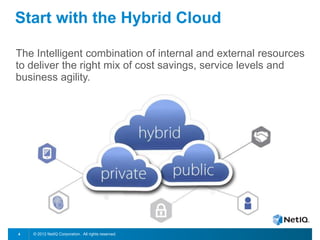
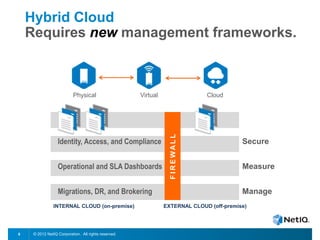
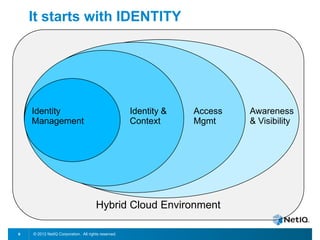
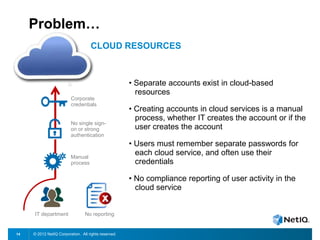
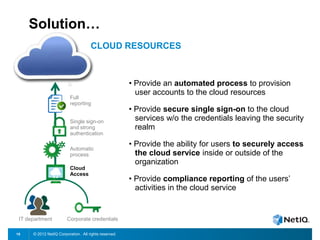
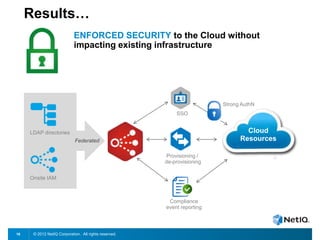
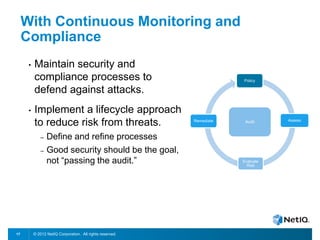
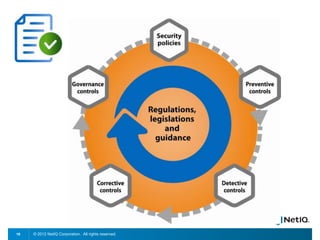
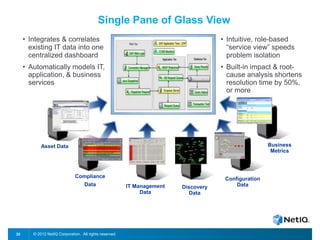
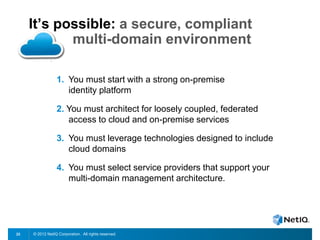
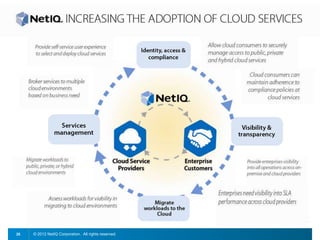
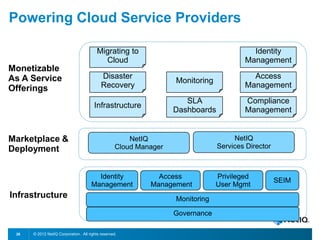
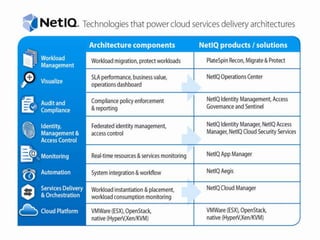
The document discusses how organizations can regain control over their hybrid cloud environments through identity and access management, visibility, and continuous compliance. It recommends starting with a strong identity fabric and leveraging identity context to gain awareness and visibility. Continuous monitoring is needed to maintain security and compliance across physical, virtual, and cloud systems through automation and real-time alerts. Role-based dashboards can provide the right visibility for different users. NetIQ provides expertise and products that can help power cloud service providers and enterprises in securing hybrid cloud environments.