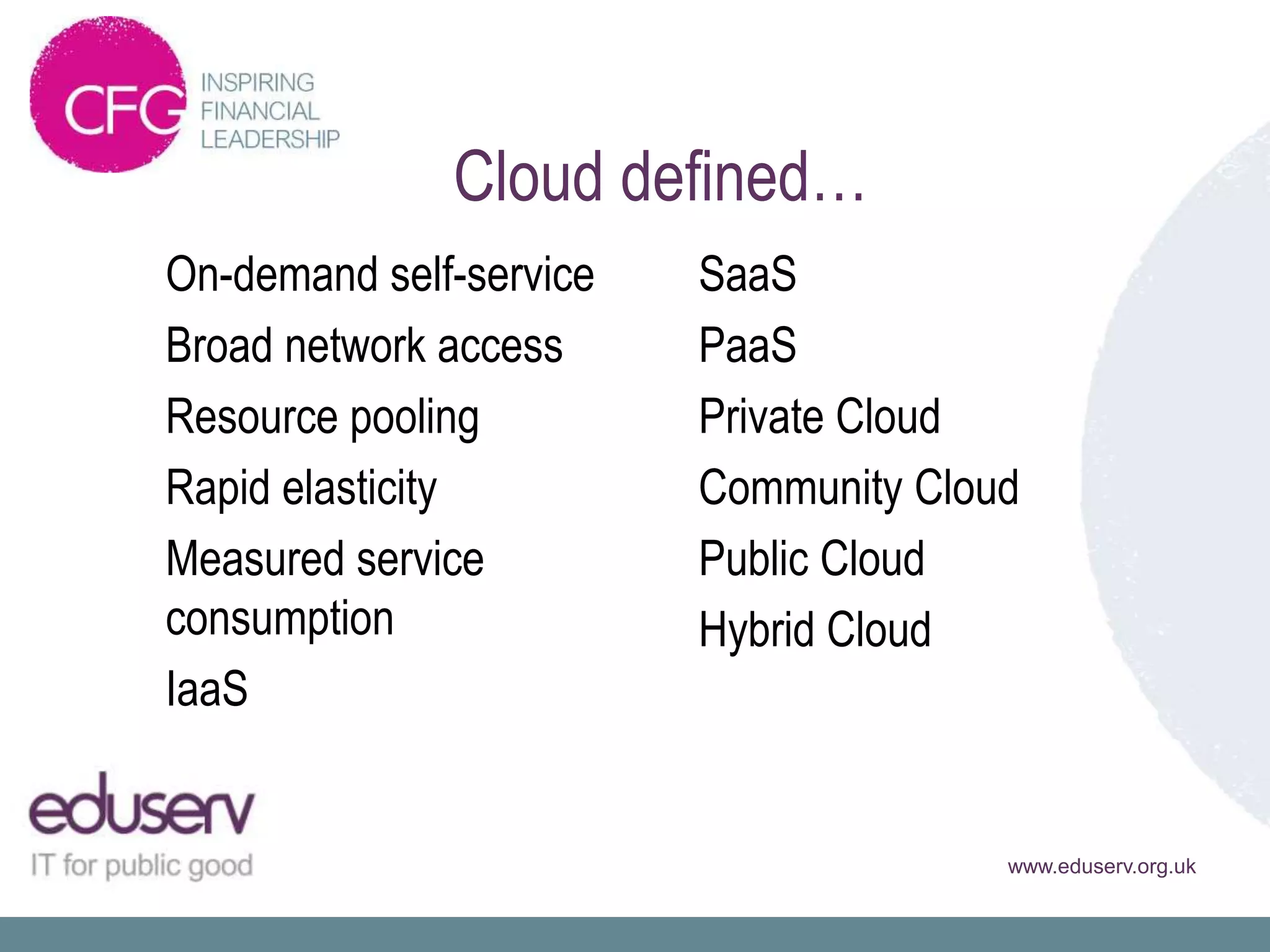
![Cloud defined…
Cloud computing is a model for enabling
ubiquitous, convenient, on-demand network access
to a shared pool of configurable computing resources
(e.g., networks, servers, storage, applications, and
services) that can be rapidly provisioned and
released with minimal management effort or service
provider interaction.
[National Institute of Standards and Technology]
www.eduserv.org.uk](https://image.slidesharecdn.com/edzedlewski-130320101956-phpapp01/75/4B-Is-the-cloud-safe-Ed-Zedlewski-2-2048.jpg)