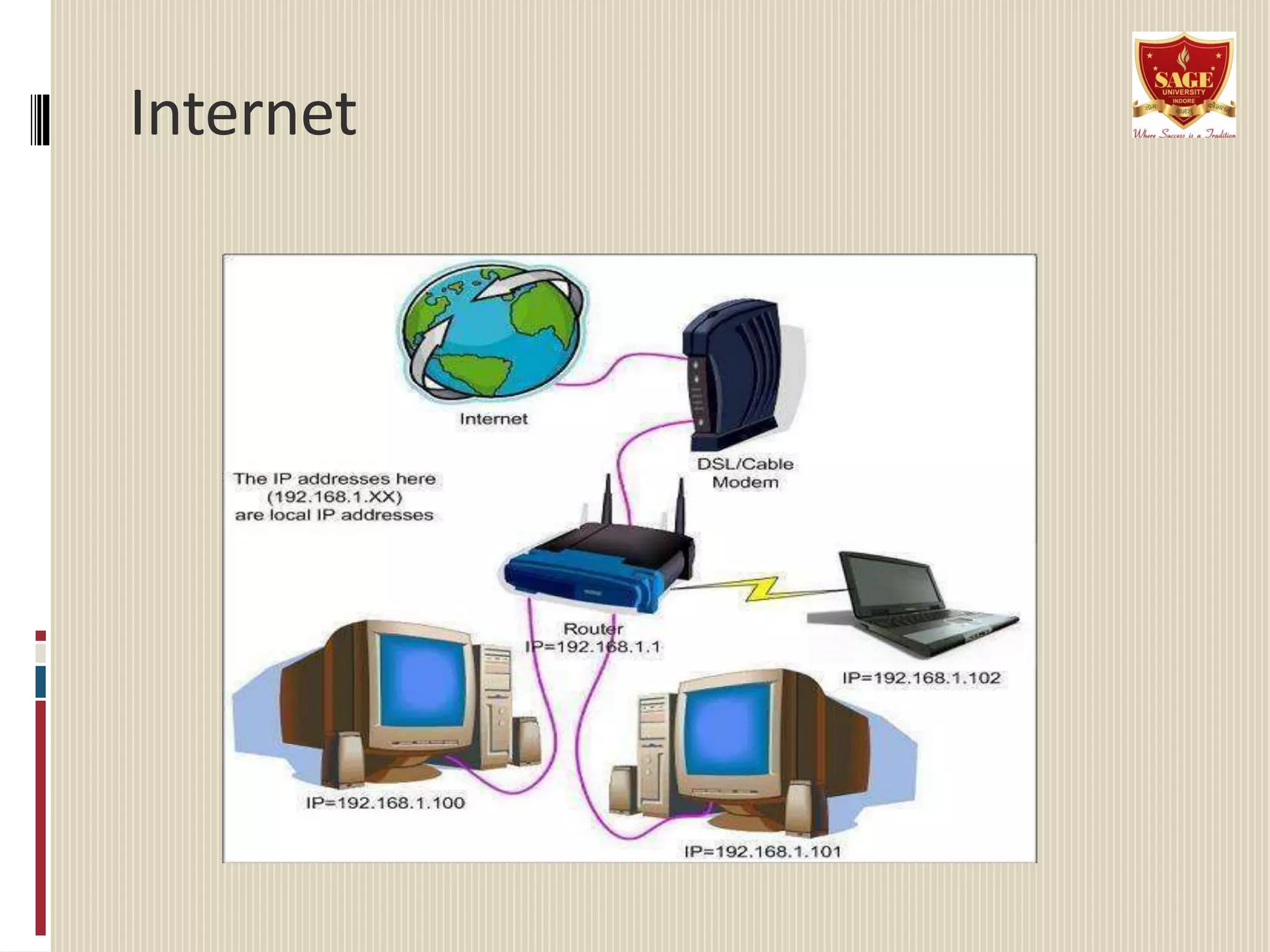
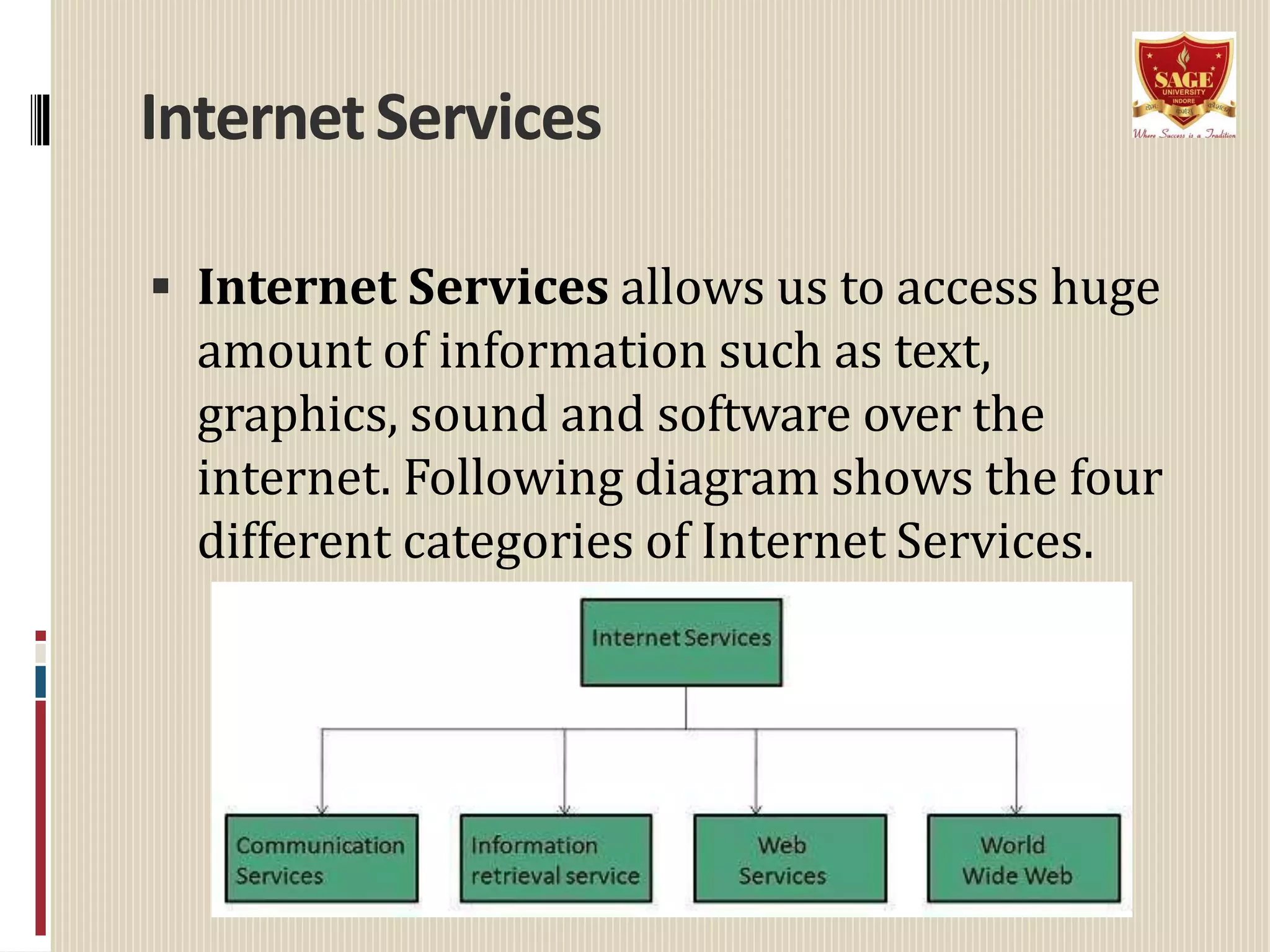
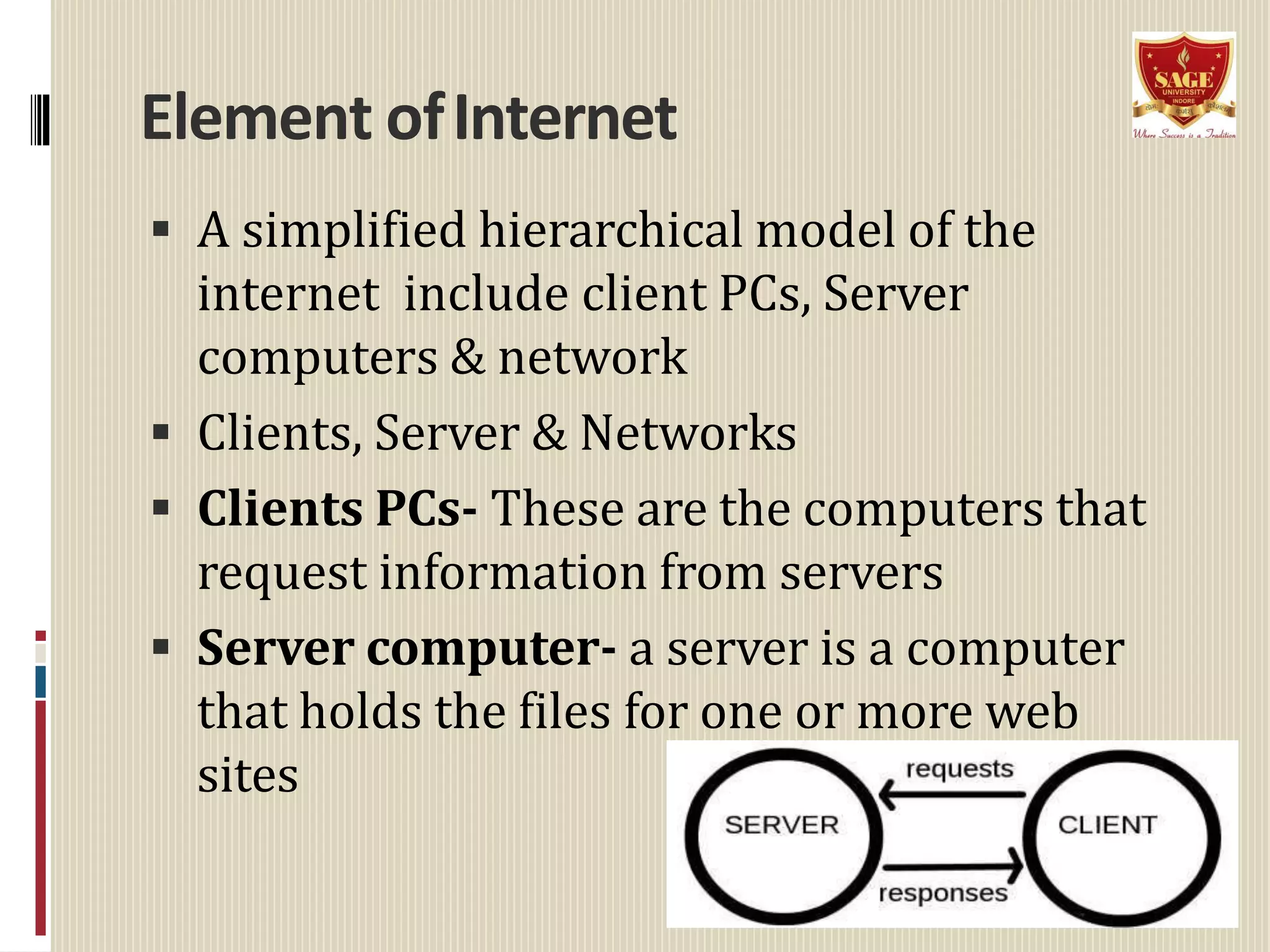
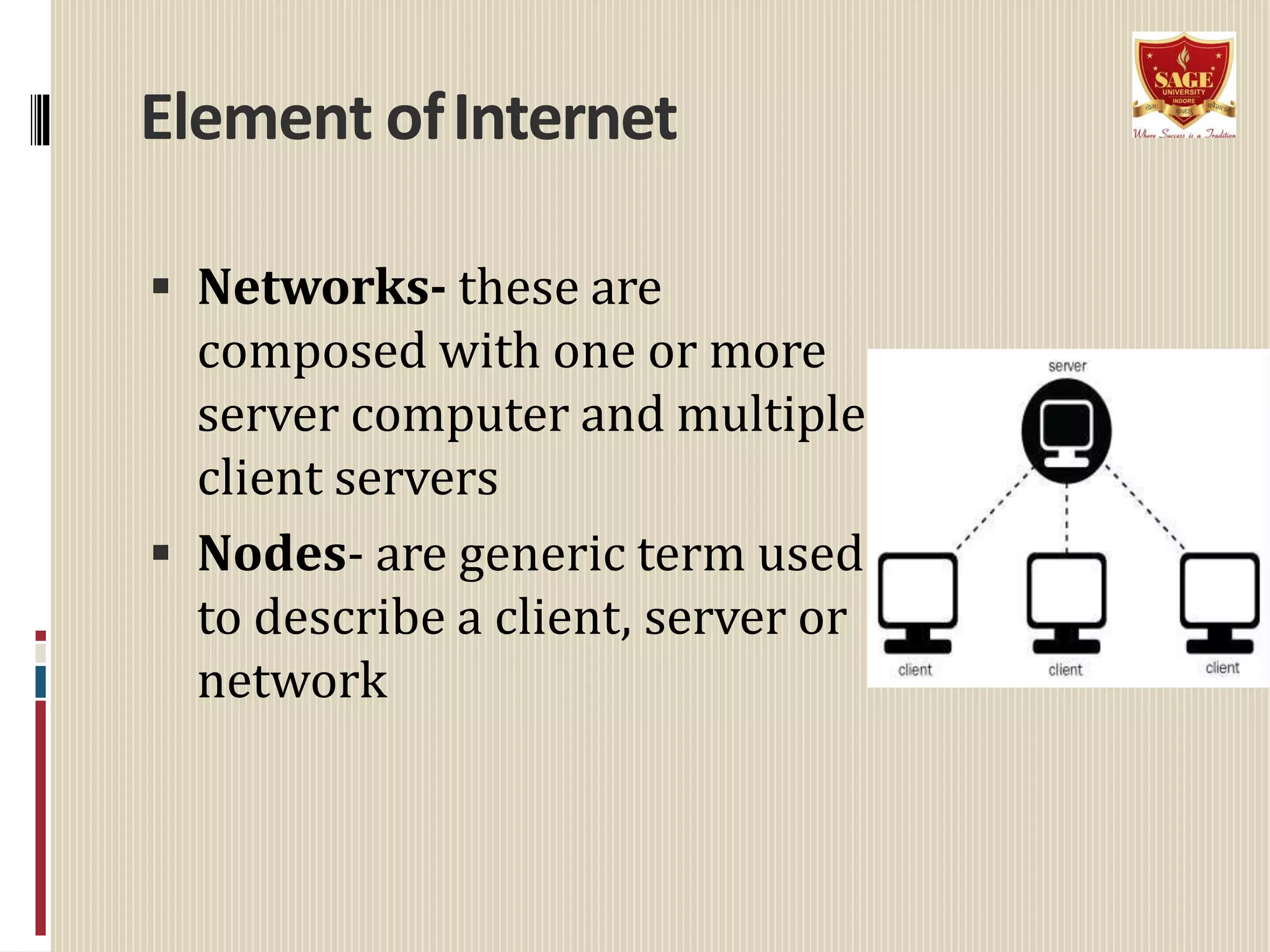
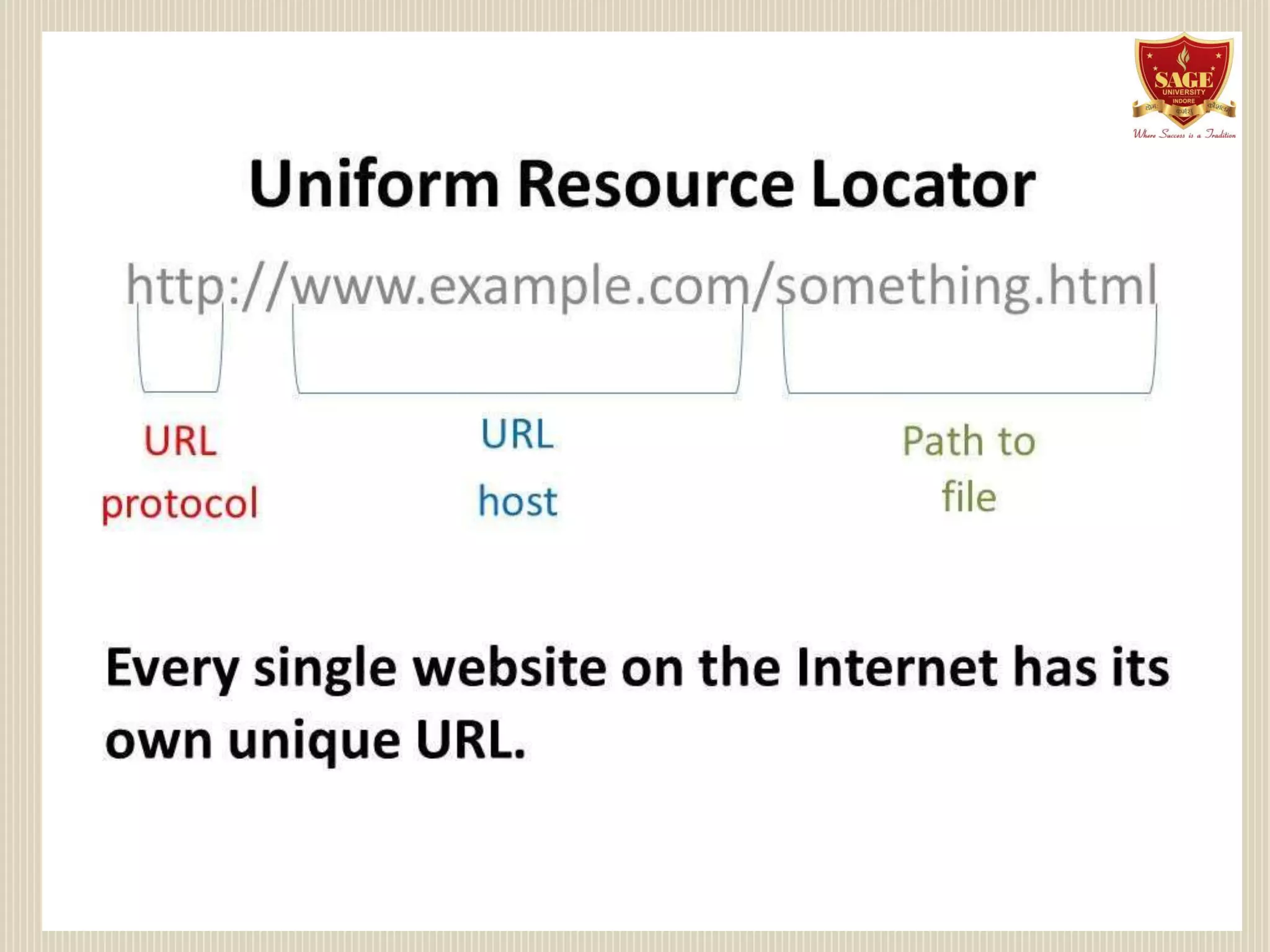
The document provides information about the internet including its origin, components, services, protocols, and impact. It describes how the internet began as a US Department of Defense network called ARPANET that later expanded to include universities and research institutions. Key components that enable the internet include clients, servers, networks, and nodes. Services like email, FTP, and the World Wide Web allow sharing of information. Protocols like IP and TCP/IP define how data is transmitted. The rise of the World Wide Web in the 1990s increased accessibility of internet resources. The internet has significantly impacted society through online communication, commerce, and access to information but has also enabled new forms of cybercrime.