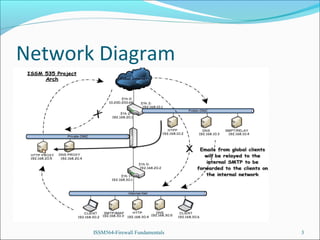
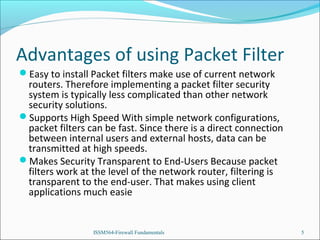
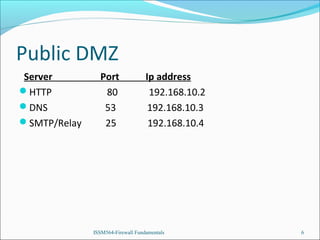
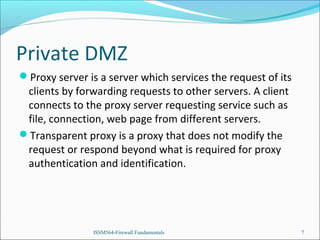
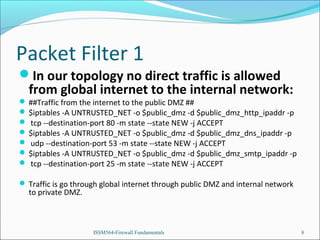
The presentation introduces the group's network and firewall architecture, including a public DMZ, private DMZ, and internal network. It discusses packet filtering and configuring iptables rules to allow certain traffic to the public DMZ servers while blocking other traffic. It also covers tweaks to prevent common attacks like IP spoofing, IP smurfing, SYN flooding and ping flooding through techniques like disabling IP spoofing and source routing, enabling SYN cookies, and rate limiting ICMP echo requests.