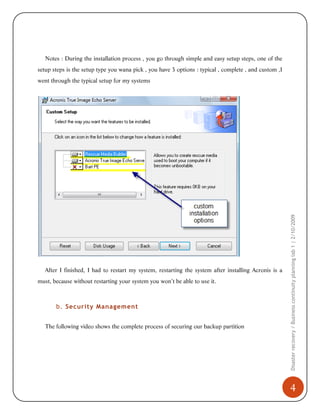
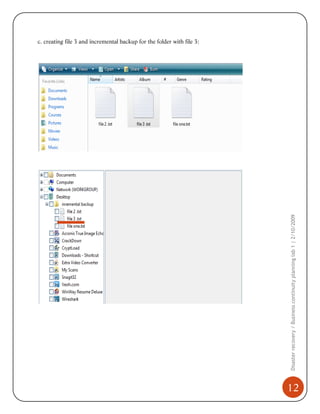
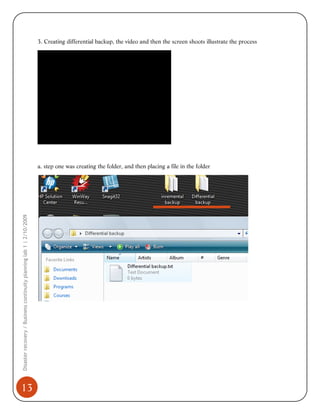
This document provides details on implementing disaster recovery and business continuity planning using the software Acronis True Image. It describes:
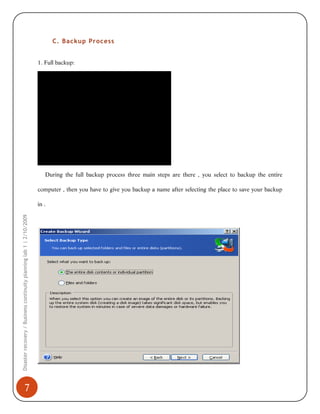
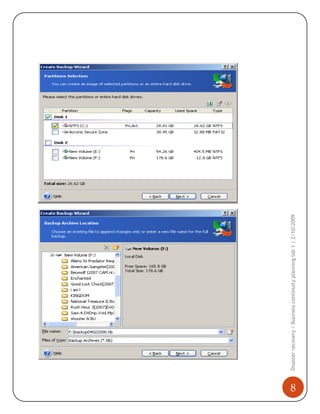
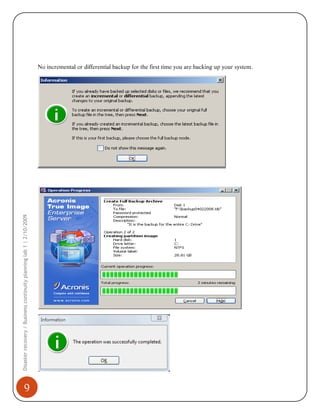
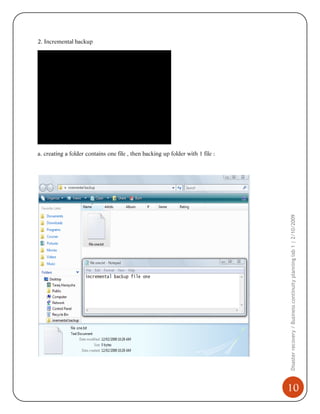
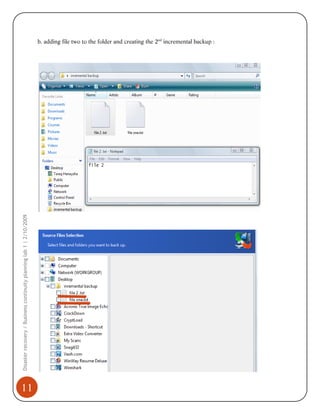
1) Installing and using Acronis to perform full, incremental, and differential backups of a system. This creates images that can restore the system in the event of failure.
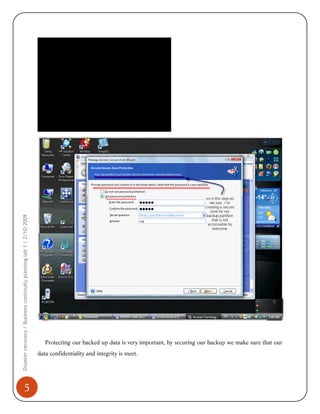
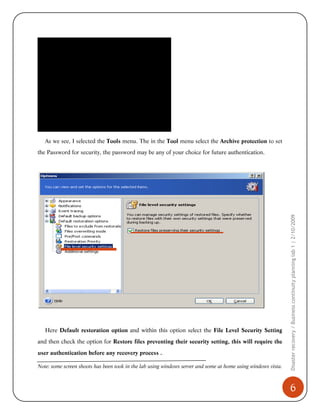
2) The security features of Acronis to password protect backup archives.
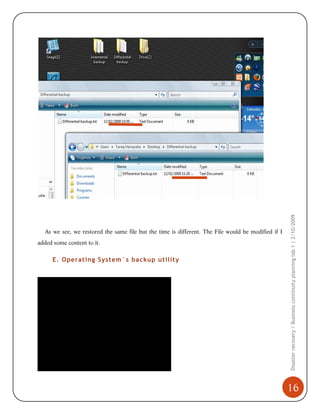
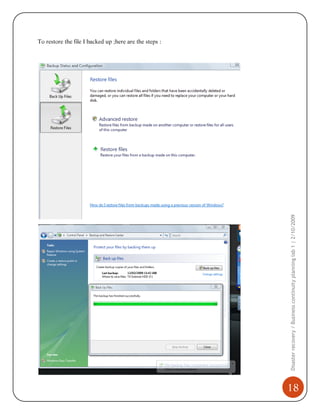
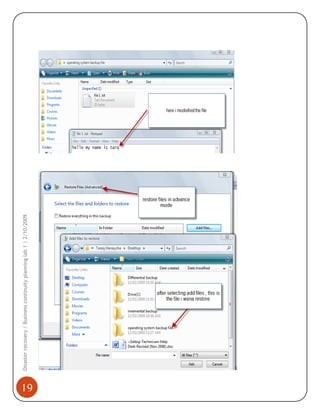
3) The restoration process where backed up files and folders can be recovered.
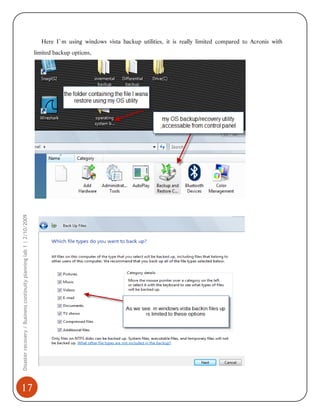
4) A comparison of Acronis' backup approach to the backup utility of the Windows operating system, noting advantages and limitations of each.