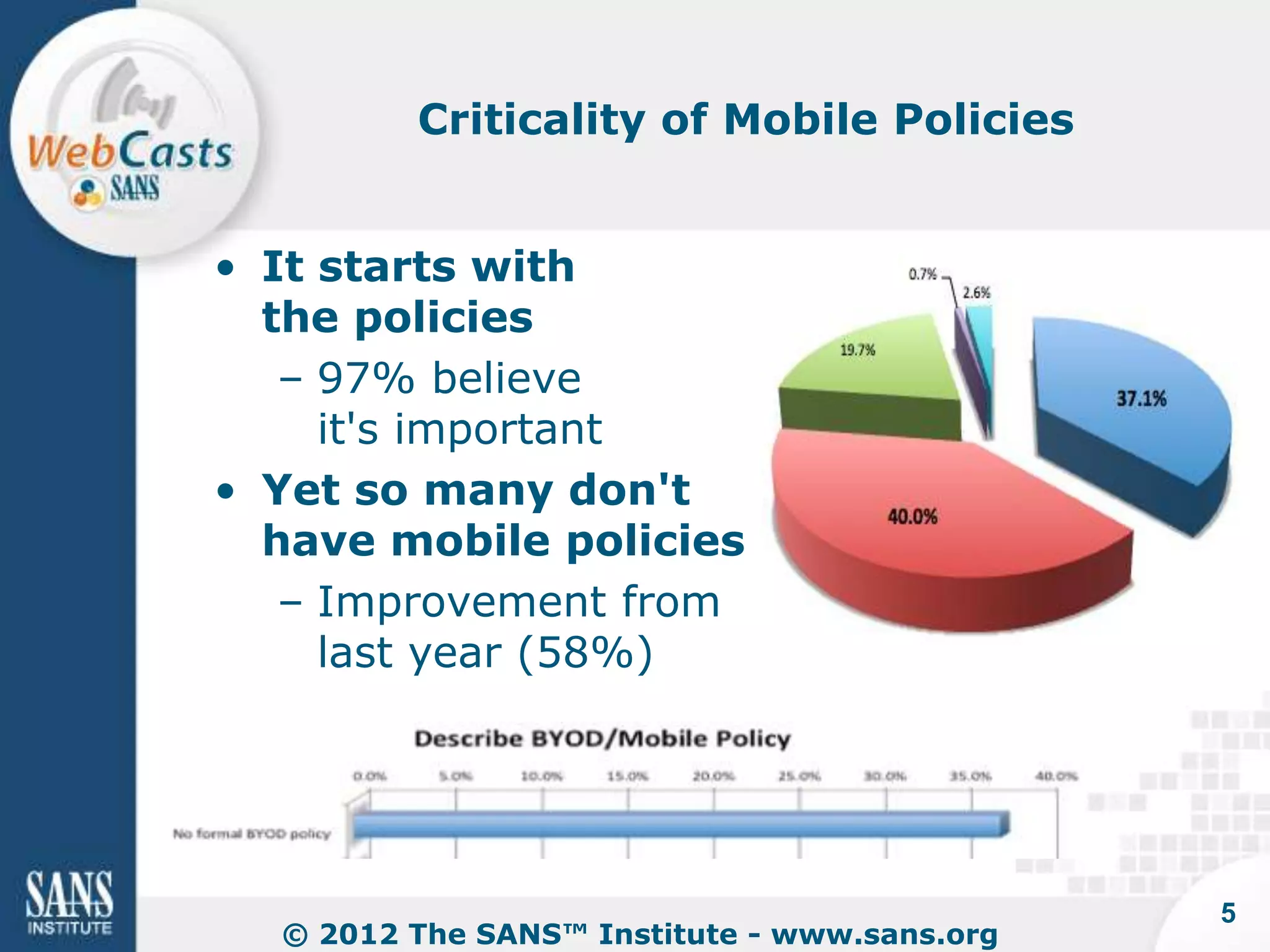
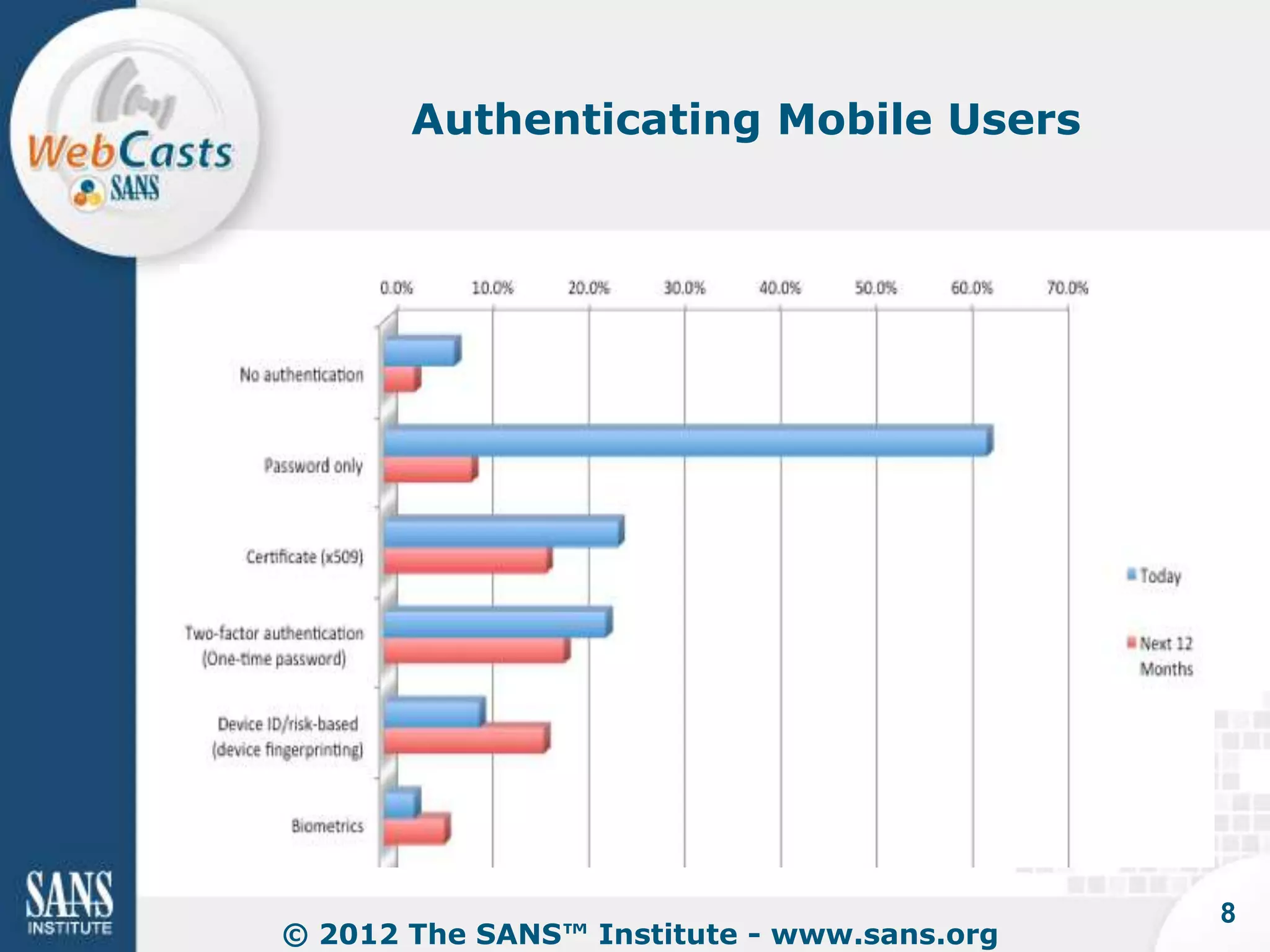
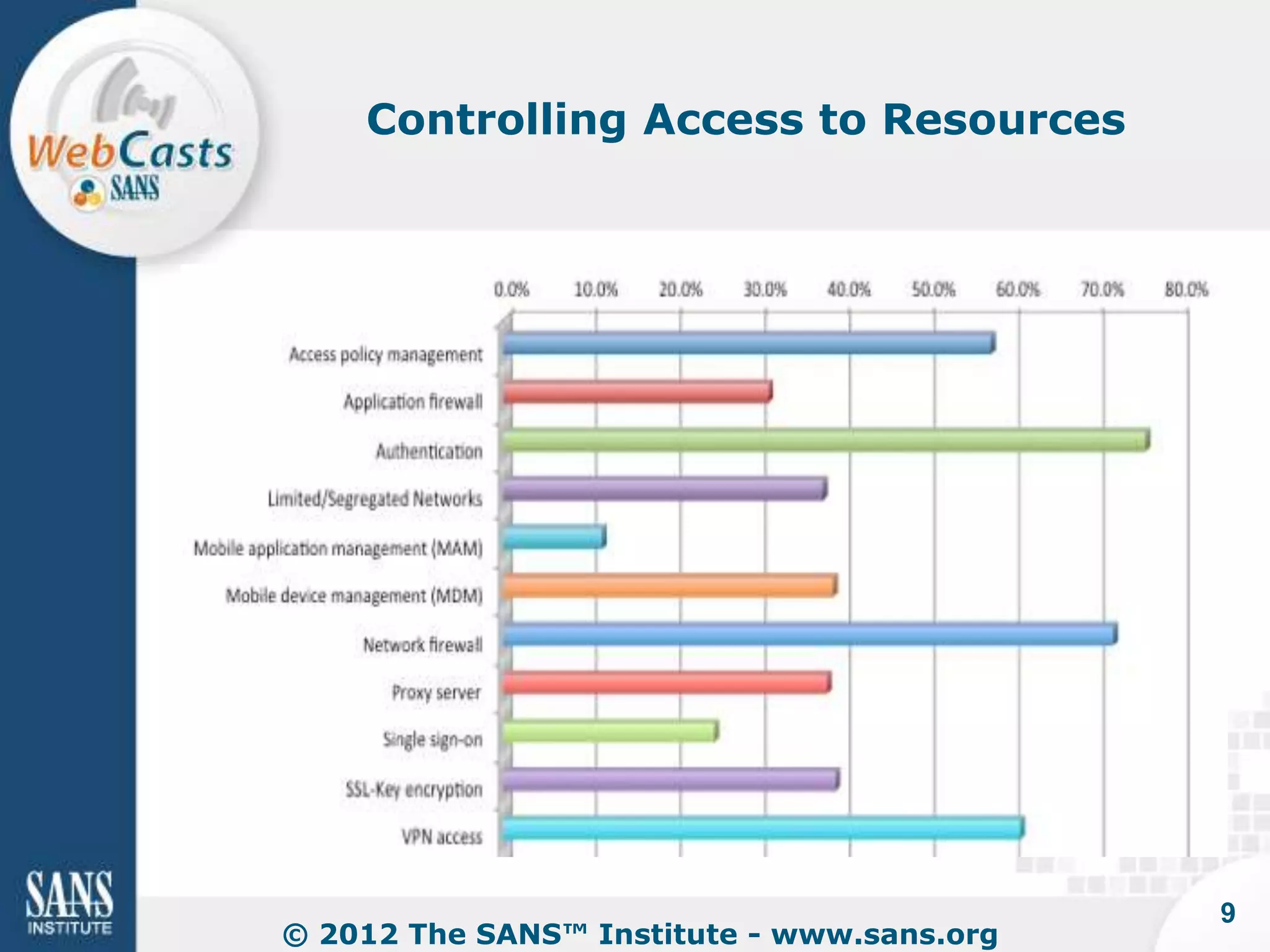
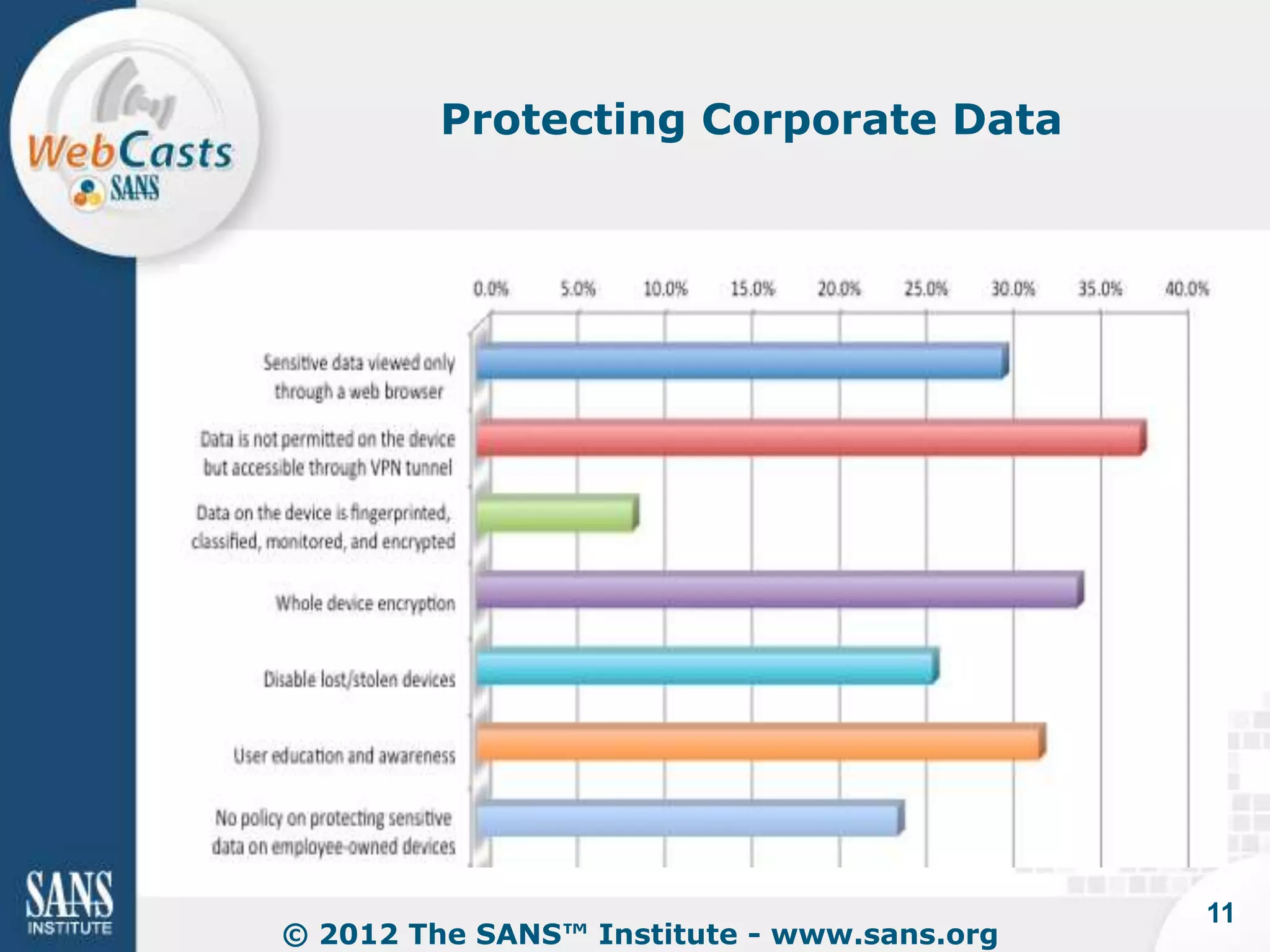
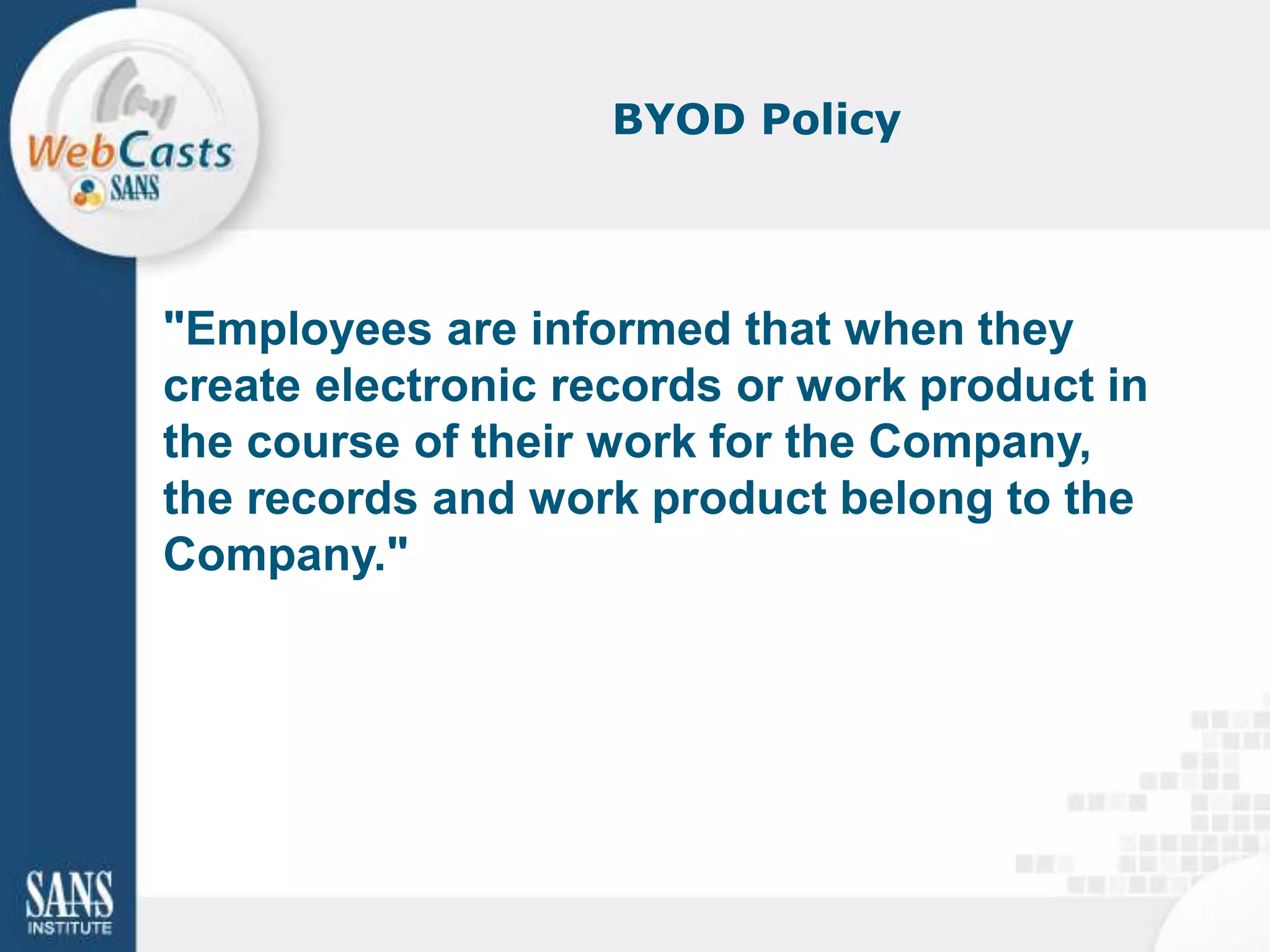
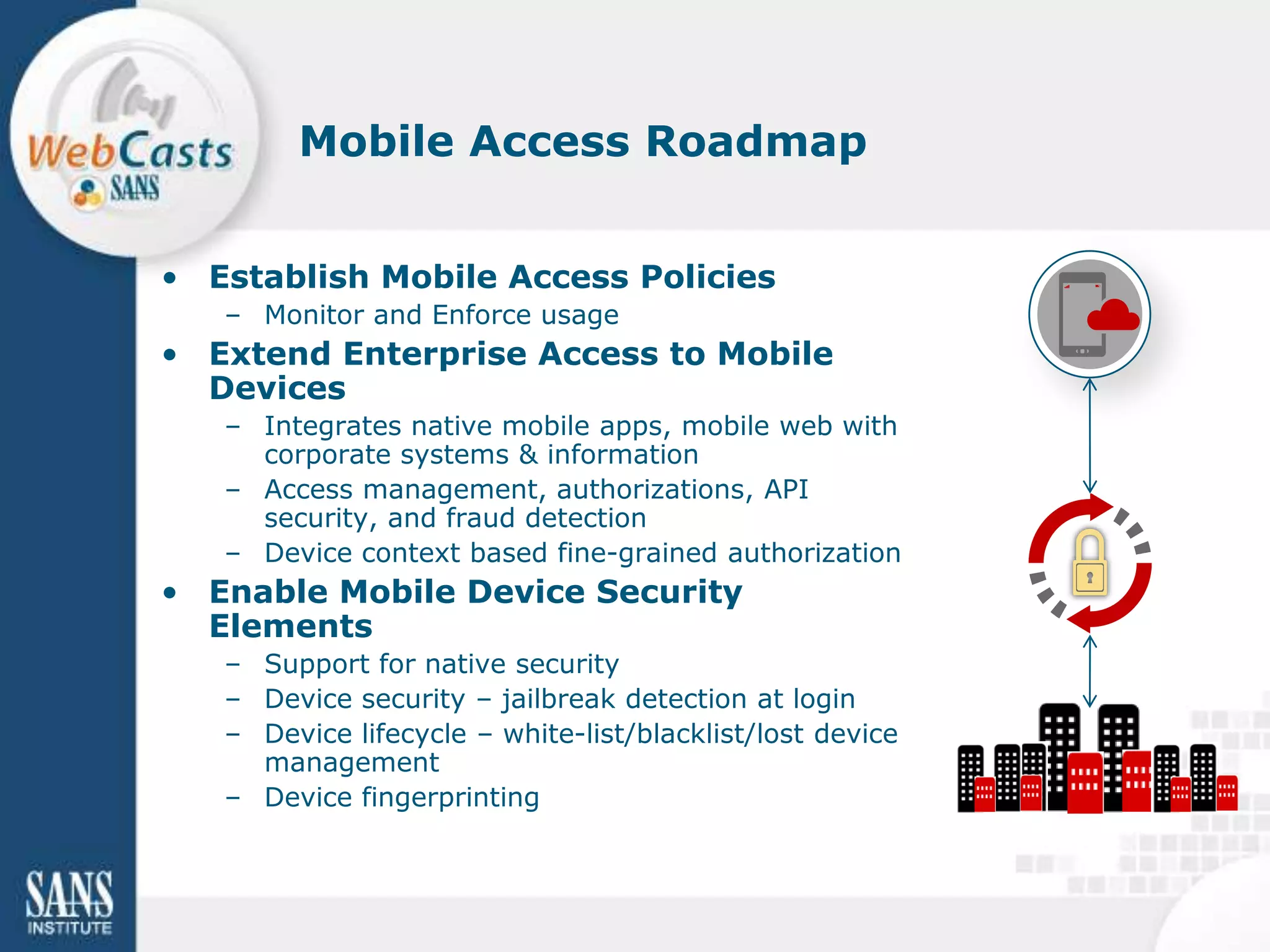
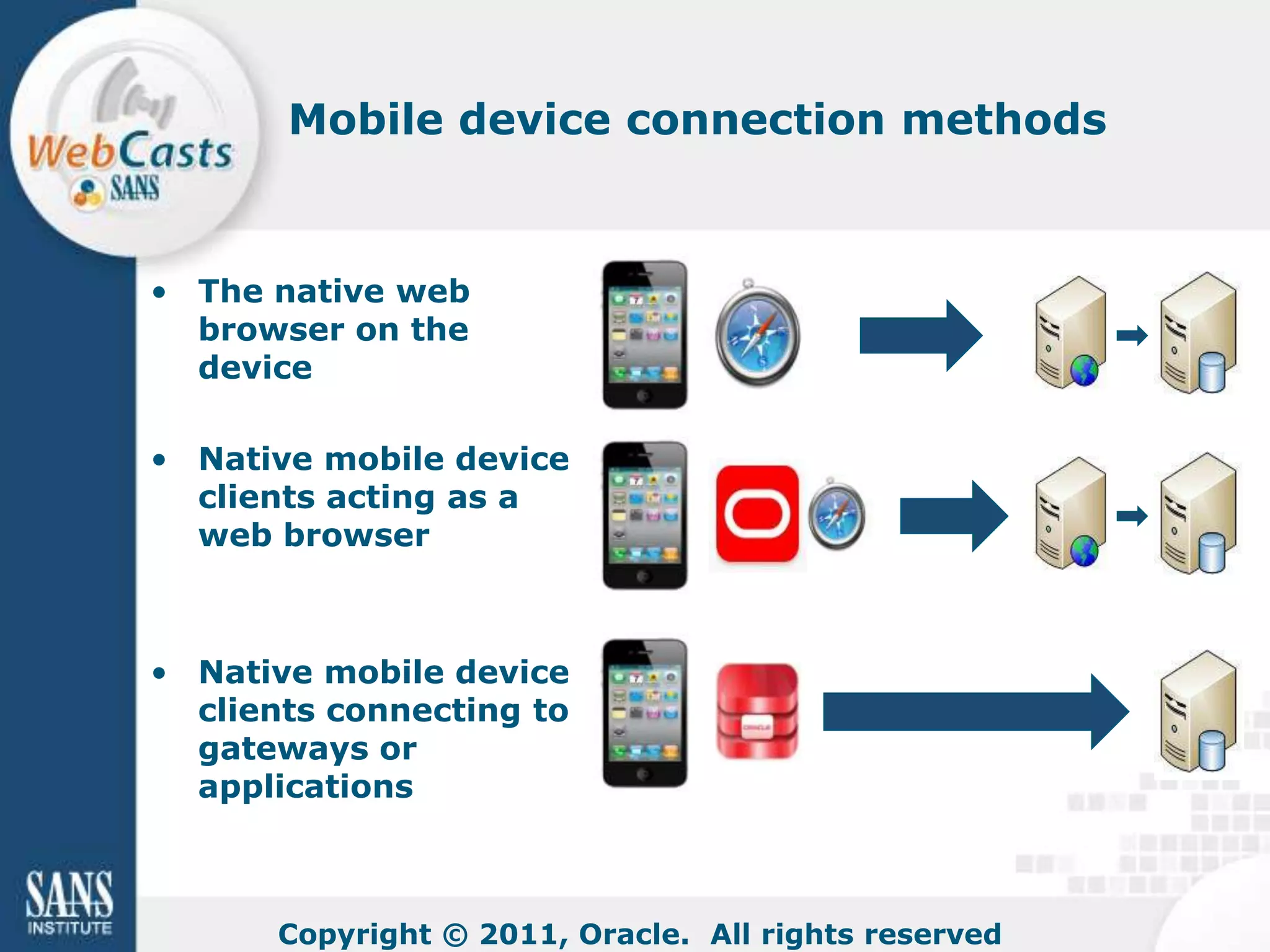
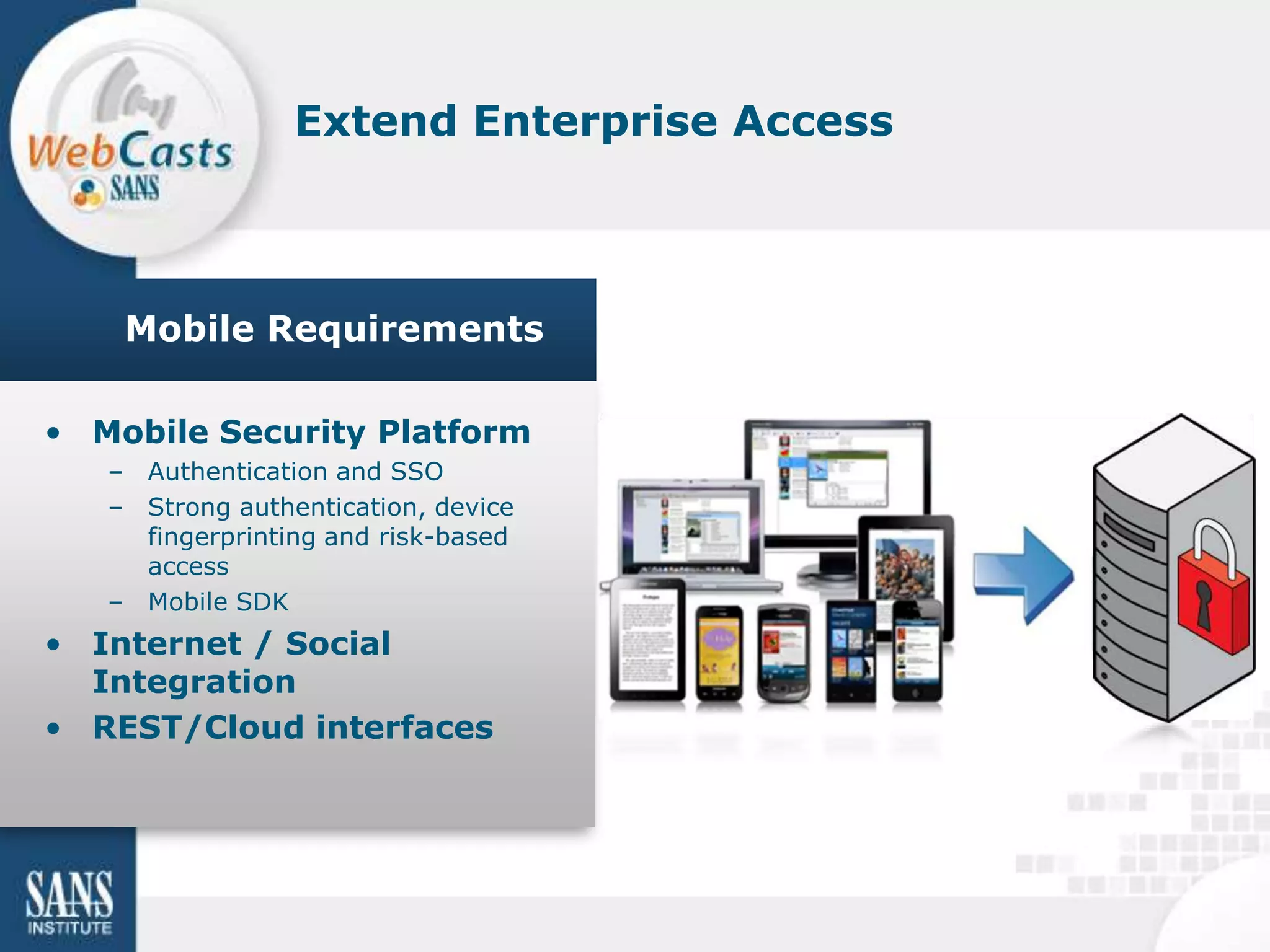
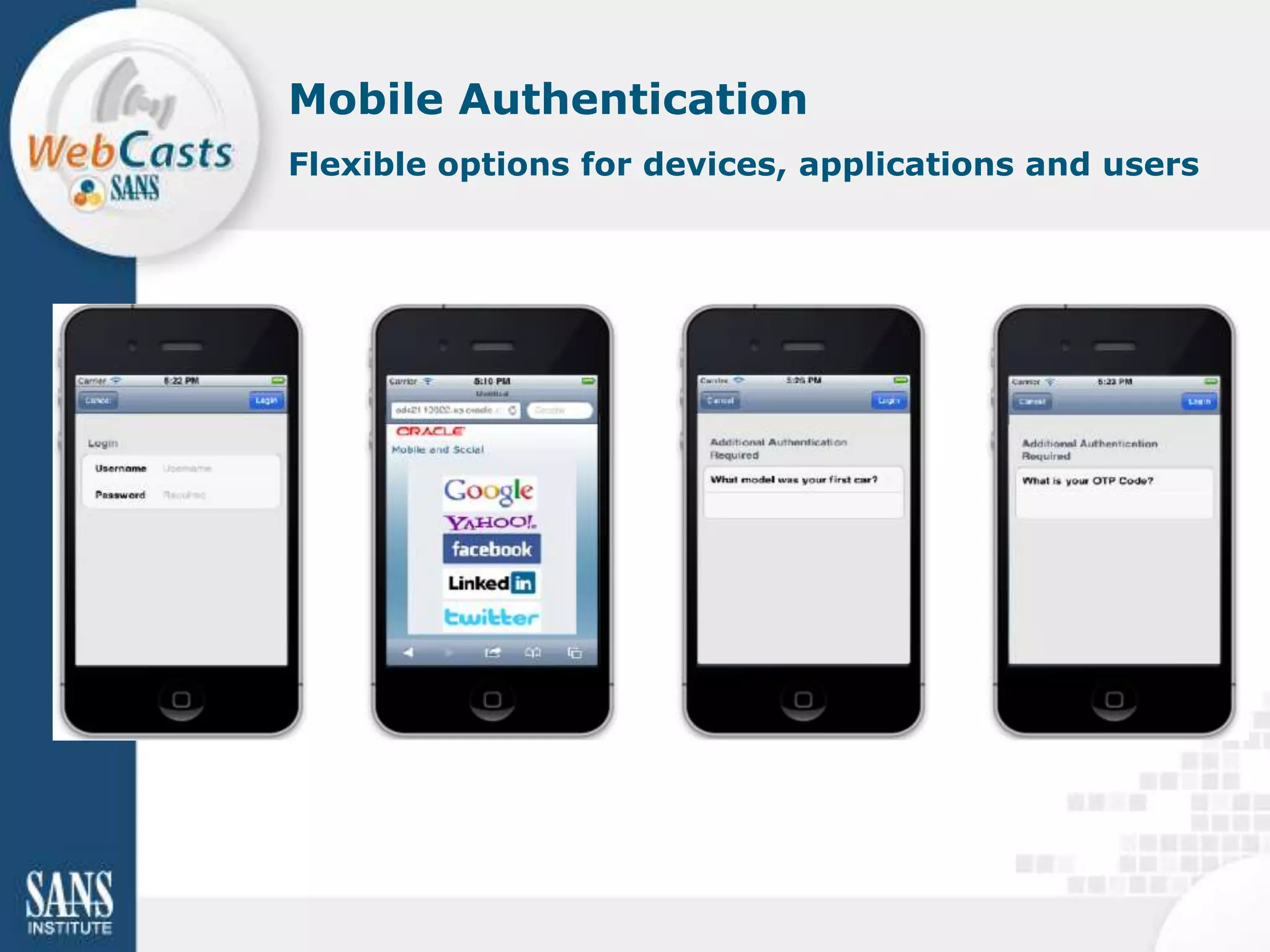
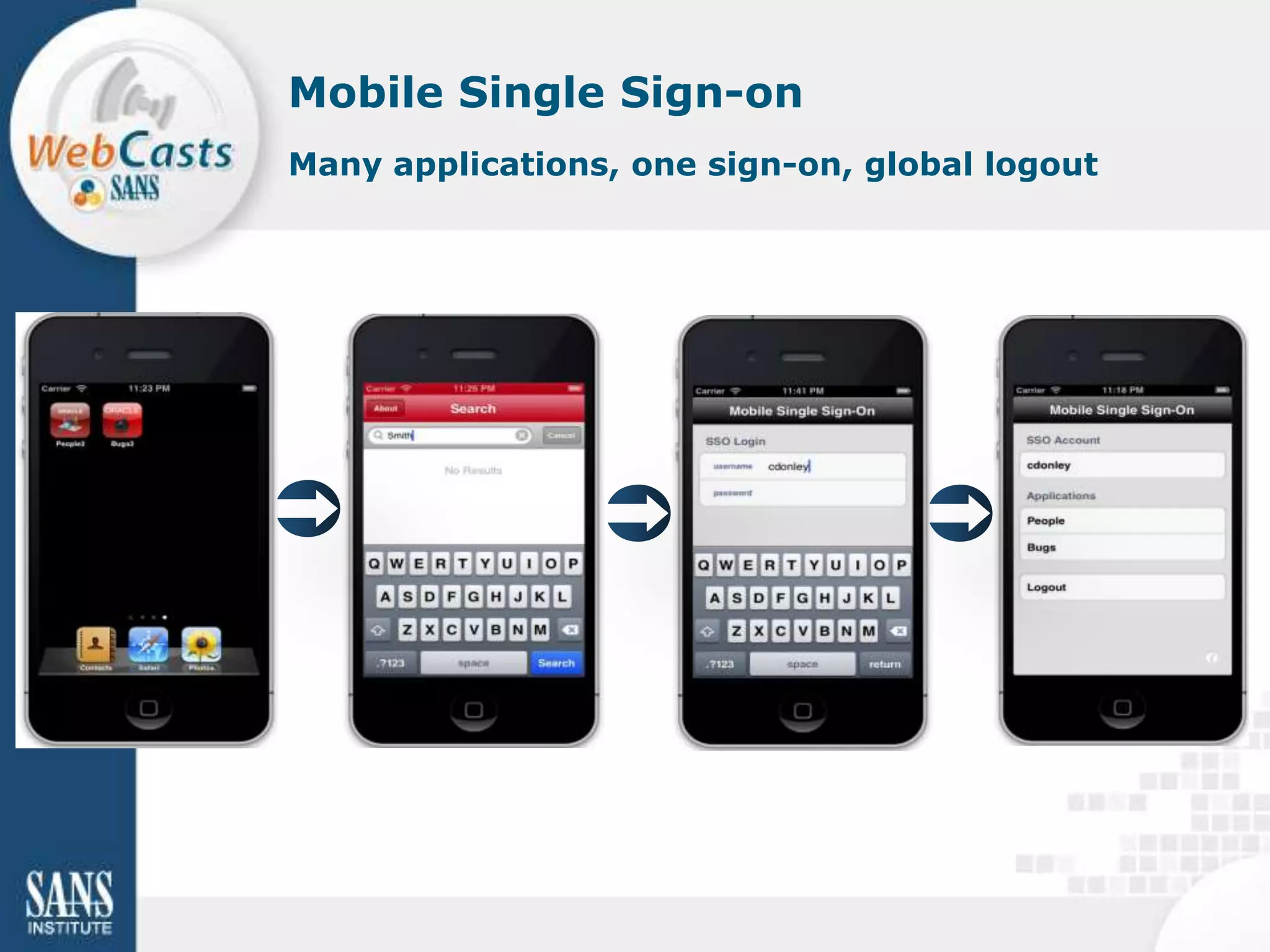
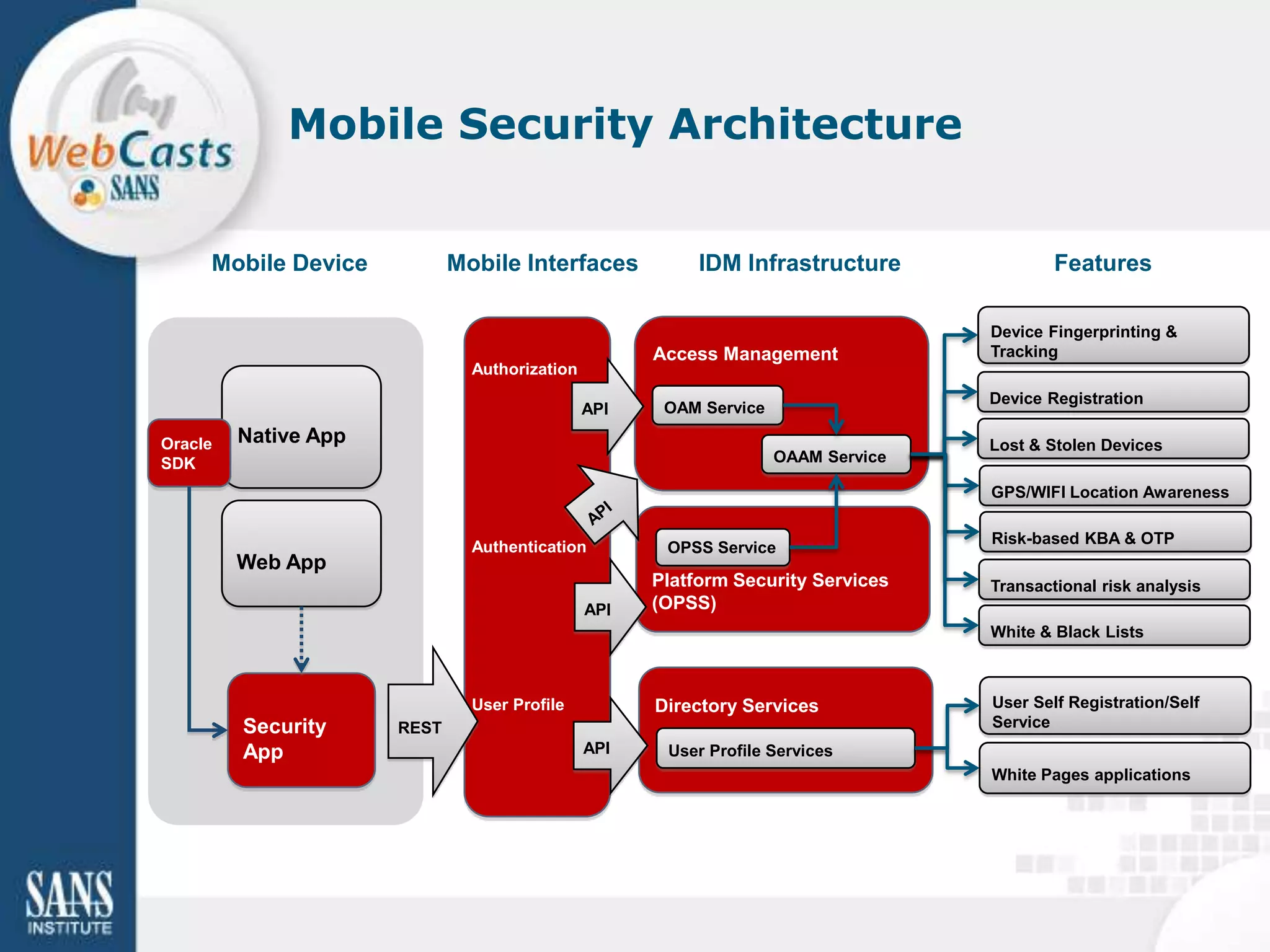
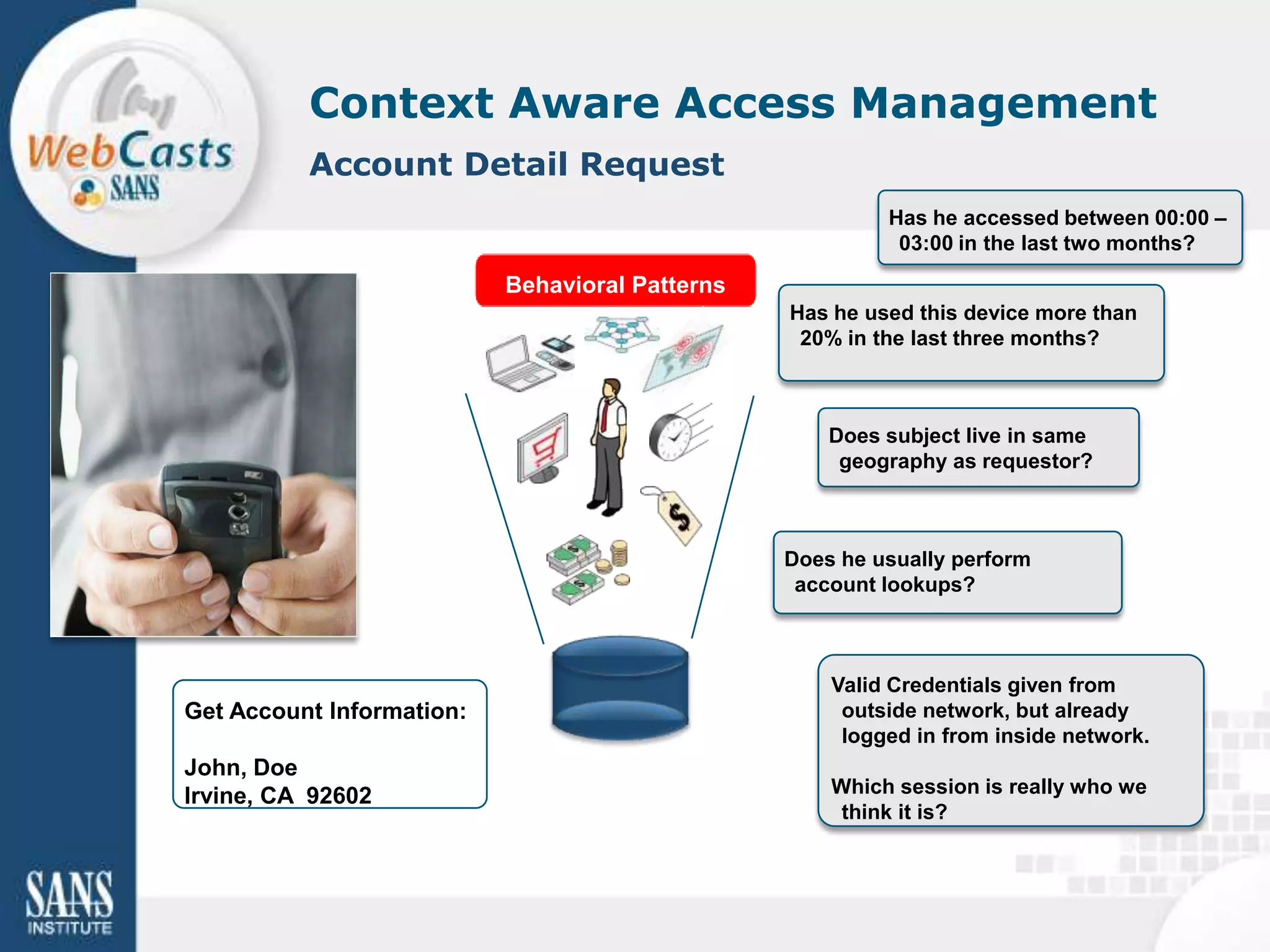
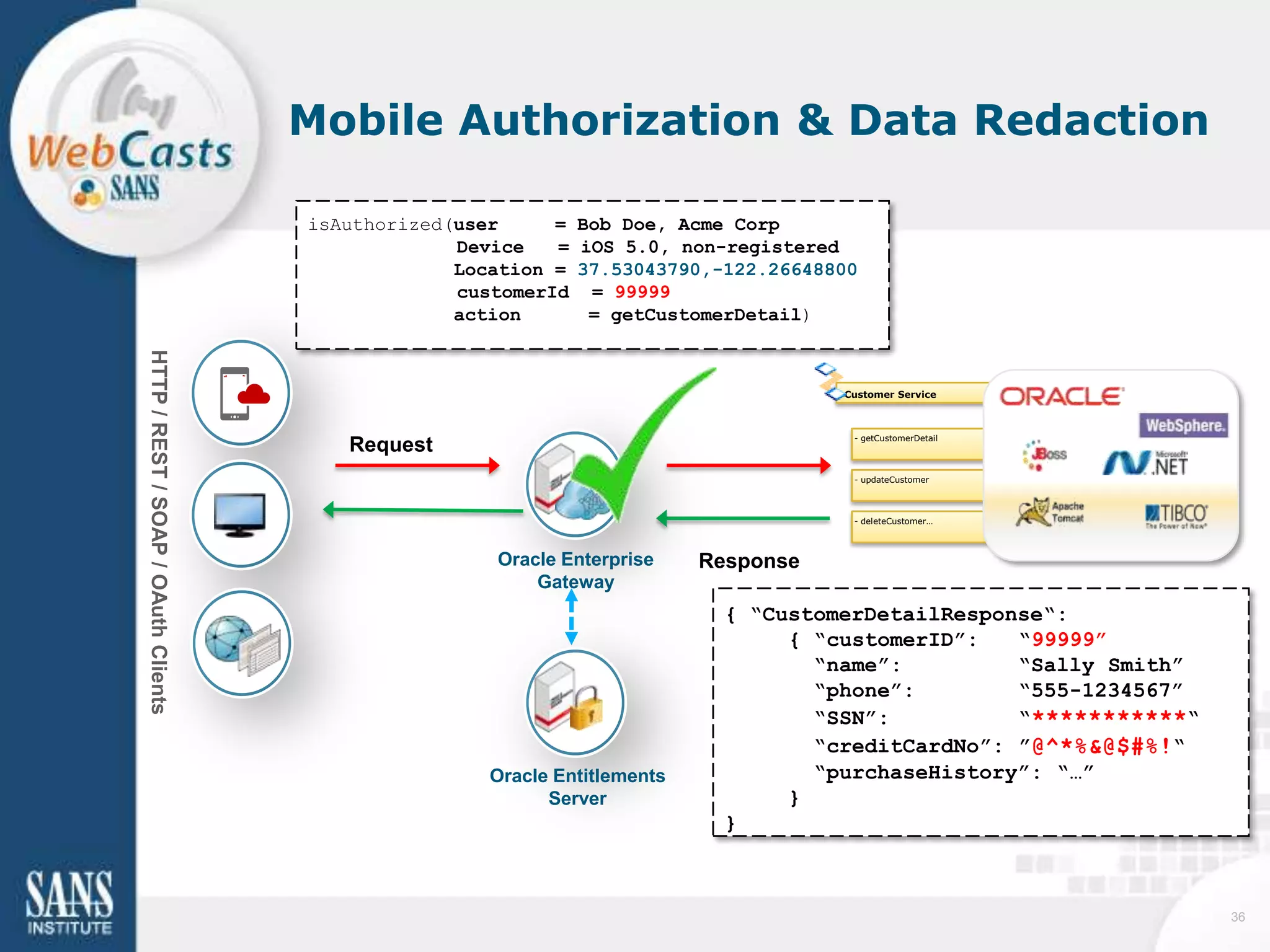
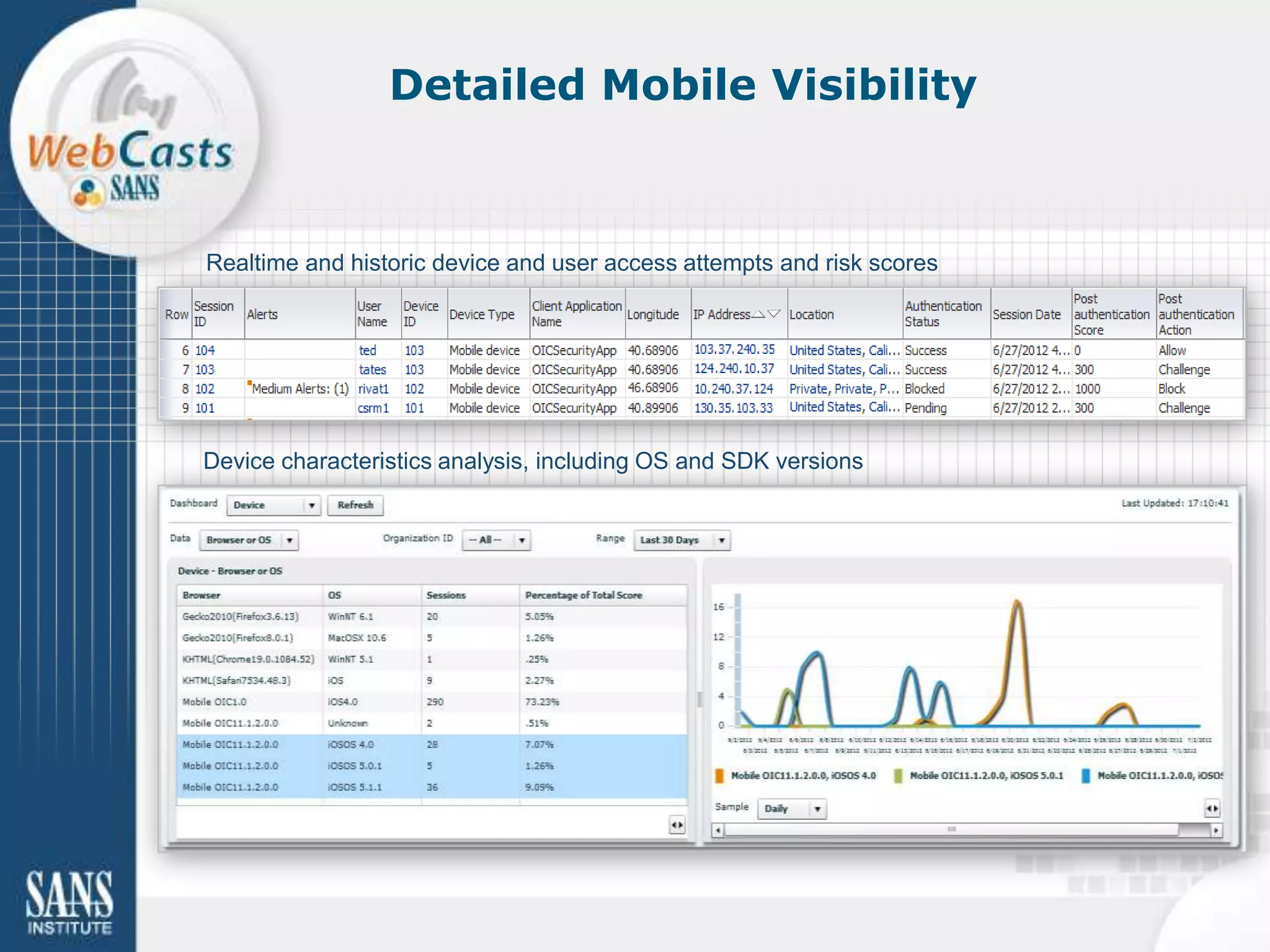
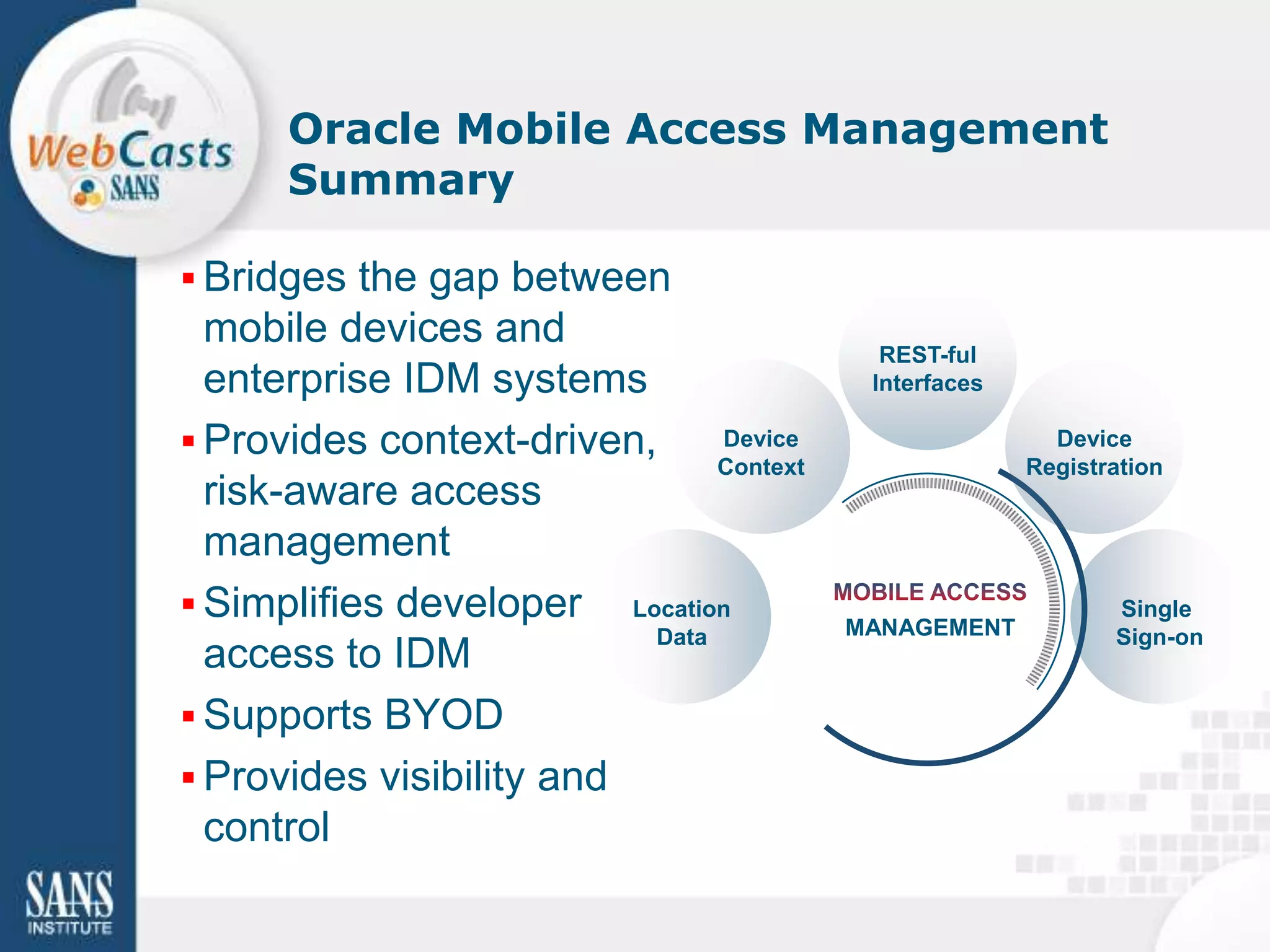
Developing and enforcing a BYOD policy is important for companies using mobile devices. The document discusses a mobility survey that found 97% of respondents feel mobile policies are important, yet many organizations still do not have policies. It also covers the top 3 mobile security practices of authenticating users, controlling access to resources, and protecting corporate data. Implementing an effective BYOD policy presents challenges in finding the right balance of security controls without upsetting employees.