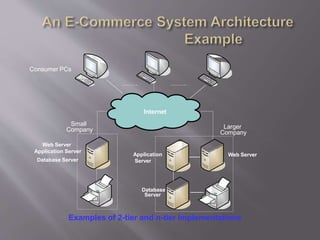
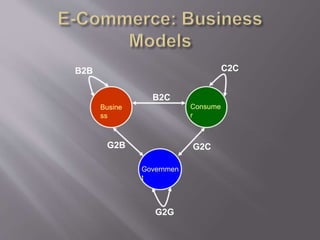
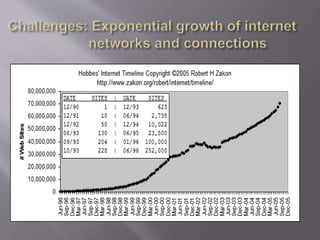
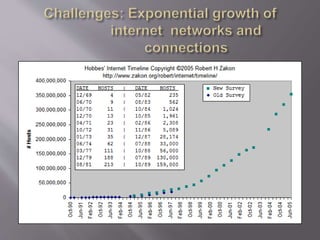
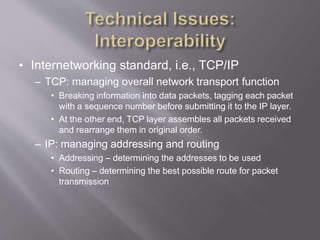
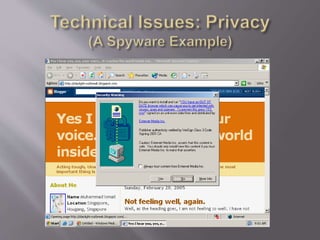
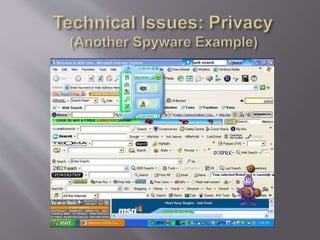
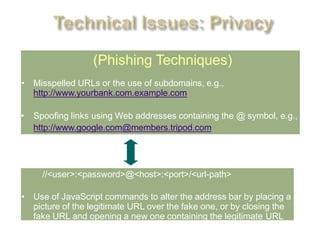
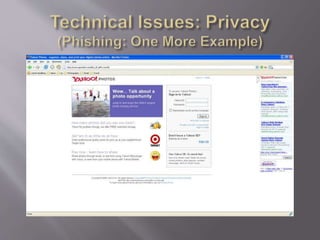
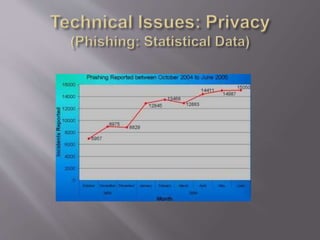
This document discusses key concepts related to cyber laws and rights in e-commerce. It covers what e-commerce is, important business models, and challenges. Some challenges discussed include technical issues, security threats like denial of service attacks and viruses, privacy concerns, and legal issues around intellectual property and consumer protections. Trust is also highlighted as an important barrier that must be addressed for e-business to be successful. Overall infrastructure development, relevant laws and regulations, consumer advocacy groups, education, and growing the IT workforce are emphasized as important tasks to realize the full potential of e-commerce.