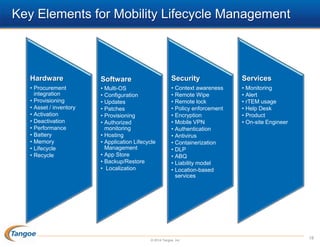
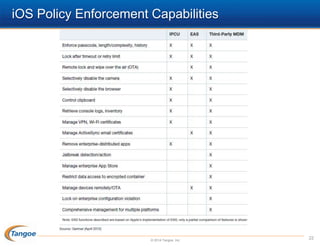
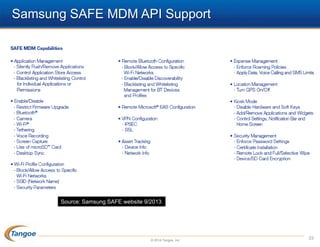
The document discusses the management of the 'great Blackberry migration,' highlighting the challenges faced due to the decline of Blackberry compared to competitors and the rise of BYOD (Bring Your Own Device) trends. It emphasizes the necessity of risk assessment, policy development, and help desk considerations while transitioning to new mobile platforms. The presentation outlines key strategies for ensuring security, managing expectations, and avoiding mistakes during the migration process.