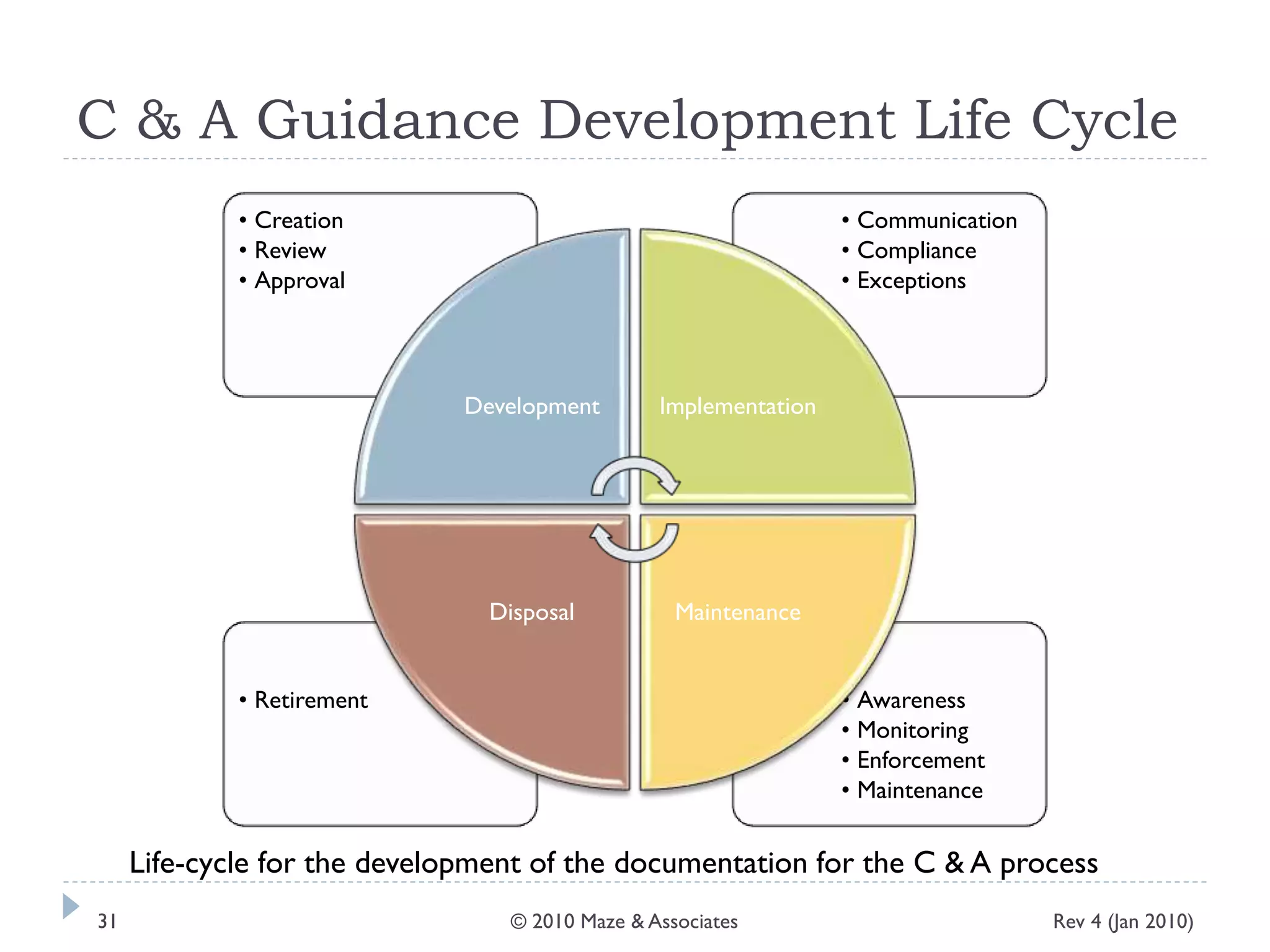
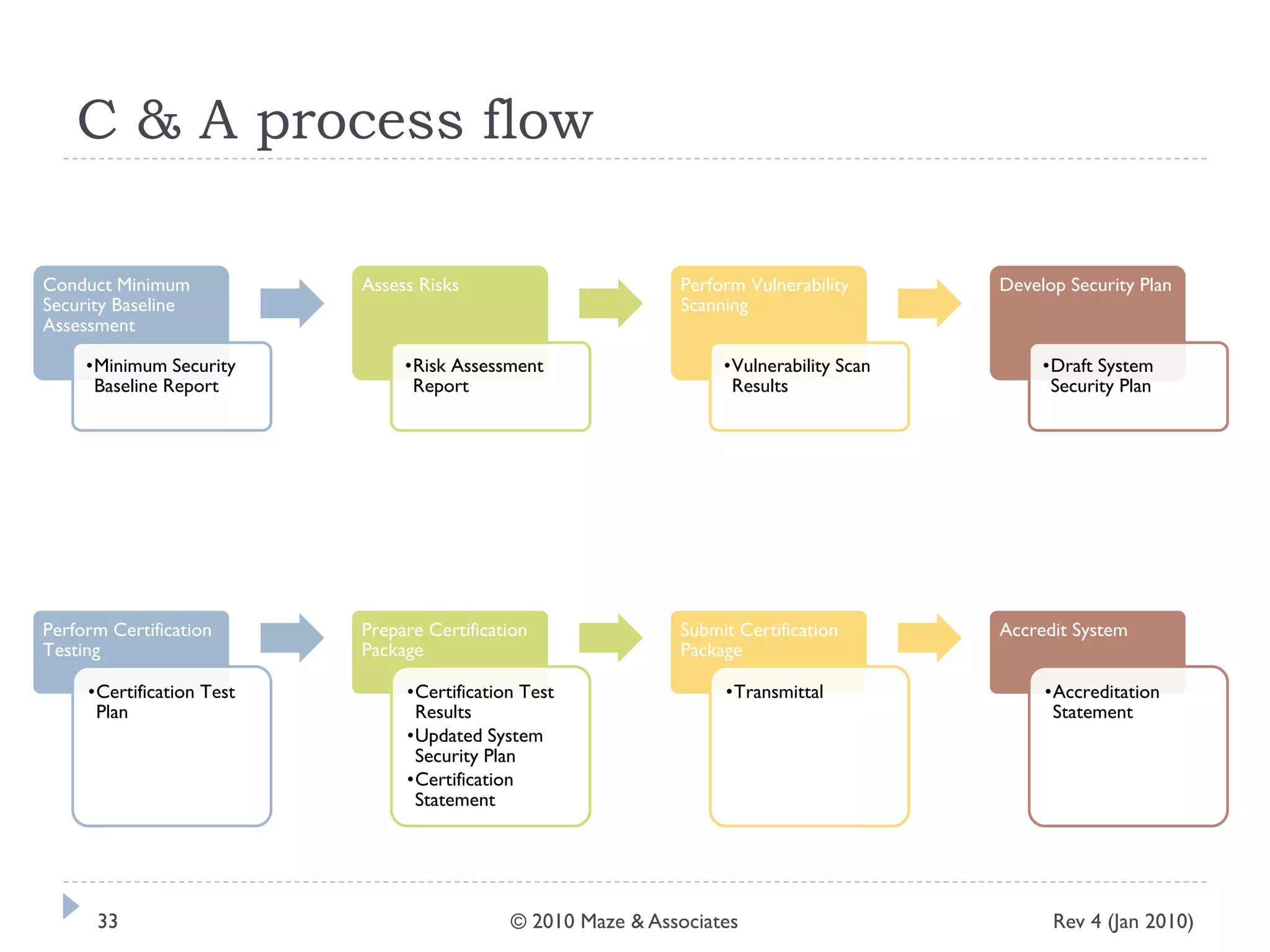
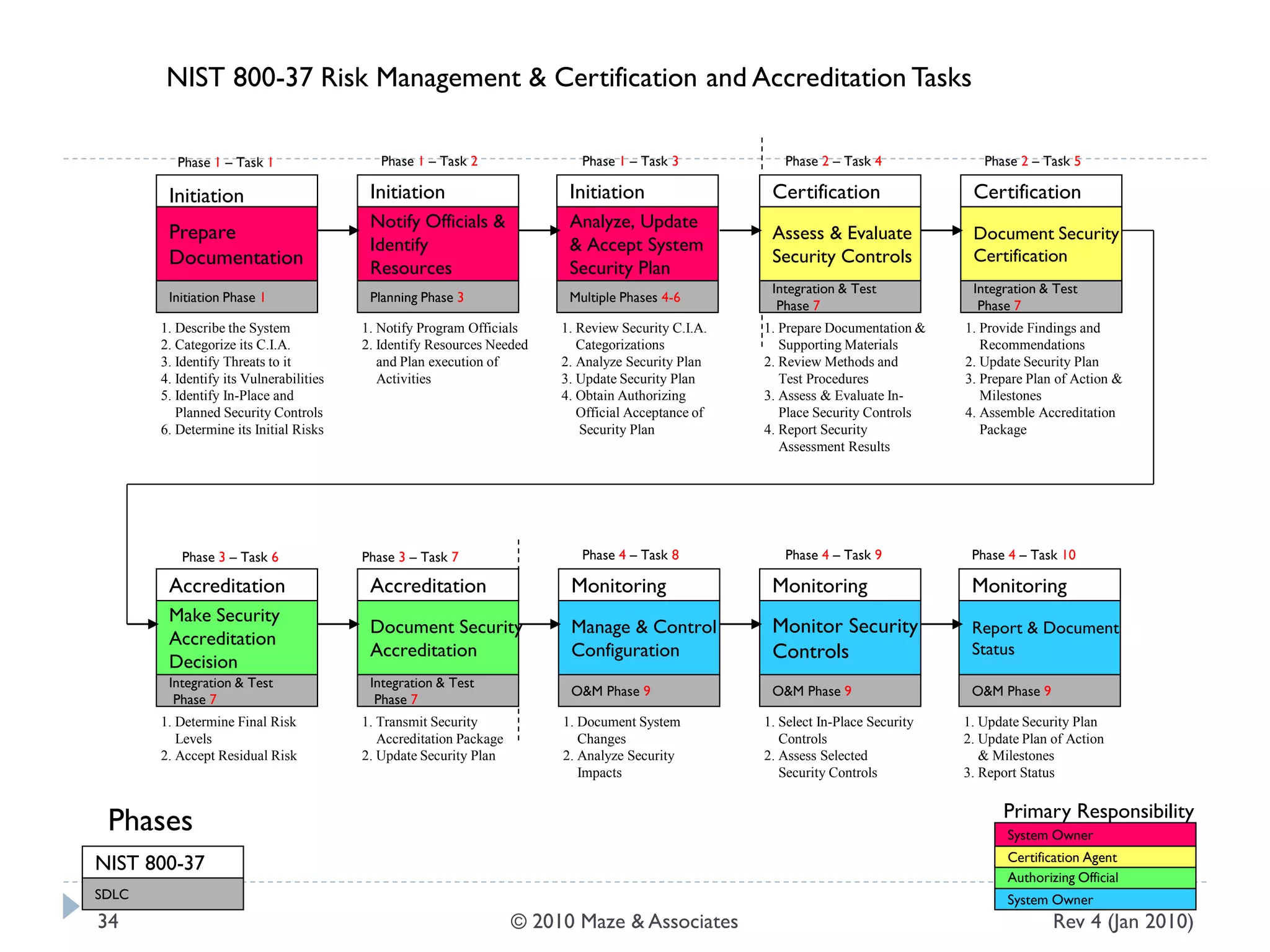
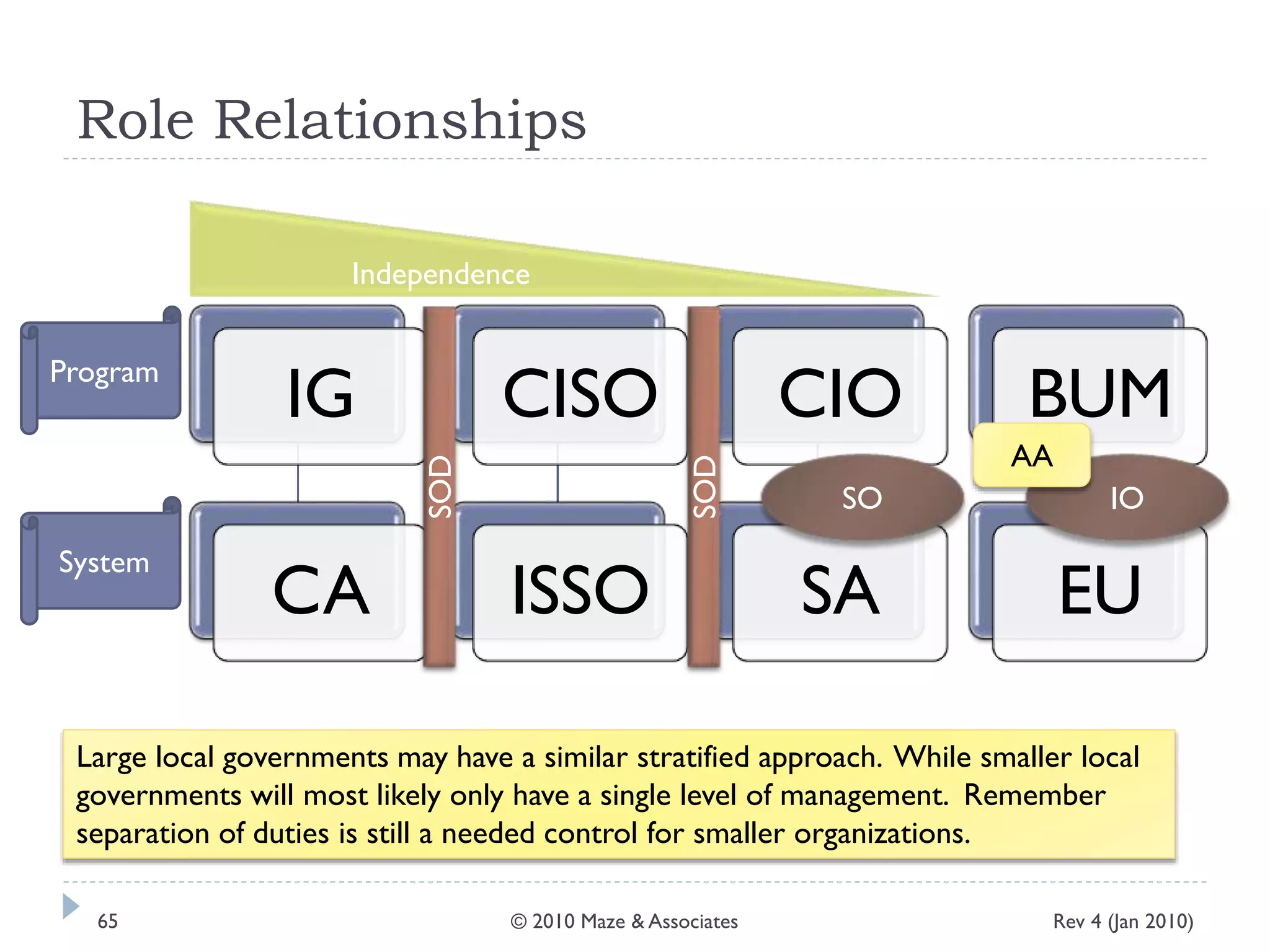
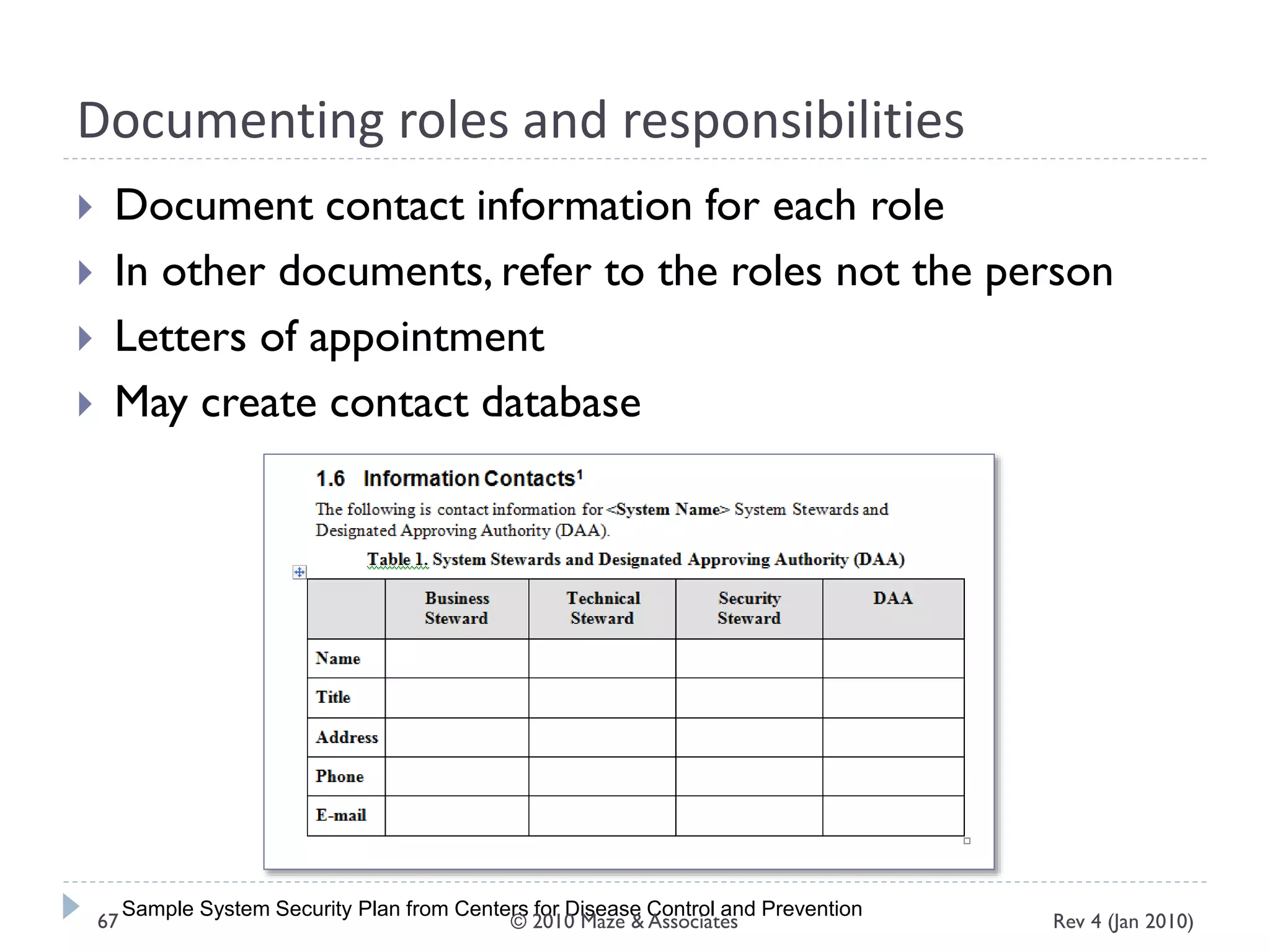
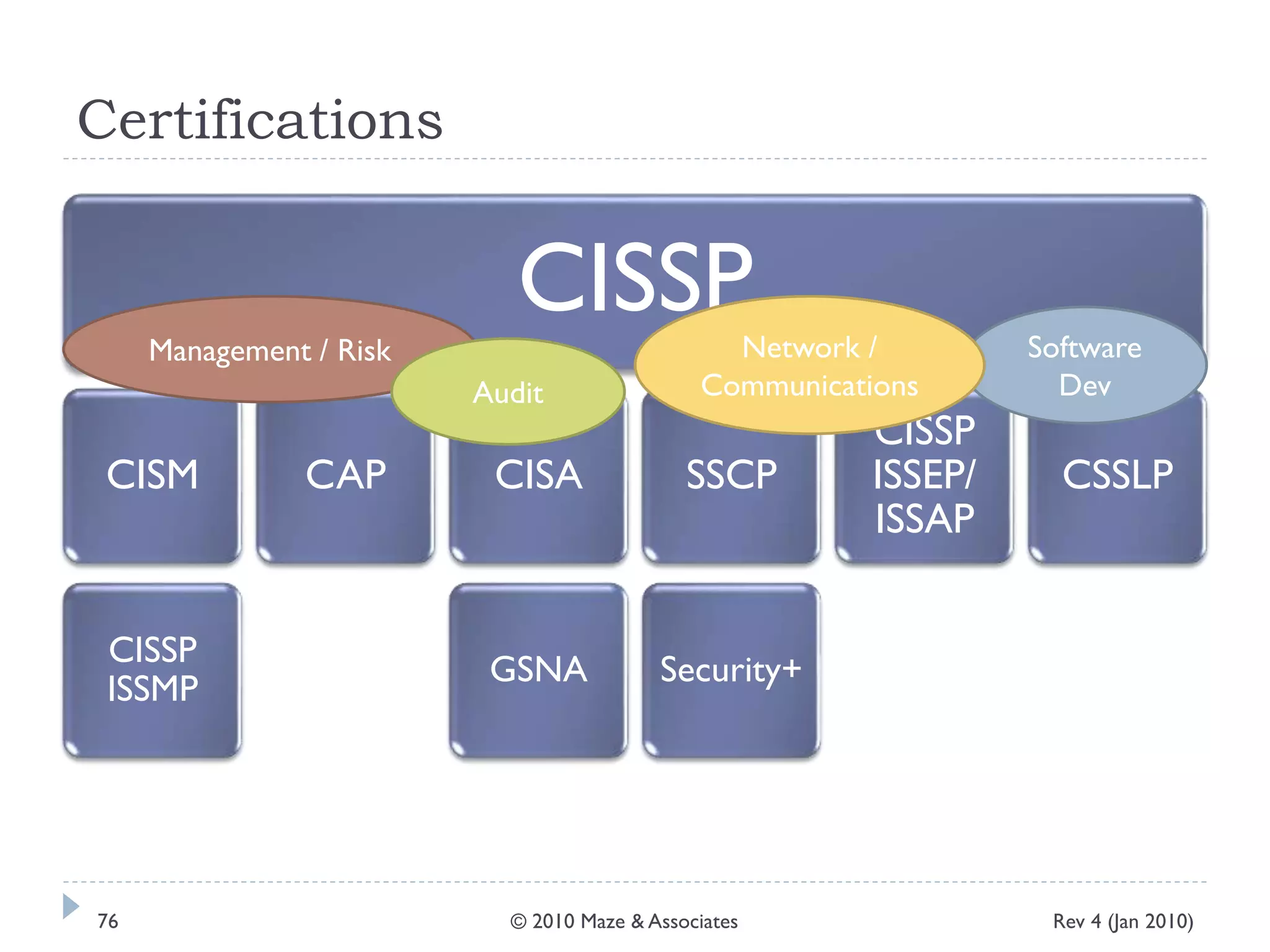
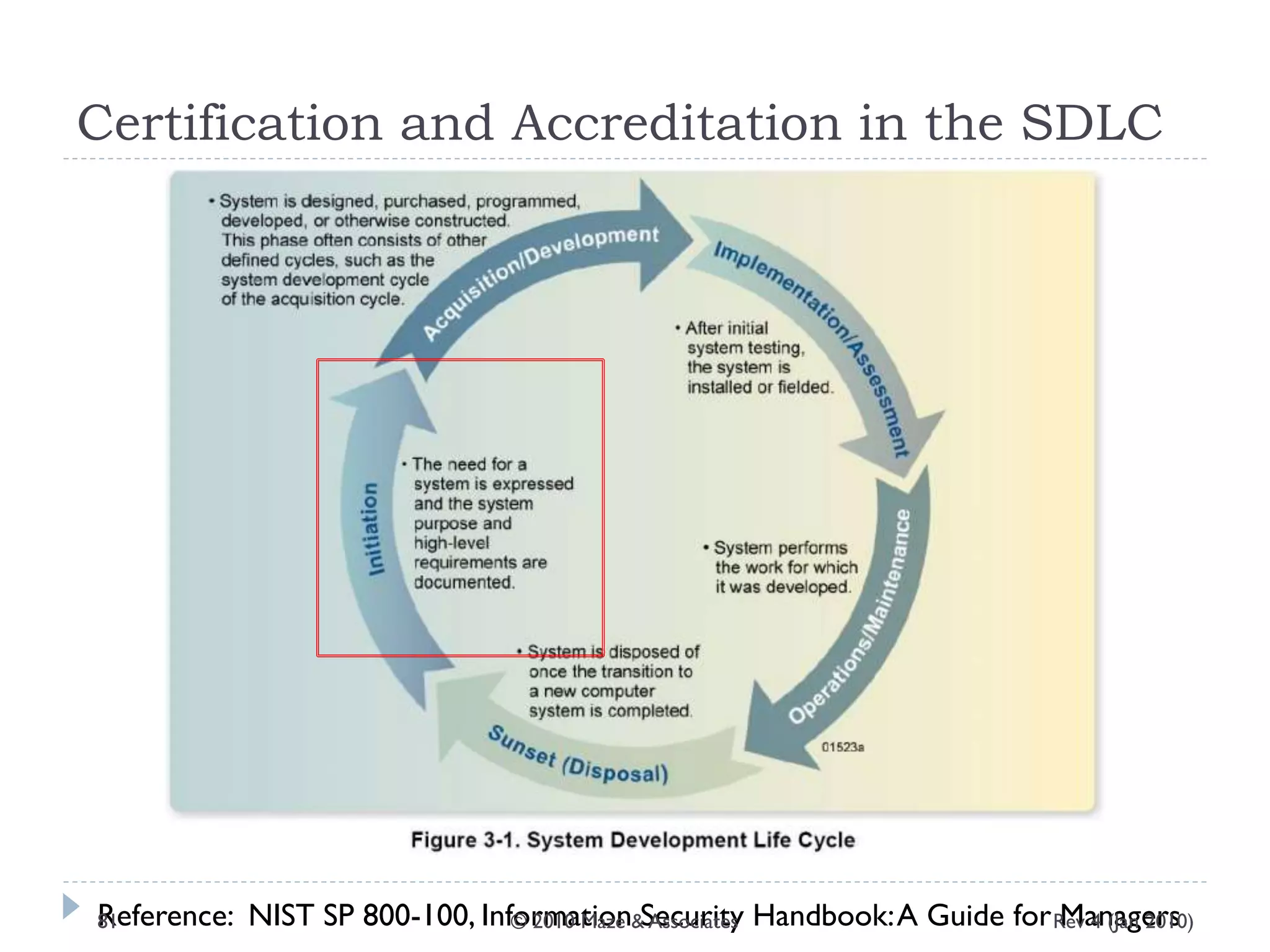
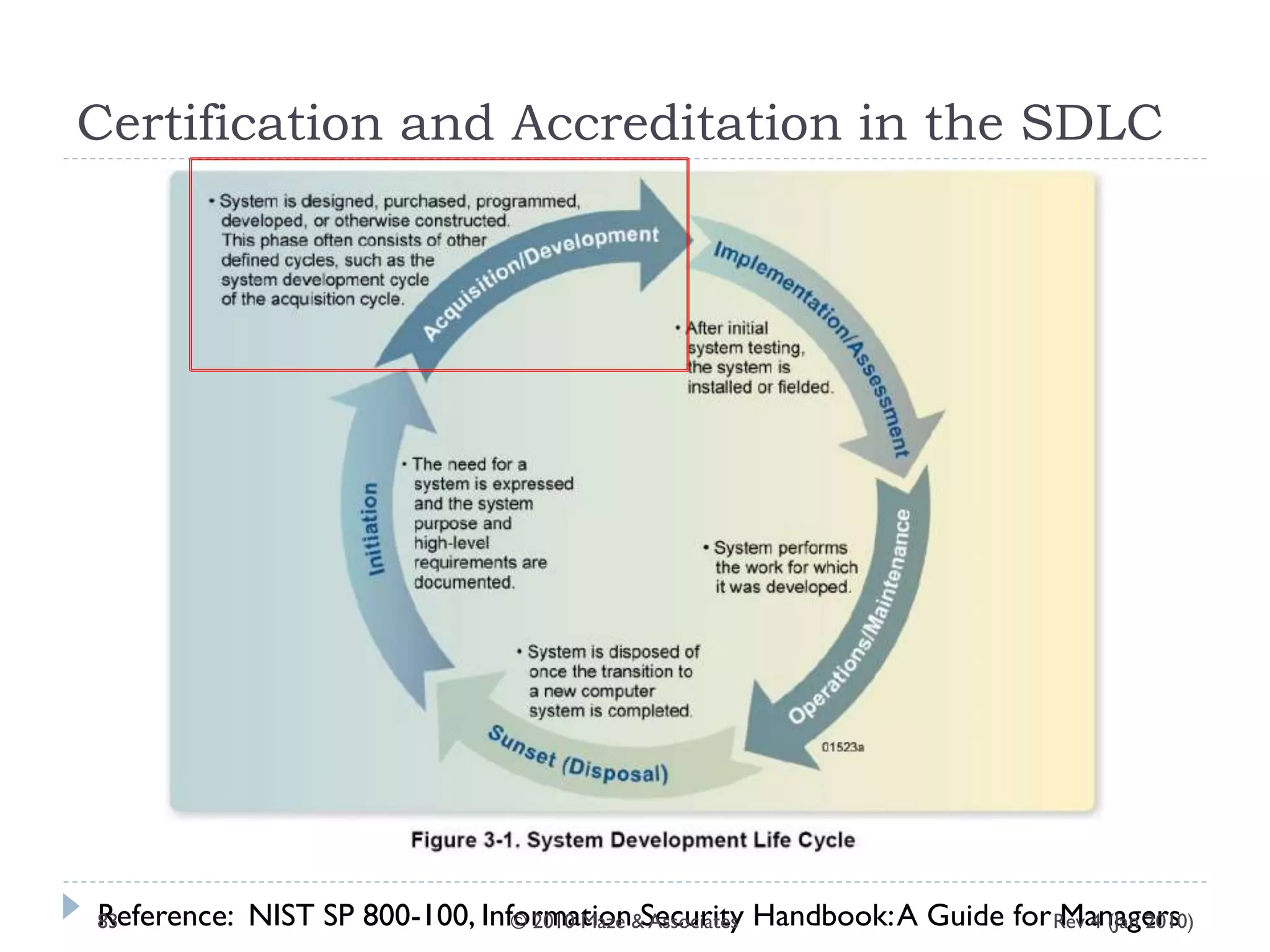
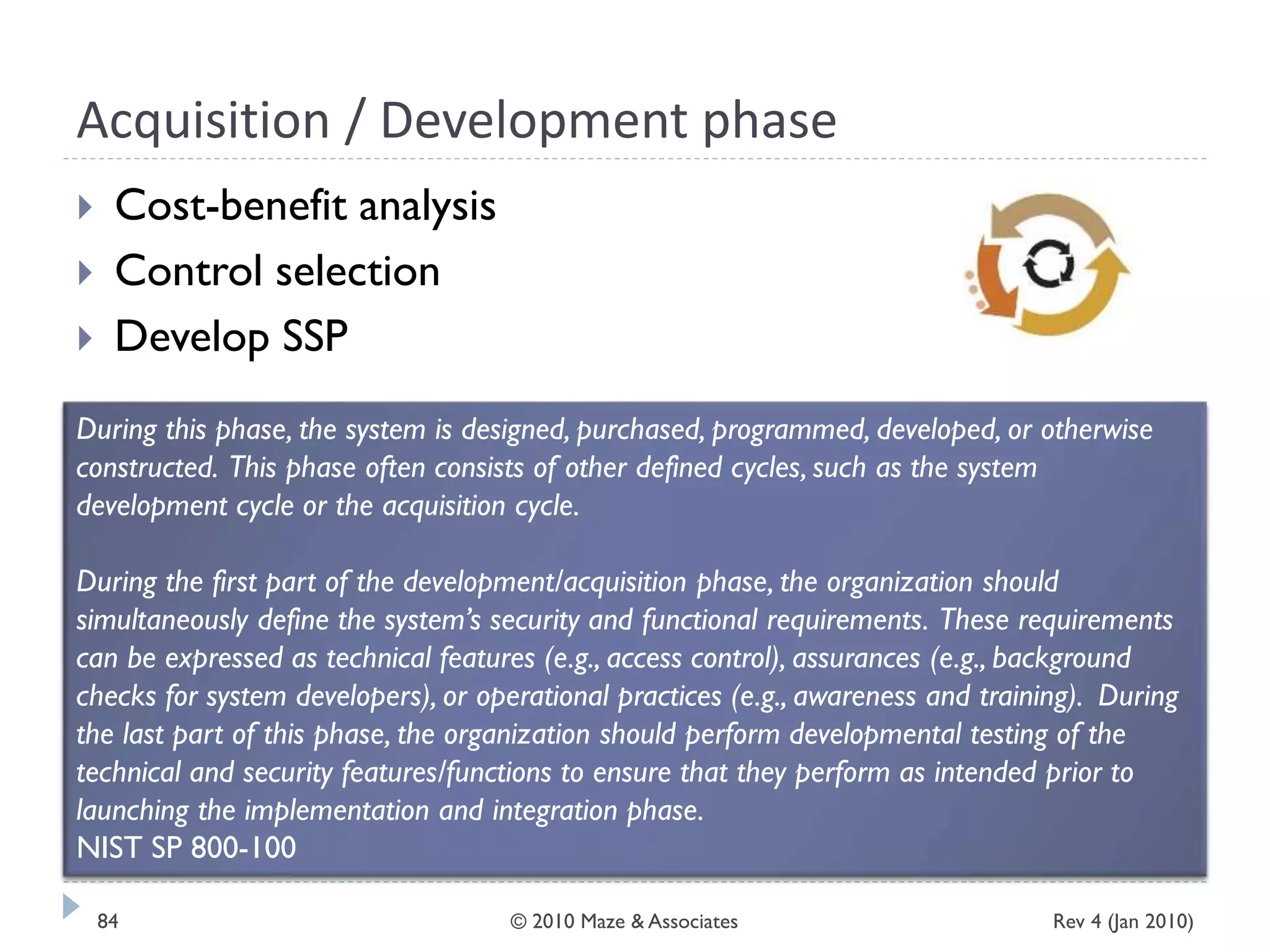
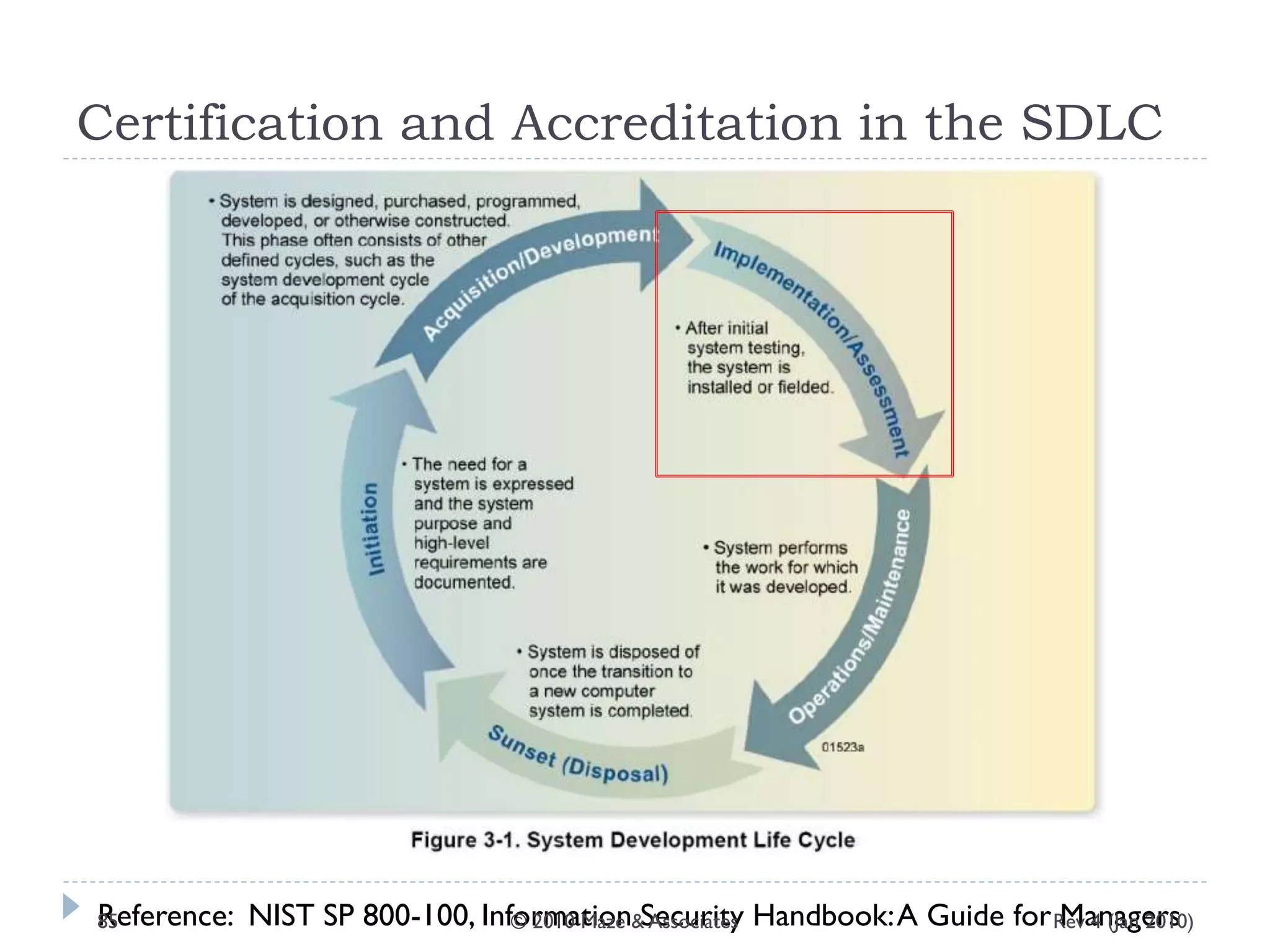
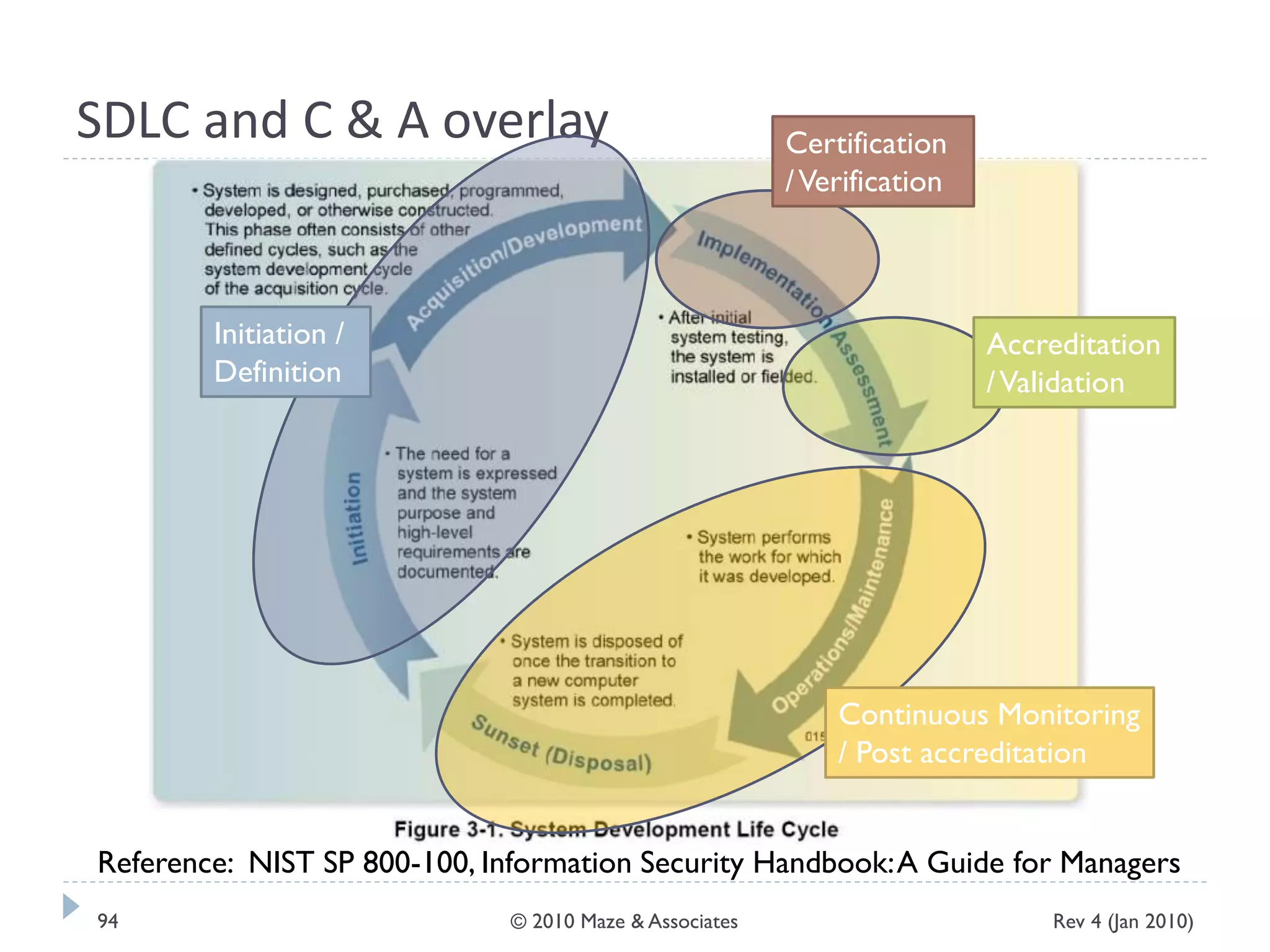
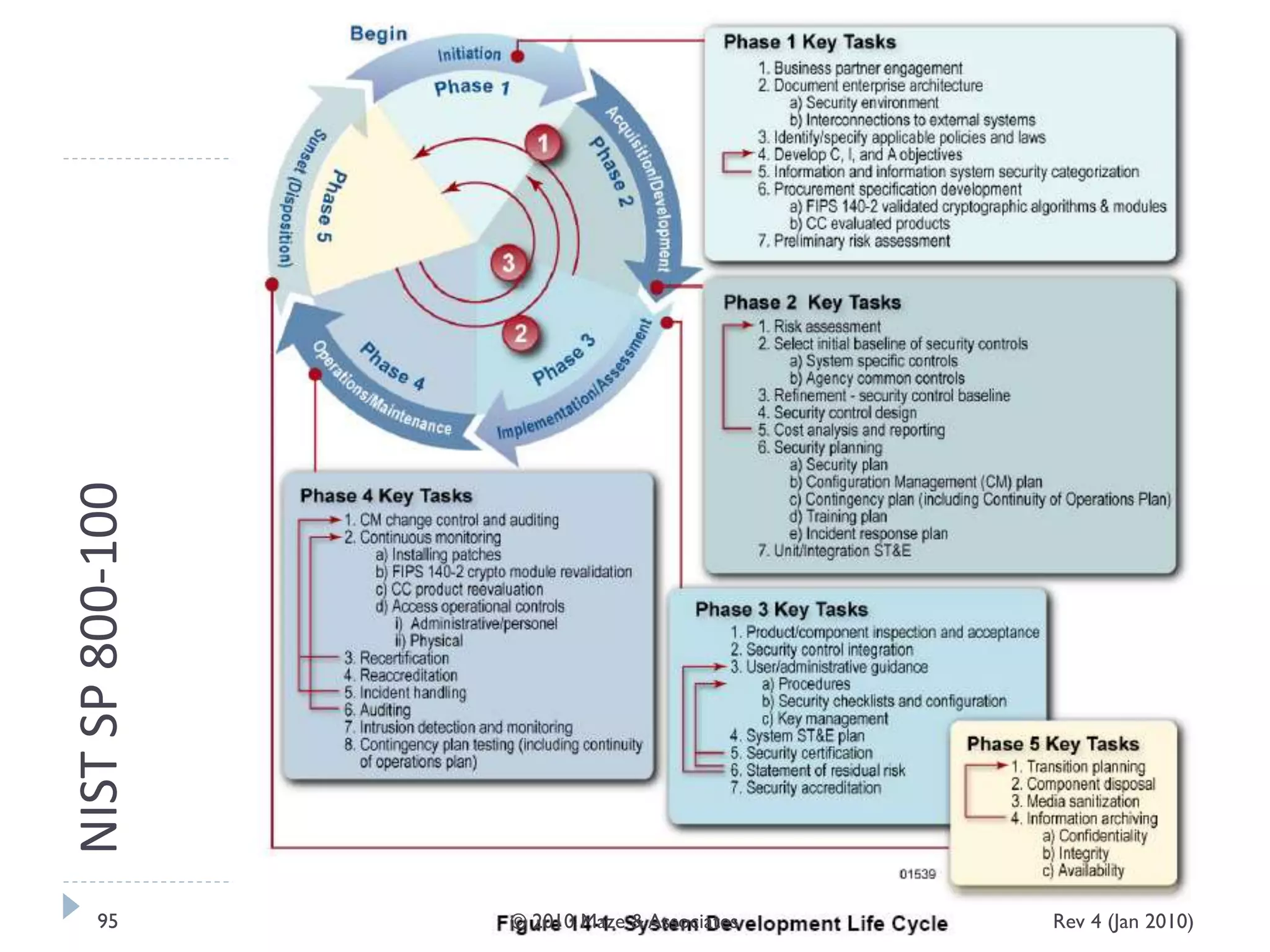
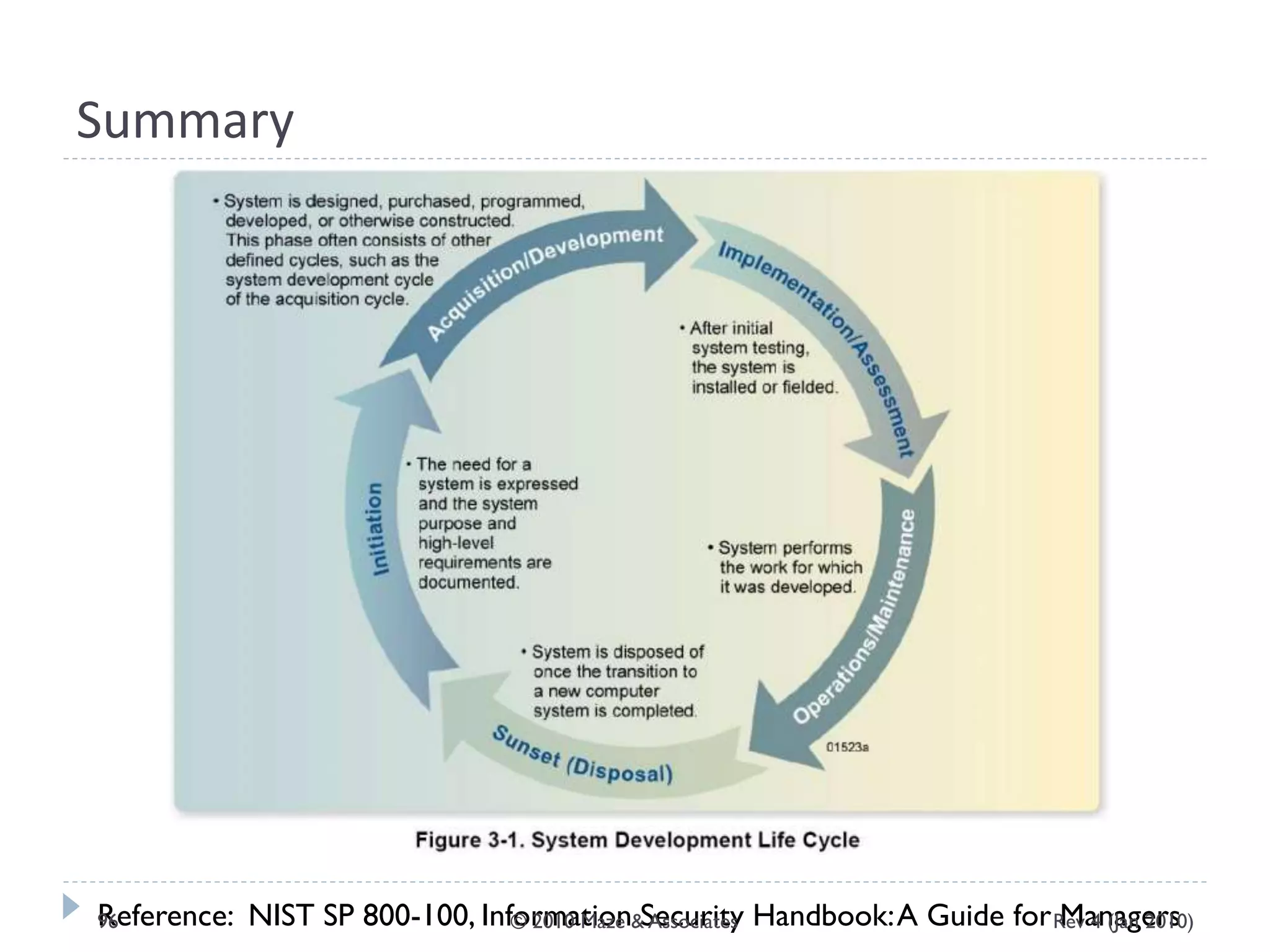
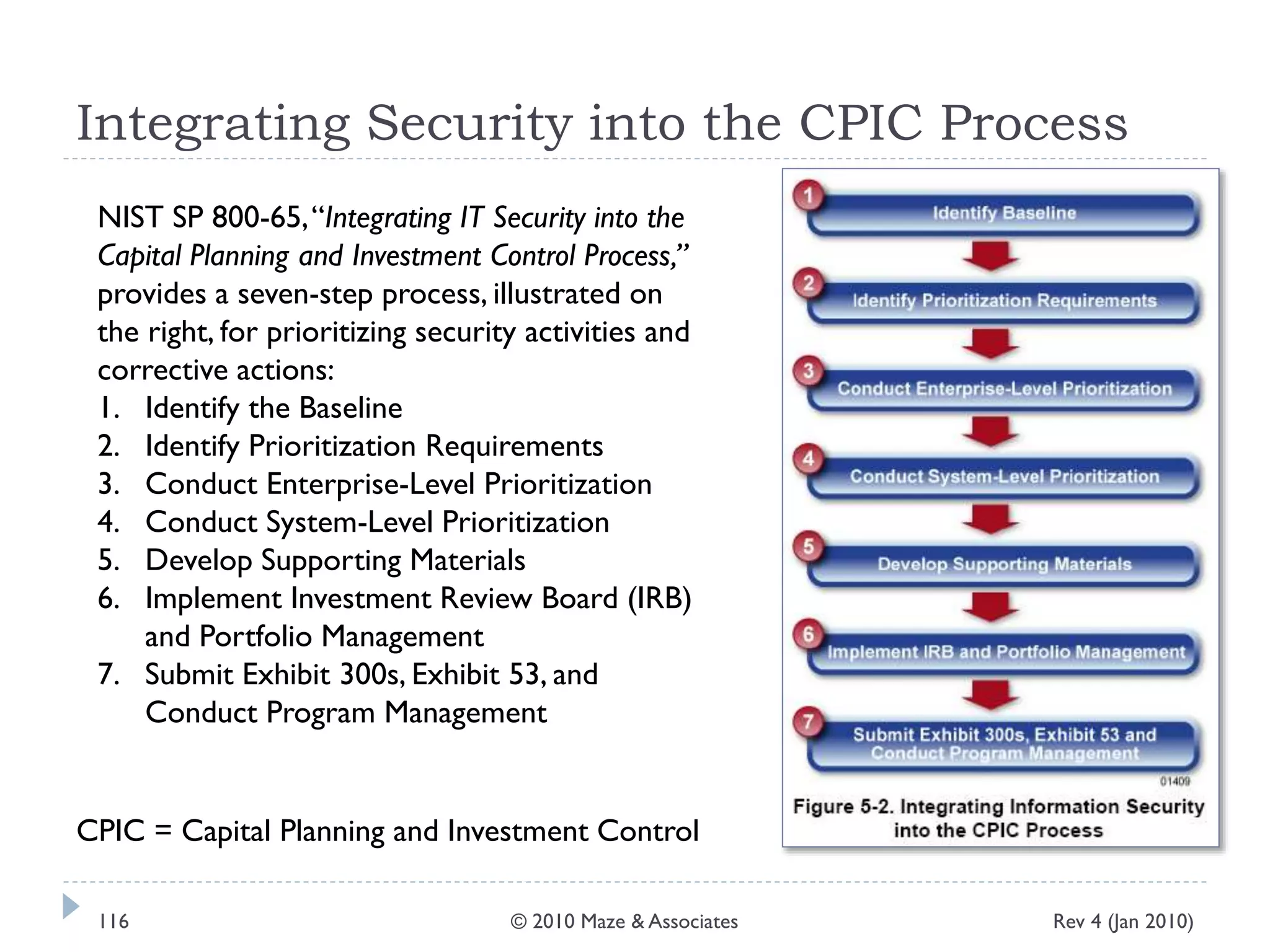
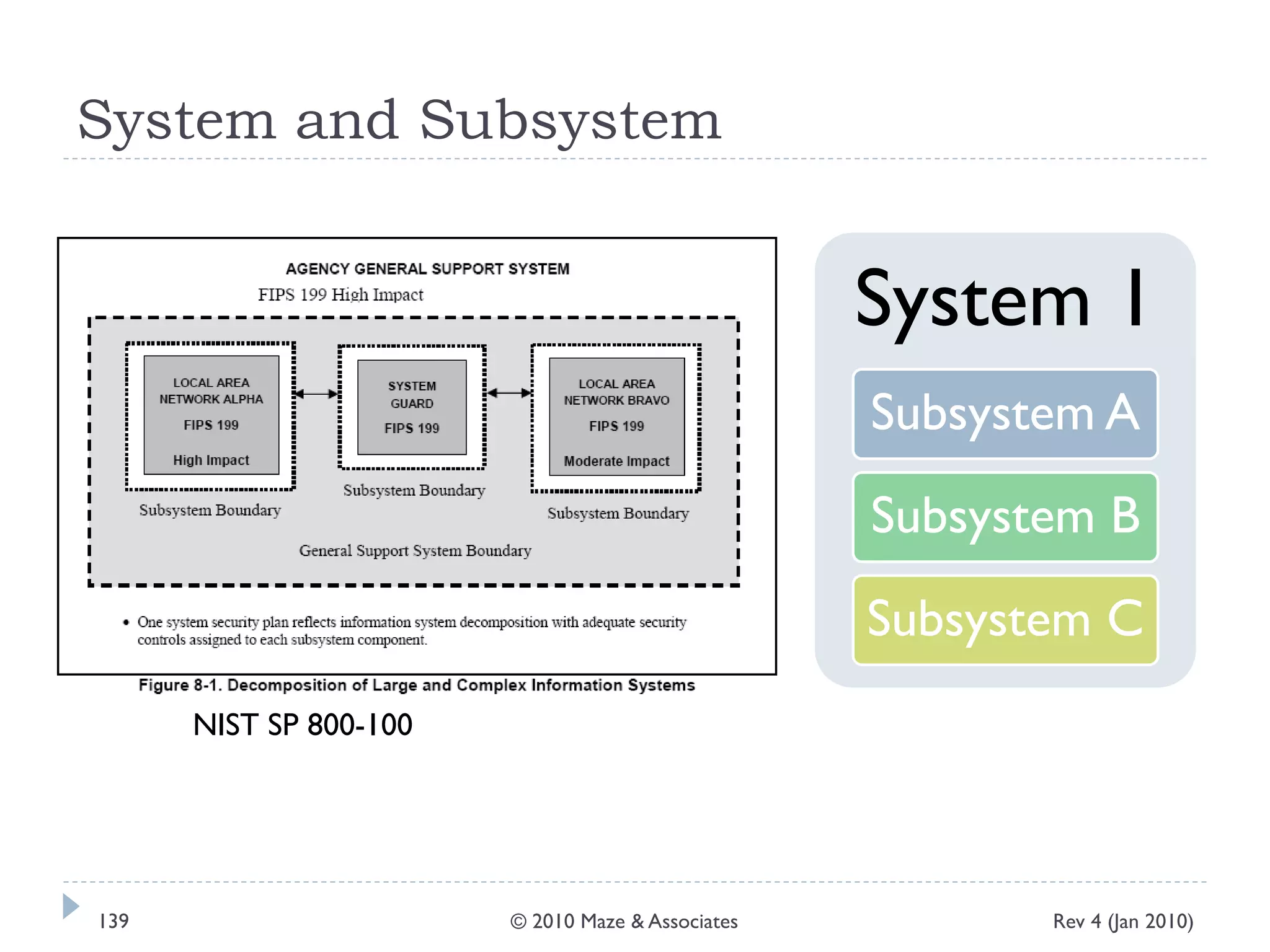
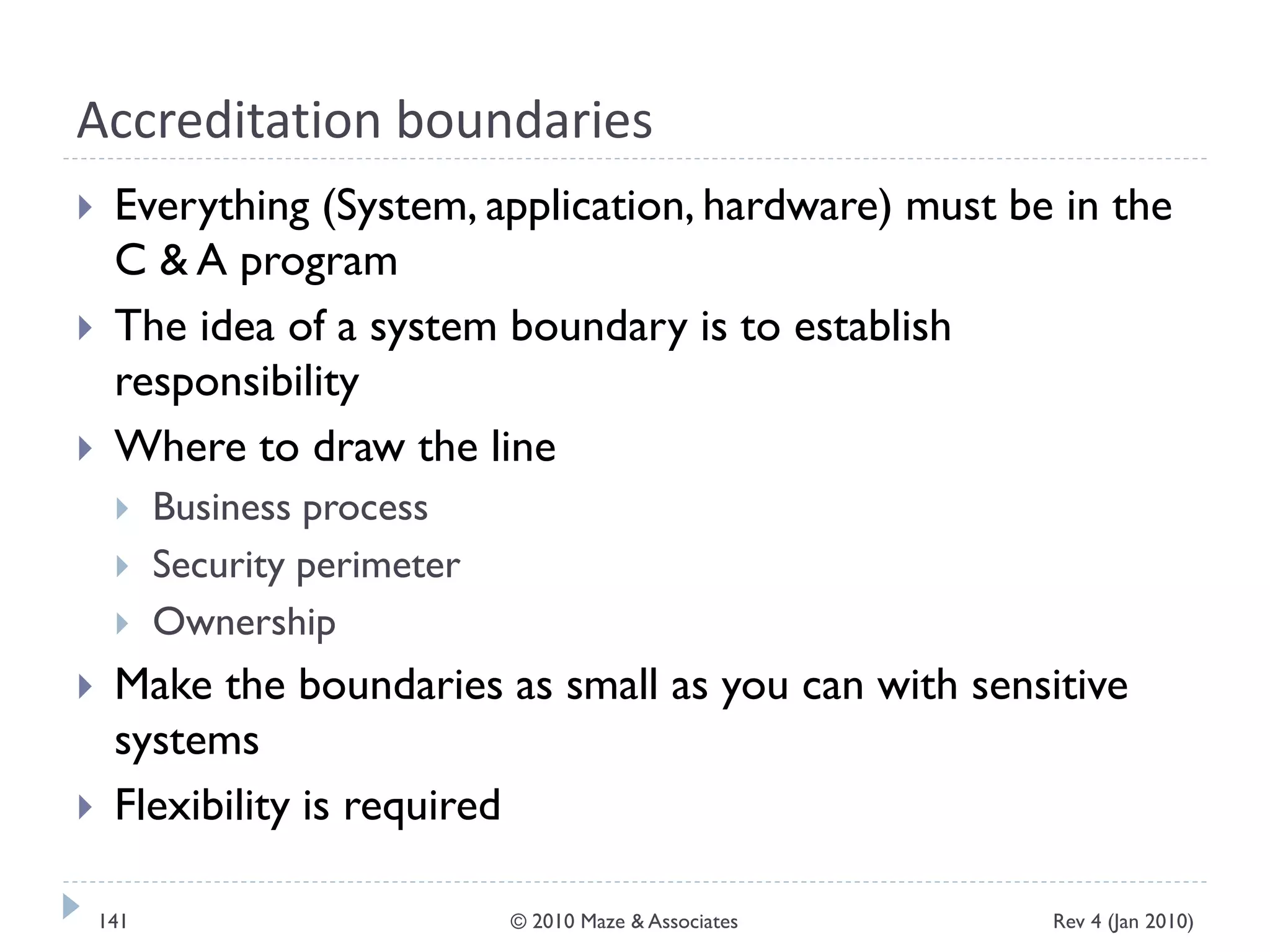
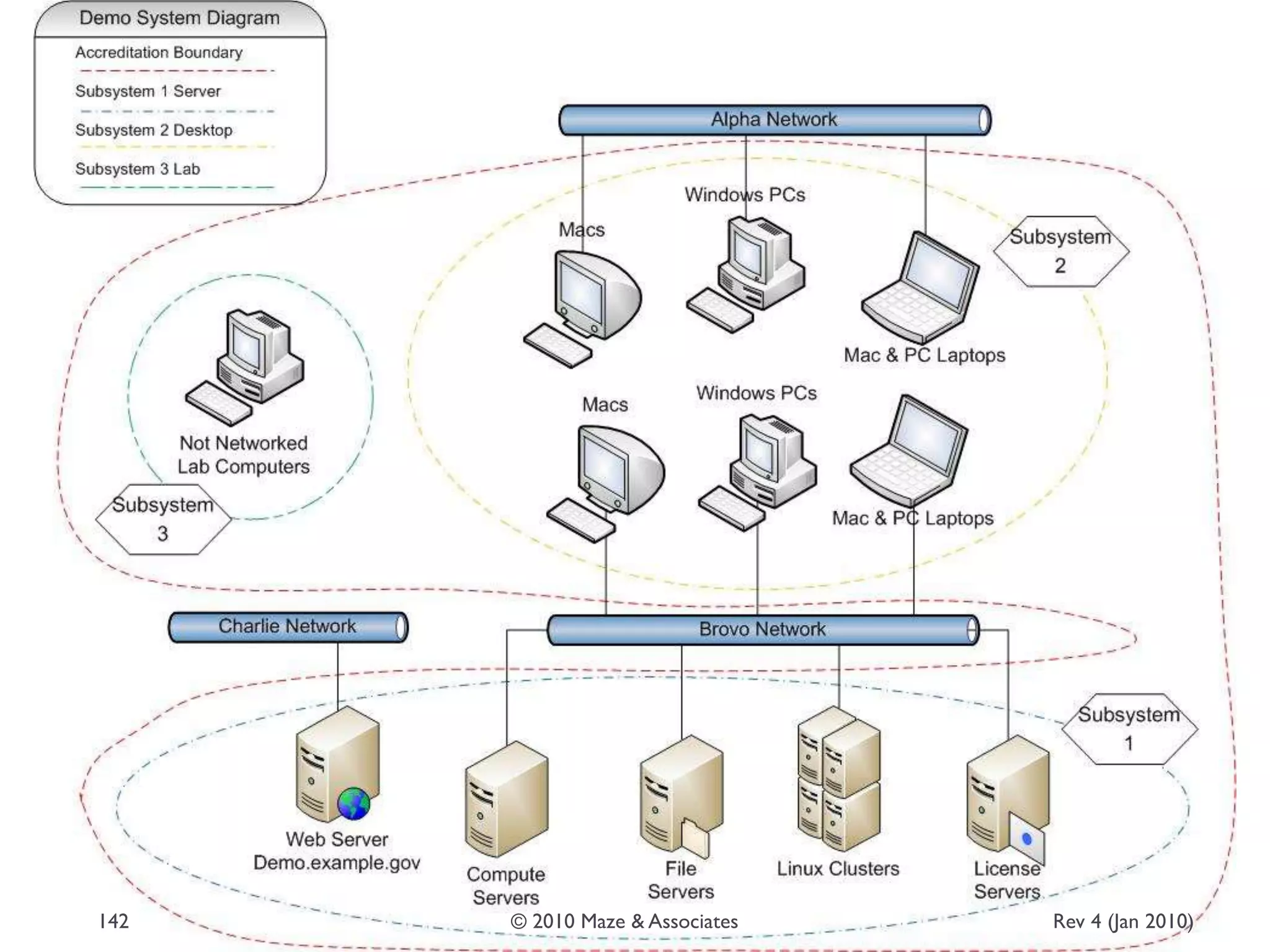
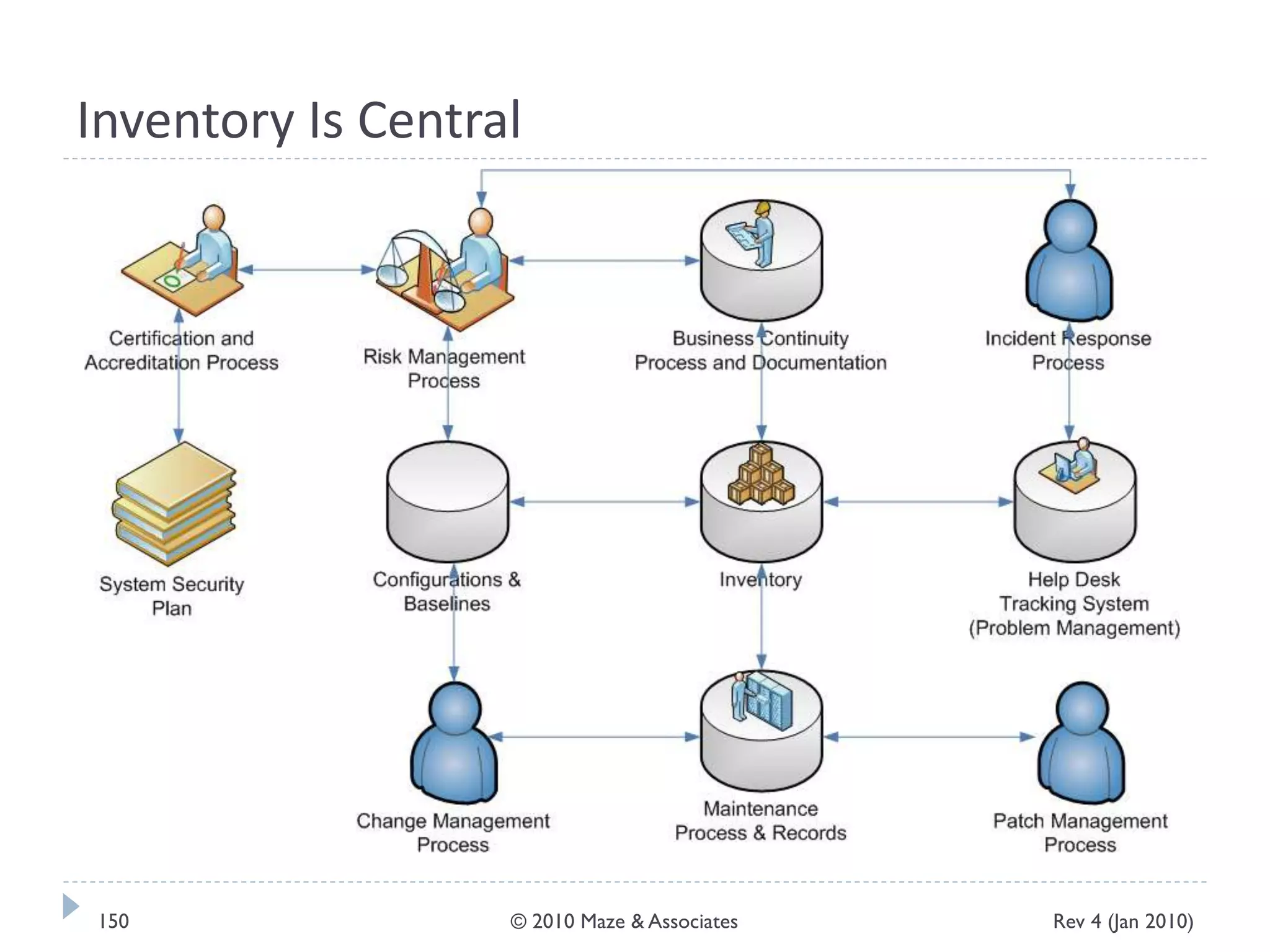
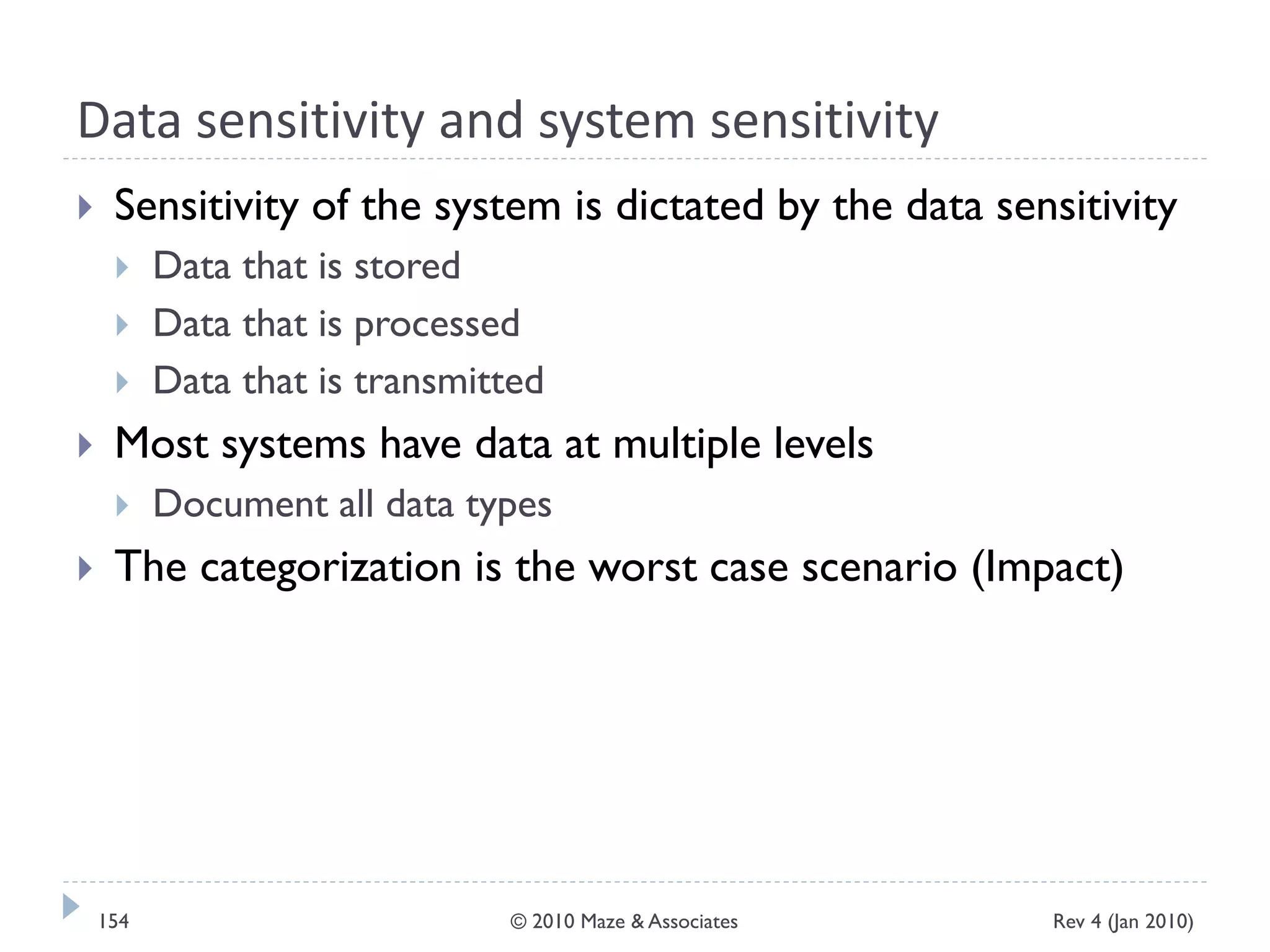
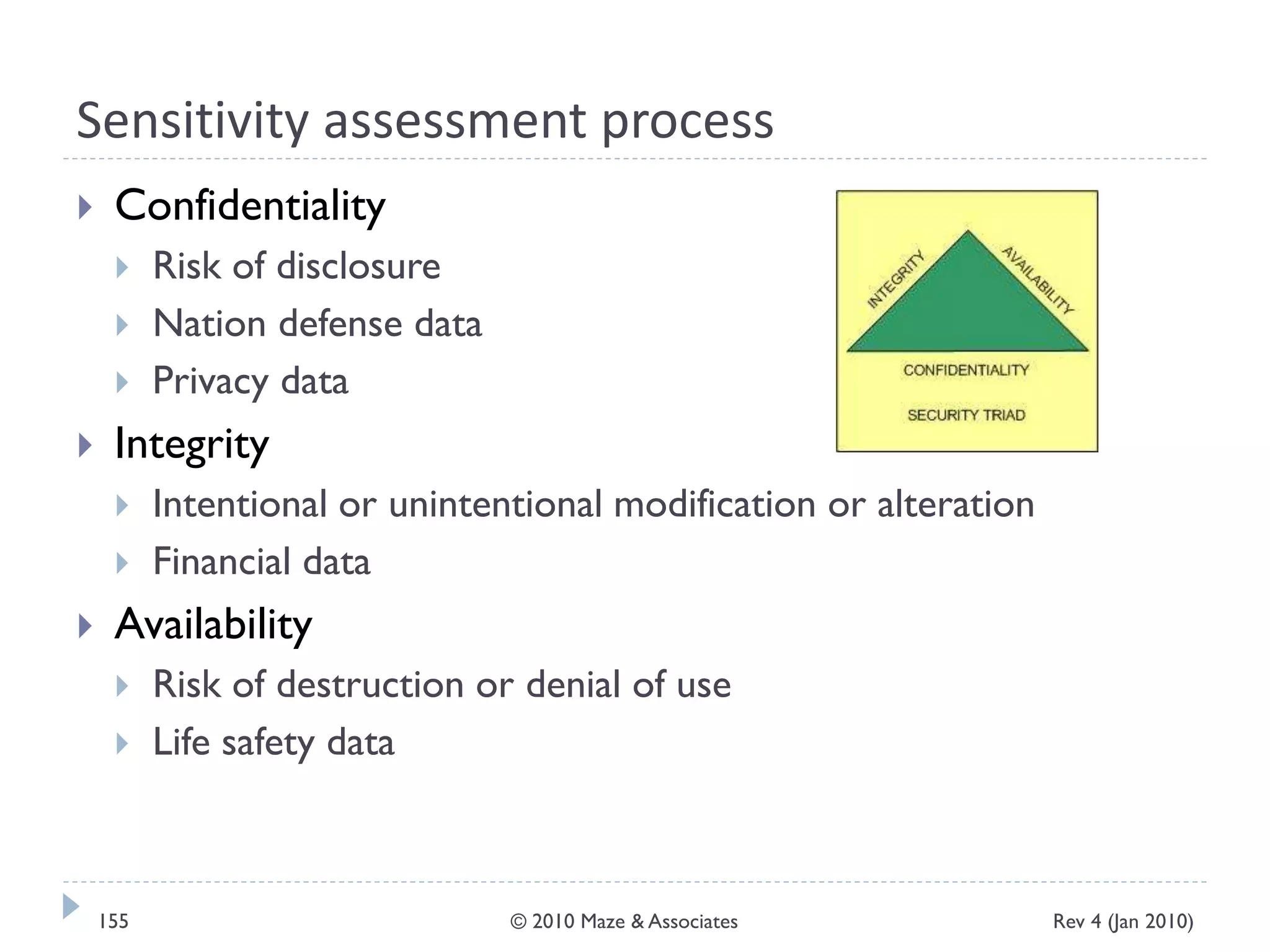
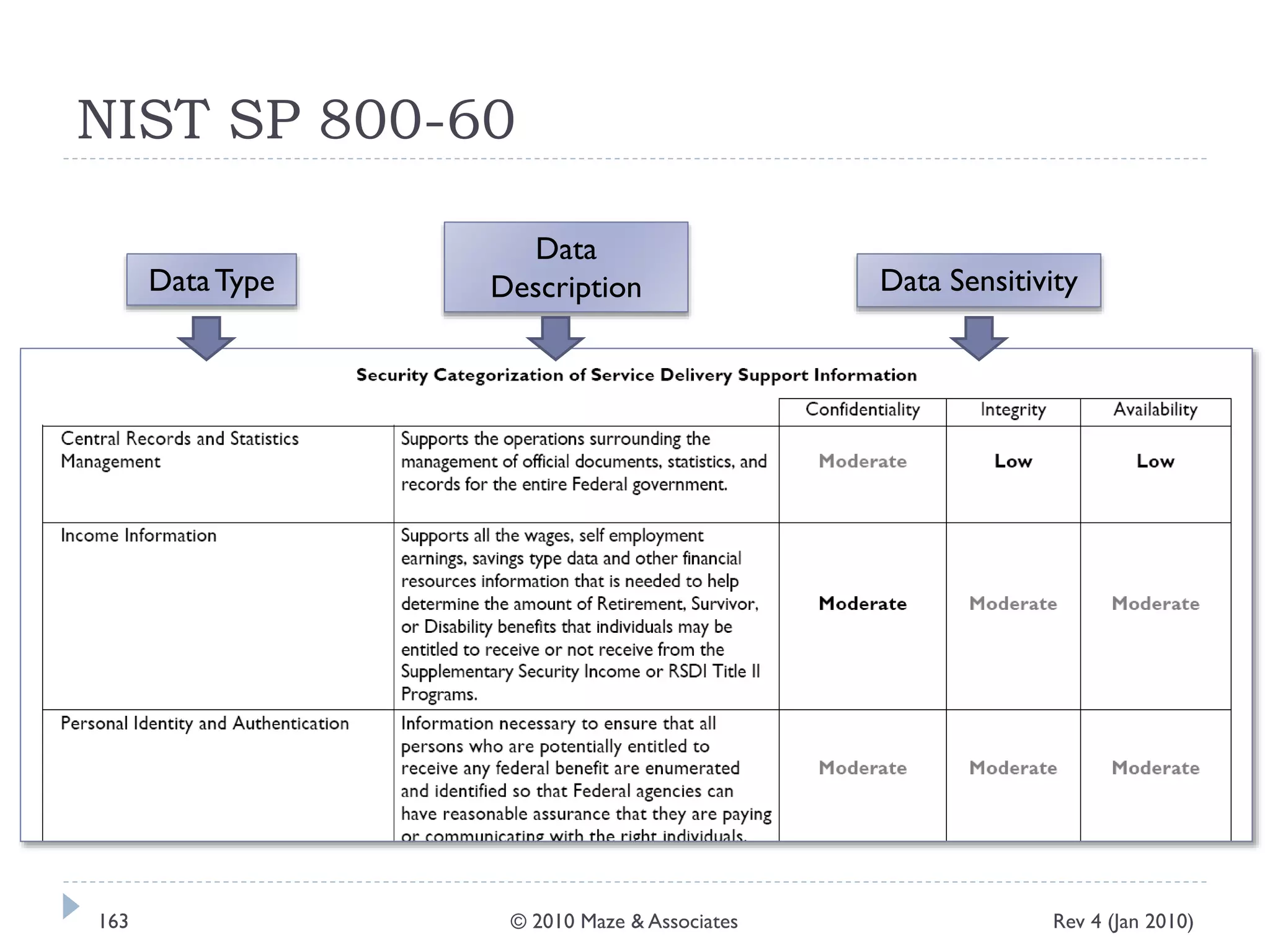
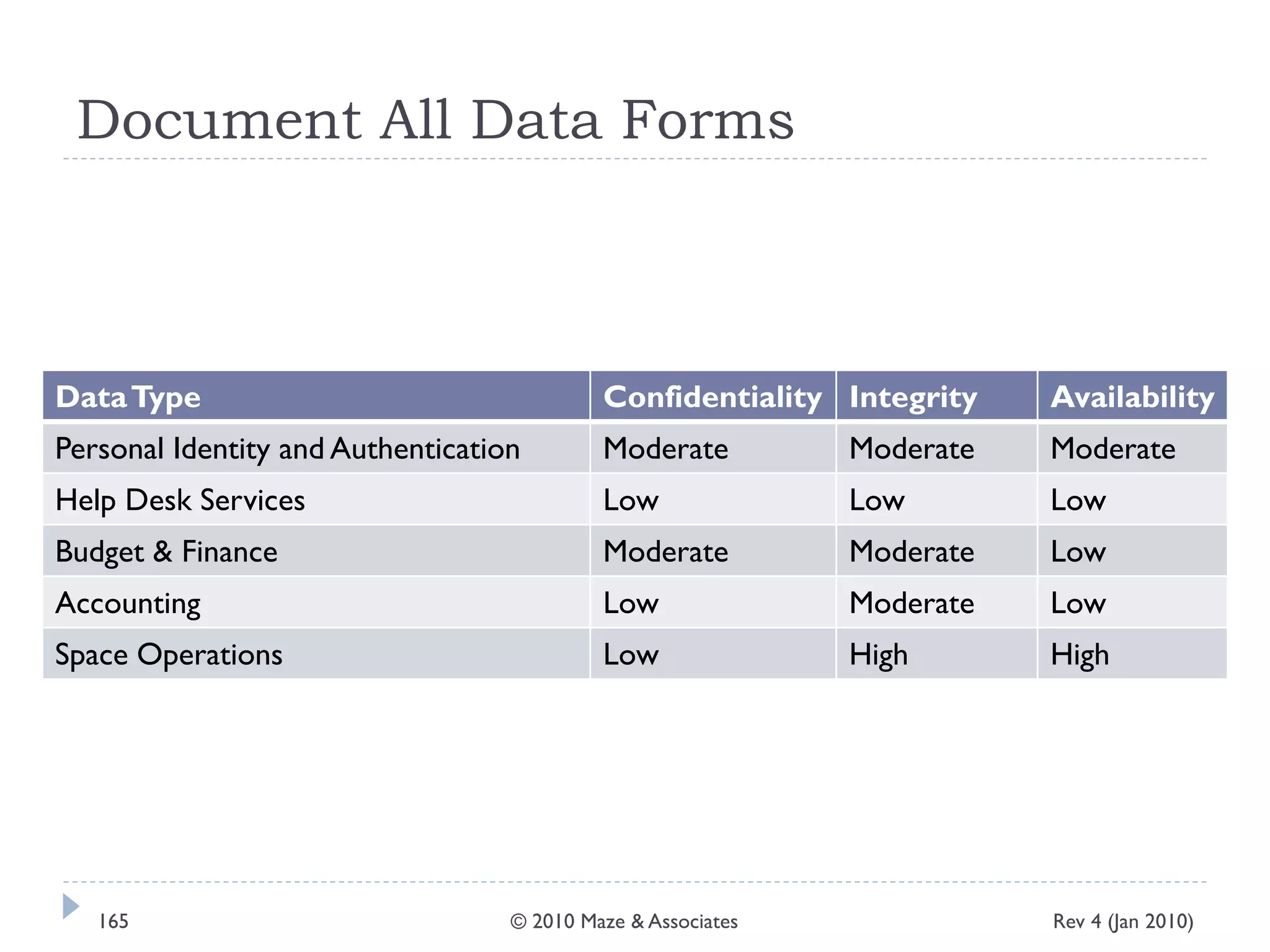
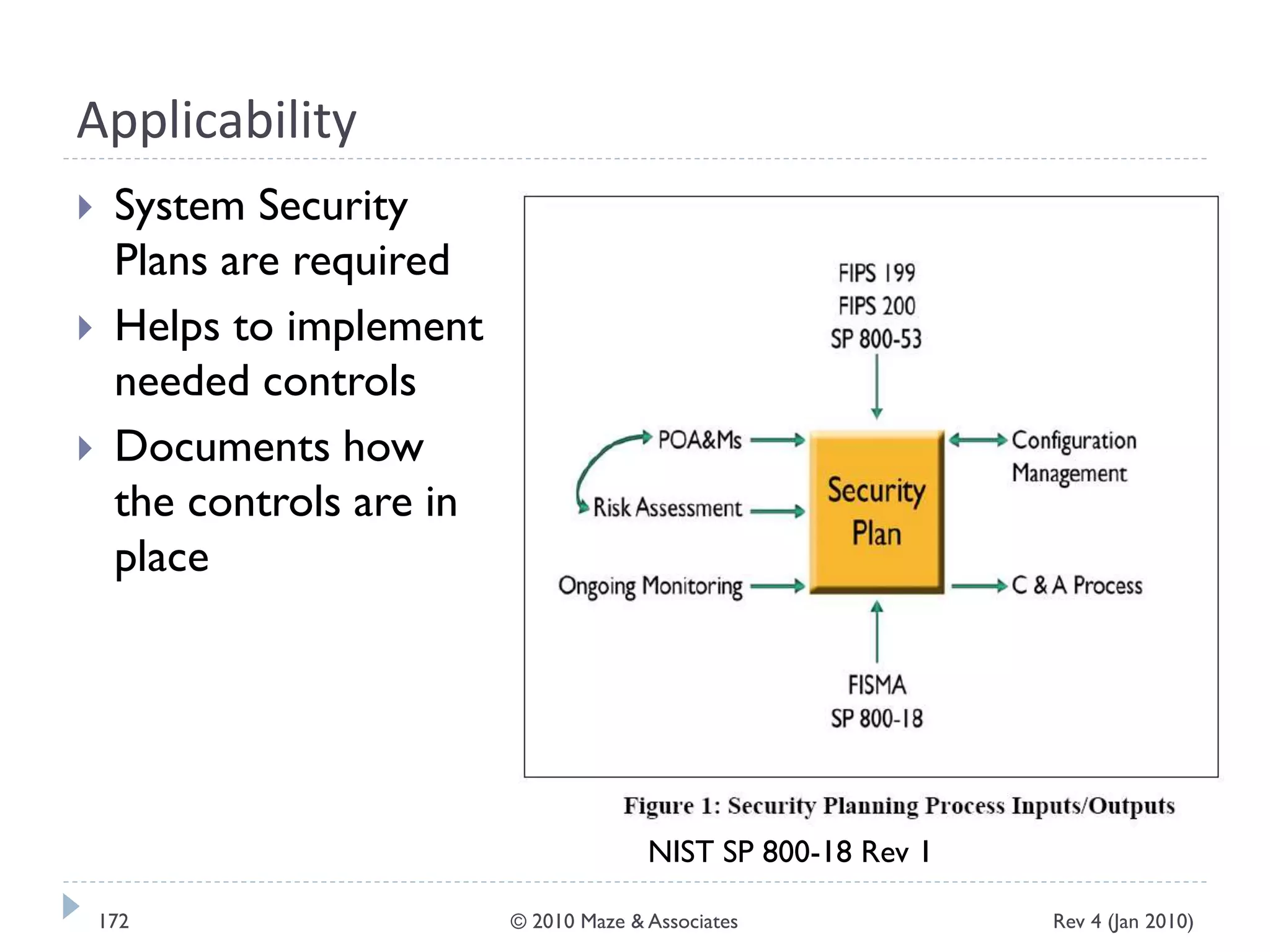
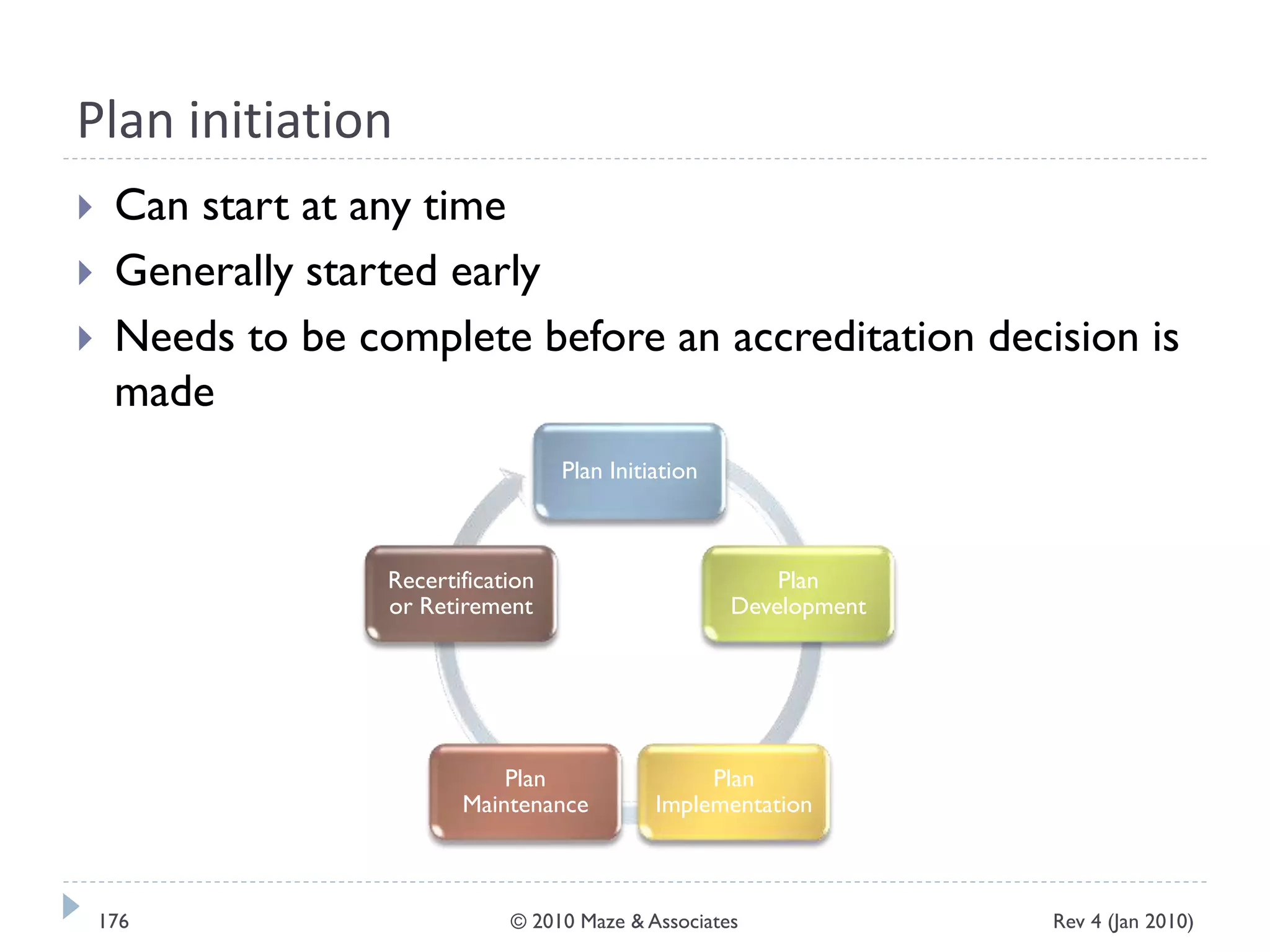
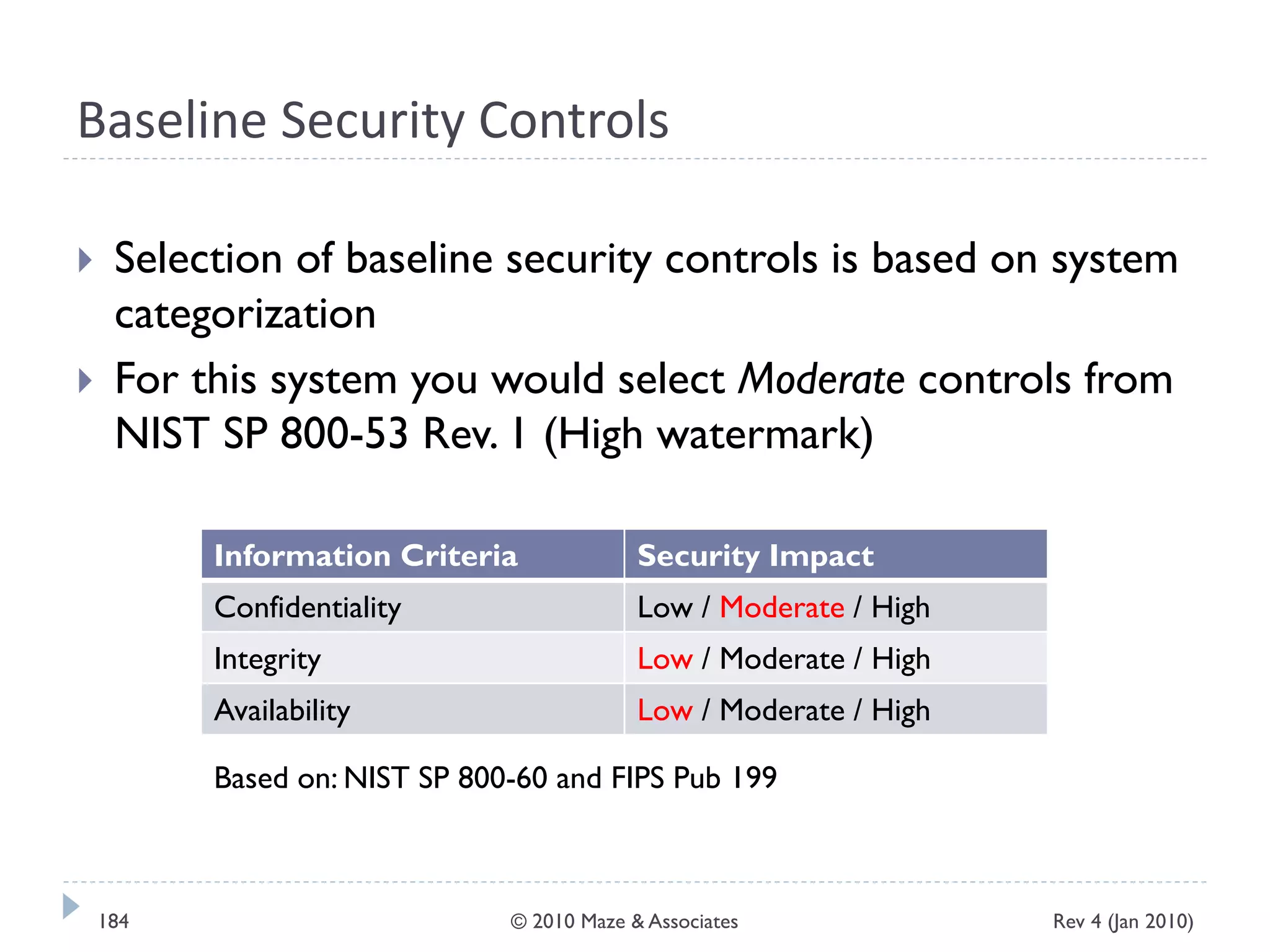
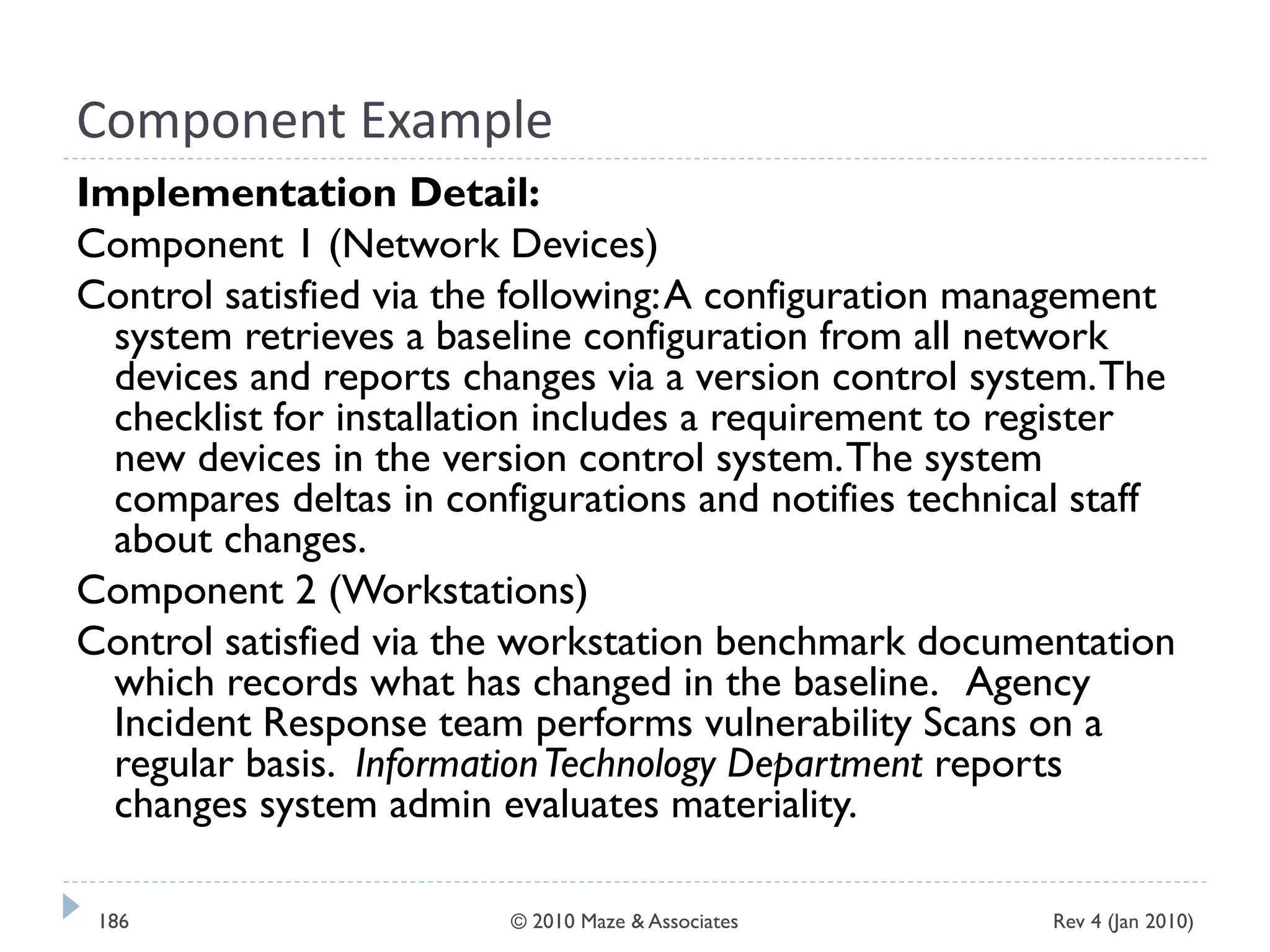
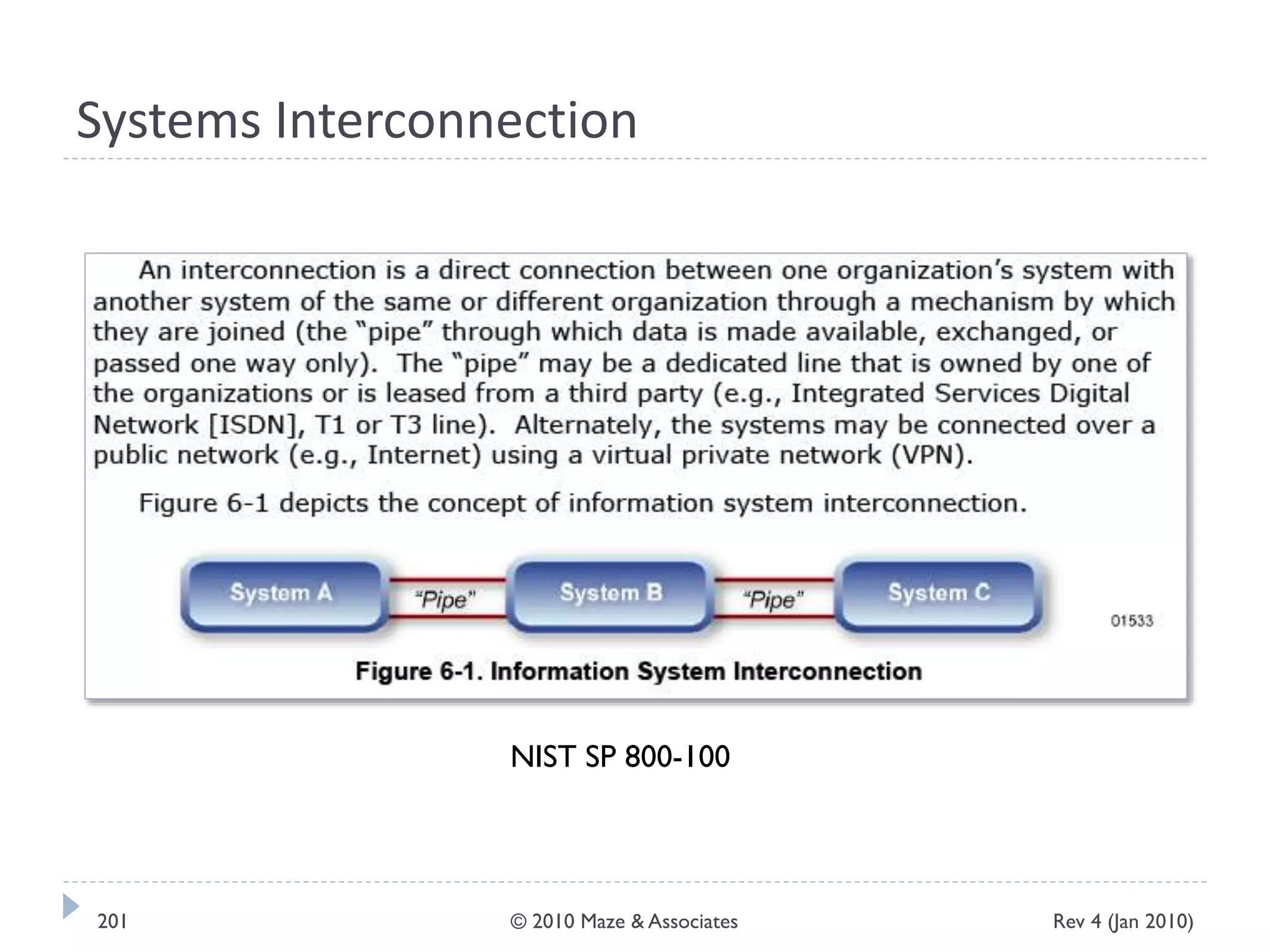
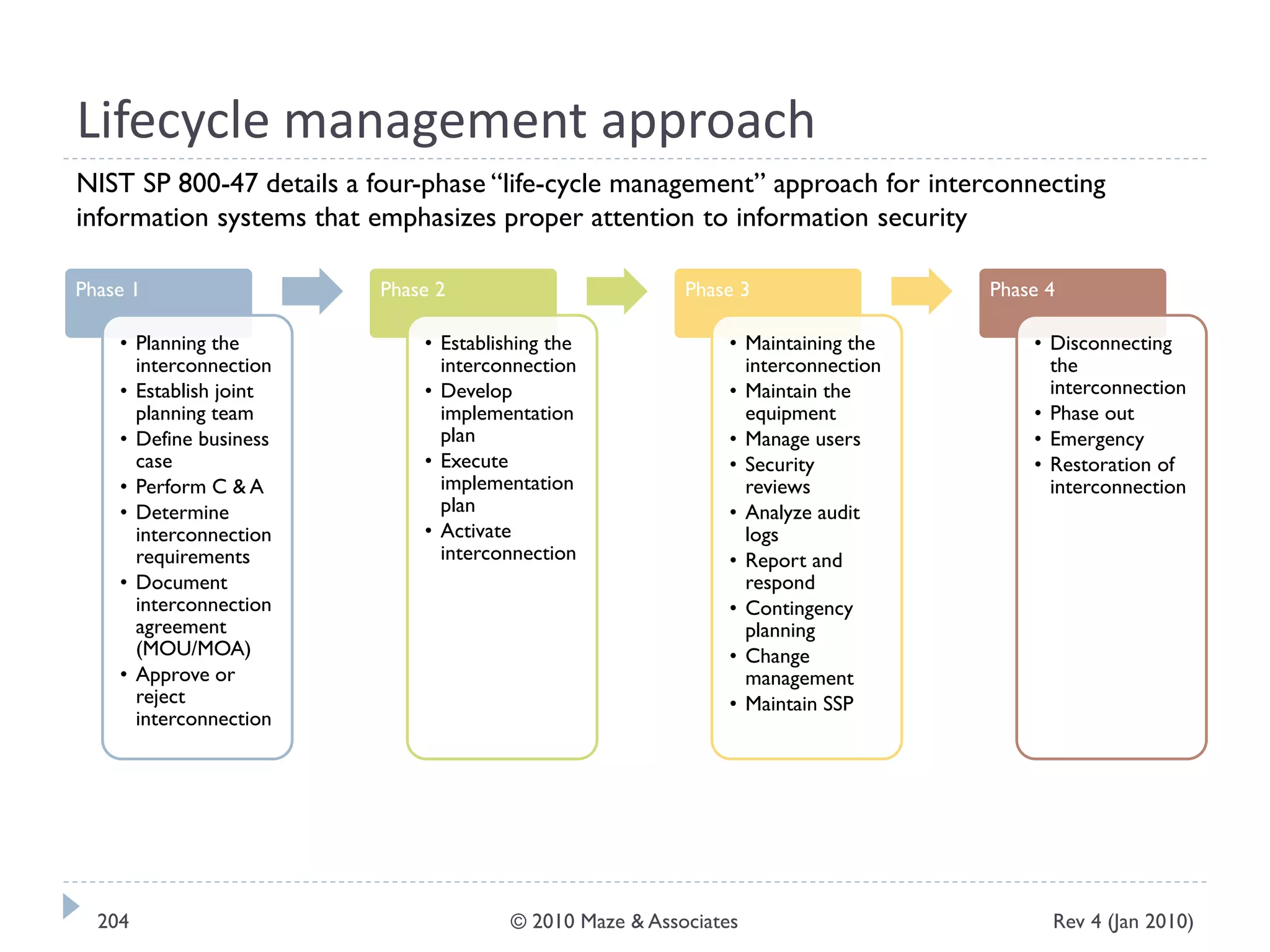
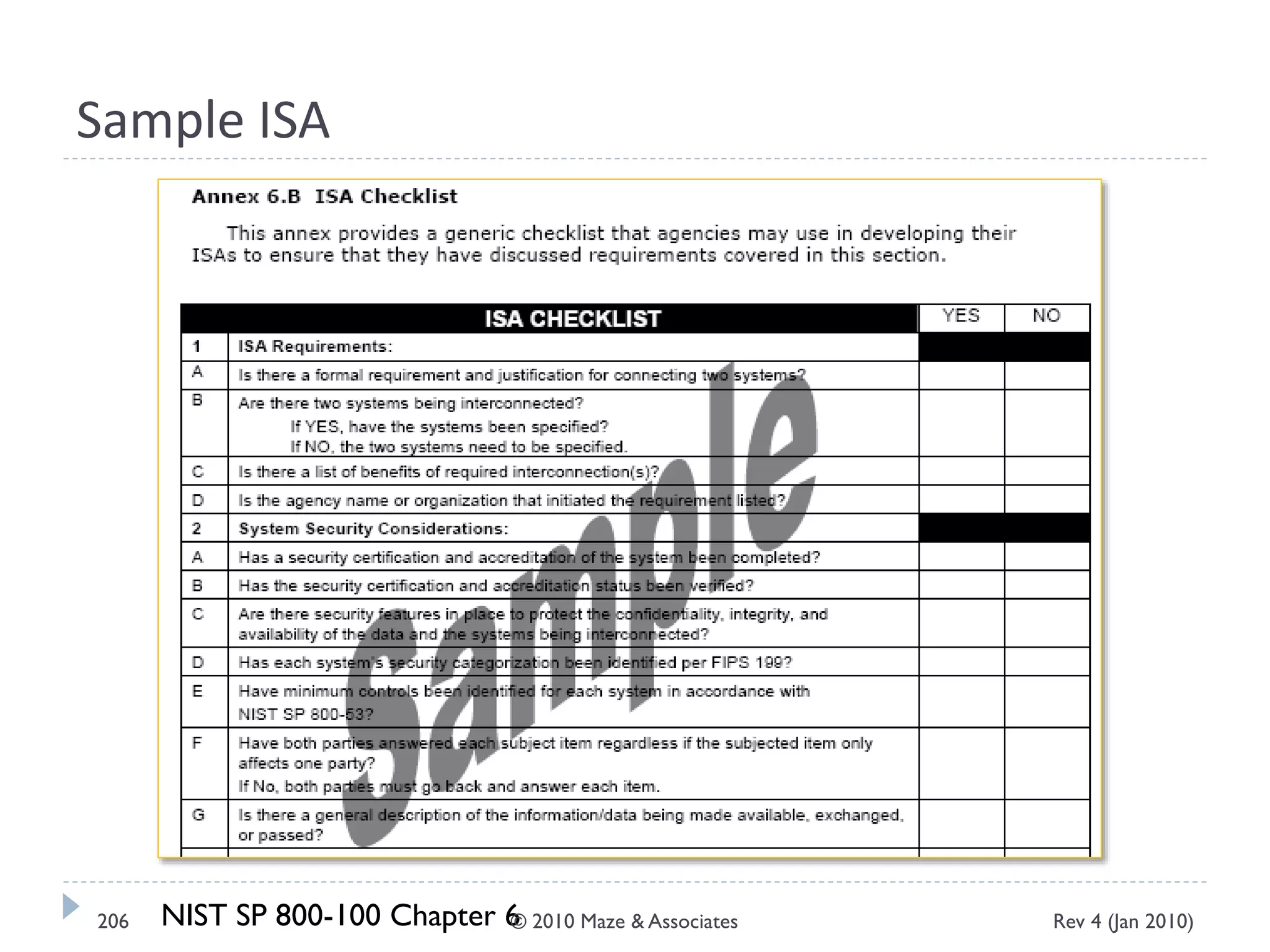
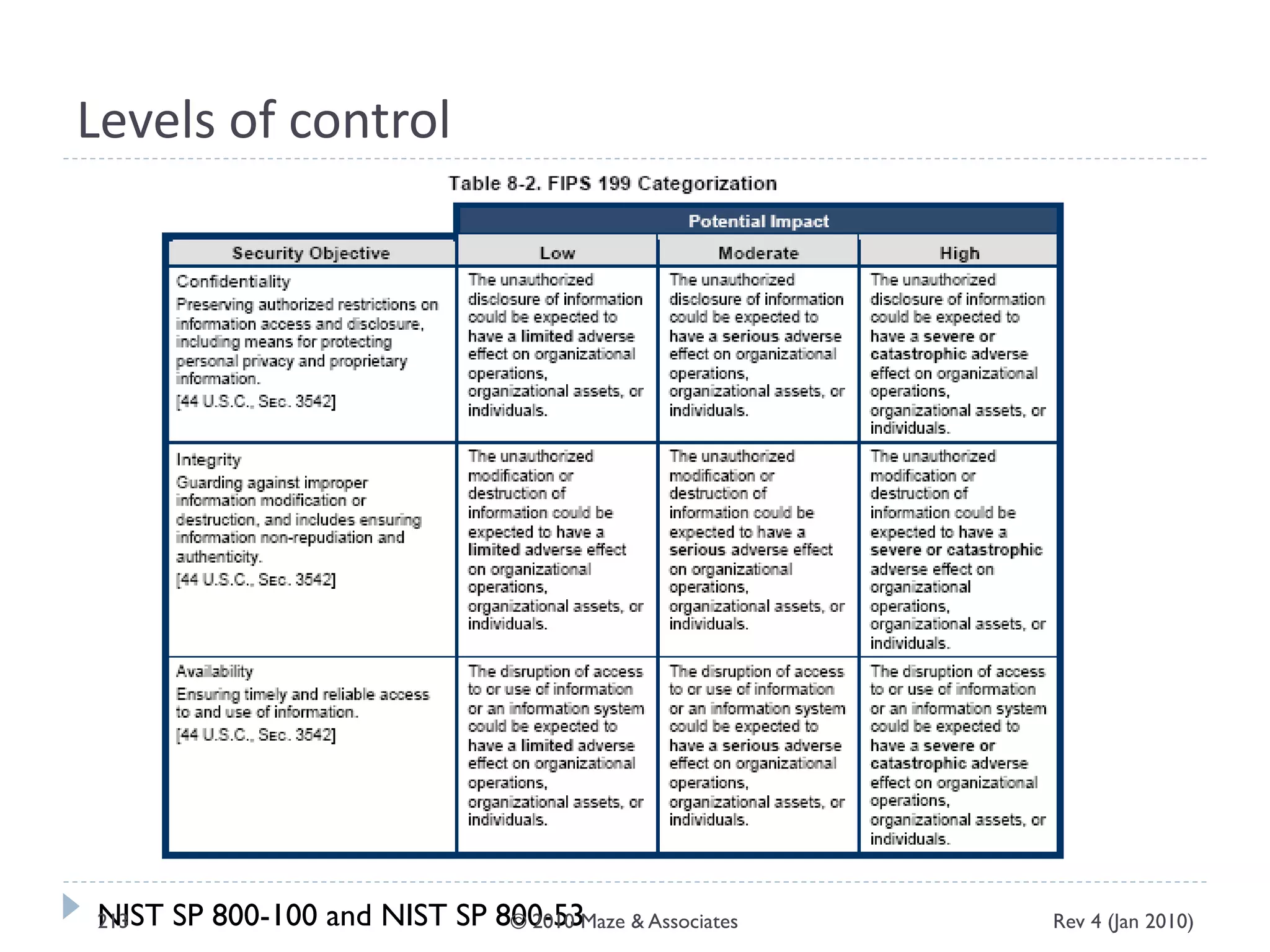
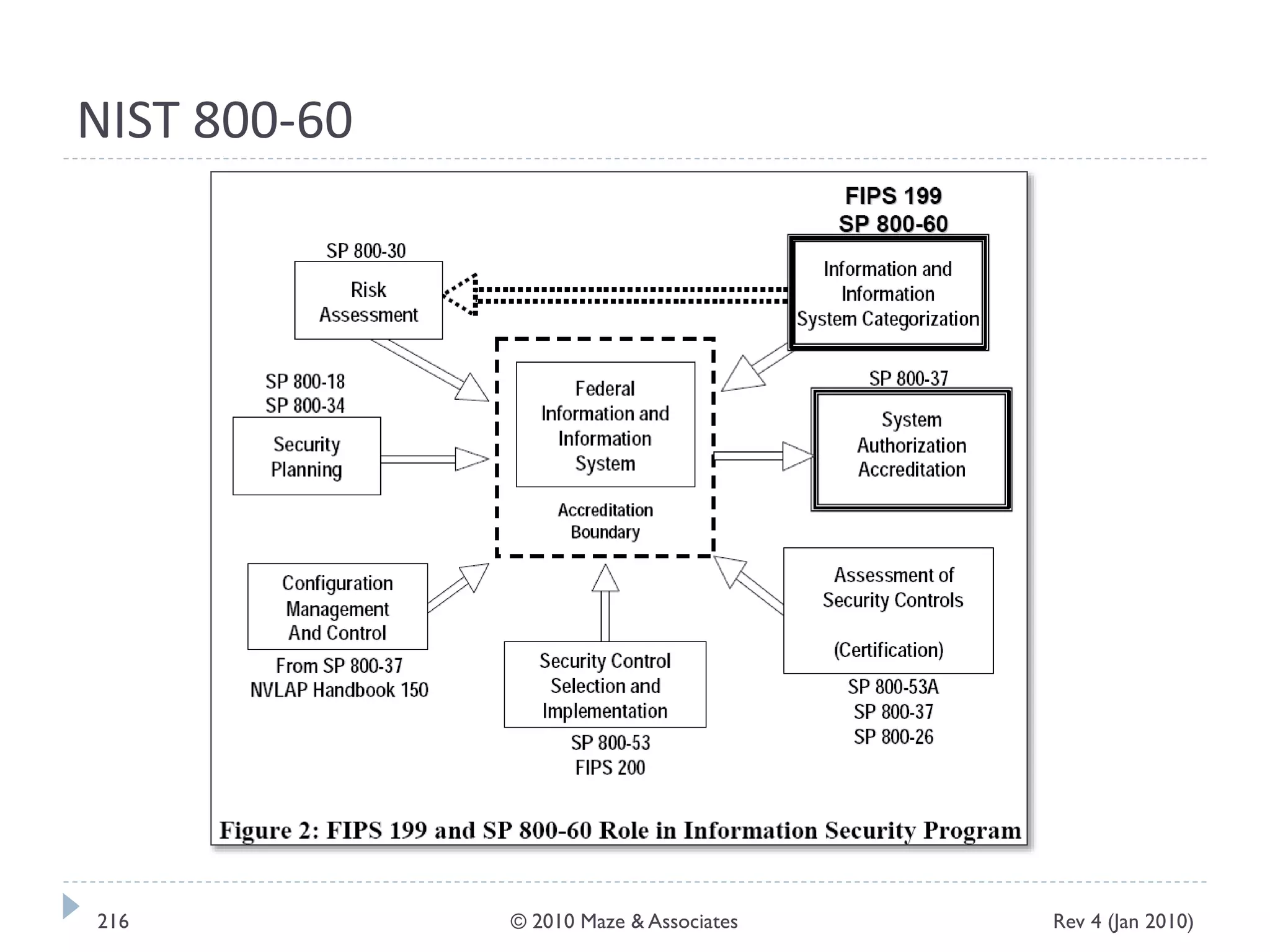
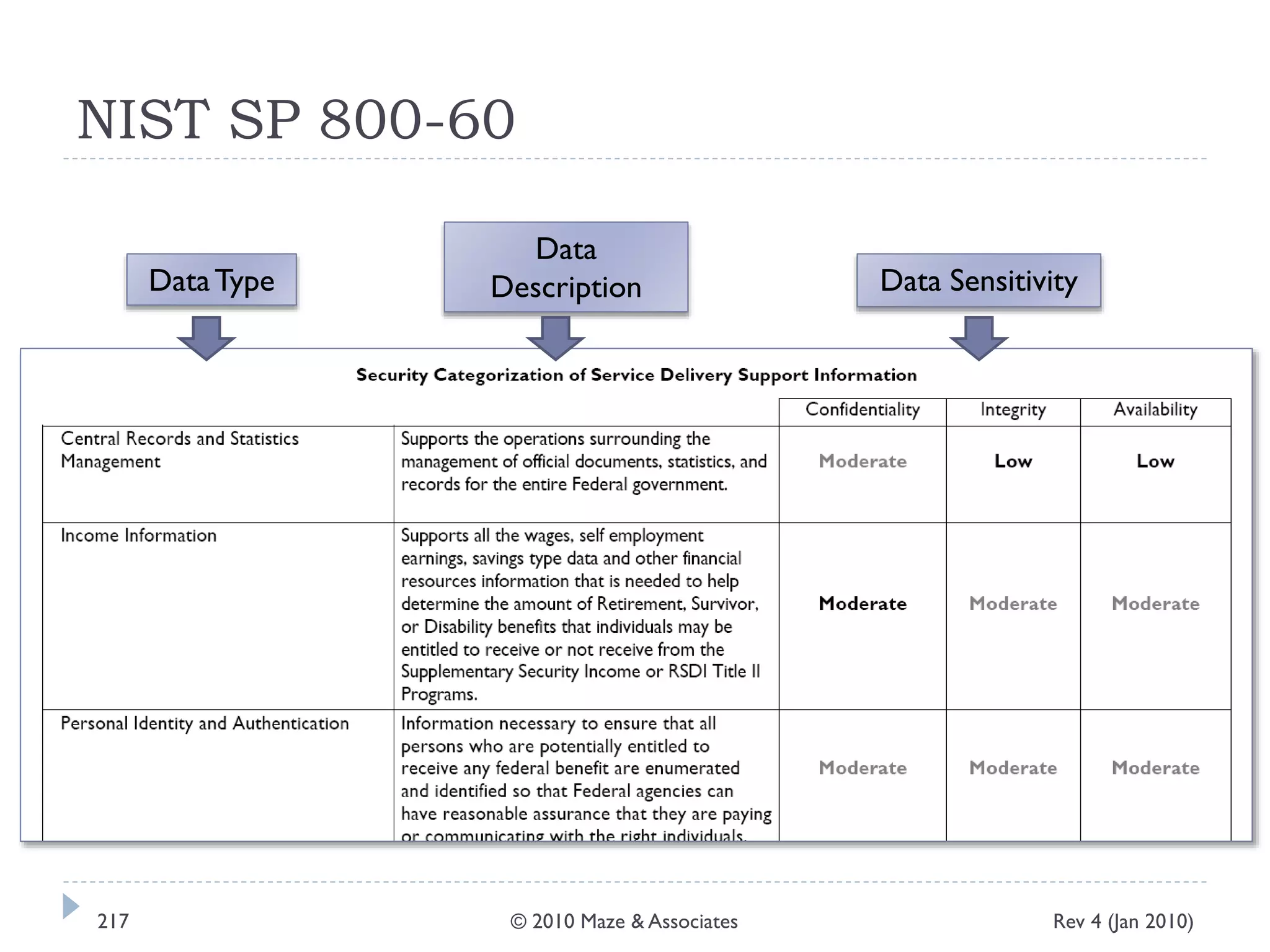
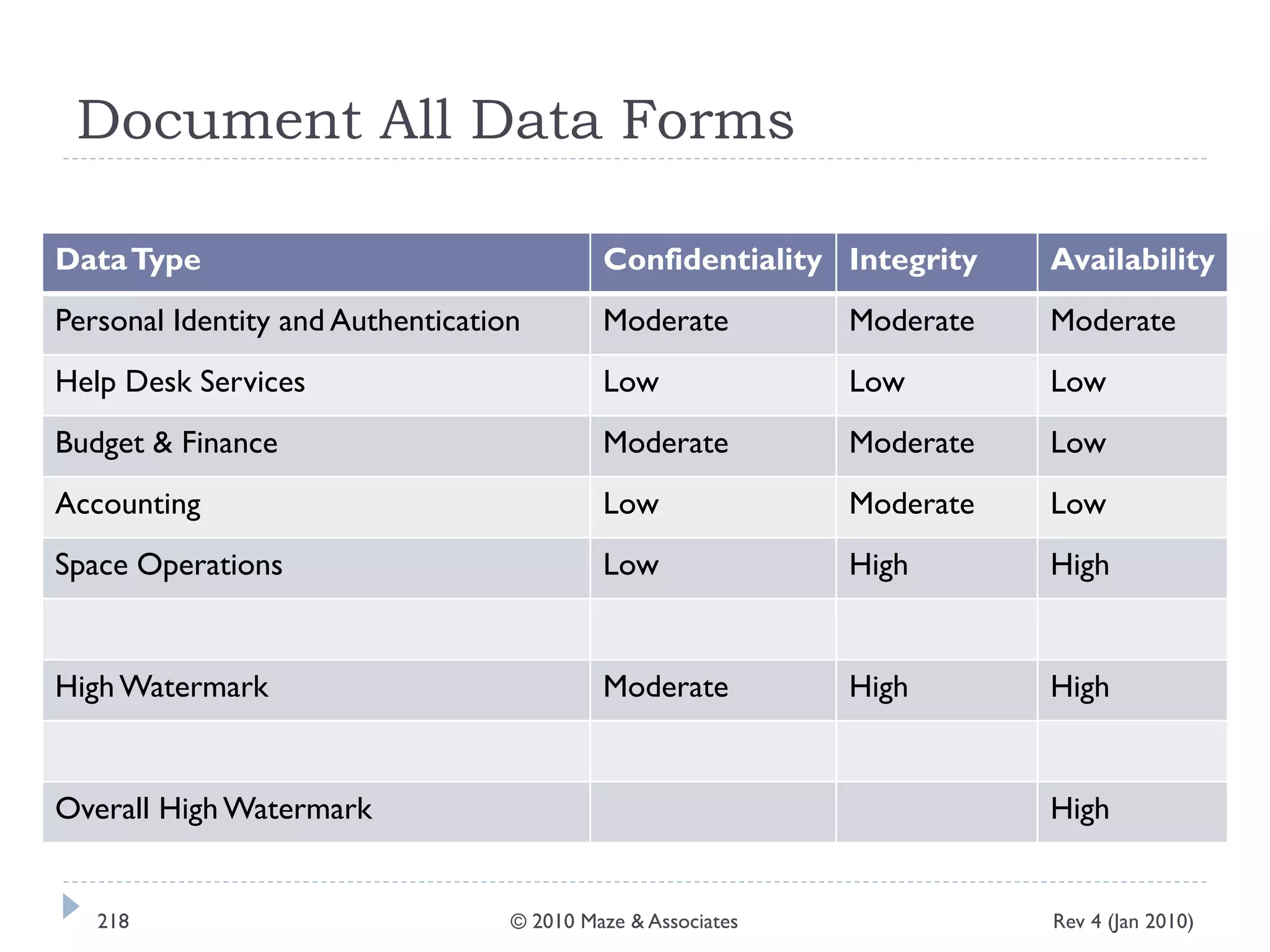
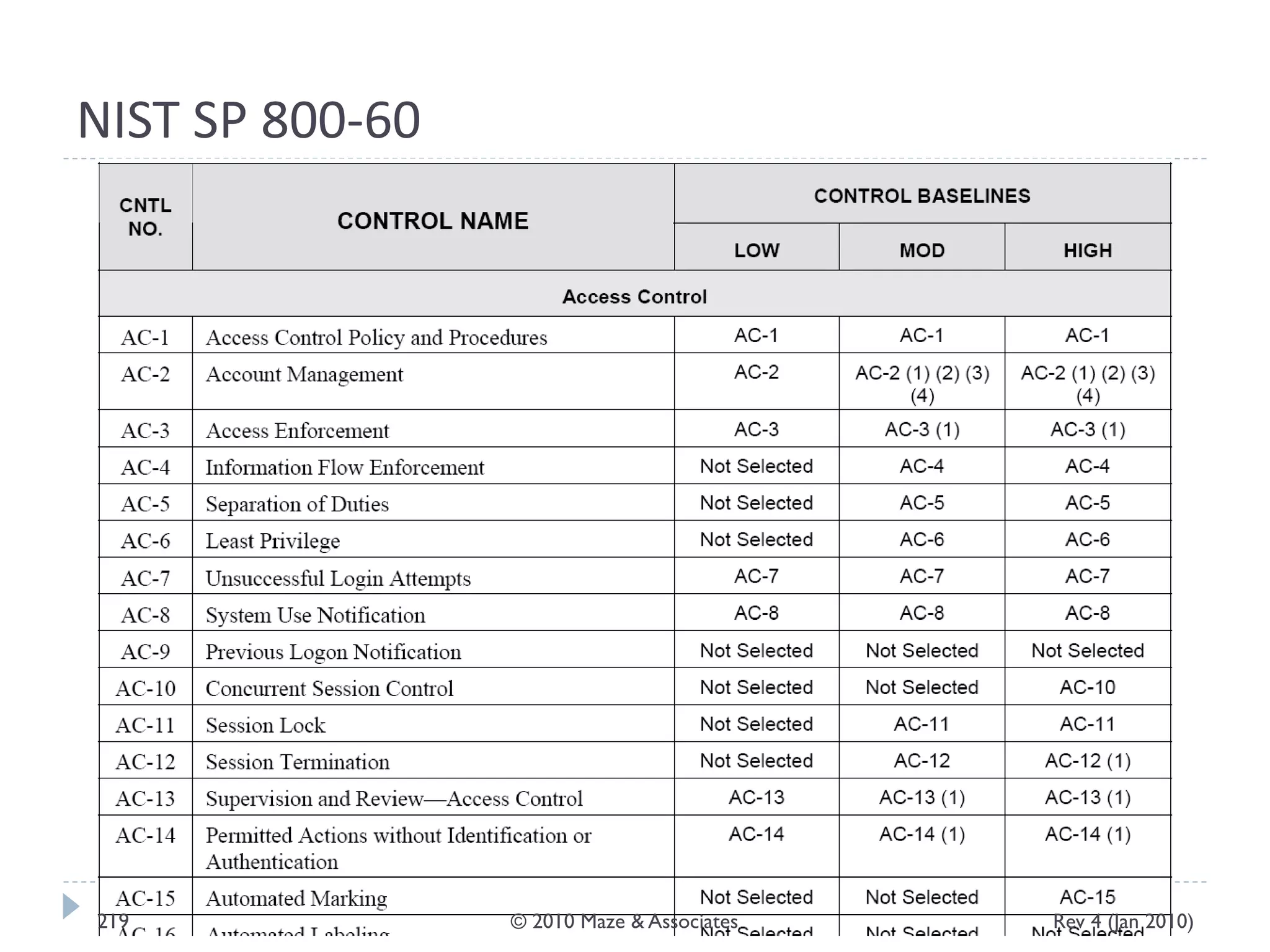
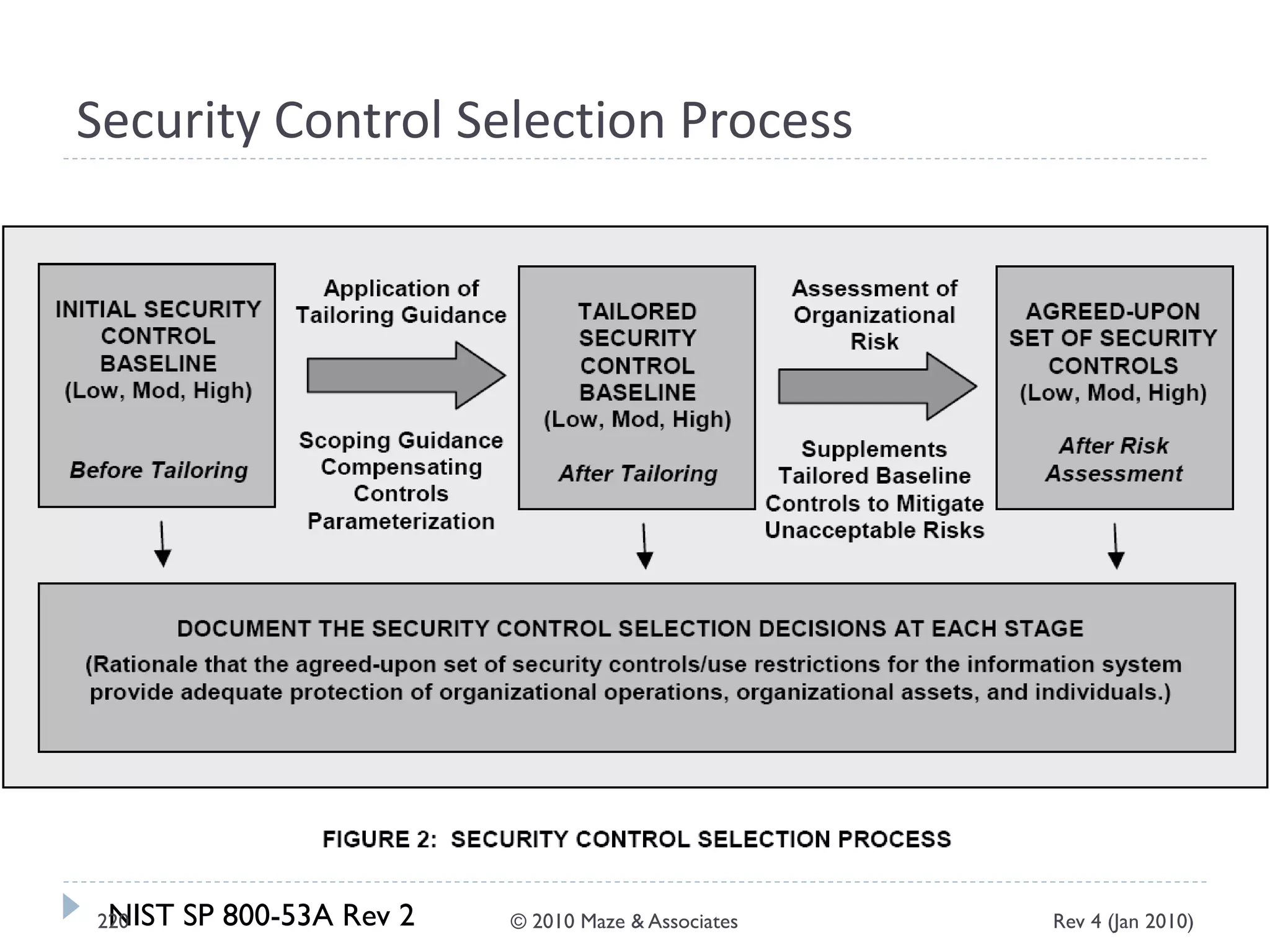
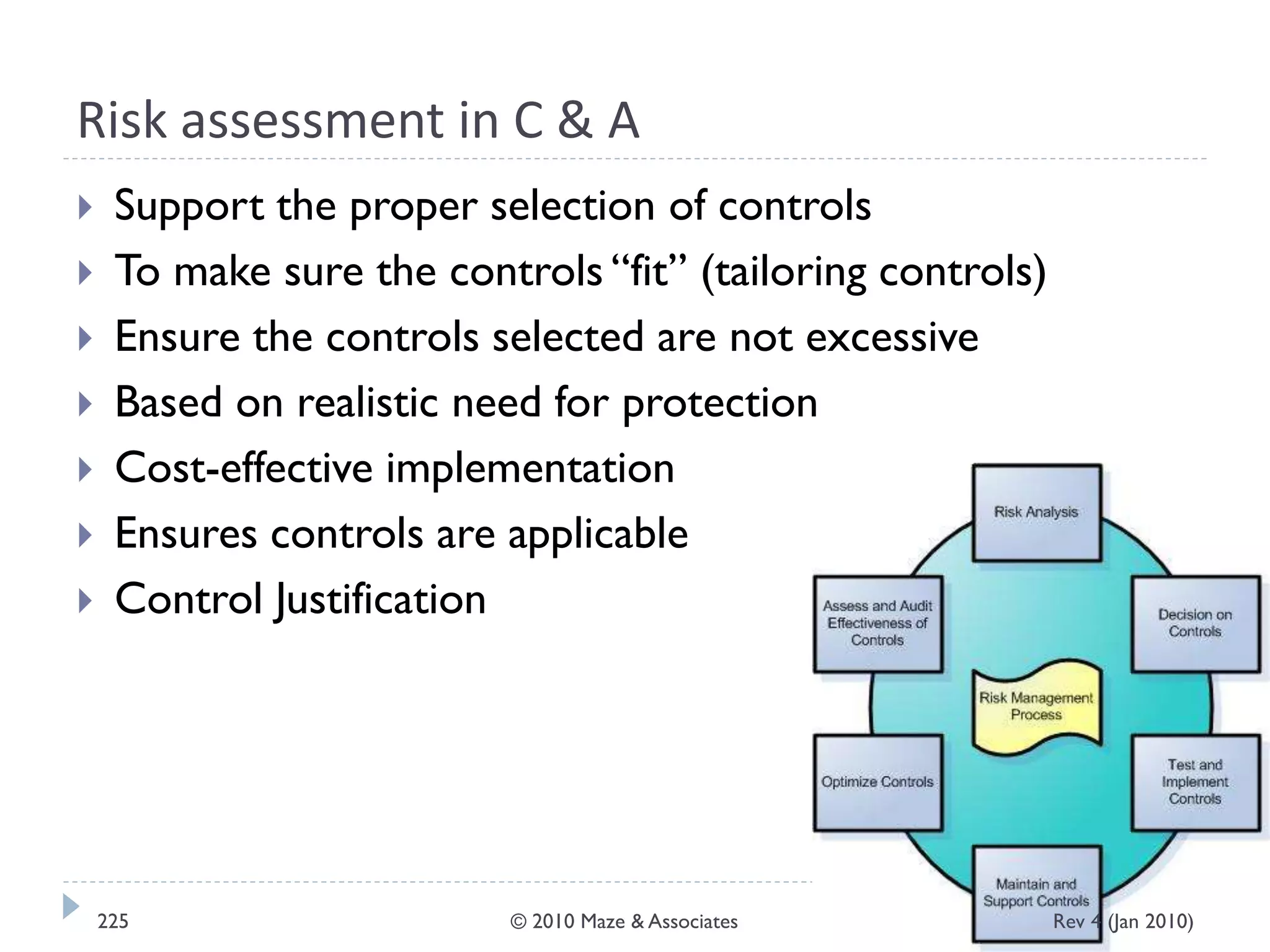
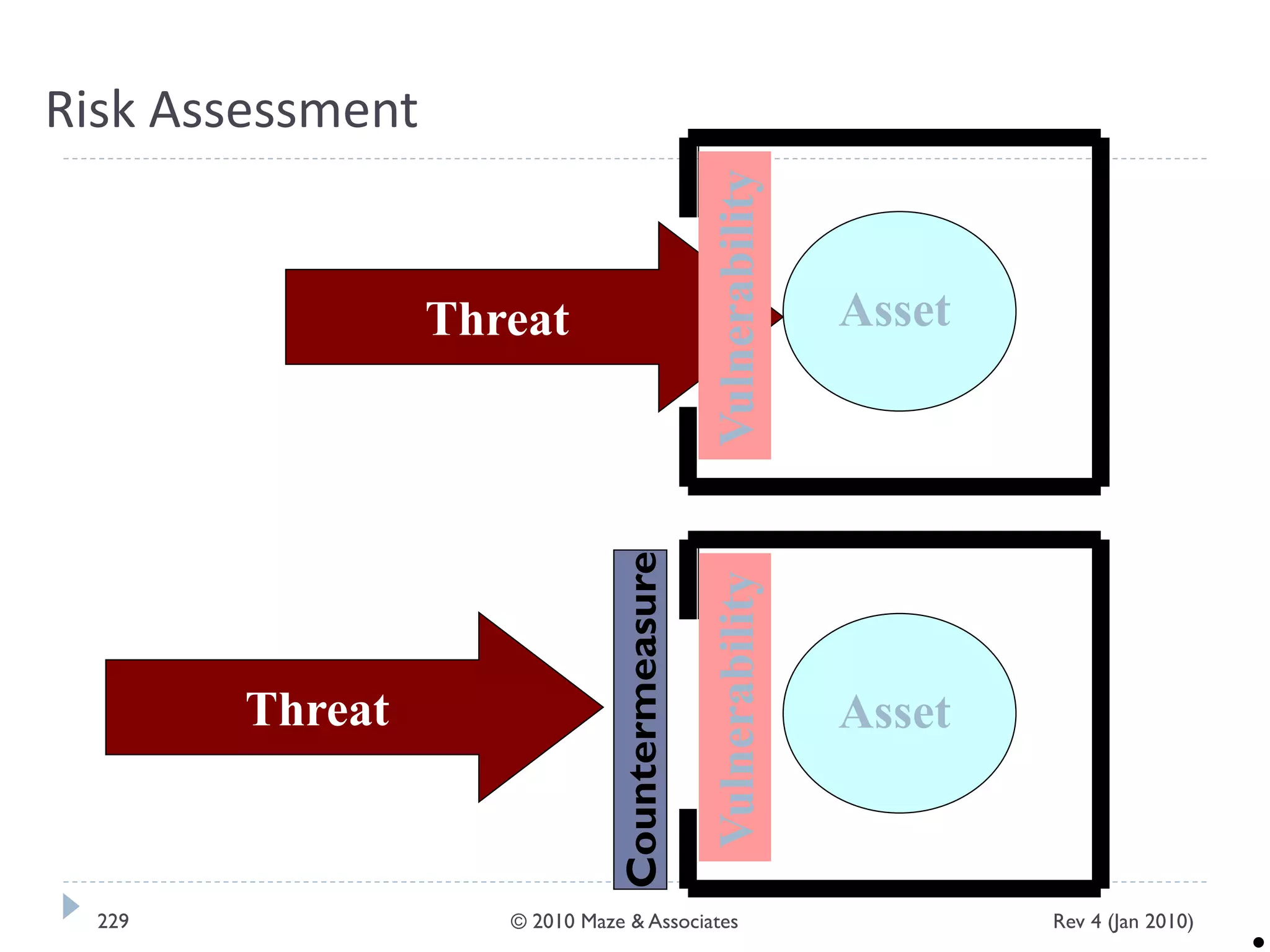
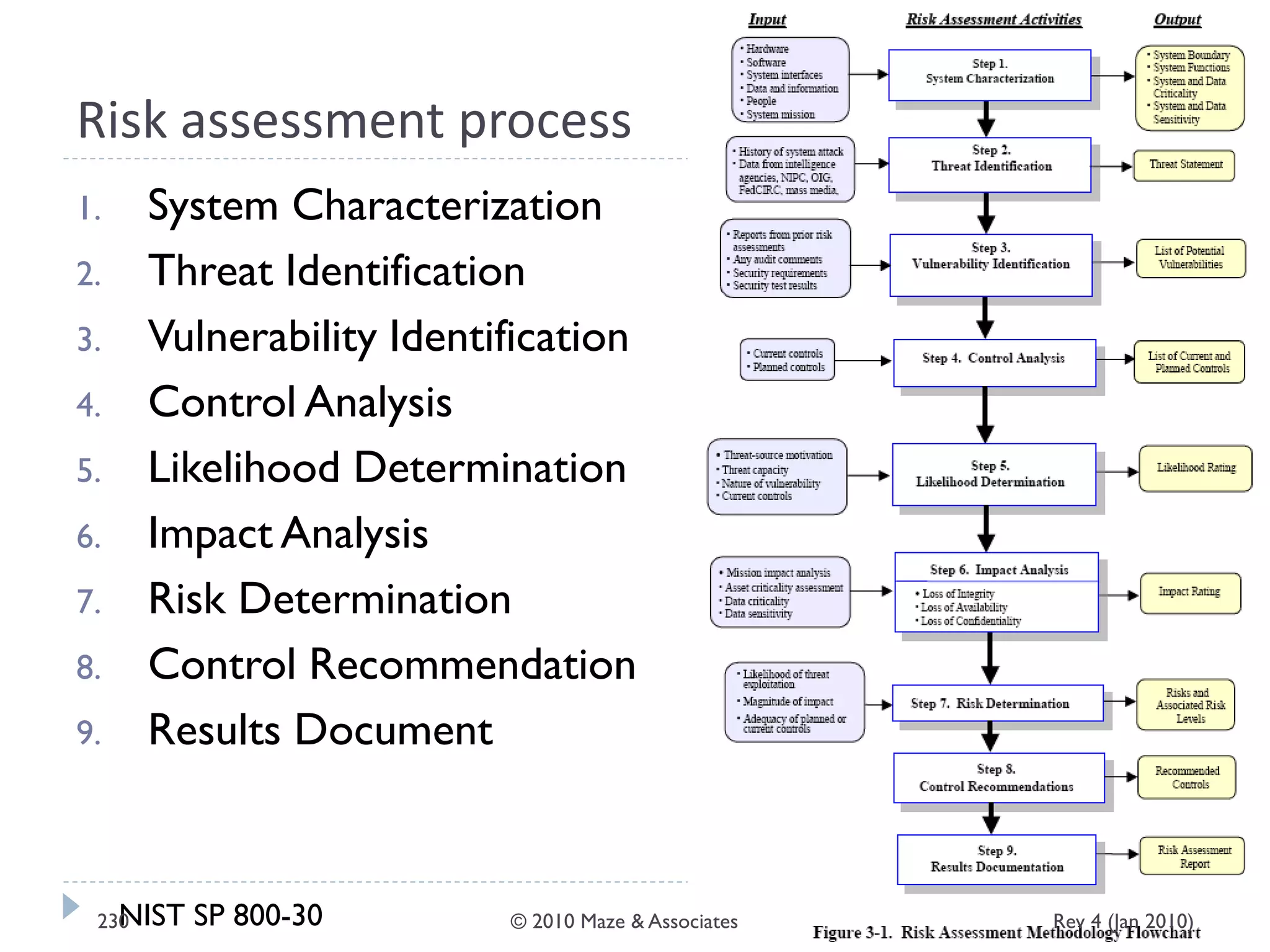
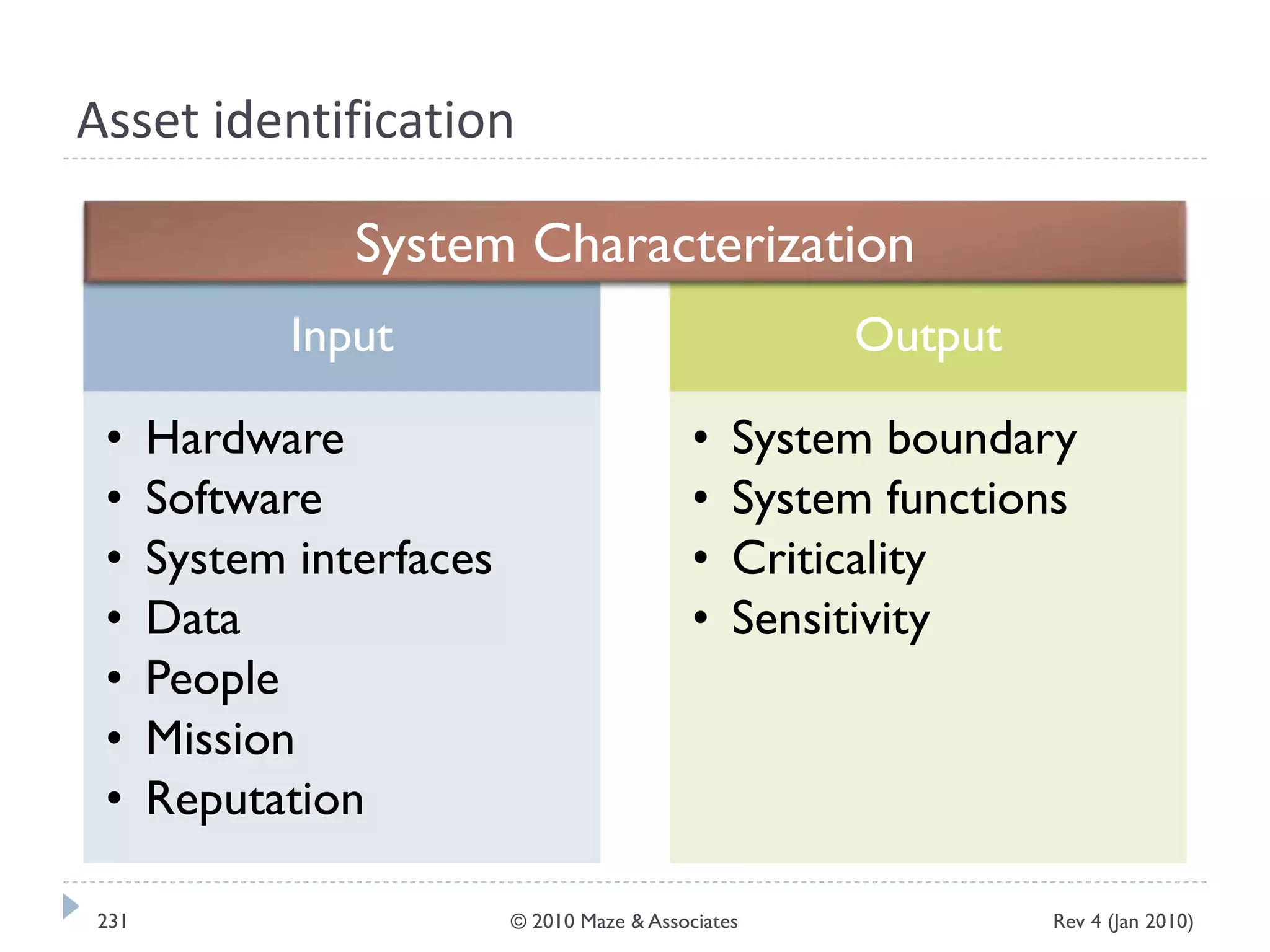
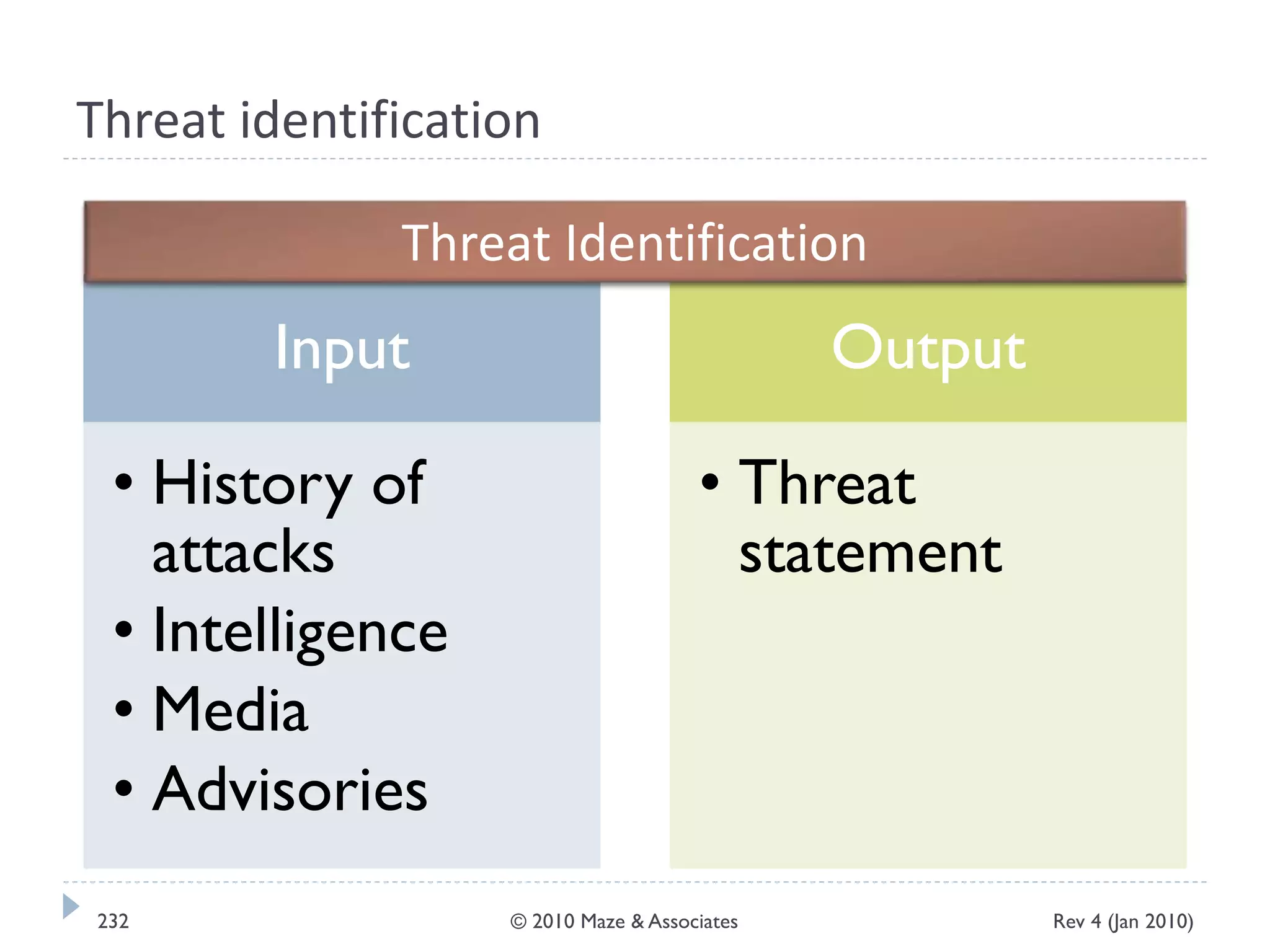
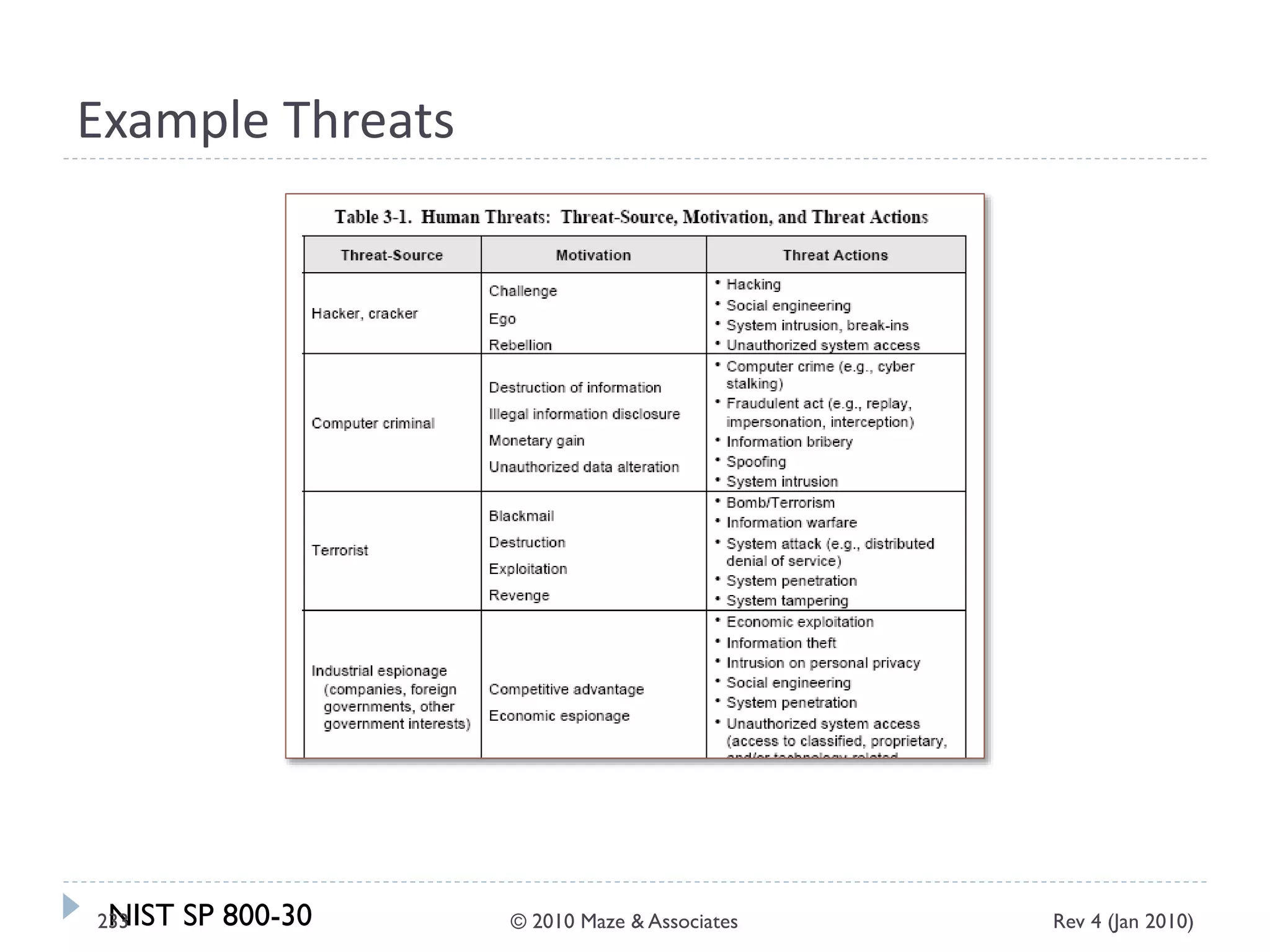
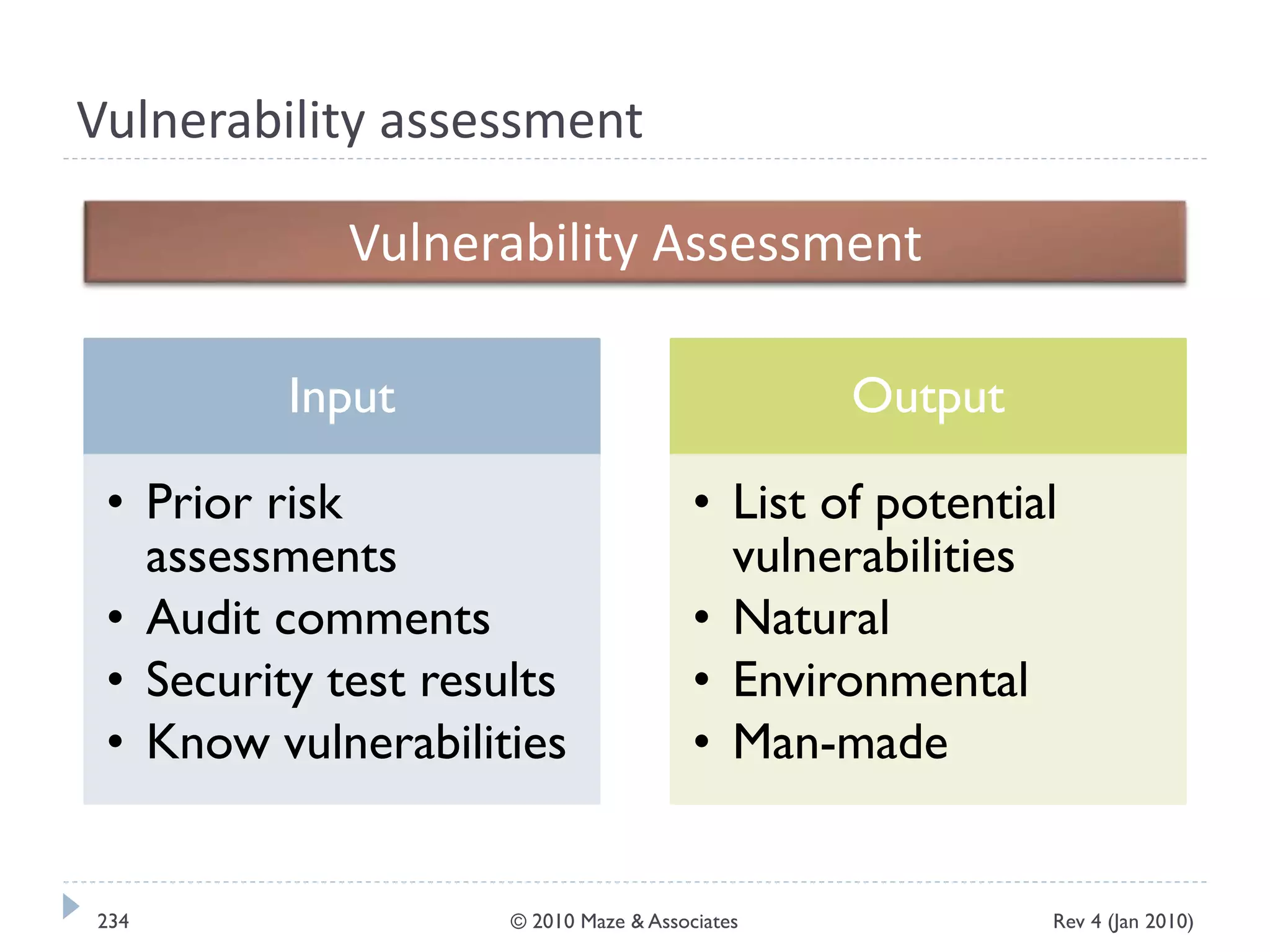
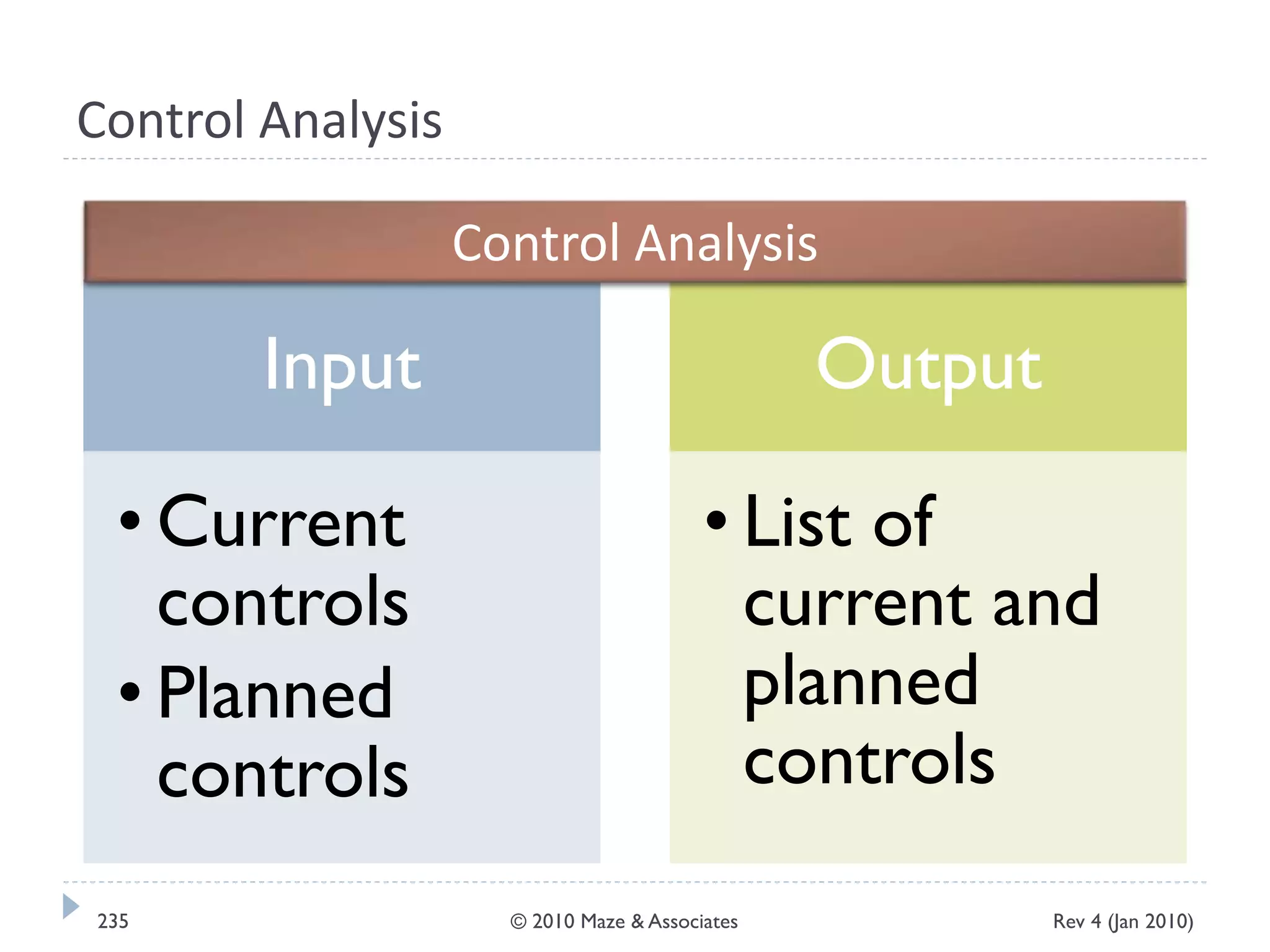
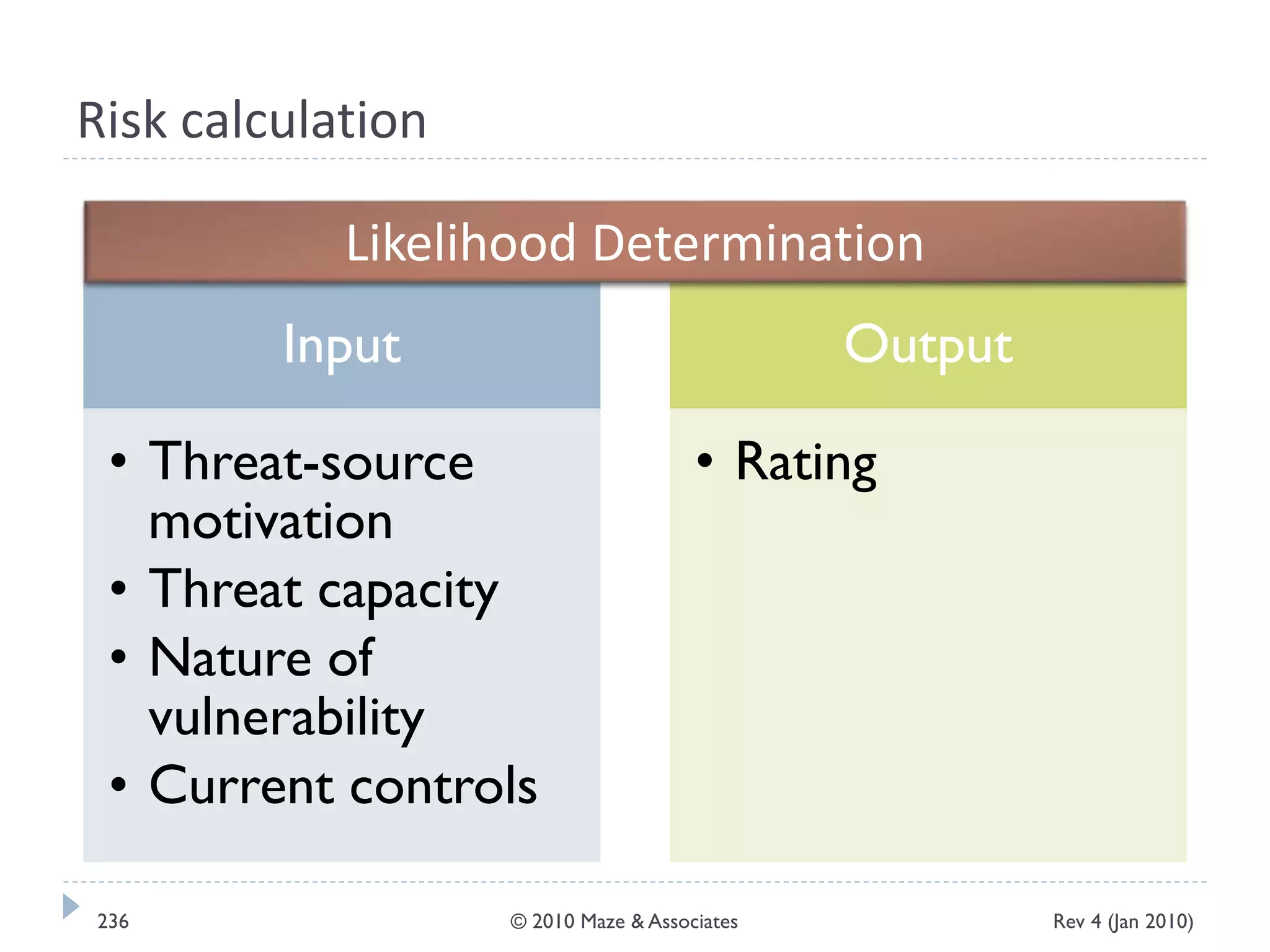
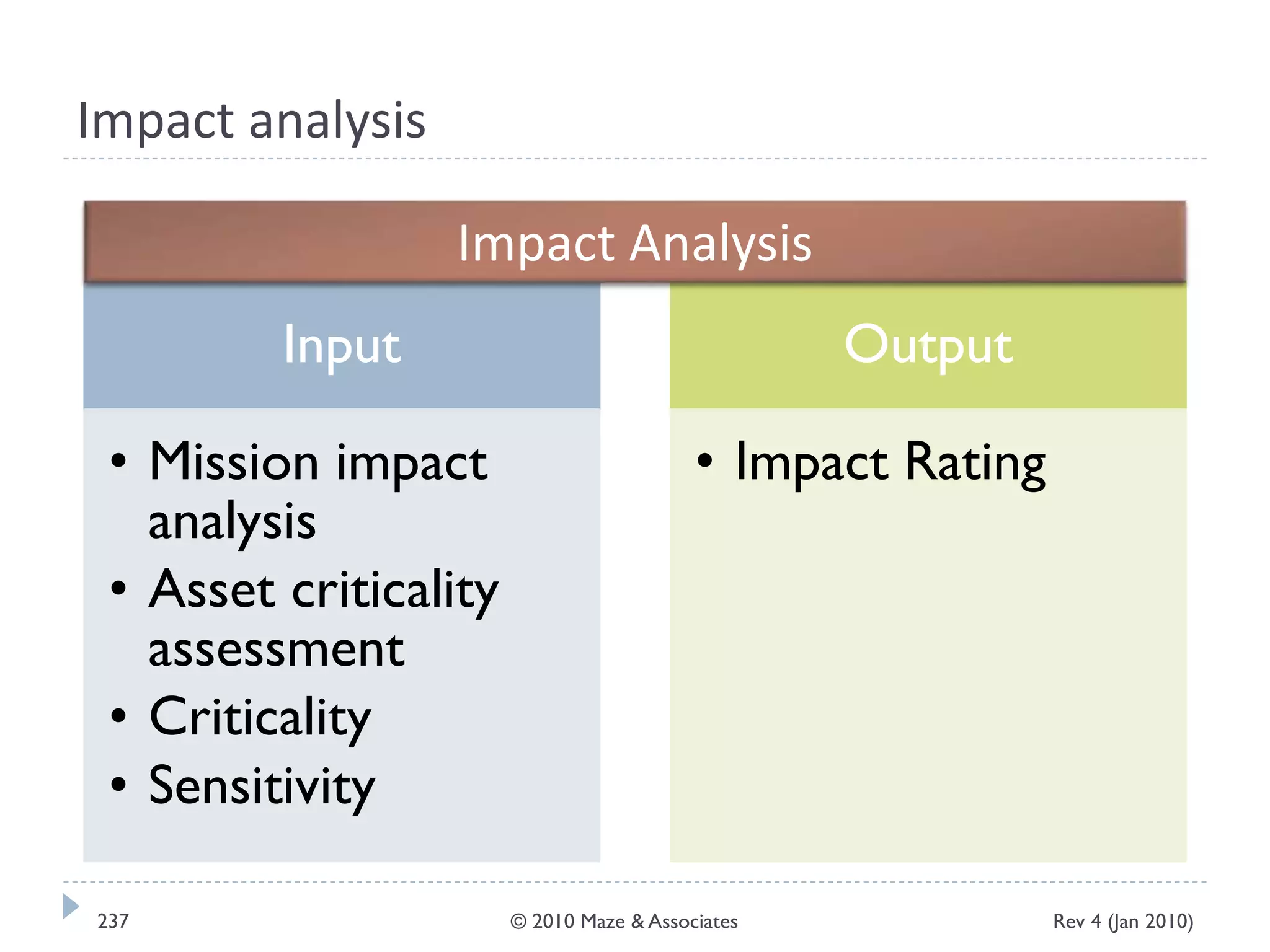
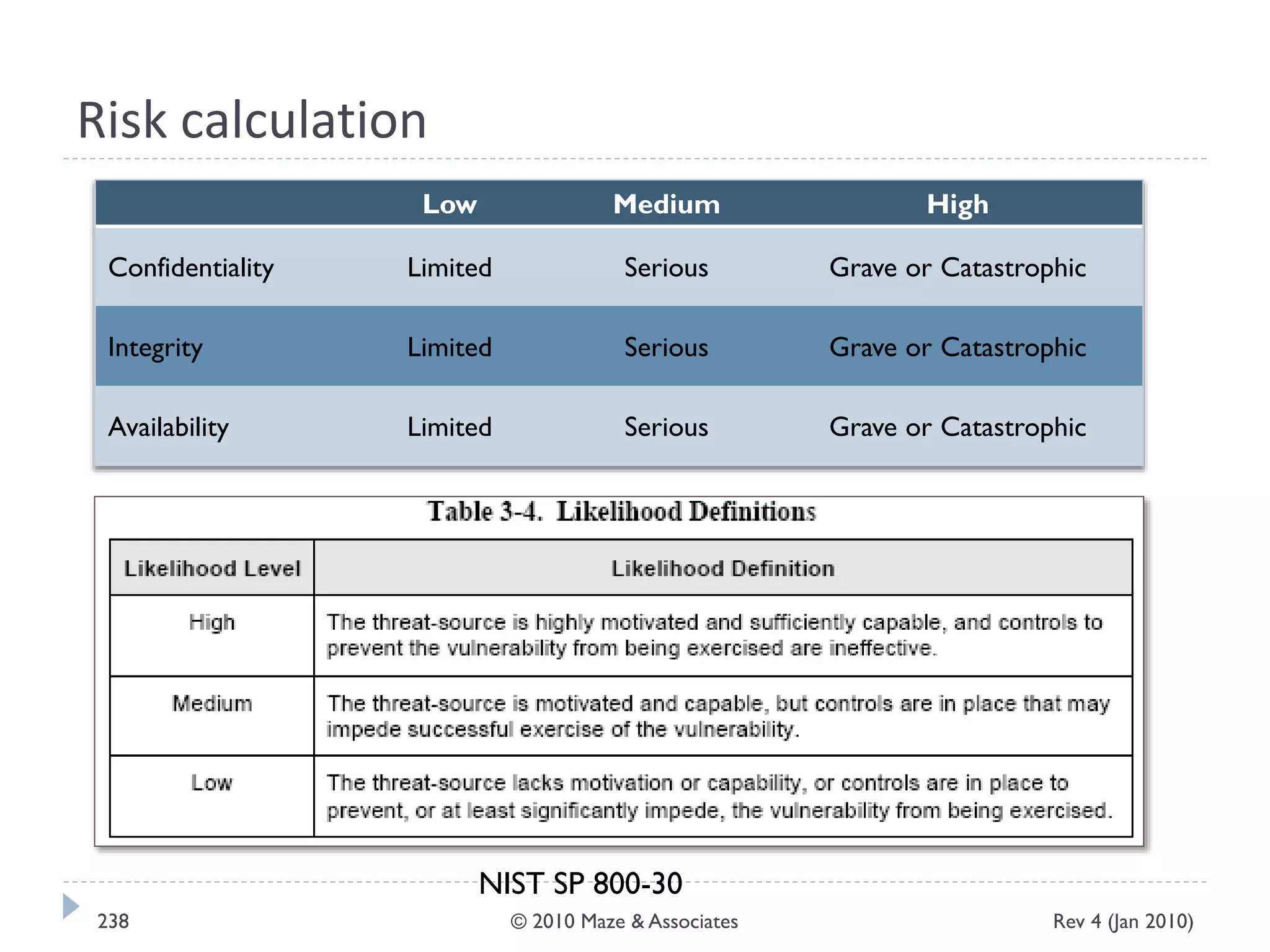
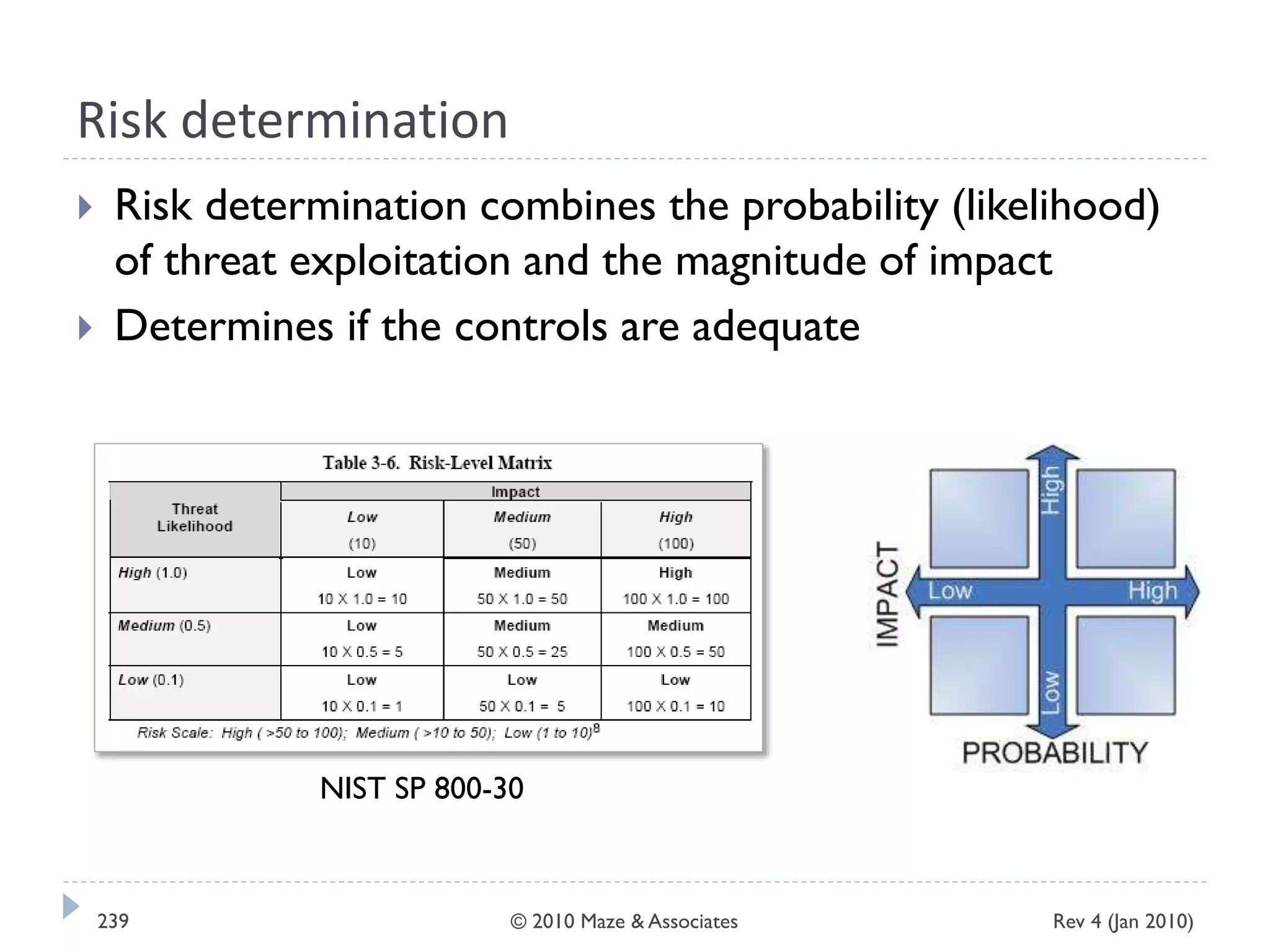
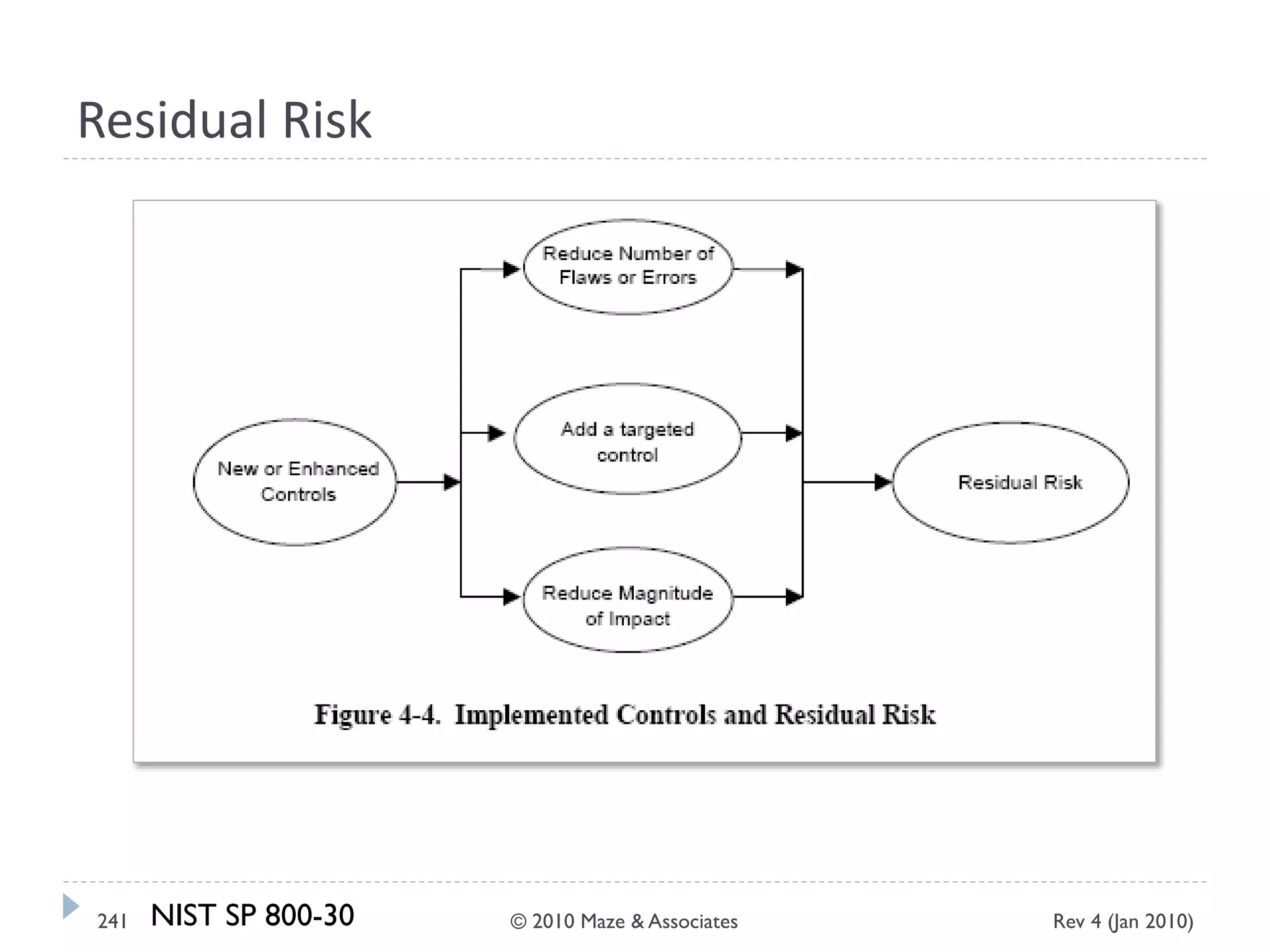
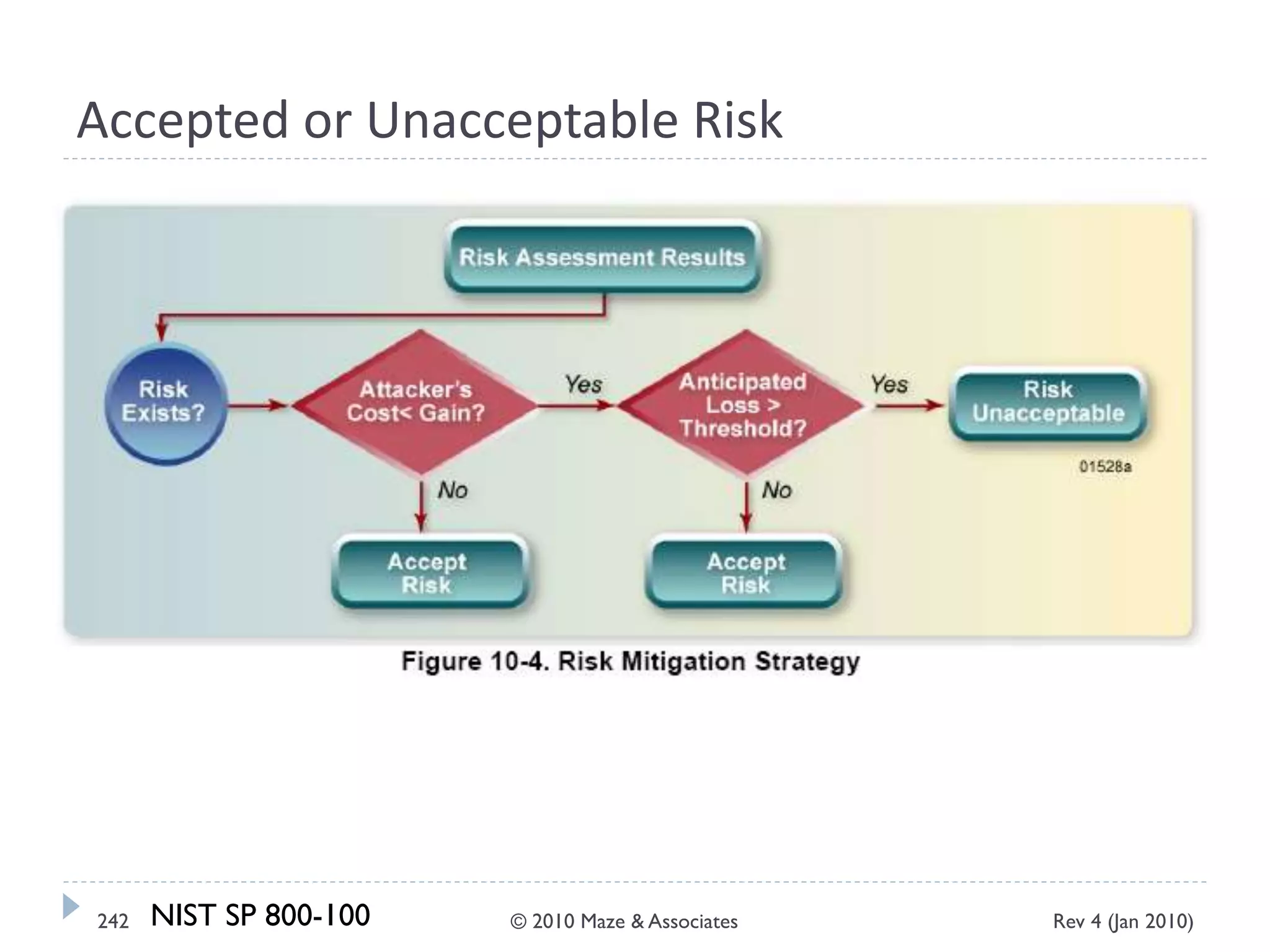
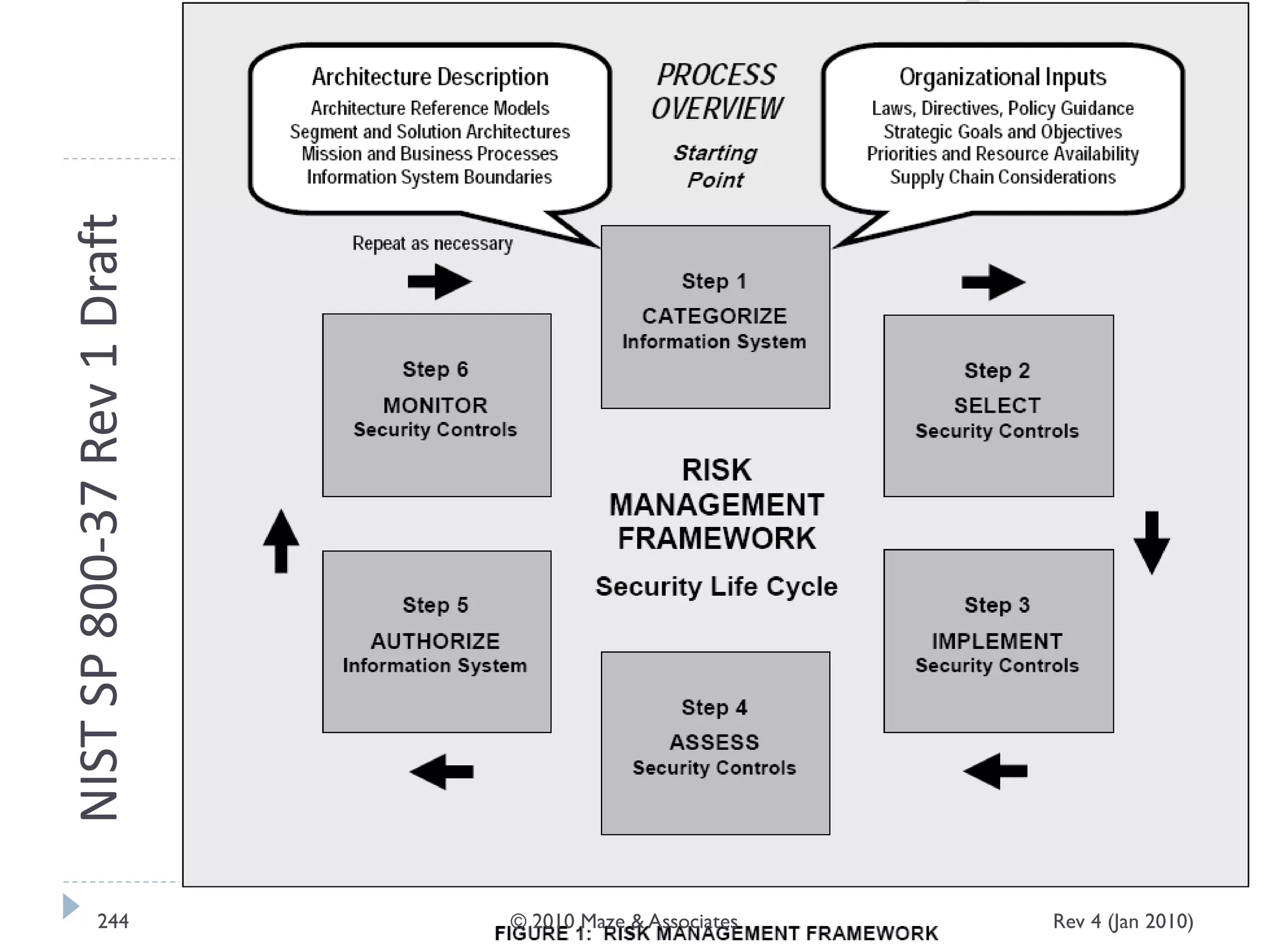
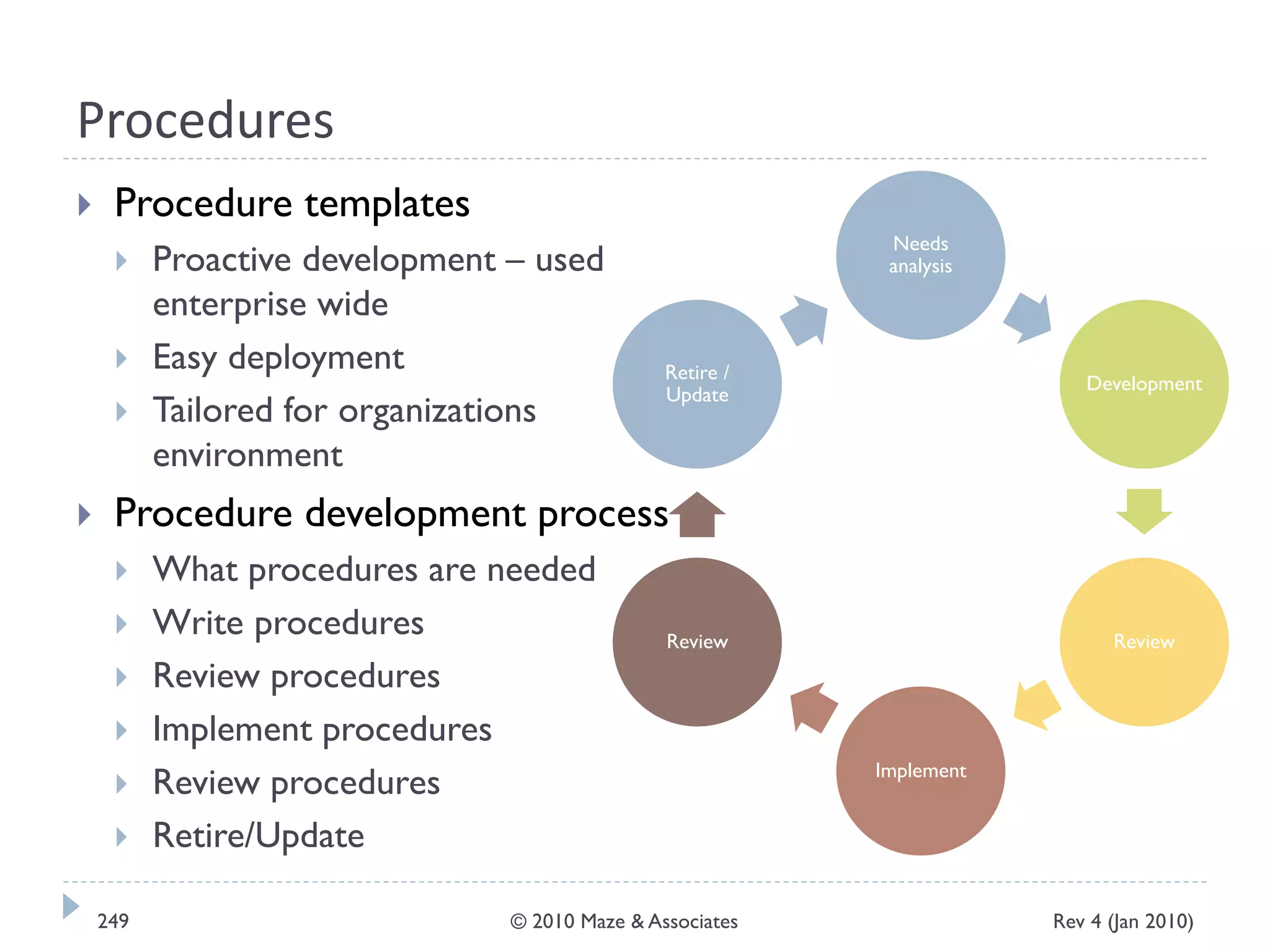
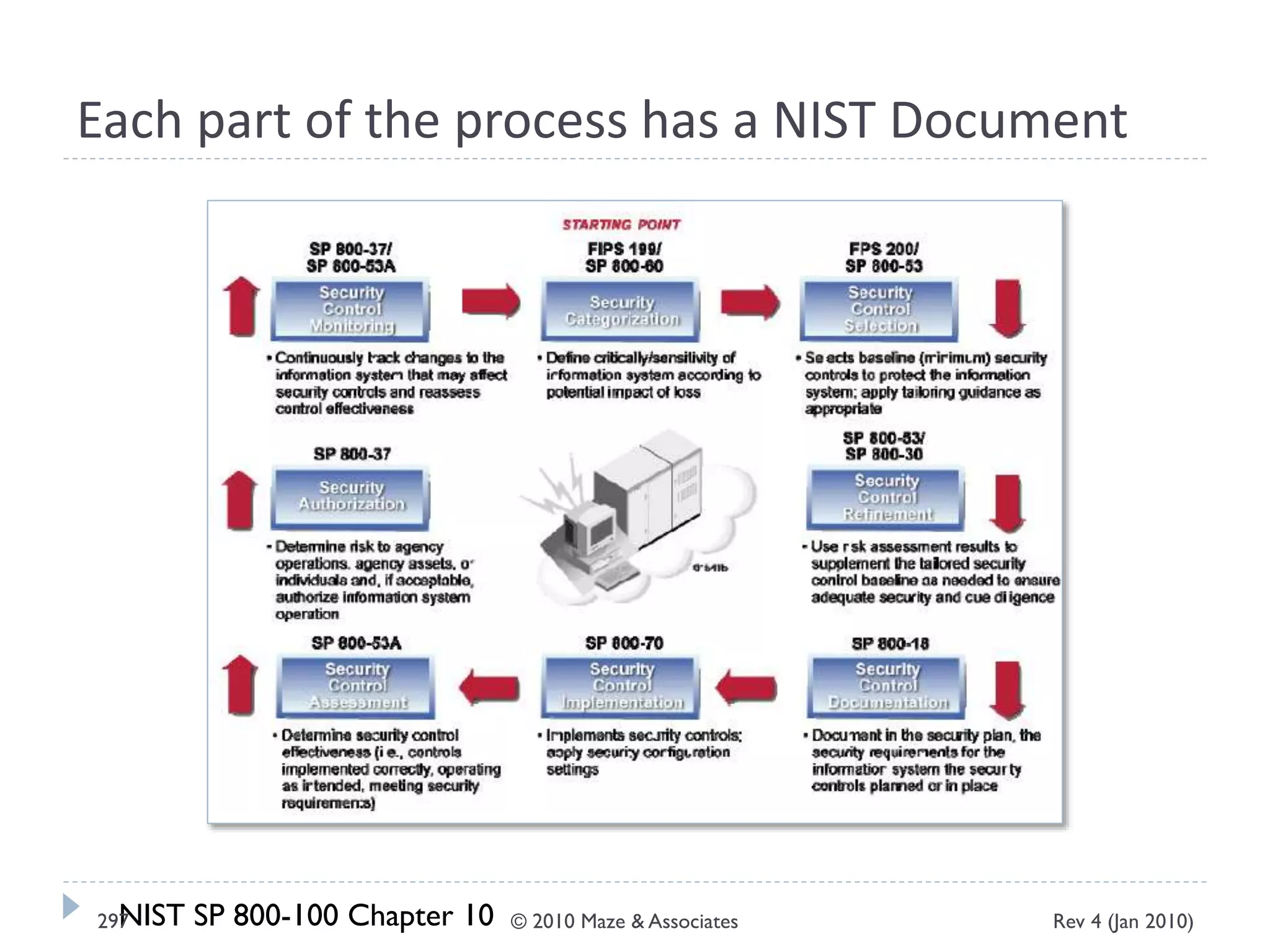
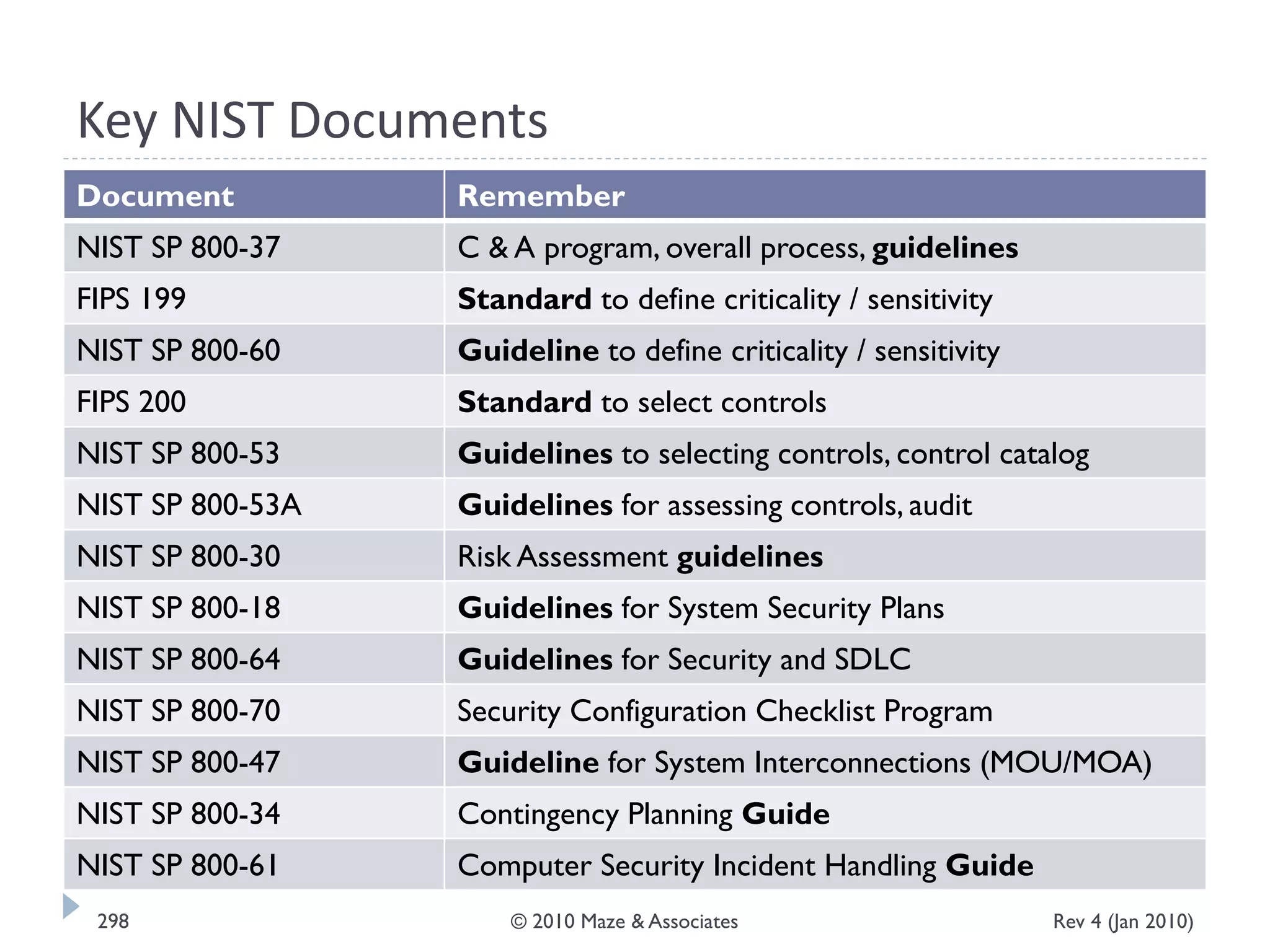
The document provides guidance on implementing a National Institute of Standards and Technology (NIST) framework for local governments. It discusses key elements of establishing a successful certification and accreditation (C&A) program, including developing a business case, setting goals and milestones, providing oversight, maintaining visibility, allocating resources, developing guidance documents, integrating the program, establishing points of contact, measuring progress, and tracking activities and compliance. The overall guidance emphasizes project management best practices for planning and implementing an effective C&A program based on NIST standards.